Computer Virus
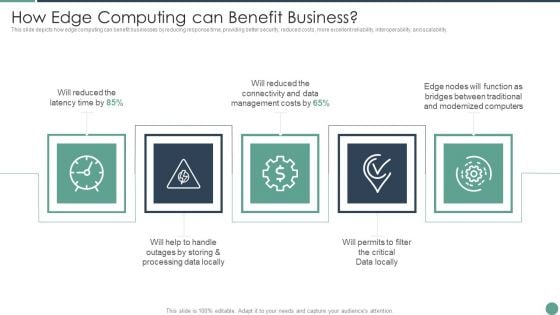
Distributed Computing How Edge Computing Can Benefit Business Elements PDF
This slide depicts how edge computing can benefit businesses by reducing response time, providing better security, reduced costs, more excellent reliability, interoperability, and scalability.This is a Distributed Computing How Edge Computing Can Benefit Business Elements PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Costs, Processing Locally, Data Locally You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Confidential Computing System Technology Benefits Of Confidential Computing Topics PDF
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Want to ace your presentation in front of a live audience Our Confidential Computing System Technology Benefits Of Confidential Computing Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
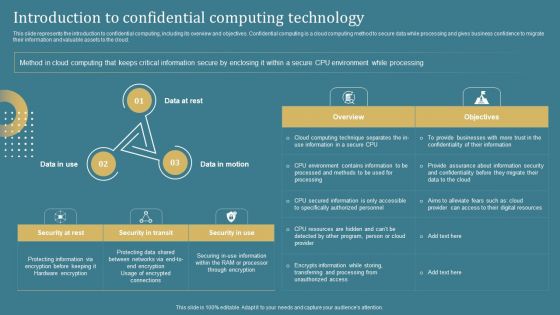
Confidential Computing System Technology Introduction To Confidential Computing Microsoft PDF
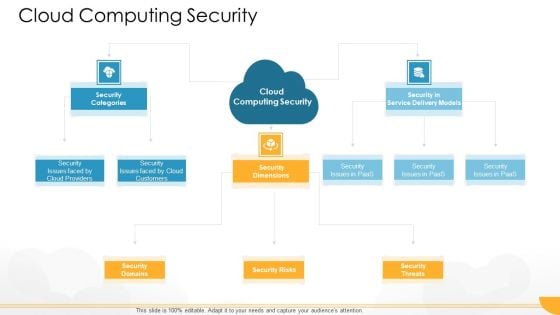
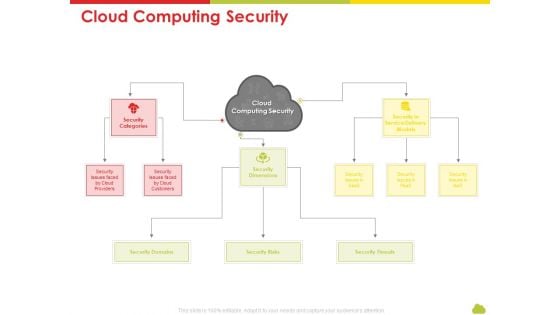
Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
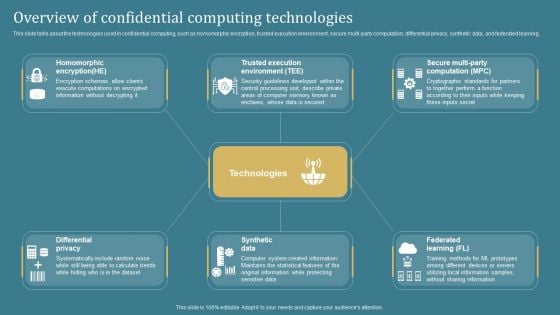
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
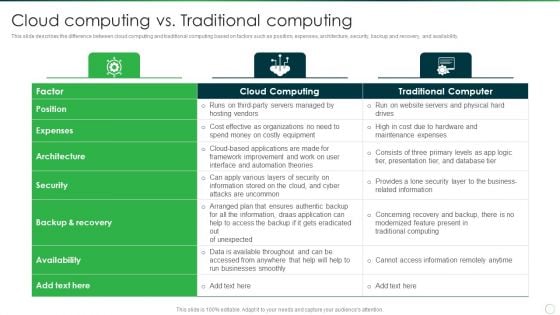
Google Cloud Computing System Cloud Computing Vs Traditional Computing Mockup PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability. Deliver and pitch your topic in the best possible manner with this Google Cloud Computing System Cloud Computing Vs Traditional Computing Mockup PDF. Use them to share invaluable insights on Cloud Computing, Traditional Computer, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
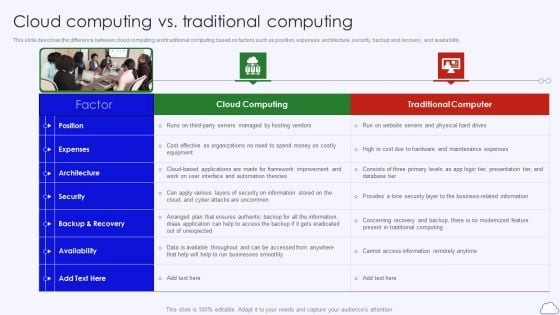
Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability.This is a Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Traditional Computer, Architecture, Availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
This slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Pitch your topic with ease and precision using this Pre And Post Process Results Of Cyber Security Process Changes Sample PDF. This layout presents information on Process Results, Process Changes, Key Insights. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Impact And Solutions For Major Challenges In Network Safety Ppt PowerPoint Presentation Icon Structure PDF
Persuade your audience using this impact and solutions for major challenges in network safety ppt powerpoint presentation icon structure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including major impacts, key solutions, issue, computer viruses. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.
