Computer Virus
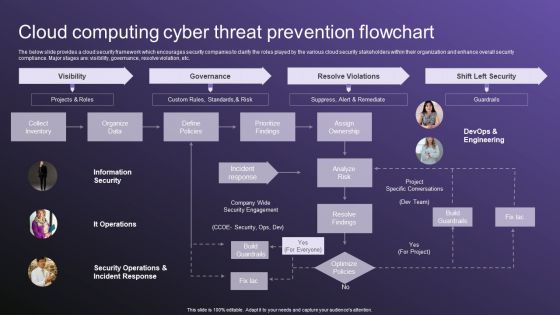
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
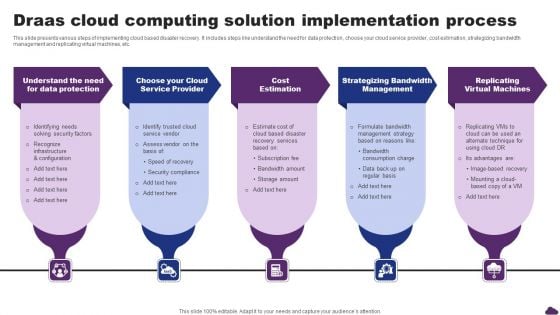
Draas Cloud Computing Solution Implementation Process Infographics PDF
This slide presents various steps of implementing cloud based disaster recovery. It includes steps like understand the need for data protection, choose your cloud service provider, cost estimation, strategizing bandwidth management and replicating virtual machines, etc. Presenting Draas Cloud Computing Solution Implementation Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Strategizing Bandwidth Management, Replicating Virtual Machines, Cost Estimation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Components Challenges For IT Professional Icons PDF
This slide focuses on challenges of cloud infrastructure which IT professionals are facing such as cloud security, lack of resources and expertise, information technology governance and cloud migration. Persuade your audience using this cloud computing components challenges for it professional icons pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cloud security, lack of expertise, cloud migration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Computing Testing Framework With Database Icons PDF
This template covers about framework of cloud testing with data base and service level agreement. Further, it cover about testing repository with security. Persuade your audience using this cloud computing testing framework with database icons pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including service, application, system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
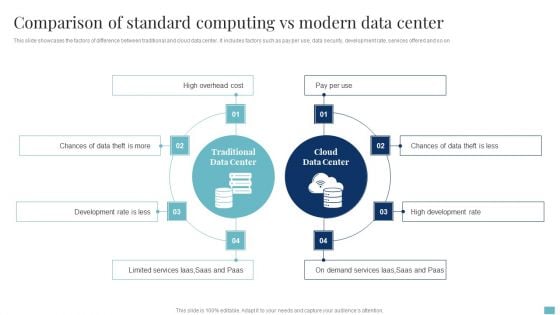
Comparison Of Standard Computing Vs Modern Data Center Mockup PDF
This slide showcases the factors of difference between traditional and cloud data center. It includes factors such as pay per use, data security, development rate, services offered and so on. Persuade your audience using this Comparison Of Standard Computing Vs Modern Data Center Mockup PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Development, High Overhead Cost, Cloud Data Center. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
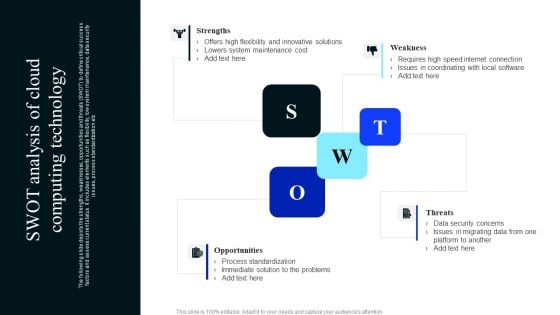
SWOT Analysis Of Cloud Computing Technology Download PDF
The following slide depicts the strengths, weaknesses, opportunities and threats SWOT to define critical success factors and assess current status. It includes elements such as flexibility, low system maintenance, data security issues, process standardization etc. Presenting SWOT Analysis Of Cloud Computing Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths, Weakness, Threats, Opportunities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
