Access Control
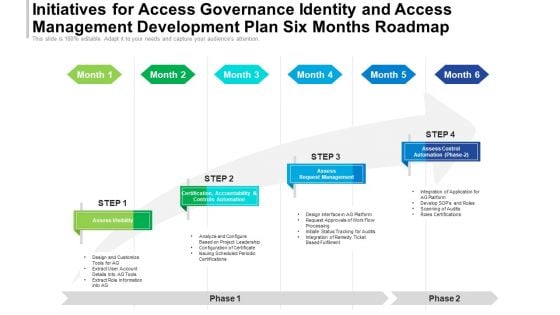
Initiatives For Access Governance Identity And Access Management Development Plan Six Months Roadmap Rules
Presenting the initiatives for access governance identity and access management development plan six months roadmap rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
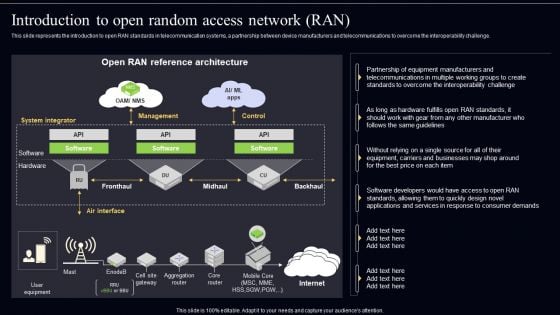
Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
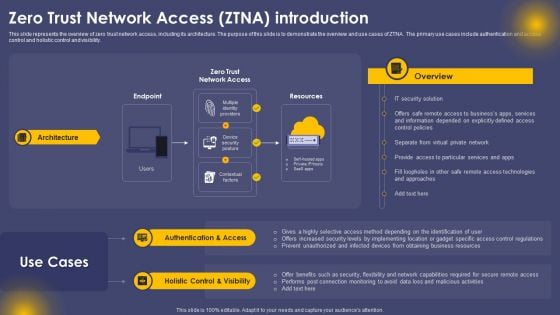
Zero Trust Network Access Ztna Introduction Ppt Slide PDF
This slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Slidegeeks has constructed Zero Trust Network Access Ztna Introduction Ppt Slide PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
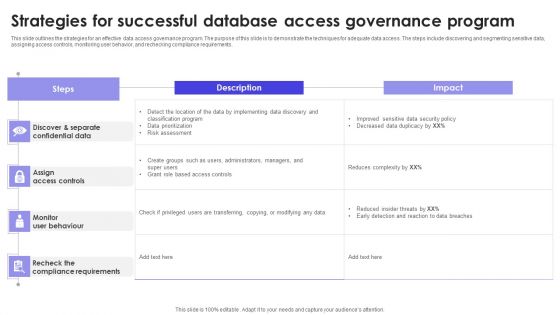
Strategies For Successful Database Access Governance Program Infographics PDF
This slide outlines the strategies for an effective data access governance program. The purpose of this slide is to demonstrate the techniques for adequate data access. The steps include discovering and segmenting sensitive data, assigning access controls, monitoring user behavior, and rechecking compliance requirements. Pitch your topic with ease and precision using this Strategies For Successful Database Access Governance Program Infographics PDF. This layout presents information on Steps, Description, Impact . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Features Of Zero Trust Network Access Security Model Sample PDF
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Explore a selection of the finest Features Of Zero Trust Network Access Security Model Sample PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Features Of Zero Trust Network Access Security Model Sample PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
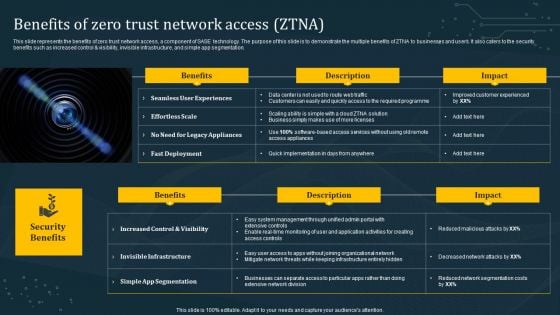
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Identify And Access Management Technique Model Icons PDF
This slide shows controls management model for designing IAM strategy. The purpose of this slide is to highlight important phases with concerned stages for IAM strategy. It include phases such as prepare, develop and deliver , etc. Persuade your audience using this Identify And Access Management Technique Model Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Develop, Deliver. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
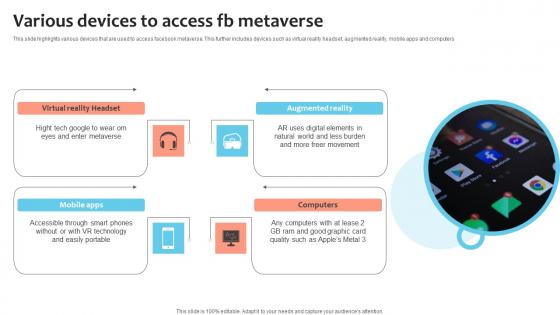
Various Devices To Access Fb Metaverse Elements Pdf
This slide highlights various devices that are used to access facebook metaverse. This further includes devices such as virtual reality headset, augmented reality, mobile apps and computers.Pitch your topic with ease and precision using this Various Devices To Access Fb Metaverse Elements Pdf This layout presents information on Augmented Reality, Accessible Through, Technology Easily Portable It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights various devices that are used to access facebook metaverse. This further includes devices such as virtual reality headset, augmented reality, mobile apps and computers.