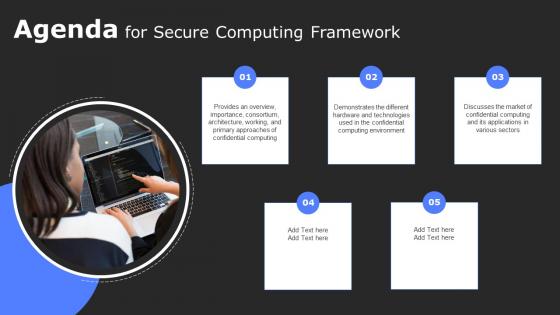
Agenda For Secure Computing Framework Portrait Pdf
Create an editable Agenda For Secure Computing Framework Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Secure Computing Framework Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Secure Computing Framework Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
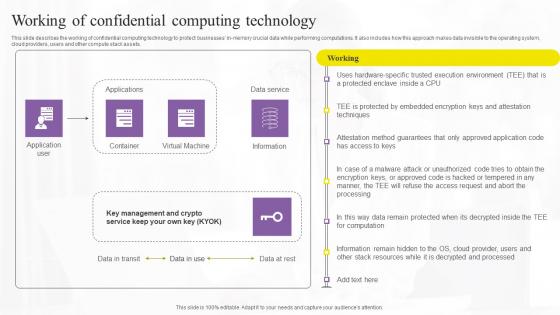
Working Of Confidential Computing Technology Demonstration Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Boost your pitch with our creative Working Of Confidential Computing Technology Demonstration Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
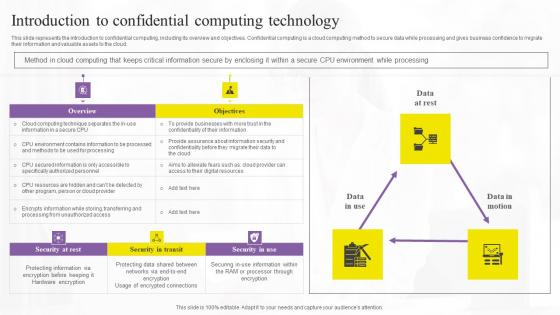
Introduction To Confidential Computing Technology Structure Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Structure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
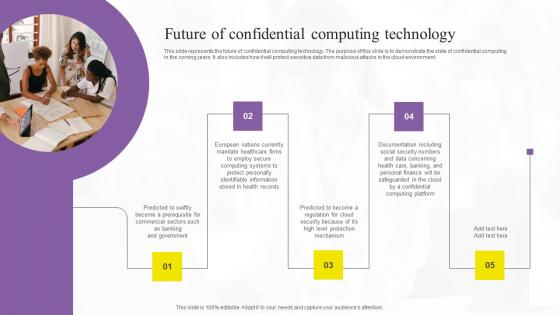
Future Of Confidential Computing Technology Download Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Take your projects to the next level with our ultimate collection of Future Of Confidential Computing Technology Download Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
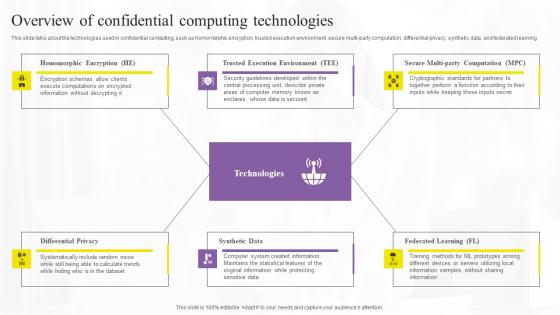
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
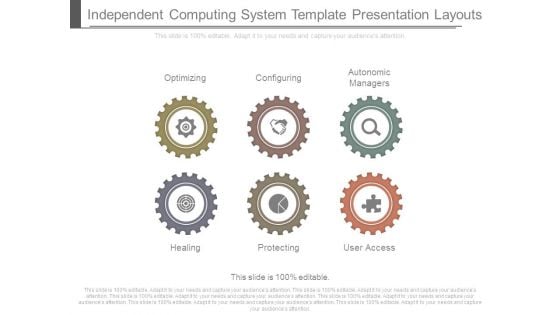
Independent Computing System Template Presentation Layouts
This is a independent computing system template presentation layouts. This is a six stage process. The stages in this process are optimizing, healing, configuring, protecting, autonomic managers, user access.