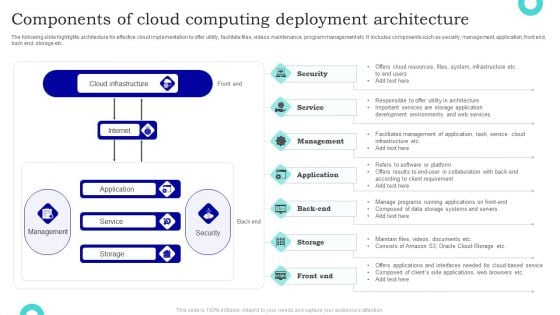
Components Of Cloud Computing Deployment Architecture Sample PDF
The following slide highlights architecture for effective cloud implementation to offer utility, facilitate files, videos maintenance, program management etc. It includes components such as security, management, application, front end, back end, storage etc. Pitch your topic with ease and precision using this Components Of Cloud Computing Deployment Architecture Sample PDF. This layout presents information on Cloud Infrastructure, Application, Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Computing Security Networking Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cloud computing security networking ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
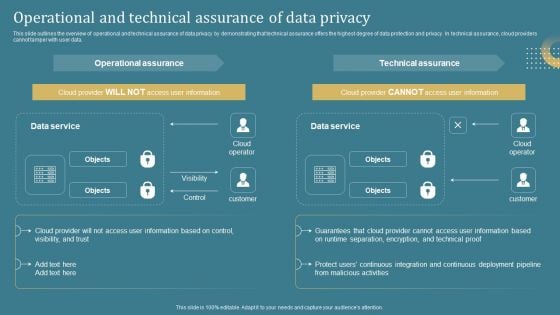
Confidential Computing System Technology Operational And Technical Assurance Mockup PDF
Cloud Computing Wifi Safety Upload Social Network Ppt Slides Graphics
This power point icon template has been designed with graphic of cloud computing, wifi and social network. These icons can be used for data upload safety features and social networking. Use these icons for social network and technology related presentations.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Data Diagrams PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
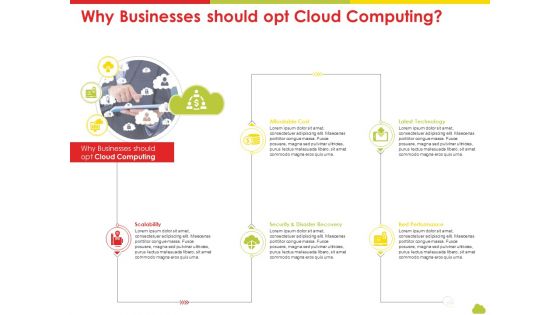
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Why Businesses Should Opt Cloud Computing Sample PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan why businesses should opt cloud computing sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like scalability, affordable cost, latest technology, best performance, security and disaster recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
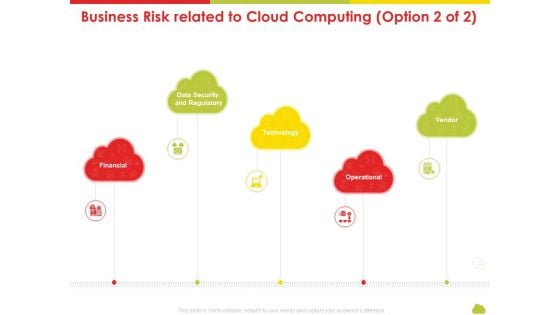
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Vendor Designs PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing vendor designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf
This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc. Want to ace your presentation in front of a live audience Our Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc.
1 Public Private Or Hybrid Cloud Computing Benefits Shown By Cloud Icons Surrounded Ppt Slides
This image slide displays public or private cloud or hybrid cloud computing benefits. This image slide has been designed with graphic of big cloud surrounded by small clouds. This image slide depicts cloud computing. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on networking and technology in your presentations. This image may be used to explain various concepts of cloud computing in your presentations. This image slide will impart professional appearance to your presentations.
