Authentication

Leadership And Authenticity Ppt Presentation
This is a leadership and authenticity ppt presentation. This is a four stage process. The stages in this process are outdoor activity day, personal leadership challenges, authentic leadership, leadership and authenticity.
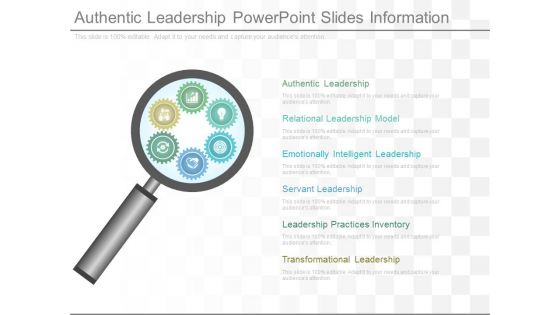
Authentic Leadership Powerpoint Slides Information
This is a authentic leadership powerpoint slides information. This is a six stage process. The stages in this process are authentic leadership, relational leadership model, emotionally intelligent leadership, servant leadership, leadership practices inventory, transformational leadership.
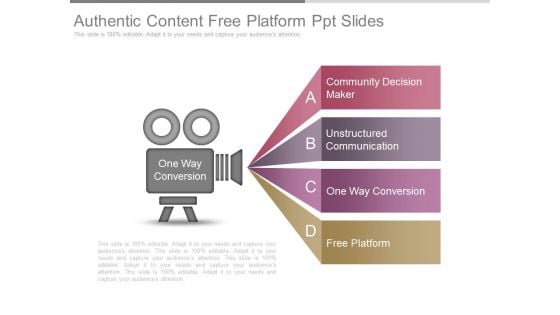
Authentic Content Free Platform Ppt Slides
This is a authentic content free platform ppt slides. This is a four stage process. The stages in this process are design, success, business.

Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Emotional Appeal Authenticity that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Italian Food Dishes Authentic Dish Palo Risotto Clipart PDF
Pitch your topic with ease and precision using this Italian Food Dishes Authentic Dish Palo Risotto Clipart PDF. This layout presents information on Italian Food Dishes, Authentic Dish Palo Risotto. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
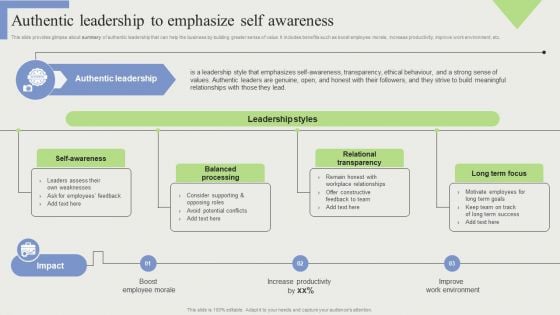
Authentic Leadership To Emphasize Self Awareness Themes PDF
This slide provides glimpse about summary of authentic leadership that can help the business by building greater sense of value. It includes benefits such as boost employee morale, increase productivity, improve work environment, etc. Boost your pitch with our creative Authentic Leadership To Emphasize Self Awareness Themes PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Authentic American Cuisine Stamp Sign Logo Ppt PowerPoint Presentation File Graphics Template
This is a authentic american cuisine stamp sign logo ppt powerpoint presentation file graphics template. This is a three stage process. The stages in this process are american cuisine, american meal, american food.

Authentic American Food Burger Logo Stamp Design Ppt PowerPoint Presentation File Elements
This is a authentic american food burger logo stamp design ppt powerpoint presentation file elements. This is a four stage process. The stages in this process are american cuisine, american meal, american food.