Zero Trust Network Access Performance Tracking Dashboar Slides Pdf
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Performance Tracking Dashboar Slides Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

Zero Trust Network Access System Use Cases Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Present like a pro with Zero Trust Network Access System Use Cases Themes Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
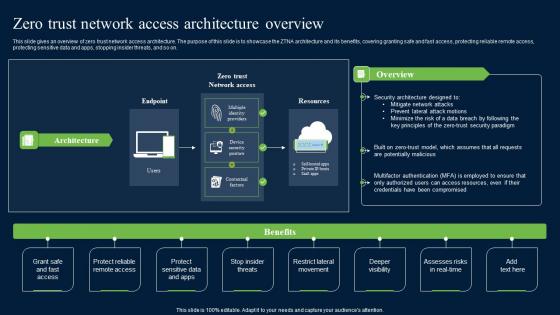
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
Access Denied In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Access Denied In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Access Denied that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Access Denied In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
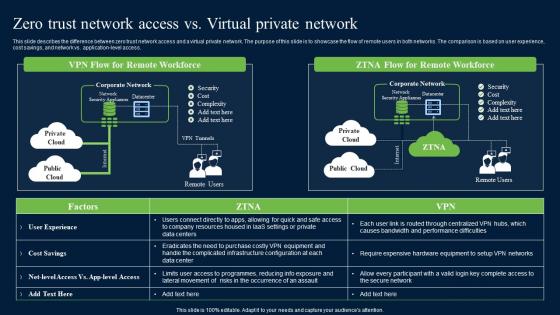
Zero Trust Network Access Vs Virtual Private Network Mockup Pdf
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Vs Virtual Private Network Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Vs Virtual Private Network Mockup Pdf today and make your presentation stand out from the rest This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.