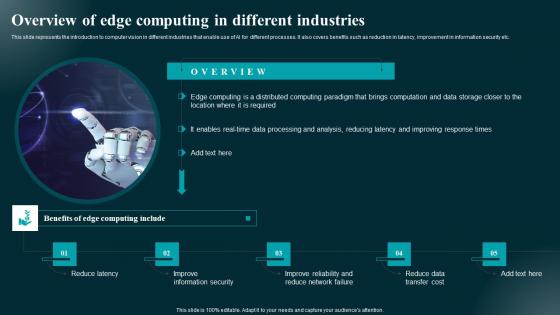
Overview Of Edge Computing In Different Industries Applications And Impact Themes Pdf
This slide represents the introduction to computer vision in different industries that enable use of AI for different processes. It also covers benefits such as reduction in latency, improvement in information security etc. Find a pre-designed and impeccable Overview Of Edge Computing In Different Industries Applications And Impact Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the introduction to computer vision in different industries that enable use of AI for different processes. It also covers benefits such as reduction in latency, improvement in information security etc.
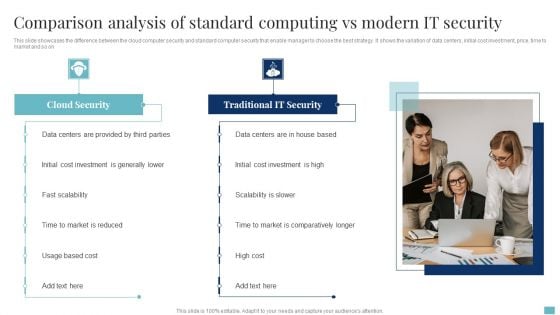
Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF
This slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on. Persuade your audience using this Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Data Centers, Cloud Security, Cost Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
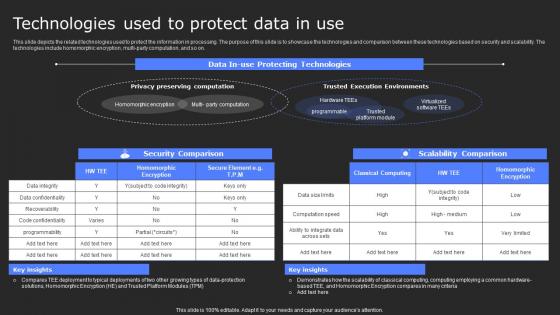
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

1 Computers Behind A Firewall Connected To A Centralized Server Ppt Slides
This image slide displays computer behind a firewall connected to a centralized server. This image slide has been crafted with graphic of laptops, server and firewall icon connected. This image slide depicts security in networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts technology, networking and security. This image slide will enhance the quality of your presentations.
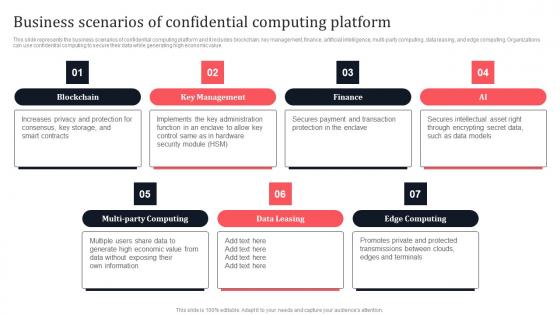
Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Boost your pitch with our creative Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
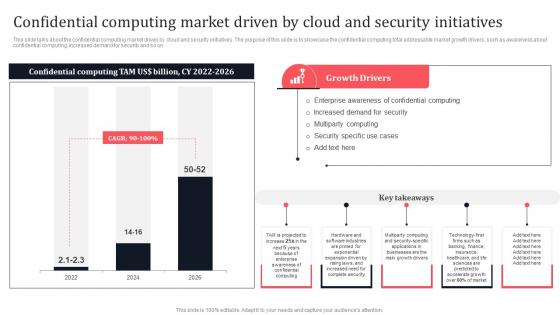
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
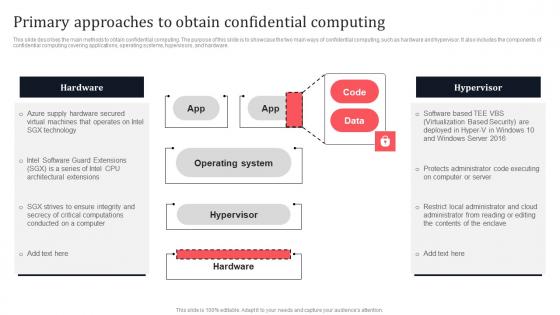
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
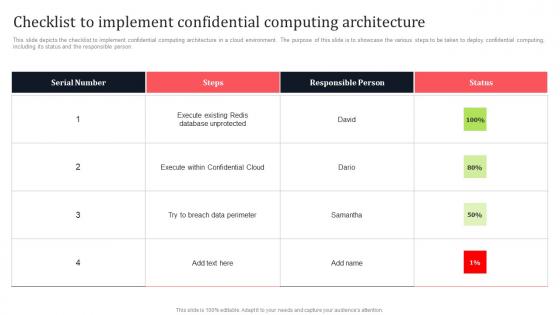
Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person.
