Access Control
5G Network Applications And Features Media Access Control MAC Layer Functions Graphics PDF
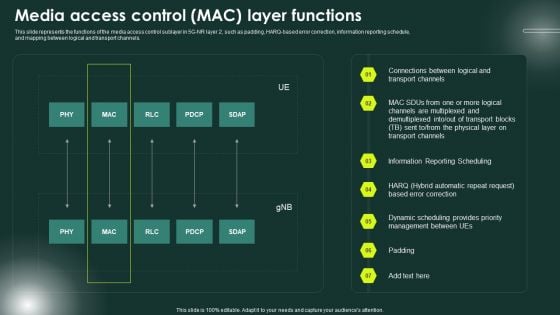
This slide represents the functions of the media access control sublayer in 5G-NR layer 2, such as padding, HARQ-based error correction, information reporting schedule, and mapping between logical and transport channels. Find a pre-designed and impeccable 5G Network Applications And Features Media Access Control MAC Layer Functions Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF
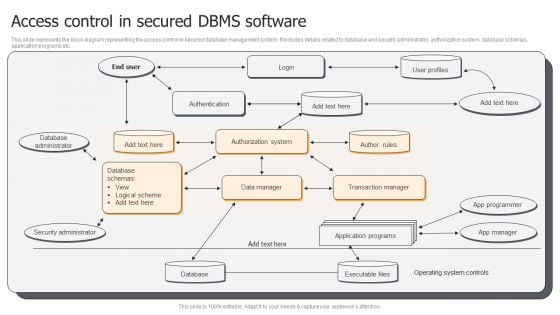
This slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Database Administrator, Security Administrator, Database, Application Programs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Media Access Control Mac Layer Functions 5G Functional Architecture Clipart PDF
Deliver an awe inspiring pitch with this creative Media Access Control Mac Layer Functions 5G Functional Architecture Clipart PDF bundle. Topics like Transport Channels, Scheduling Provides, Management Between can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Media Access Control Mac Layer Functions 5G Network Functional Architecture Inspiration PDF
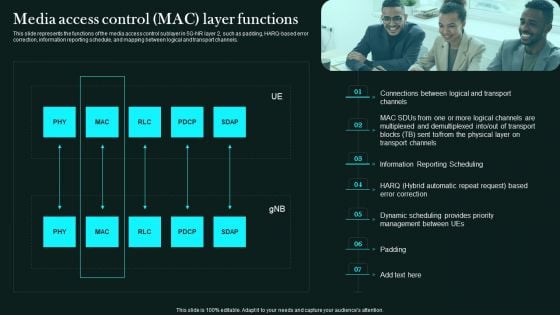
This slide represents the functions of the media access control sublayer in 5G-NR layer 2, such as padding, HARQ-based error correction, information reporting schedule, and mapping between logical and transport channels.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Media Access Control Mac Layer Functions 5G Network Functional Architecture Inspiration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Radio Frequency Identification Technology Access Control System Ppt PowerPoint Presentation Ideas Elements PDF
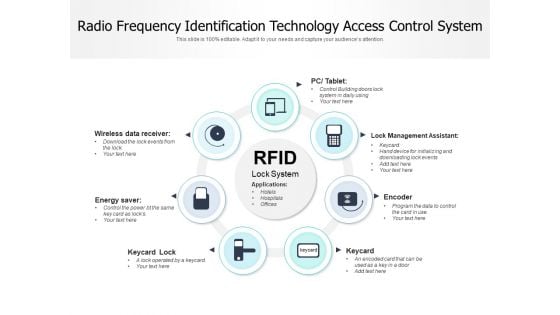
Persuade your audience using this radio frequency identification technology access control system ppt powerpoint presentation ideas elements pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including pc table, lock management assistant, encoder, keycard, keycard lock, energy saver, wireless data receiver. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
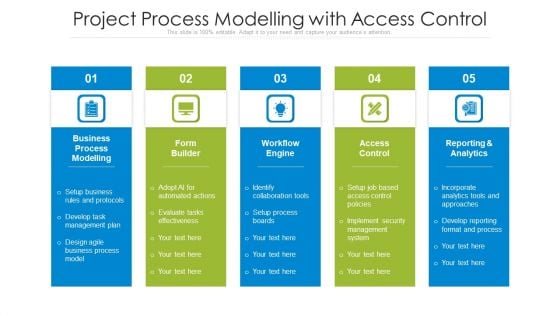
Project Process Modelling With Access Control Ppt PowerPoint Presentation Styles Layouts PDF
Persuade your audience using this project process modelling with access control ppt powerpoint presentation styles layouts pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including setup business rules and protocols, develop task management plan, design agile business process model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
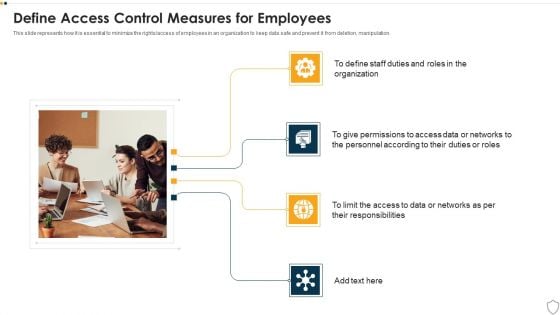
Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Define Access Control Measures For Employees Ppt Styles Good PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting it security define access control measures for employees ppt styles good pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like organization, responsibilities, access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Define Access Control Measures For Employees Ppt Show Clipart Images PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a cybersecurity define access control measures for employees ppt show clipart images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
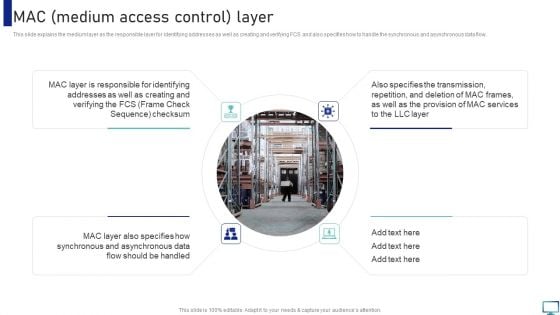
Optimizing Fiber Distributed Data Interface To Enhance Processes Mac Medium Access Control Layer Portrait PDF
This slide explains the medium layer as the responsible layer for identifying addresses as well as creating and verifying FCS and also specifies how to handle the synchronous and asynchronous data flow. Slidegeeks is here to make your presentations a breeze with Optimizing Fiber Distributed Data Interface To Enhance Processes Mac Medium Access Control Layer Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Role Based Access Control Model Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Role Based Access Control Model Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the Twelve slides included in this sample template can be used to present a birds eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Access Control Computer Screen With Lock Ppt PowerPoint Presentation Ideas Templates
This is aaccess control computer screen with lock ppt powerpoint presentation ideas templates. This is a two stage process. The stages in this process are access rights, access management, business.

Security Management Plan Steps In Detail Adopting Access Controls Clipart PDF
Deliver and pitch your topic in the best possible manner with this Security management plan steps in detail adopting access controls clipart pdf. Use them to share invaluable insights on logical access controls, physical access controls, control implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Demonstration PDF
Presenting security management plan steps in detail adopting access controls demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like logical access controls, control implementation, physical access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Determine User Access Controls Levels Guidelines PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Deliver an awe inspiring pitch with this creative developing firm security strategy plan determine user access controls levels guidelines pdf bundle. Topics like administrator, maintainer, guest or disabled can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Control Access To Private Content Ppt PowerPoint Presentation Portfolio Outfit
This is a control access to private content ppt powerpoint presentation portfolio outfit. This is a three stage process. The stages in this process are access rights, access management, business.