Student Access Report In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Student Access Report In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Student Access Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Student Access Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
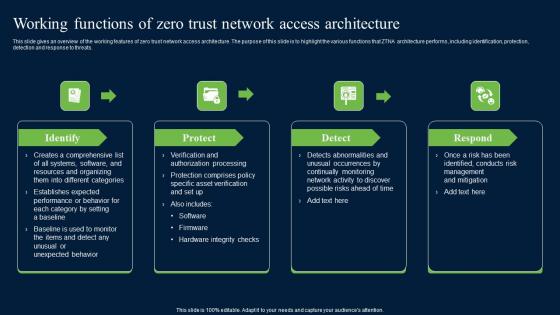
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
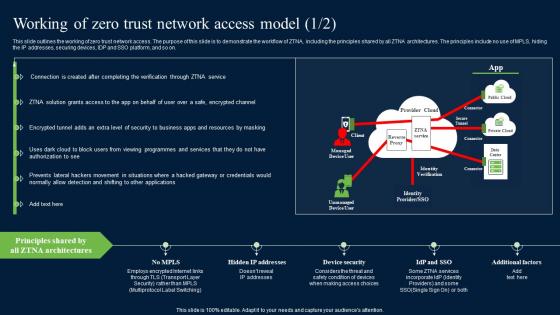
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
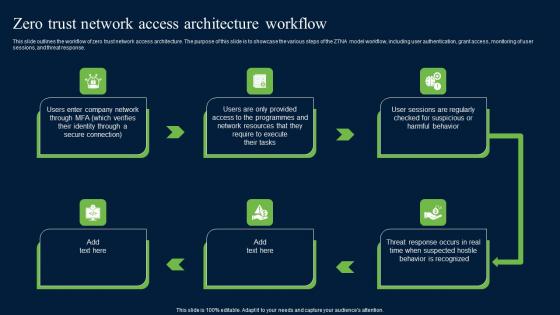
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
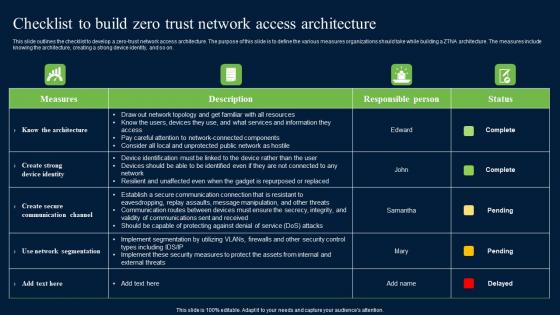
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
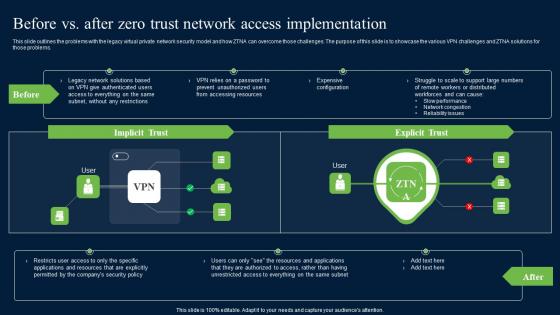
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
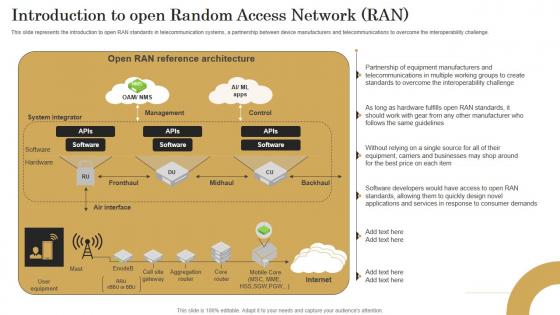
Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge.
Access Form Templates Ppt PowerPoint Presentation Layouts Sample Cpb
This is a access form templates ppt powerpoint presentation layouts sample cpb. This is a four stage process. The stages in this process are access form templates.
Complete Data Easy Access To Data Ppt Example
This is a complete data easy access to data ppt example. This is a four stage process. The stages in this process are trust data, complete data, easy access to data, intuitive tools.
House Training Program Custom Access Ppt PowerPoint Presentation Show Visuals
This is a house training program custom access ppt powerpoint presentation show visuals. This is a six stage process. The stages in this process are house training program, custom access.