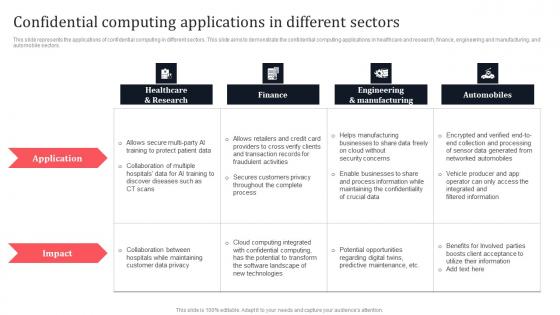
Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present like a pro with Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.
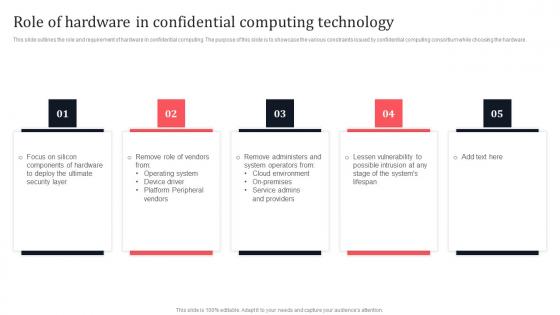
Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf today and make your presentation stand out from the rest. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Create an editable Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
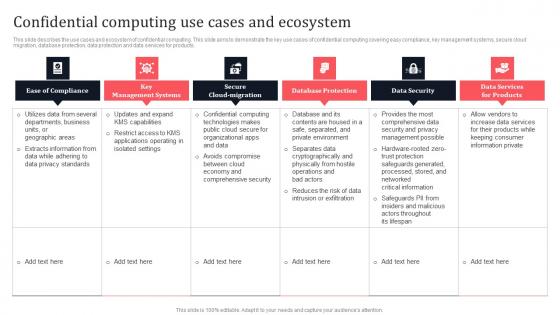
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
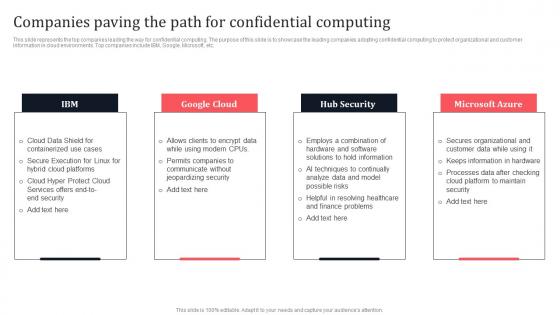
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf
Pitch your topic with ease and precision using this Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf. This layout presents information on Cloud Computing Service, Level Agreement Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf
Pitch your topic with ease and precision using this Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf. This layout presents information on Showcasing Cloud Computing, Service Level Agreement, Model Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
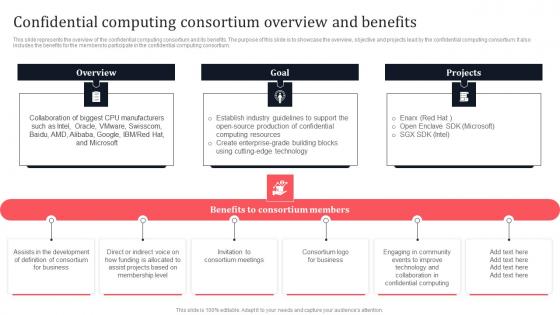
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
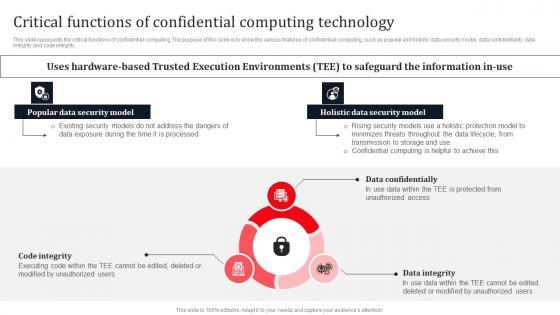
Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.

Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf today and make your presentation stand out from the rest. This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
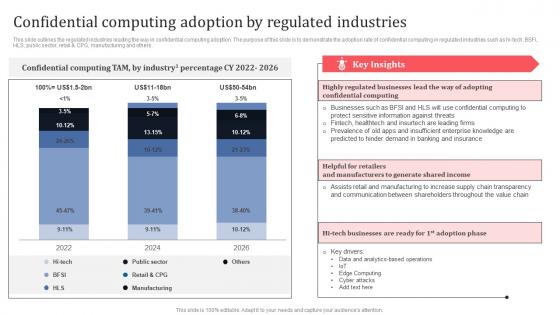
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
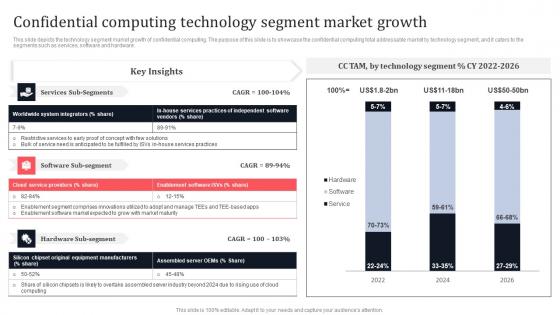
Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. This Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
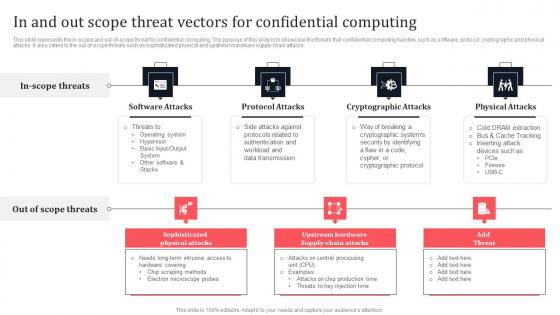
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
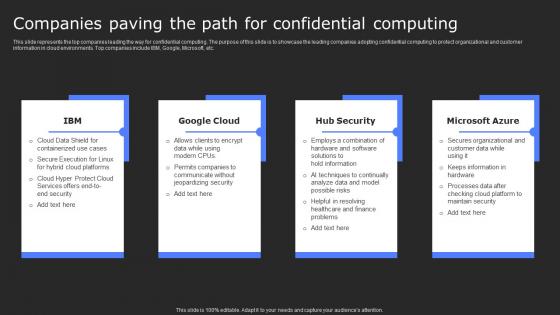
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
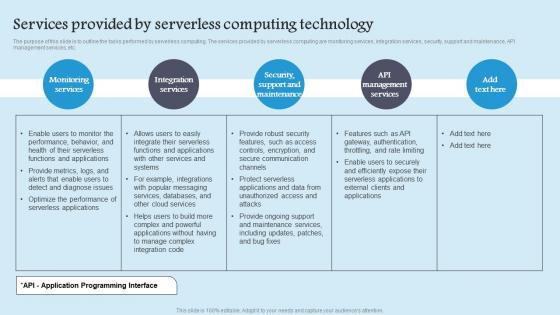
Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf
The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc. Do you know about Slidesgeeks Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc.
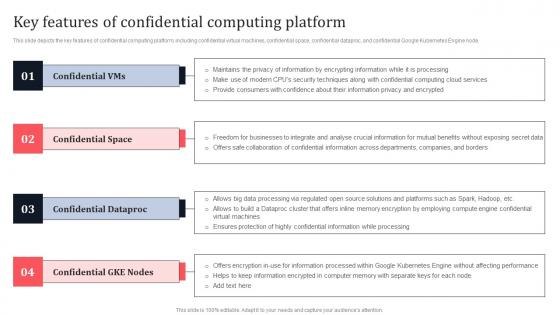
Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Find a pre-designed and impeccable Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node.