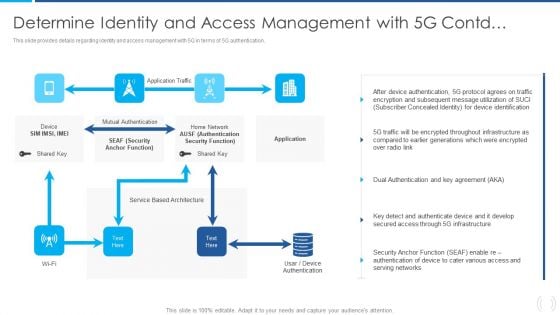
Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF Use them to share invaluable insights on Mutual Authentication, Authentication Security, Service Based and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
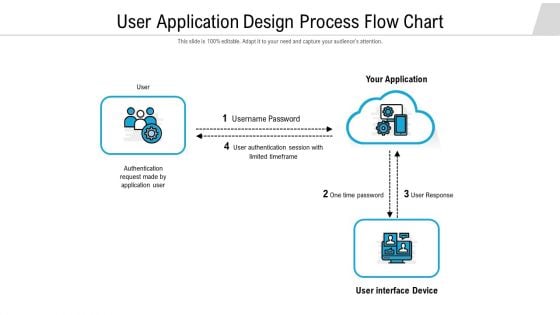
User Application Design Process Flow Chart Demonstration PDF
Presenting user application design process flow chart demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including authentication request made by application user, username password, authentication session with limited timeframe. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
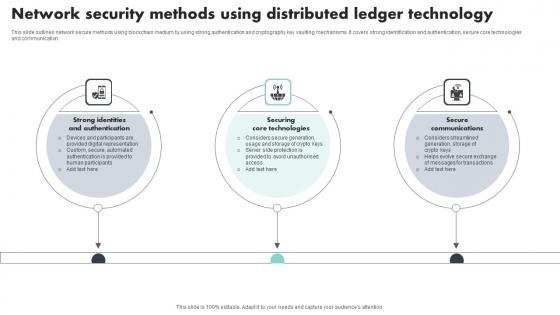
Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
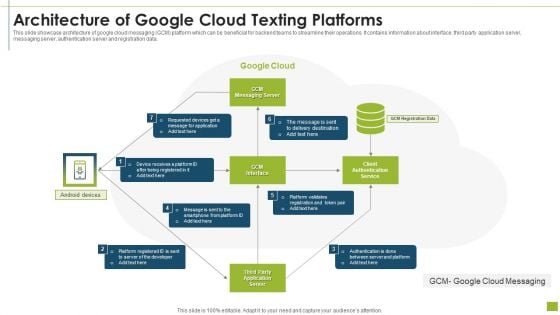
Architecture Of Google Cloud Texting Platforms Demonstration PDF
This slide showcase architecture of google cloud messaging GCM platform which can be beneficial for backend teams to streamline their operations. It contains information about interface, third party application server, messaging server, authentication server and registration data.Showcasing this set of slides titled architecture of google cloud texting platforms demonstration pdf The topics addressed in these templates are authentication is done between, server and platform, client authentication service All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Password Protection Information Security Icon Ppt Powerpoint Presentation Visual Aids Portfolio
This is a password protection information security icon ppt powerpoint presentation visual aids portfolio. This is a three stage process. The stages in this process are password, access approval, authentication icon.
User Access And Validation Vector Icon Ppt Powerpoint Presentation Slides Slideshow
This is a user access and validation vector icon ppt powerpoint presentation slides slideshow. This is a four stage process. The stages in this process are password, access approval, authentication icon.
Mail With Key Email Security Vector Icon Ppt Powerpoint Presentation Icon Templates
This is a mail with key email security vector icon ppt powerpoint presentation icon templates. This is a three stage process. The stages in this process are password, access approval, authentication icon.
Mobile With Fingerprint Scanner Vector Icon Ppt Powerpoint Presentation Outline Slide
This is a mobile with fingerprint scanner vector icon ppt powerpoint presentation outline slide. This is a four stage process. The stages in this process are password, access approval, authentication icon.