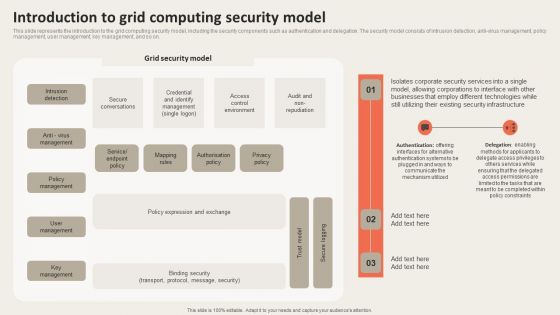
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
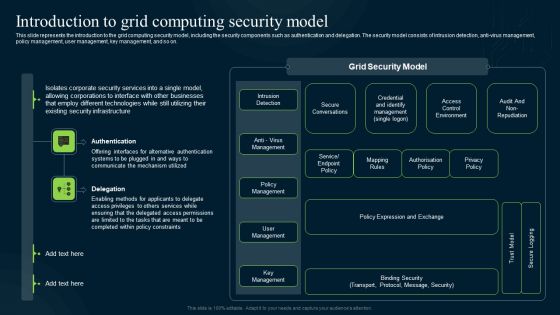
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
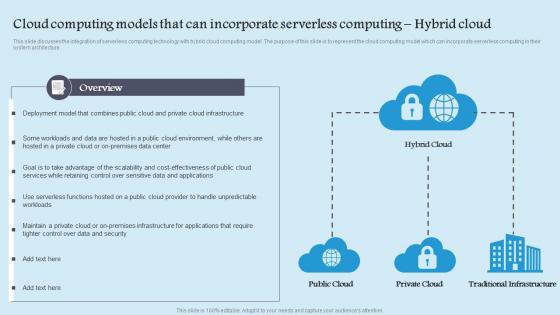
Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf
This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture. This Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture.
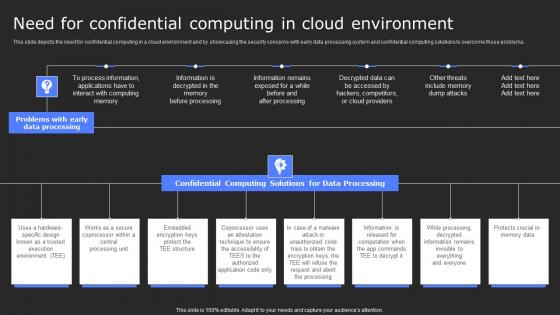
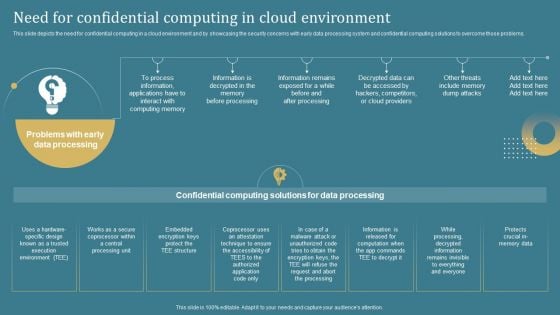
Need For Confidential Computing In Cloud Secure Computing Framework Brochure Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. There are so many reasons you need a Need For Confidential Computing In Cloud Secure Computing Framework Brochure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.
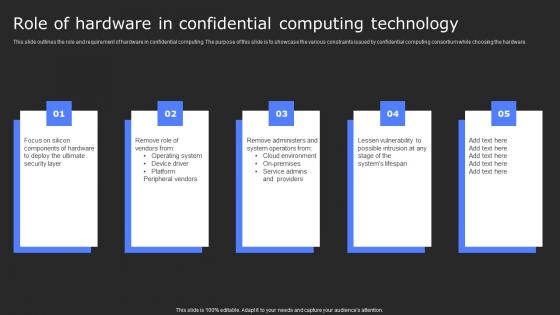
Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Find highly impressive Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.