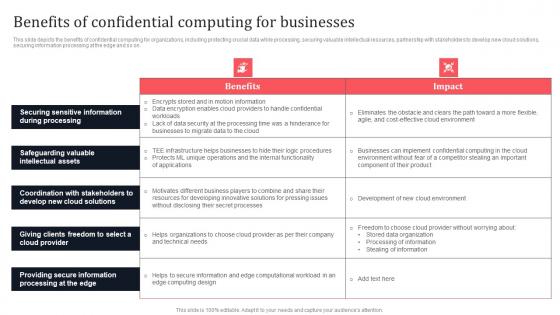
Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Do you know about Slidesgeeks Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
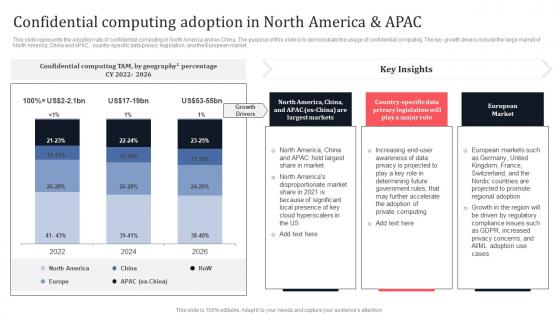
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
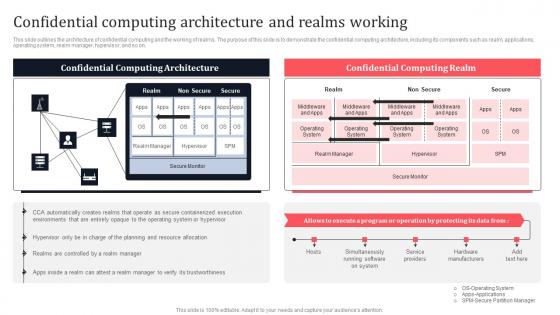
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
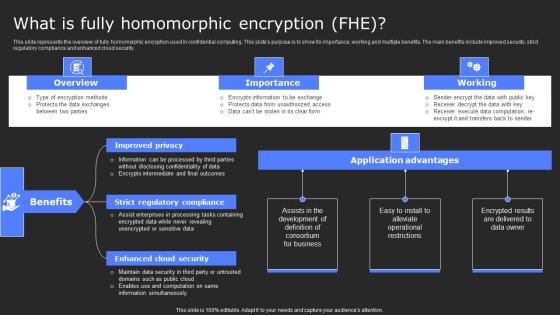
What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.

For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf
Are you searching for a For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf from Slidegeeks today. Our For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf
Find highly impressive Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. Our Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
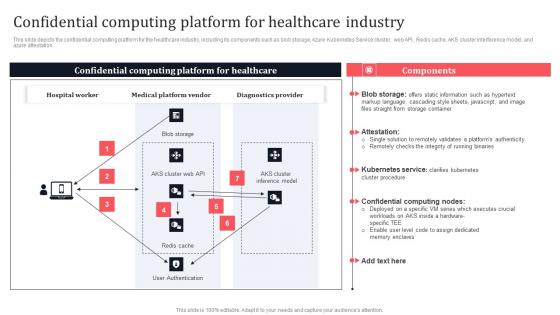
Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. This modern and well-arranged Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.

Secure Multi Party Computation SMPC Ppt Powerpoint Presentation Complete Deck With Slides
This Secure Multi Party Computation SMPC Ppt Powerpoint Presentation Complete Deck With Slides is meant for audiences who need a new vision and mission to bring energy back to their enterprise. The eighty three-slides in the complete deck complement the spirit of risk-taking and investment that the adventure of business requires. There is also scope for ample customization, which is a hallmark of a good presentation. Improvise on the presentations or even while you make your point before you esteemed audience. There is no better way to win new clients in business than a passionate presentation we have the raw material, what is stopping you from giving your best Download now and showcase your business potential to the world. Our Secure Multi Party Computation SMPC Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
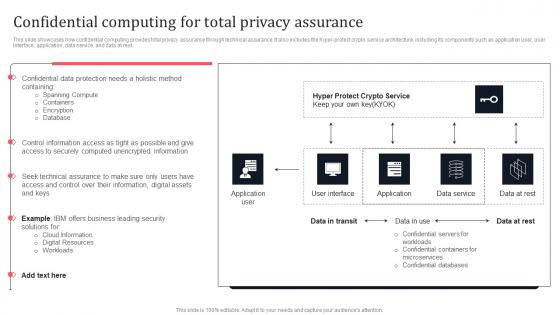
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Budget For Implementing Confidential Computing Architecture Secure Multi Party Brochure Pdf
This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Find a pre-designed and impeccable Budget For Implementing Confidential Computing Architecture Secure Multi Party Brochure Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance.