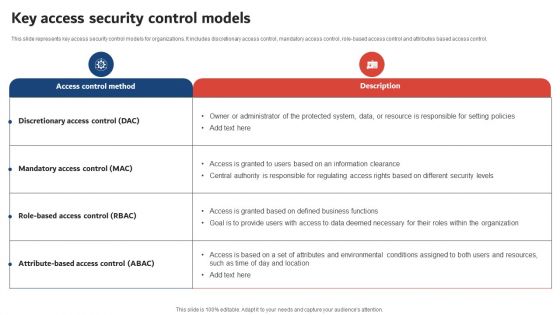
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Security Control Laptop Access Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security control laptop access ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the eleven slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Rate Limits For Controlling User Access Creative Applications For Open AI Elements Pdf
This slide showcases rate limits for ChatGPT and ChatGPT-4 which will enforce users to utilize application programming interface APIs abilities in controlled manner. It provides details about tokens per minute and requests per minute. Take your projects to the next level with our ultimate collection of Rate Limits For Controlling User Access Creative Applications For Open AI Elements Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide showcases rate limits for ChatGPT and ChatGPT-4 which will enforce users to utilize application programming interface APIs abilities in controlled manner. It provides details about tokens per minute and requests per minute.
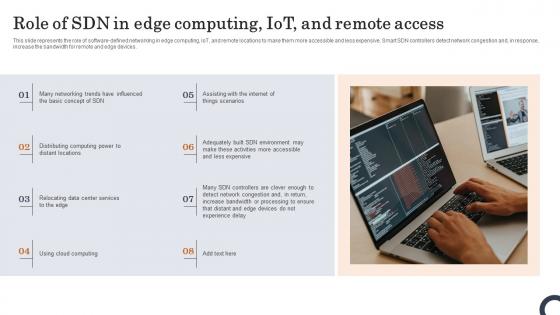
Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. This Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices.

Leveraging Openai API For Business Rate Limits For Controlling User Access Pictures PDF
This slide showcases rate limits for ChatGPT and ChatGPT-4 which will enforce users to utilize application programming interface APIs abilities in controlled manner. It provides details about tokens per minute and requests per minute. There are so many reasons you need a Leveraging Openai API For Business Rate Limits For Controlling User Access Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
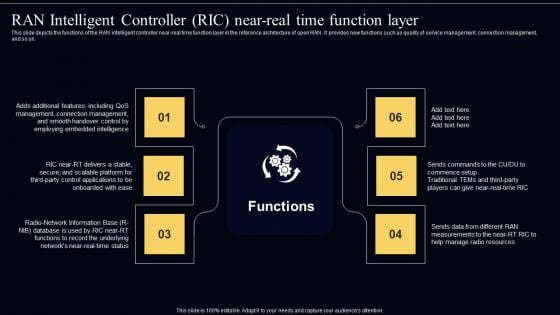
Open Radio Access Network IT RAN Intelligent Controller RIC Near Real Time Function Layer Professional PDF
This slide depicts the functions of the RAN intelligent controller near-real time function layer in the reference architecture of open RAN. It provides new functions such as quality of service management, connection management, and so on. This modern and well arranged Open Radio Access Network IT RAN Intelligent Controller RIC Near Real Time Function Layer Professional PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Docsend Capital Fundraising Controls For Limiting Doc Access Ppt Inspiration Smartart PDF
This slide shows the controls for limiting doc access such as tracking doc forwarding, Expiration dates, etc. Deliver an awe inspiring pitch with this creative docsend capital fundraising controls for limiting doc access ppt inspiration smartart pdf bundle. Topics like controls for limiting doc access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Docsend Capital Raising Pitch Deck Controls For Limiting Doc Access Themes PDF
This slide shows the controls for limiting doc access such as tracking doc forwarding, Expiration dates, etc.Deliver an awe inspiring pitch with this creative Docsend Capital Raising Pitch Deck Controls For Limiting Doc Access Themes PDF bundle. Topics like Expiration Dates, Passcode Required, Download Restrictions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
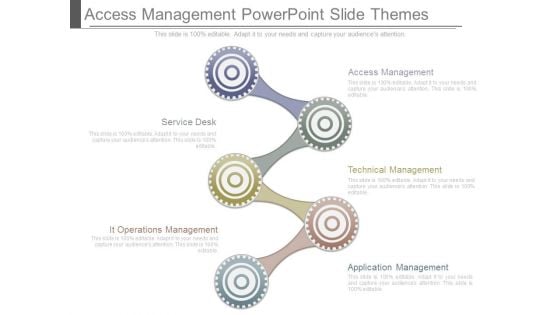
Access Management Powerpoint Slide Themes
This is a access management powerpoint slide themes. This is a five stage process. The stages in this process are access management, service desk, technical management, it operations management, application management.