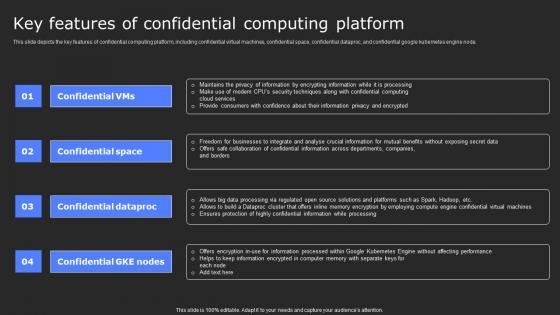
Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node. Create an editable Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node.
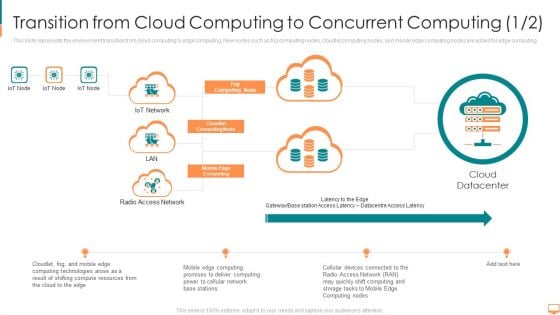
Transition From Cloud Computing To Concurrent Computing Base Ppt Ideas Aids PDF
This slide represents the environment transition from cloud computing to edge computing. New nodes such as fog computing nodes, cloudlet computing nodes, and mobile edge computing nodes are added for edge computing. Deliver an awe inspiring pitch with this creative transition from cloud computing to concurrent computing base ppt ideas aids pdf bundle. Topics like technologies, computing, resources, promises, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
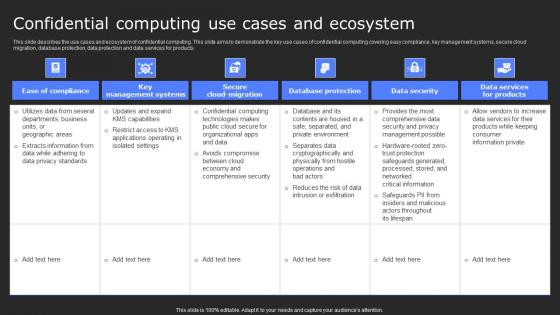
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
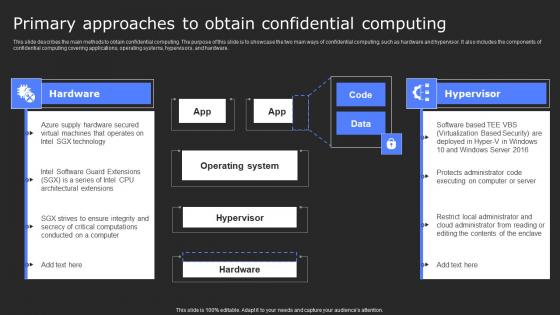
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
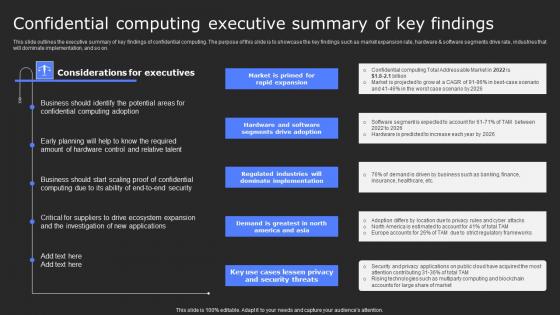
Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.