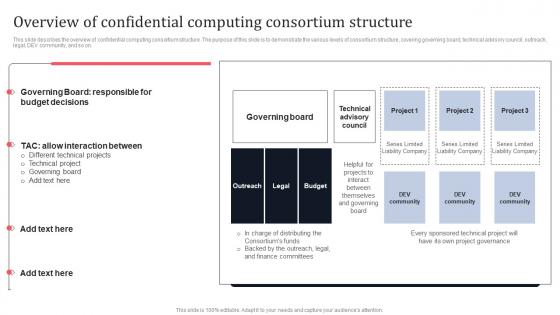
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
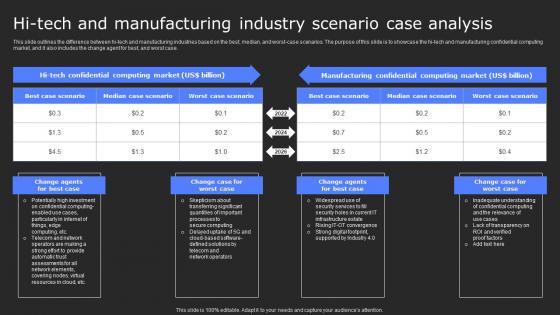
Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
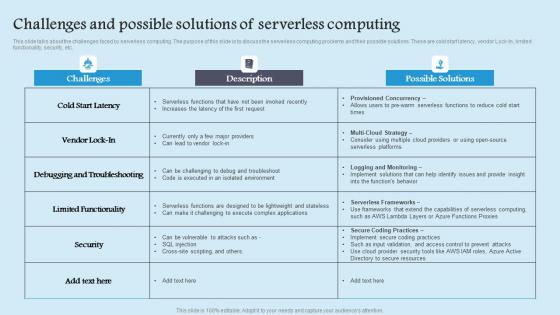
Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf
This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
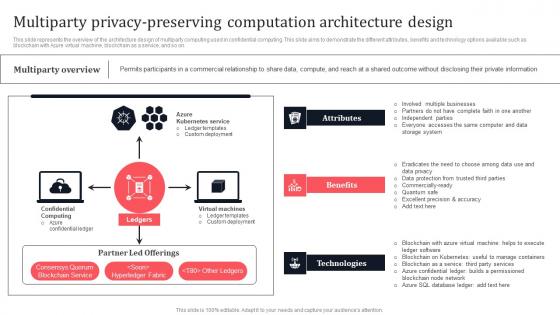
Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Create an editable Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
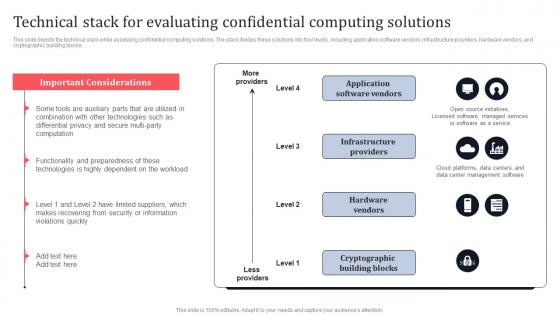
Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
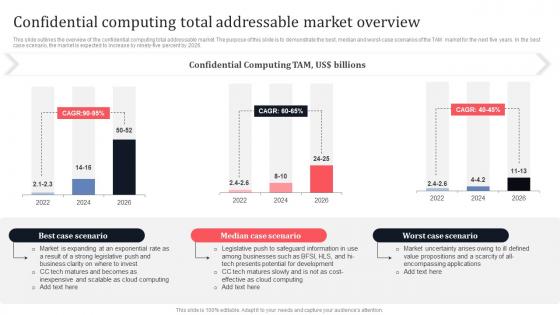
Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Welcome to our selection of the Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.

 Home
Home