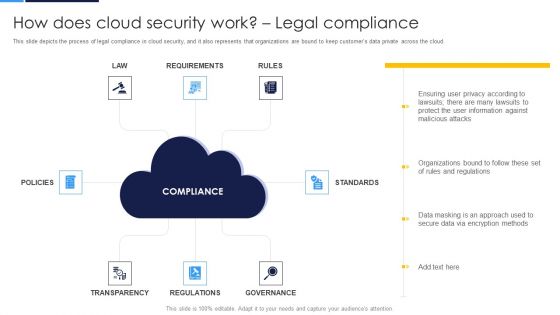
Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enterprise Cloud Security Solutions Professional PDF
This slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Deliver an awe inspiring pitch with this creative Enterprise Cloud Security Solutions Professional PDF bundle. Topics like Services Proactively, Analyze Cost Benefits, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
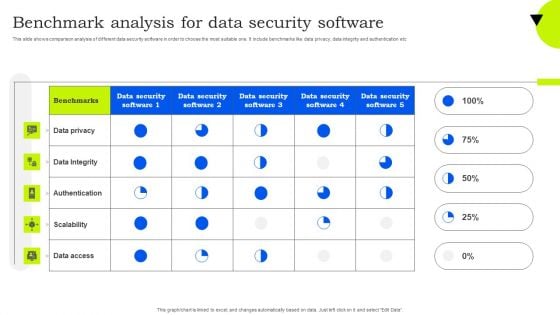
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
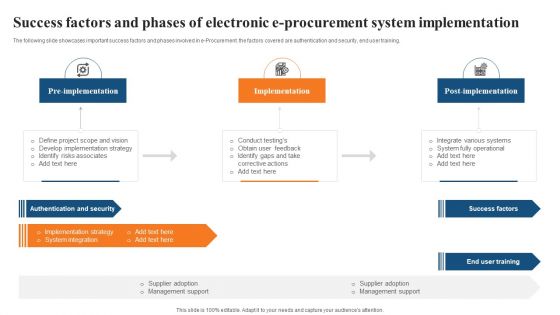
Success Factors And Phases Of Electronic E Procurement System Implementation Formats PDF
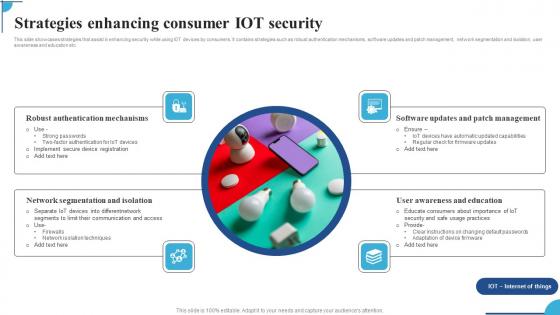
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.
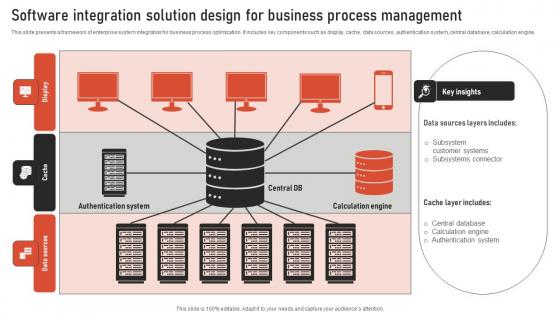
Software Integration Solution Design For Business Process Management Template Pdf
This slide presents a framework of enterprise system integration for business process optimization. It includes key components such as display, cache, data sources, authentication system, central database, calculation engine. Pitch your topic with ease and precision using this Software Integration Solution Design For Business Process Management Template Pdf. This layout presents information on Data Sources Layers, Authentication System, Calculation Engine. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents a framework of enterprise system integration for business process optimization. It includes key components such as display, cache, data sources, authentication system, central database, calculation engine.
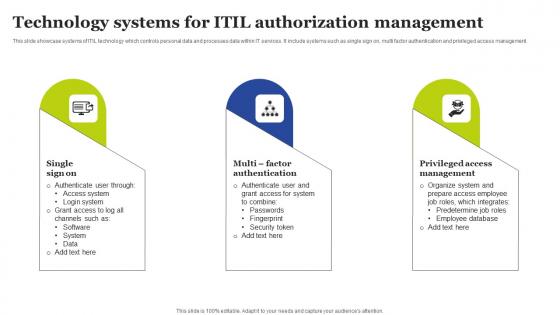
Technology Systems For ITIL Authorization Management Rules Pdf
This slide showcase systems of ITIL technology which controls personal data and processes data within IT services. It include systems such as single sign on, multi factor authentication and privileged access management. Pitch your topic with ease and precision using this Technology Systems For ITIL Authorization Management Rules Pdf This layout presents information on Single Sign, Multi Factor Authentication, Privileged Access Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase systems of ITIL technology which controls personal data and processes data within IT services. It include systems such as single sign on, multi factor authentication and privileged access management.

Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Phase 3 Respond To Cloud Protection Issues Ideas PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. This is a Phase 3 Respond To Cloud Protection Issues Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information, Cloud Service, Advanced Authentication Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
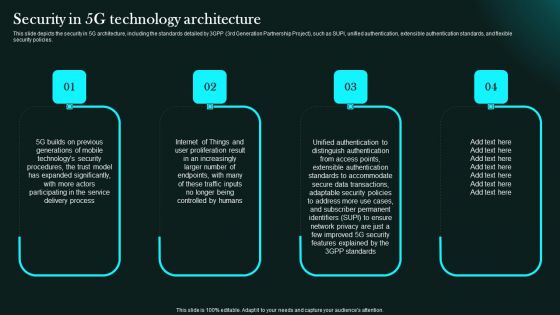
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
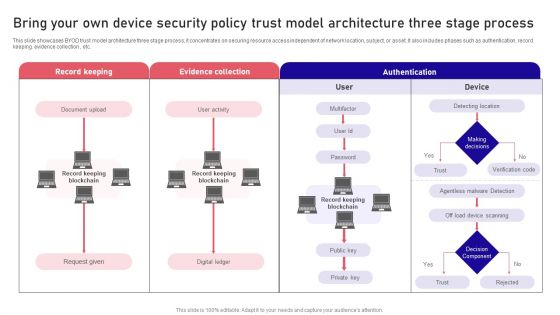
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
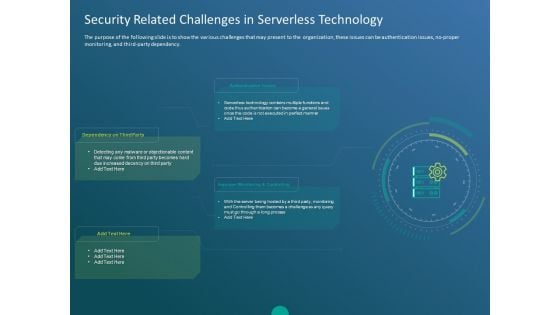
Functioning Of Serverless Computing Security Related Challenges In Serverless Technology Graphics PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. This is a functioning of serverless computing security related challenges in serverless technology graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication issues, dependency third party, improper monitoring and controlling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
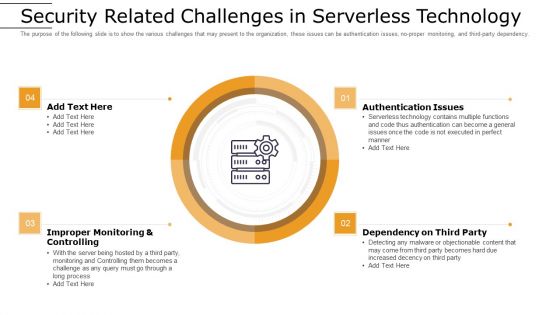
Cloud Computing Technology Implementation Plan Security Related Challenges In Serverless Technology Ideas PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. Presenting cloud computing technology implementation plan security related challenges in serverless technology ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like improper monitoring and controlling, authentication issues, dependency on third party. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
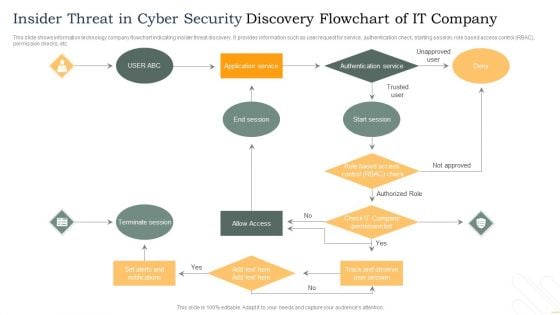
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
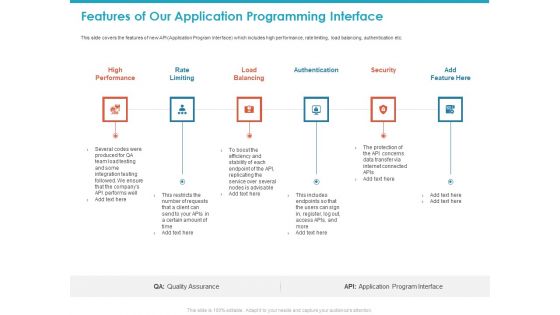
Features Of Our Application Programming Interface Ppt Layouts Layout Ideas PDF
This slide covers the features of new API Application Program Interface which includes high performance, rate limiting, load balancing, authentication etc. This is a features of our application programming interface ppt layouts layout ideas pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high performance, rate limiting, load balancing, authentication, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5G Identifiers, 5G Authentication . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
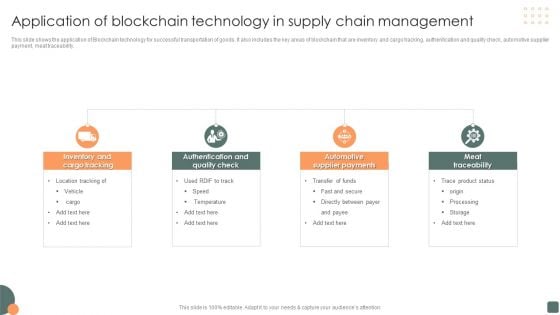
Application Of Blockchain Technology In Supply Chain Management Introduction PDF