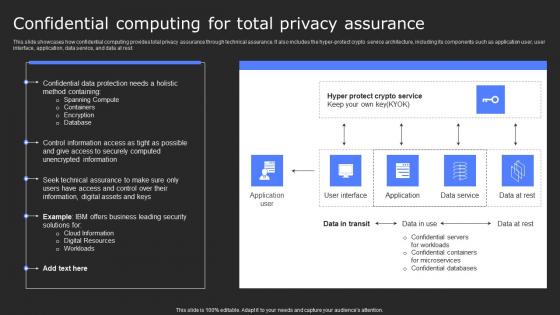
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
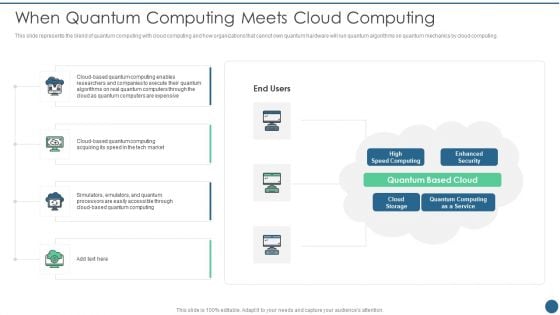
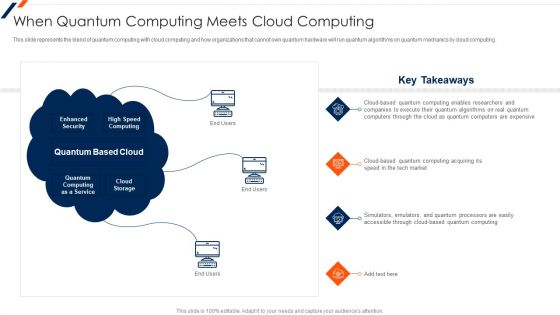
Quantum Key Distribution When Quantum Computing Meets Cloud Computing Summary PDF
This slide represents the blend of quantum computing with cloud computing and how organizations that cannot own quantum hardware will run quantum algorithms on quantum mechanics by cloud computing. Deliver and pitch your topic in the best possible manner with this Quantum Key Distribution When Quantum Computing Meets Cloud Computing Summary PDF Use them to share invaluable insights on Enhanced Security, Quantum Computing, Speed Computing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
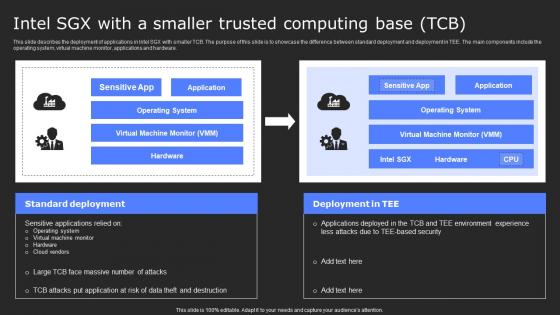
Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Find a pre-designed and impeccable Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
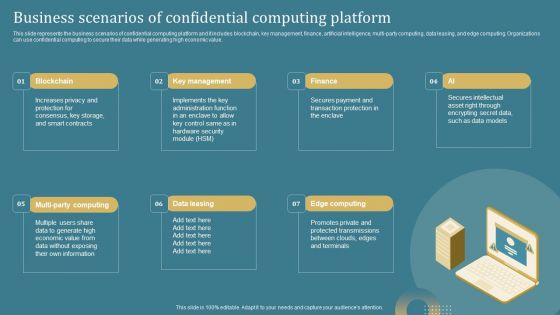
Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
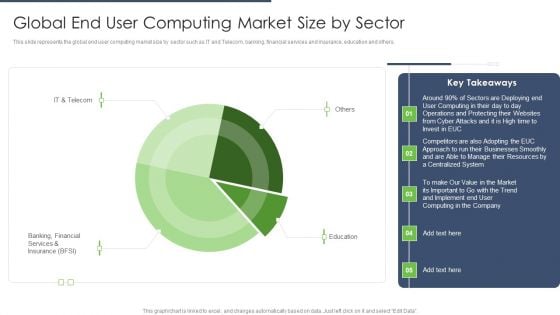
End User Computing Global End User Computing Market Size By Sector Designs PDF
This slide represents the global end user computing market size by sector such as IT and Telecom, banking, financial services and insurance, education and others.Deliver an awe inspiring pitch with this creative End User Computing Global End User Computing Market Size By Sector Designs PDF bundle. Topics like Operations Protecting, Businesses Smoothly, Computing Company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
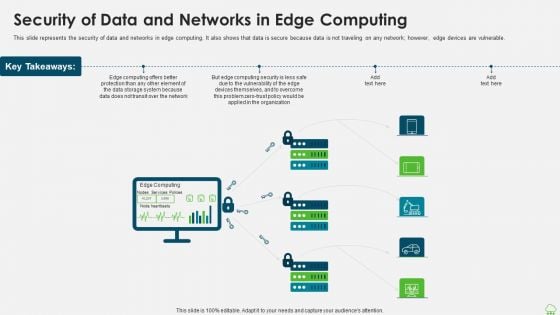
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
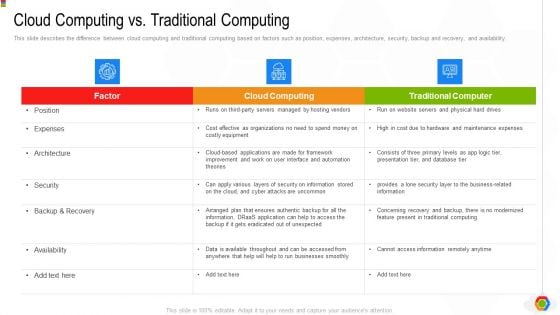
Google Cloud Console IT Cloud Computing Vs Traditional Computing Ppt File Ideas PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability. Deliver an awe inspiring pitch with this creative google cloud console it cloud computing vs traditional computing ppt file ideas pdf bundle. Topics like security, backup and recovery, architecture, expenses, position can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Service Models IT Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a cloud computing service models it cloud computing in manufacturing industry inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simulation, cyber security, cloud computing, system integration, autonomous robots. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Distributed Computing IT Challenges And Solutions Of Edge Computing Deployment Icons PDF
This slide represents the challenges and solutions of edge computing deployment in the organization, and it includes challenges such as scale, performance, control, and security. Deliver and pitch your topic in the best possible manner with this distributed computing it challenges and solutions of edge computing deployment icons pdf. Use them to share invaluable insights on performance, security, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Confidential Computing System Technology Working Of Confidential Computing Technology Icons PDF