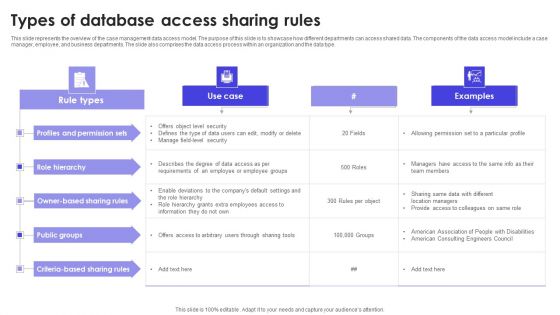
Types Of Database Access Sharing Rules Slides PDF
This slide represents the overview of the case management data access model. The purpose of this slide is to showcase how different departments can access shared data. The components of the data access model include a case manager, employee, and business departments. The slide also comprises the data access process within an organization and the data type. Showcasing this set of slides titled Types Of Database Access Sharing Rules Slides PDF. The topics addressed in these templates are Public Groups, Role Hierarchy, Permission Sets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
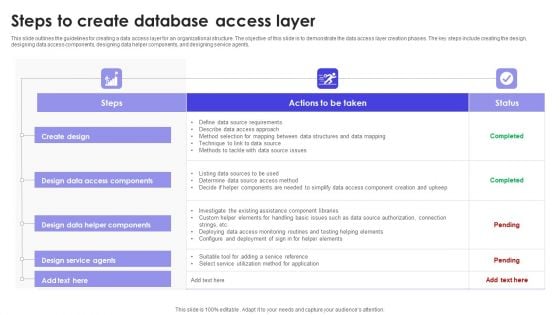
Steps To Create Database Access Layer Slides PDF
This slide outlines the guidelines for creating a data access layer for an organizational structure. The objective of this slide is to demonstrate the data access layer creation phases. The key steps include creating the design, designing data access components, designing data helper components, and designing service agents. Showcasing this set of slides titled Steps To Create Database Access Layer Slides PDF. The topics addressed in these templates are Data Access Components, Create Design, Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
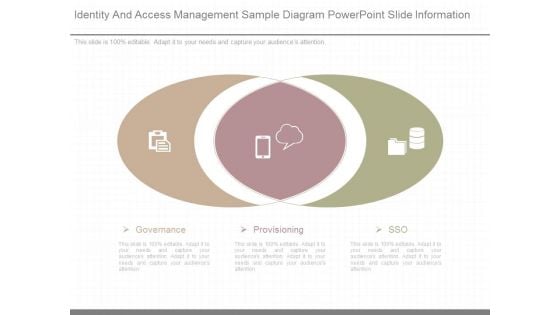
Identity And Access Management Sample Diagram Powerpoint Slide Information
This is a identity and access management sample diagram powerpoint slide information. This is a two stage process. The stages in this process are governance, provisioning, sso.
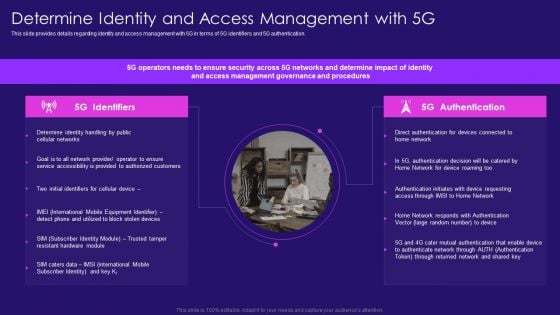
Determine Identity And Access Management With 5G Information PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. Deliver an awe inspiring pitch with this creative Determine Identity And Access Management With 5G Information PDF bundle. Topics like Determine Identity, Accessibility Provided, Identifiers Cellular can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
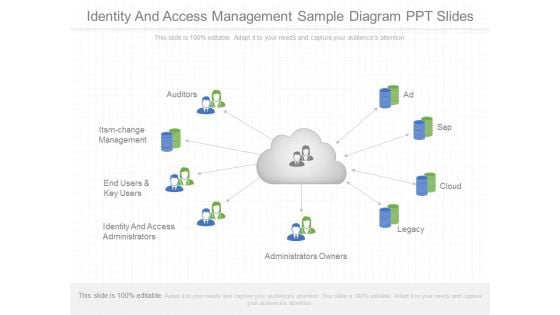
Identity And Access Management Sample Diagram Ppt Slides
This is a identity and access management sample diagram ppt slides. This is a nine stage process. The stages in this process are auditors, itsm change management, end users and key users, identity and access administrators, administrators owners, legacy, cloud, sap, ad.