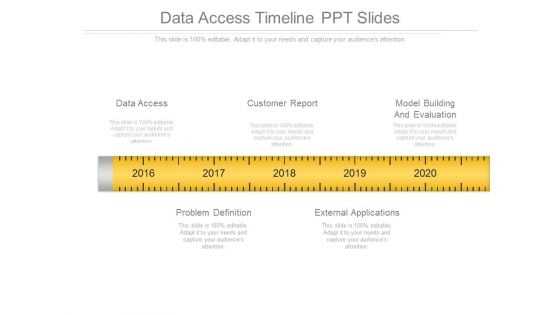
Data Access Timeline Ppt Slides
This is a data access timeline ppt slides. This is a five stage process. The stages in this process are data access, customer report, model building and evaluation, problem definition, external applications.
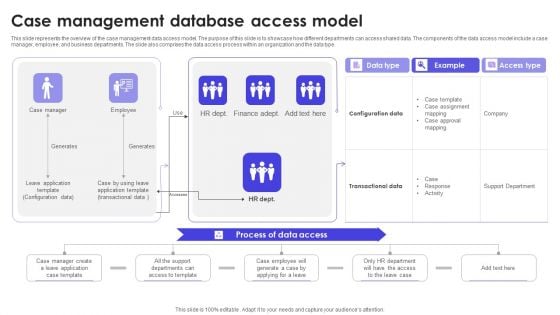
Case Management Database Access Model Download PDF
This slide represents the overview of the case management data access model. The purpose of this slide is to showcase how different departments can access shared data. The components of the data access model include a case manager, employee, and business departments. The slide also comprises the data access process within an organization and the data type. Showcasing this set of slides titled Case Management Database Access Model Download PDF. The topics addressed in these templates are Data Access, Example, Data Type. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
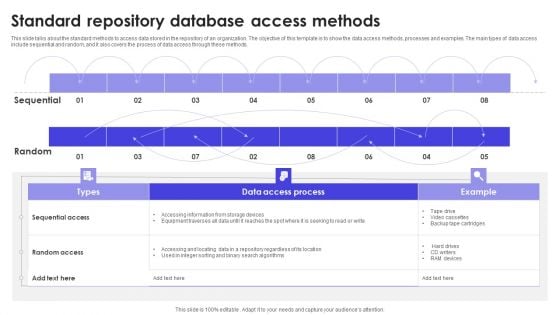
Standard Repository Database Access Methods Formats PDF
This slide talks about the standard methods to access data stored in the repository of an organization. The objective of this template is to show the data access methods, processes and examples. The main types of data access include sequential and random, and it also covers the process of data access through these methods. Pitch your topic with ease and precision using this Standard Repository Database Access Methods Formats PDF. This layout presents information on Sequential, Random, Methods. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Increasing Speed Access Knowledge Ppt Sample
This is a increasing speed access knowledge ppt sample. This is a four stage process. The stages in this process are increasing speed access knowledge, reducing communication costs, increasing satisfaction of suppliers, partner and external experts.

Easy Access To Distribution Channels Ppt Slides
This is an easy access to distribution channels ppt slides. This is a four stage process. The stages in this process are industry overview, easy access to distribution channels, low initial capital investment, lower consumer switching costs.