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. This Confidential Computing System Technology Working Of Confidential Computing Technology Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Working Of Confidential Computing Technology Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
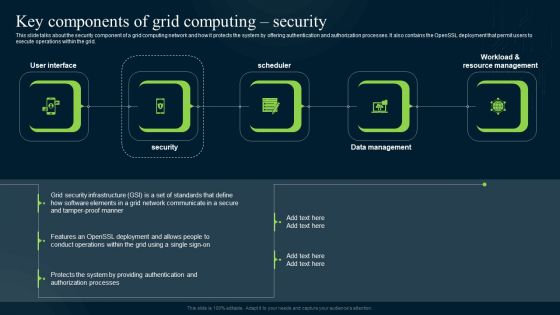
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
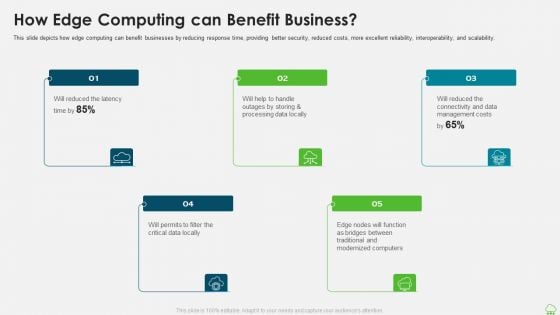
Distributed Computing IT How Edge Computing Can Benefit Business Template PDF
This slide depicts how edge computing can benefit businesses by reducing response time, providing better security, reduced costs, more excellent reliability, interoperability, and scalability. Presenting distributed computing it how edge computing can benefit business template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management costs, processing data, computers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
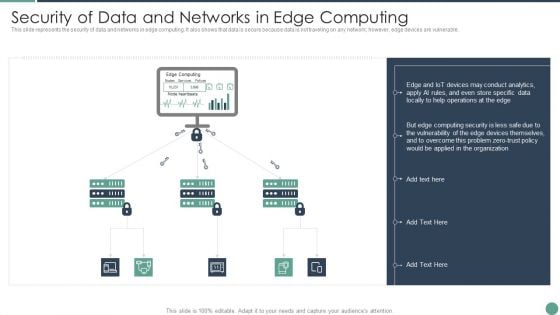
Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
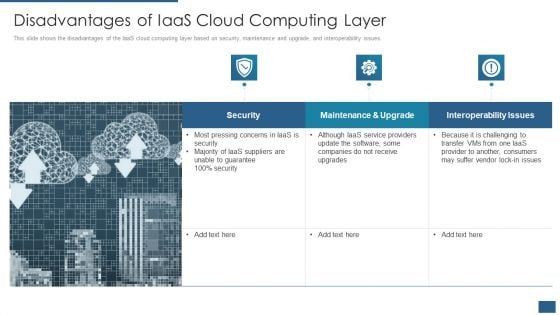
Cloud Computing Service Models IT Disadvantages Of Iaas Cloud Computing Layer Rules PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. Deliver an awe inspiring pitch with this creative cloud computing service models it disadvantages of iaas cloud computing layer rules pdf bundle. Topics like security, maintenance and upgrade, interoperability issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
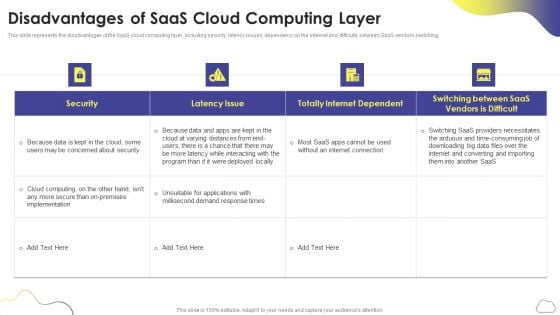
Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Deliver and pitch your topic in the best possible manner with this Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF. Use them to share invaluable insights on Security, Latency Issue, Totally Internet Dependent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Confidential Computing System Technology Need For Confidential Computing In Cloud Guidelines PDF

Quantum Computing For Everyone IT How Will Quantum Computing Help Enterprises Download PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it how will quantum computing help enterprises download pdf. Use them to share invaluable insights on development, optimization, accelerate autonomous, transform cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
When Quantum Computing Meets Cloud Computing Ppt Model Example File PDF
This is a When Quantum Computing Meets Cloud Computing Ppt Model Example File PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enhanced Security, High Speed Computing, Quantum Based Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing Challenges And Solutions Of Edge Computing Deployment Designs PDF