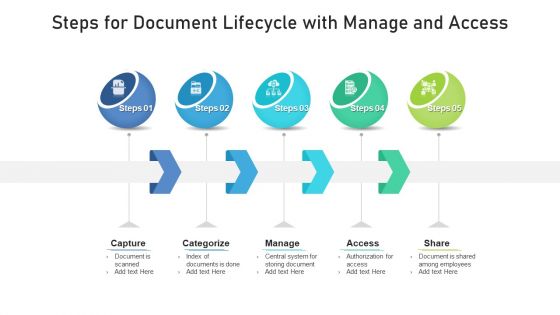
Steps For Document Lifecycle With Manage And Access Template PDF
Presenting steps for document lifecycle with manage and access template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including capture, categorize, manage, access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
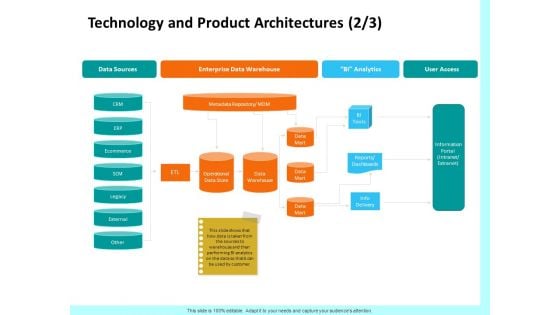
Firm Productivity Administration Technology And Product Architectures Access Background PDF
Presenting this set of slides with name firm productivity administration technology and product architectures access background pdf. This is a one stage process. The stages in this process are data sources, enterprise data warehouse, bi analytics, user access, crm, erp, ecommerce, scm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon For Server Database Access Management Background PDF
Persuade your audience using this Icon For Server Database Access Management Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Server Database, Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Based Identify And Access Management Technique Introduction PDF
Presenting Cloud Based Identify And Access Management Technique Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Based Identify, Access Management, Technique. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Identify And Access Management Technique Icon Information PDF
Showcasing this set of slides titled Identify And Access Management Technique Icon Information PDF. The topics addressed in these templates are Identify, Access Management, Technique. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Identify And Access Management Technique Mechanism Icon Information PDF
Persuade your audience using this Identify And Access Management Technique Mechanism Icon Information PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Access Management, Technique Mechanism. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
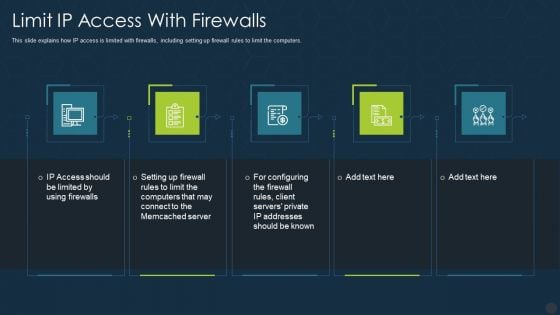
Memcache Technology IT Limit Ip Access With Firewalls Pictures PDF
This slide explains how IP access is limited with firewalls, including setting up firewall rules to limit the computers. This is a memcache technology it limit ip access with firewalls pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like limit ip access with firewalls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Market Access With Arrow Icon Ppt PowerPoint Presentation File Smartart
Presenting this set of slides with name market access with arrow icon ppt powerpoint presentation file smartart. This is a one stage process. The stage in this process is market access with arrow icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
System Access To Management Ppt PowerPoint Presentation Topics
This is a system access to management ppt powerpoint presentation topics. This is a five stage process. The stages in this process are business, management, analysis, strategy, success, process.
Zero Trust Network Access Architecture Overview Icons PDF
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Retrieve professionally designed Zero Trust Network Access Architecture Overview Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
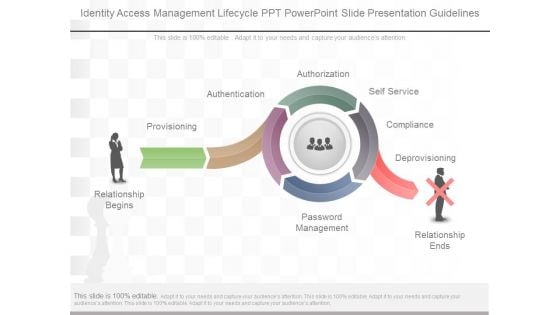
Identity Access Management Lifecycle Ppt Powerpoint Slide Presentation Guidelines
This is a identity access management lifecycle ppt powerpoint slide presentation guidelines. This is a five stage process. The stages in this process are relationship begins, provisioning, authentication, authorization, self service, compliance, deprovisioning, password management, relationship ends.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Difference Identity Access Management Ppt PowerPoint Presentation Outline Introduction Cpb
Presenting this set of slides with name difference identity access management ppt powerpoint presentation outline introduction cpb. This is an editable Powerpoint five stages graphic that deals with topics like difference identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