Access Of Distribution Channels Ppt Slide Design
This is a access of distribution channels ppt slide design. This is a four stage process. The stages in this process are brand identity, economies of scale, access of distribution channels, product differentiation.
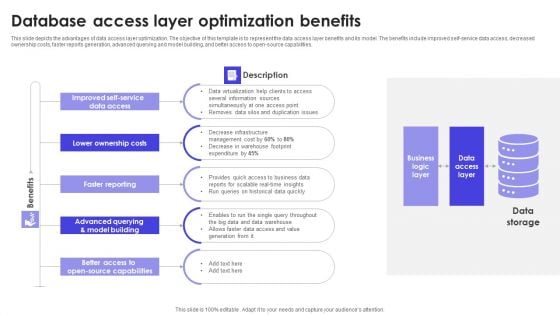
Database Access Layer Optimization Benefits Slides PDF
This slide depicts the advantages of data access layer optimization. The objective of this template is to represent the data access layer benefits and its model. The benefits include improved self-service data access, decreased ownership costs, faster reports generation, advanced querying and model building, and better access to open-source capabilities. Presenting Database Access Layer Optimization Benefits Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Benefits, Lower Ownership Costs, Faster Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Access Worldwide Template Powerpoint Templates
This is a internet access worldwide template powerpoint templates. This is a four stage process. The stages in this process are information, technology, innovation, foundation.
Analytical Access Example Sample Presentation Ppt
This is a analytical access example sample presentation ppt. This is a four stage process. The stages in this process are hypothesis, collect facts, optimize, measure.
Inventory Management Access Diagram Powerpoint Themes
This is a inventory management access diagram powerpoint themes. This is a eight stage process. The stages in this process are product inventory, product sales, physical inventory, store manager, engage, measure, accounting manager, supplier manager.

System Access Benefits Ppt PowerPoint Presentation Visuals
This is a system access benefits ppt powerpoint presentation visuals. This is a one stage process. The stages in this process are for human resource management, for operation management, for goal and target setting.
Initiatives For Access Governance Identity And Access Management Development Plan Five Year Roadmap Themes
We present our initiatives for access governance identity and access management development plan five year roadmap themes. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for access governance identity and access management development plan five year roadmap themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
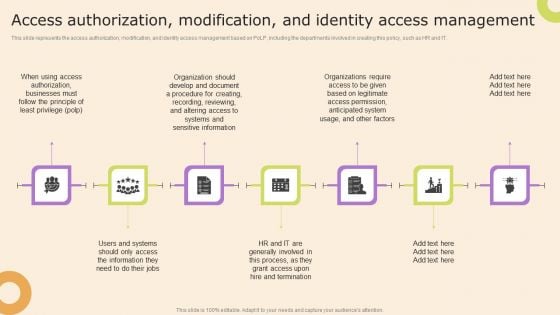
Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF
This slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Create an editable Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Information Technology Policy And Processes Access Authorization Modification And Identity Access Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
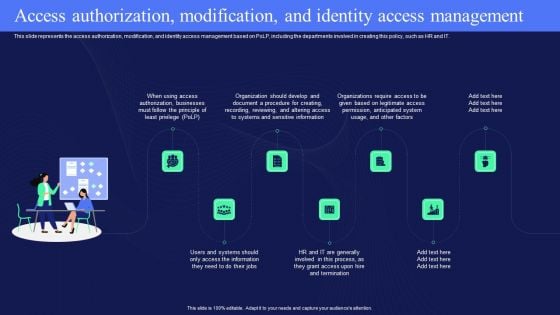
IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF
This slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
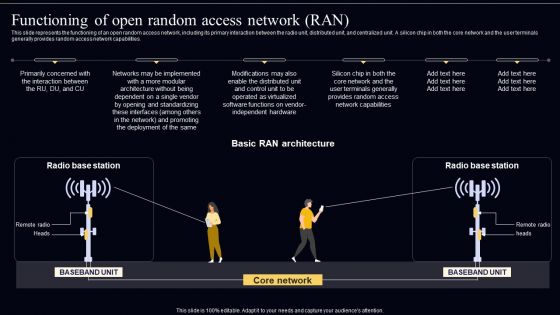
Open Radio Access Network IT Functioning Of Open Random Access Network RAN Sample PDF
This slide represents the functioning of an open random access network, including its primary interaction between the radio unit, distributed unit, and centralized unit. A silicon chip in both the core network and the user terminals generally provides random access network capabilities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Open Radio Access Network IT Functioning Of Open Random Access Network RAN Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Open Radio Access Network IT Functioning Of Open Random Access Network RAN Sample PDF.