This slide shows the application of Blockchain technology for successful transportation of goods. It also includes the key areas of blockchain that are inventory and cargo tracking, authentication and quality check, automotive supplier payment, meat traceability. Persuade your audience using this Application Of Blockchain Technology In Supply Chain Management Introduction PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Inventory And Cargo Tracking, Authentication And Quality Check, Automotive Supplier Payments. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
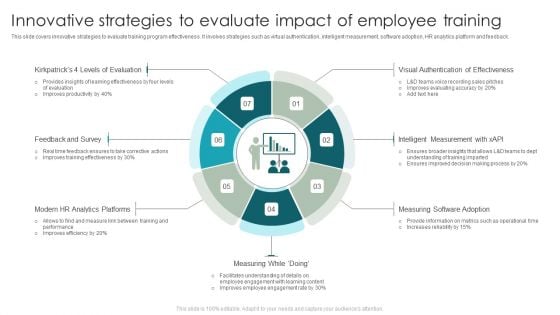
Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. Persuade your audience using this Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF. This PPT design covers Seven stages, thus making it a great tool to use. It also caters to a variety of topics including Feedback And Survey, Measuring Software Adoption, Visual Authentication Of Effectiveness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Ways To Decrease Digital Email Bounce Professional PDF
This slide shows various ways which can be used to reduce email bounce rate of the company. It covers points such as maintain email list hygiene, domain authentication and monitor email analytics. Presenting Three Ways To Decrease Digital Email Bounce Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Domain Authentication, Monitor Email Analytics, Maintain Email List Hygiene. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain In Financial Sector For Security Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled blockchain in financial sector for security ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are security, digital transactions, authentication of users. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
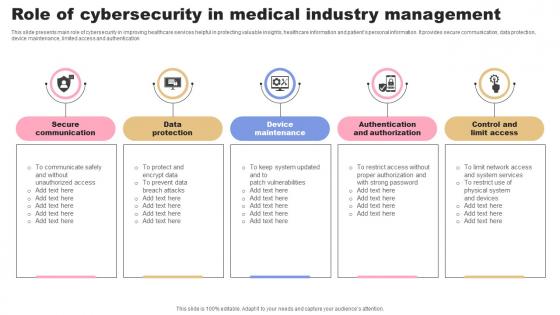
Role Of Cybersecurity In Medical Industry Management Rules Pdf
This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication Pitch your topic with ease and precision using this Role Of Cybersecurity In Medical Industry Management Rules Pdf. This layout presents information on Secure Communication, Data Protection, Maintenance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication
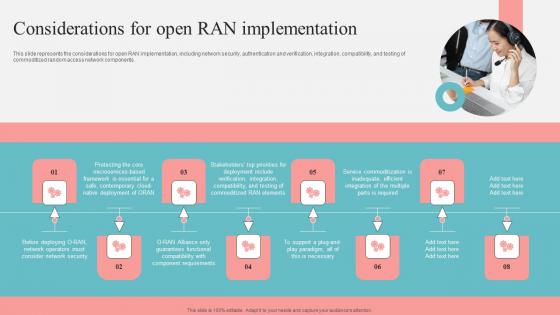
Considerations For Open Ran Implementation Unlocking The Potential Of Open Ran Brochure Pdf
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Considerations For Open Ran Implementation Unlocking The Potential Of Open Ran Brochure Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components.

Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Create an editable Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Considerations For Open Ran Implementation Revolutionizing Mobile Networks Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components.