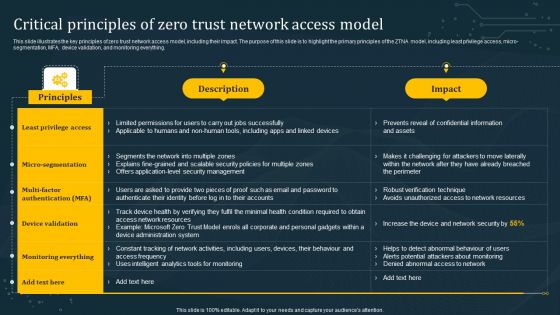
Critical Principles Of Zero Trust Network Access Model Graphics PDF
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Critical Principles Of Zero Trust Network Access Model Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Critical Principles Of Zero Trust Network Access Model Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
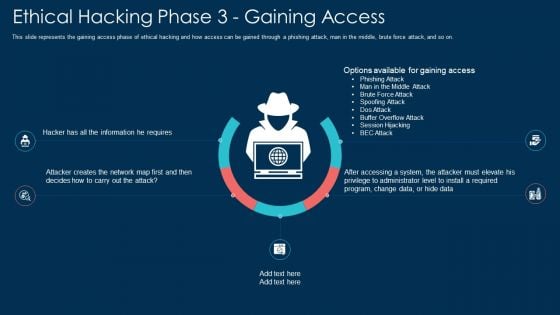
Ethical Hacking Phase 3 Gaining Access Ppt Pictures Vector PDF
This slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. This is a ethical hacking phase 3 gaining access ppt pictures vector pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Access Systems Ppt PowerPoint Presentation Layouts Gridlines Cpb
Presenting this set of slides with name data access systems ppt powerpoint presentation layouts gridlines cpb. This is an editable Powerpoint eight stages graphic that deals with topics like data access systems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
User Access Provisioning Process Ppt PowerPoint Presentation Portfolio Layouts Cpb
Presenting this set of slides with name user access provisioning process ppt powerpoint presentation portfolio layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like user access provisioning process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Access Review Process Ppt PowerPoint Presentation Show Graphic Images Cpb
Presenting this set of slides with name access review process ppt powerpoint presentation show graphic images cpb. This is an editable Powerpoint four stages graphic that deals with topics like access review process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Parallel Computing Processing Introduction To Switched Memory Access Icons PDF
This slide represents the introduction to switched memory access, and a crossbar switch is installed to connect processors. Processors use shared memory in blocks, and connections between processors are made through a crossbar switch. Deliver and pitch your topic in the best possible manner with this Parallel Computing Processing Introduction To Switched Memory Access Icons PDF. Use them to share invaluable insights on Introduction To Switched, Memory Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Quarterly Technology Implementation Roadmap Of Iris Access Regulations System Topics
We present our quarterly technology implementation roadmap of iris access regulations system topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly technology implementation roadmap of iris access regulations system topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Access Management Roles Responsibilities Ppt PowerPoint Presentation Ideas Example Cpb
Presenting this set of slides with name access management roles responsibilities ppt powerpoint presentation ideas example cpb. This is an editable Powerpoint three stages graphic that deals with topics like access management roles responsibilities to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Value Identity Access Management Ppt PowerPoint Presentation Summary Cpb
Presenting this set of slides with name business value identity access management ppt powerpoint presentation summary cpb. This is an editable Powerpoint three stages graphic that deals with topics like business value identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secure Access Management Ppt PowerPoint Presentation Pictures Layout Cpb Pdf
Presenting this set of slides with name secure access management ppt powerpoint presentation pictures layout cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like secure access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
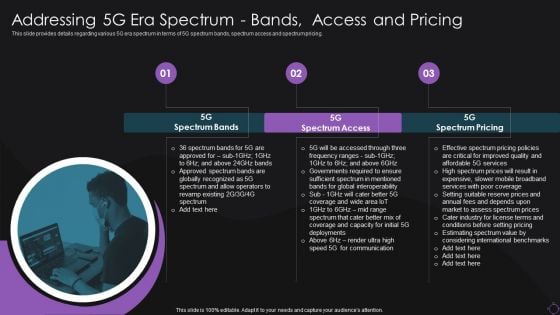
Addressing 5G Era Spectrum Bands Access And Pricing Clipart PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. This is a Addressing 5G Era Spectrum Bands Access And Pricing Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Spectrum Bands, Spectrum Access, Spectrum Pricing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home