This slide represents the challenges and solutions of edge computing deployment in the organization, and it includes challenges such as scale, performance, control, and security.This is a Distributed Computing Challenges And Solutions Of Edge Computing Deployment Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Infrastructure Environment, Repository Performance, Monitoring Controlling You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
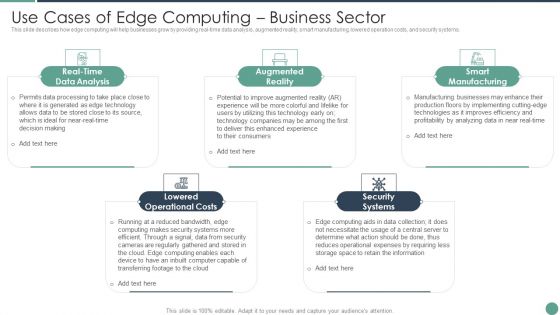
Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF
This slide describes how edge computing will help businesses grow by providing real-time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems.This is a Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Augmented Reality, Smart Manufacturing, Security Systems You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
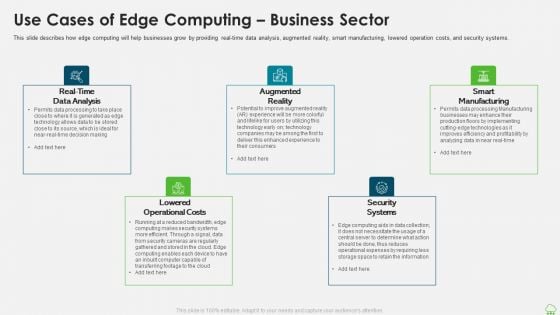
Distributed Computing IT Use Cases Of Edge Computing Business Sector Template PDF
This slide describes how edge computing will help businesses grow by providing real-time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems. This is a distributed computing it use cases of edge computing business sector template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data analysis, smart manufacturing, lowered operational costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
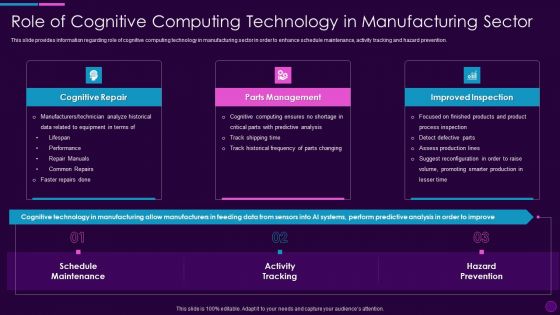
Role Of Cognitive Computing Technology In Cognitive Computing Action Plan Ppt File Aids PDF
This slide provides information regarding role of cognitive computing technology in manufacturing sector in order to enhance schedule maintenance, activity tracking and hazard prevention. Presenting role of cognitive computing technology in cognitive computing action plan ppt file aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cognitive repair, parts management, improved inspection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mesh Computing Infrastructure Adoption Process Data Governance Strategy For Cloud Computing Demonstration PDF
This slide displays a complete strategic plan for governing data structures of cloud computing. This covers data inventory and visibility, operational compliance, workload operations etc. This is a mesh computing infrastructure adoption process data governance strategy for cloud computing demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like workload operations, platform operations, protect and recover. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Security Rules PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing security rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risks, threats, domains, service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
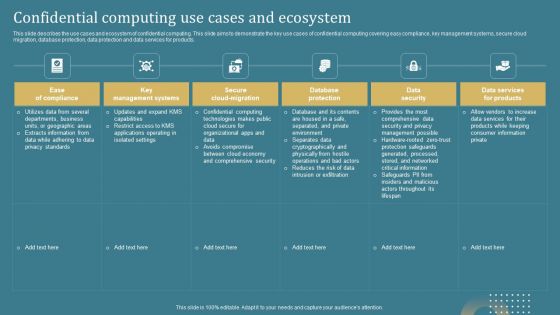
Confidential Computing System Technology Confidential Computing Use Cases And Ecosystem Demonstration PDF