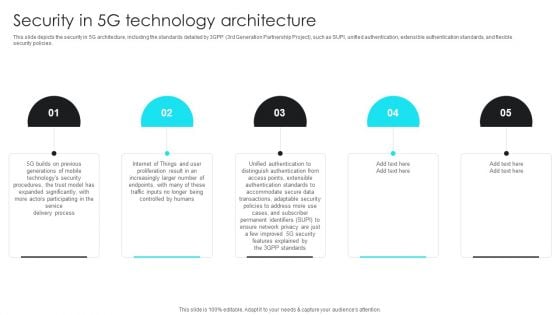
5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

5G Network Applications And Features Security In 5G Technology Architecture Download PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Find highly impressive 5G Network Applications And Features Security In 5G Technology Architecture Download PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download 5G Network Applications And Features Security In 5G Technology Architecture Download PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
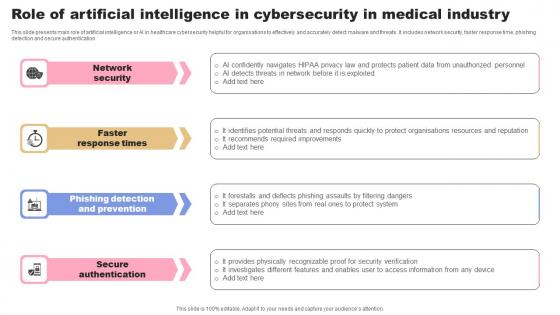
Role Of Artificial Intelligence In Cybersecurity In Medical Industry Background Pdf
This slide presents main role of artificial intelligence or AI in healthcare cybersecurity helpful for organisations to effectively and accurately detect malware and threats. It includes network security, faster response time, phishing detection and secure authentication Showcasing this set of slides titled Role Of Artificial Intelligence In Cybersecurity In Medical Industry Background Pdf. The topics addressed in these templates are Network Security, Response Times, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents main role of artificial intelligence or AI in healthcare cybersecurity helpful for organisations to effectively and accurately detect malware and threats. It includes network security, faster response time, phishing detection and secure authentication
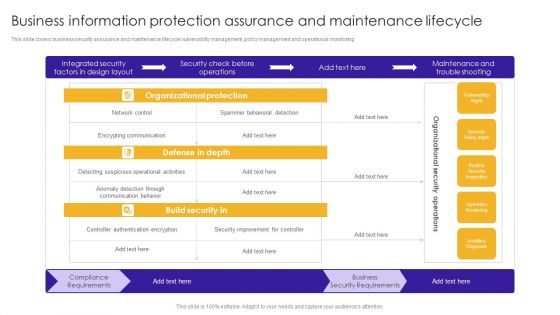
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
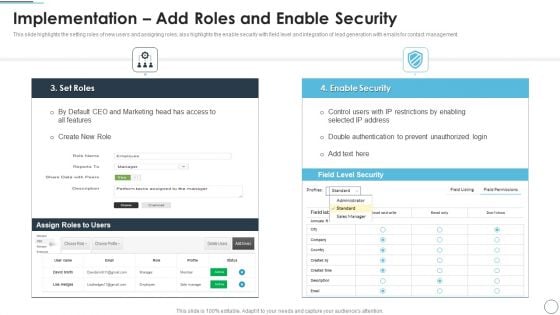
CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
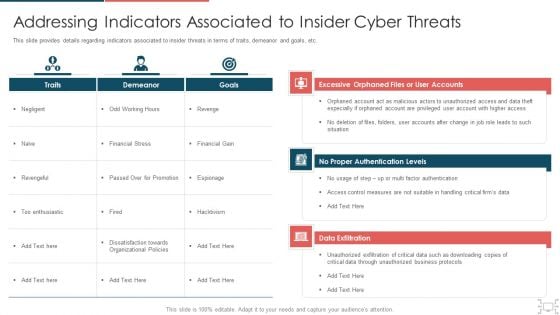
Cyber Security Administration In Organization Addressing Indicators Associated To Insider Cyber Threats Themes PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing indicators associated to insider cyber threats themes pdf. Use them to share invaluable insights on unauthorized, privileged, measures, authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Intelligent Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Template PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver and pitch your topic in the best possible manner with this Intelligent Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Template PDF. Use them to share invaluable insights on Application Delivery, IT Operations, Authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
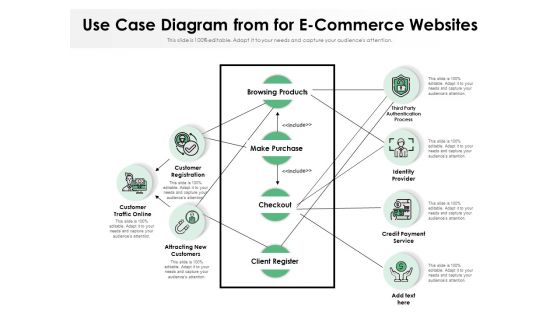
Business Case Flow Chart For Online Purchasing Process Ppt PowerPoint Presentation Infographics Display PDF