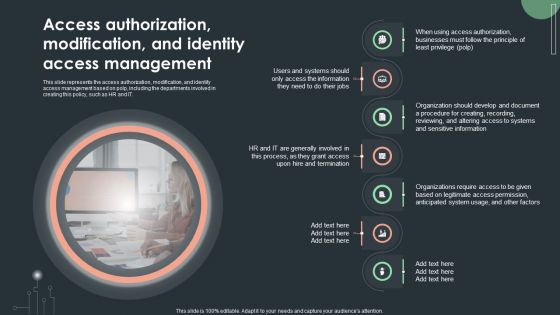
Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF
This slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
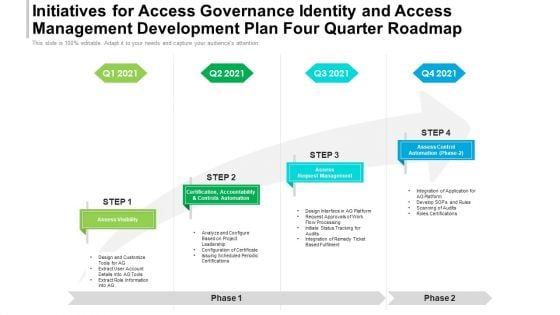
Initiatives For Access Governance Identity And Access Management Development Plan Four Quarter Roadmap Guidelines
Presenting our innovatively-structured initiatives for access governance identity and access management development plan four quarter roadmap guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
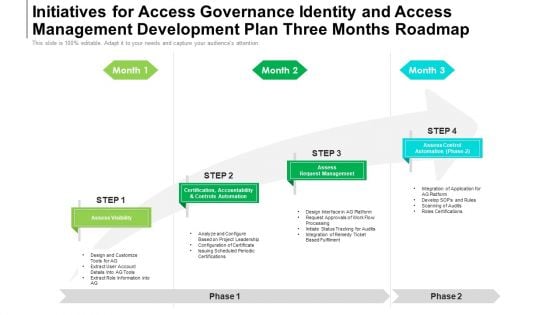
Initiatives For Access Governance Identity And Access Management Development Plan Three Months Roadmap Slides
Presenting our jaw-dropping initiatives for access governance identity and access management development plan three months roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
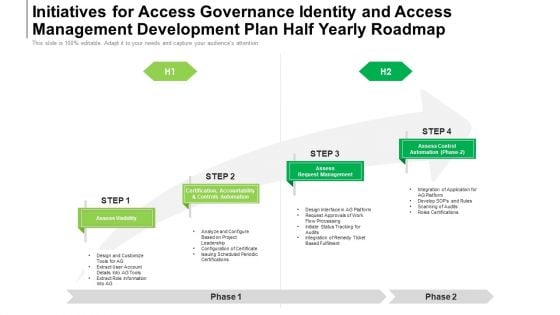
Initiatives For Access Governance Identity And Access Management Development Plan Half Yearly Roadmap Graphics
Introducing our initiatives for access governance identity and access management development plan half yearly roadmap graphics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
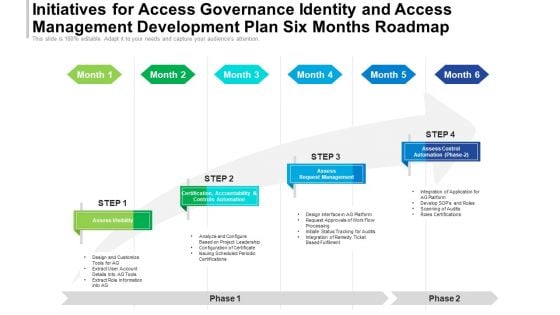
Initiatives For Access Governance Identity And Access Management Development Plan Six Months Roadmap Rules
Presenting the initiatives for access governance identity and access management development plan six months roadmap rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
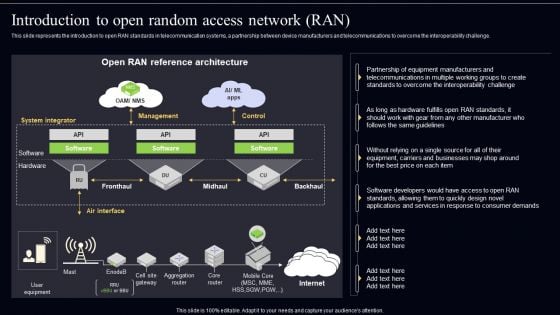
Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
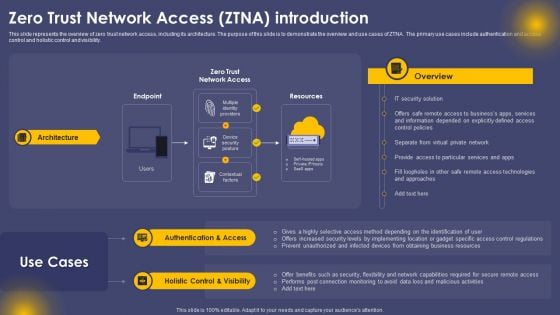
Zero Trust Network Access Ztna Introduction Ppt Slide PDF
This slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Slidegeeks has constructed Zero Trust Network Access Ztna Introduction Ppt Slide PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
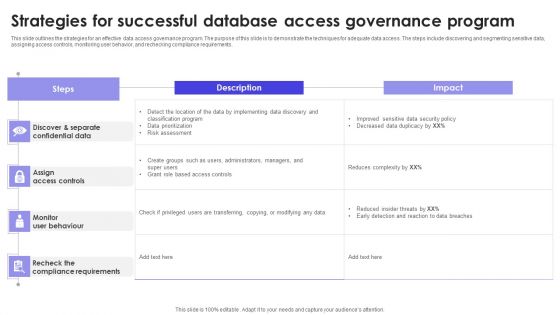
Strategies For Successful Database Access Governance Program Infographics PDF
This slide outlines the strategies for an effective data access governance program. The purpose of this slide is to demonstrate the techniques for adequate data access. The steps include discovering and segmenting sensitive data, assigning access controls, monitoring user behavior, and rechecking compliance requirements. Pitch your topic with ease and precision using this Strategies For Successful Database Access Governance Program Infographics PDF. This layout presents information on Steps, Description, Impact . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Features Of Zero Trust Network Access Security Model Sample PDF
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Explore a selection of the finest Features Of Zero Trust Network Access Security Model Sample PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Features Of Zero Trust Network Access Security Model Sample PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
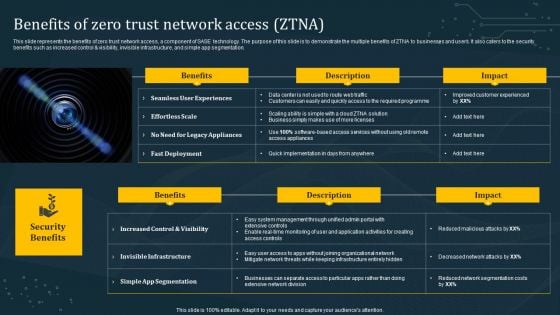
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

 Home
Home