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Retrieve professionally designed Confidential Computing System Technology Confidential Computing Use Cases And Ecosystem Demonstration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
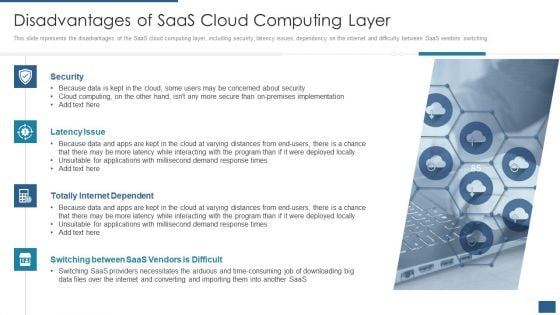
Cloud Computing Service Models IT Disadvantages Of Saas Cloud Computing Layer Elements PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Presenting cloud computing service models it disadvantages of saas cloud computing layer elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, latency issue, totally internet dependent, switching between saas vendors is difficult. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
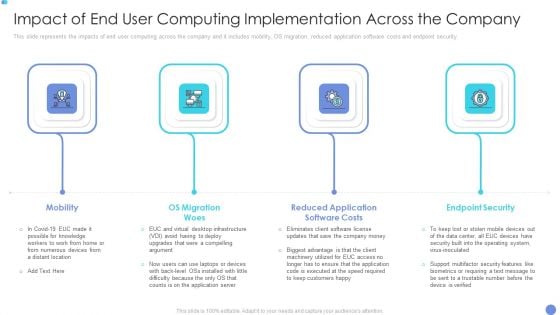
Customer Mesh Computing IT Impact Of End User Computing Implementation Across The Company Pictures PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security. Presenting customer mesh computing it impact of end user computing implementation across the company pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mobility, os migration woes, endpoint security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Maintenance And Upgrade, Security, Interoperability Issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
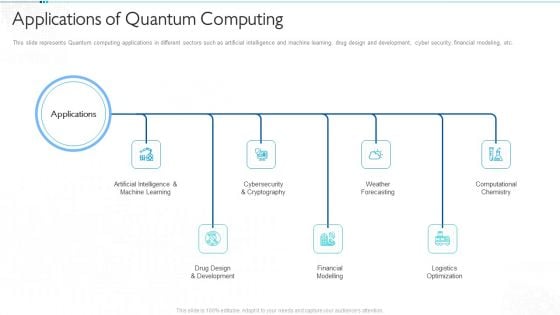
Quantum Computing For Everyone IT Applications Of Quantum Computing Infographics PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. Presenting quantum computing for everyone it applications of quantum computing infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like artificial intelligence and machine learning, drug design and development, financial modelling, weather forecasting, logistics optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
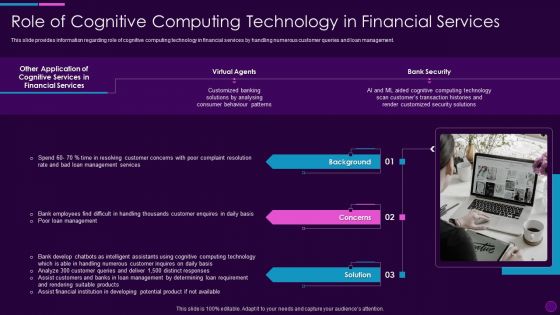
Cognitive Computing Action Plan Role Of Cognitive Computing Technology Ppt Infographics Layouts PDF
This slide provides information regarding role of cognitive computing technology in financial services by handling numerous customer queries and loan management. Presenting cognitive computing action plan role of cognitive computing technology ppt infographics layouts pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial services, virtual agents, bank security, background, concerns. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

End User Computing Application Of End User Computing In Insurance Background PDF
This slide represents the end user computing in insurance world and how it can help to generate inventory of all EUCs available in the insurance organizations.Presenting End User Computing Application Of End User Computing In Insurance Background PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Contain Actuarial, Accuracy Security, Unwelcomed Company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home