Presenting business case flow chart for online purchasing process ppt powerpoint presentation infographics display pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including customer traffic online, customer registration, attracting new customers, browsing products, make purchase, checkout, client register, credit payment service, identity provider, third party authentication process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
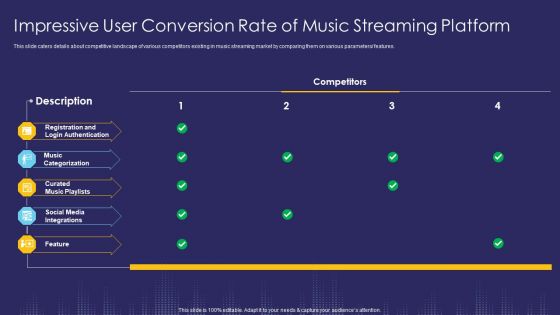
Impressive User Conversion Rate Of Music Streaming Platform Feature Ppt Model Slide Download PDF
This slide caters details about competitive landscape of various competitors existing in music streaming market by comparing them on various parameters or features. Deliver an awe inspiring pitch with this creative impressive user conversion rate of music streaming platform feature ppt model slide download pdf bundle. Topics like social media, authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
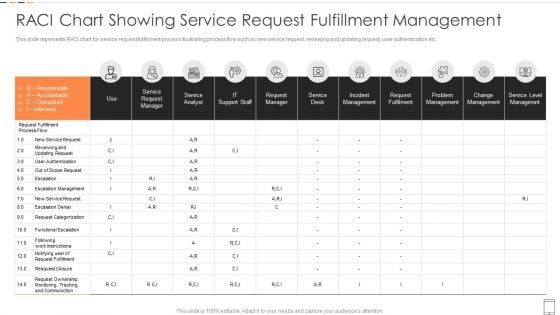
RACI Chart Showing Service Request Fulfillment Management Introduction PDF
This slide represents RACI chart for service request fulfillment process illustrating process flow such as new service request, reviewing and updating request, user authentication etc.Pitch your topic with ease and precision using this RACI Chart Showing Service Request Fulfillment Management Introduction PDF This layout presents information on Incident Management, Request Fulfilment, Problem Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
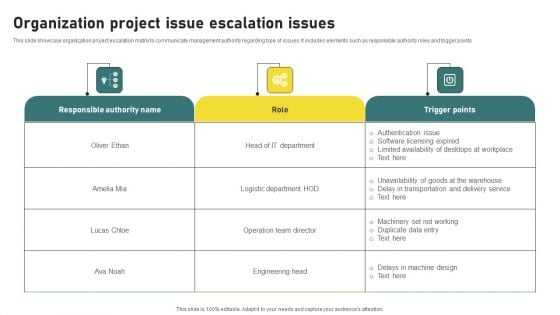
Organization Project Issue Escalation Issues Slides PDF
This slide showcase organization project escalation matrix to communicate management authority regarding type of issues. It includes elements such as responsible authority roles and trigger points. Pitch your topic with ease and precision using this Organization Project Issue Escalation Issues Slides PDF. This layout presents information on Operation Team Director, Authentication Issue. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
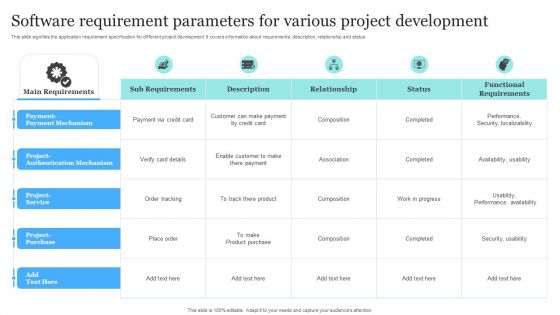
Software Requirement Parameters For Various Project Development Introduction PDF
This slide signifies the application requirement specification for different project development. It covers information about requirements, description, relationship and status. Pitch your topic with ease and precision using this Software Requirement Parameters For Various Project Development Introduction PDF. This layout presents information on Payment Payment Mechanism, Project Authentication Mechanism, Project Service, Project Purchase. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home