Cyber Security Ppt

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
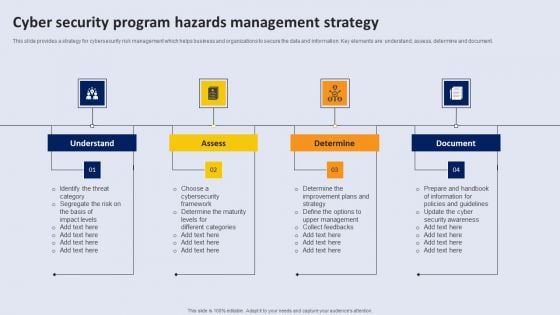
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
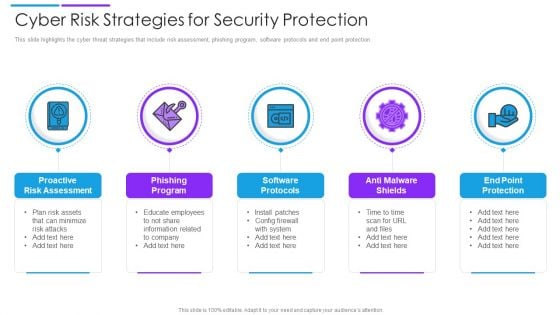
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
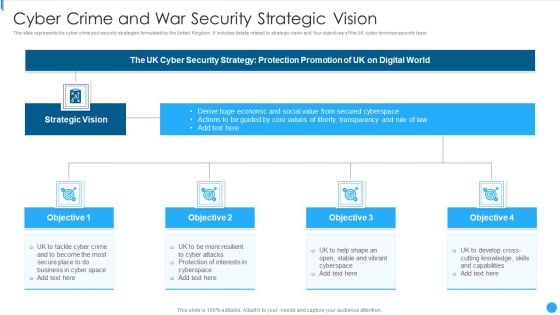
Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
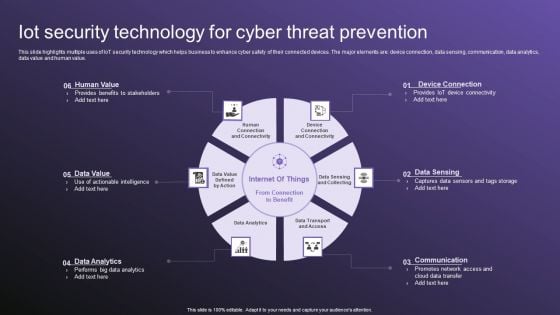
Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
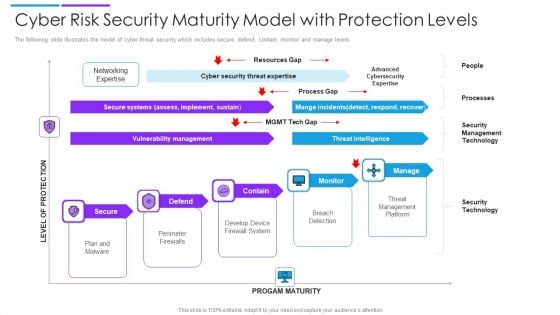
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
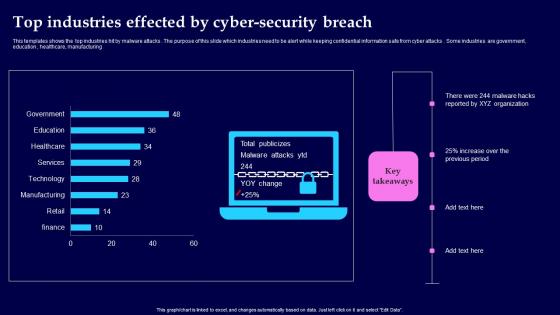
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security.
Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Incident Management Checklist Before An Incident Icons PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cyber Security Incident Management Checklist Before An Incident Icons PDF from Slidegeeks and deliver a wonderful presentation.
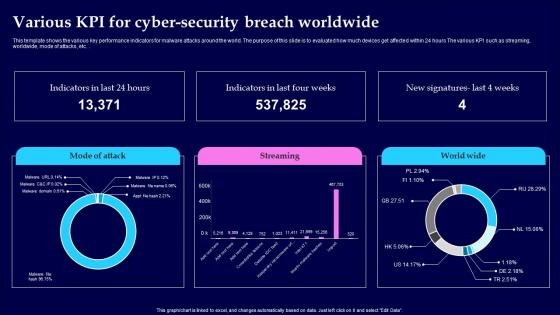
Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc.
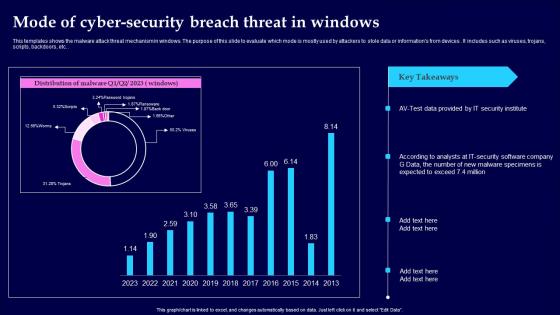
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
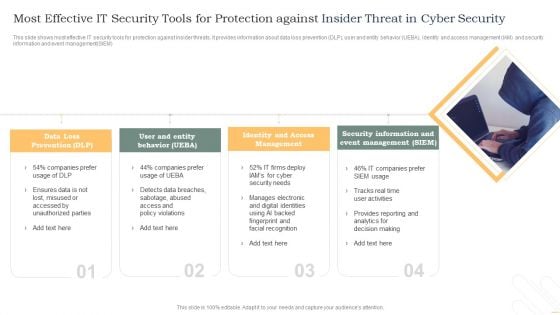
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
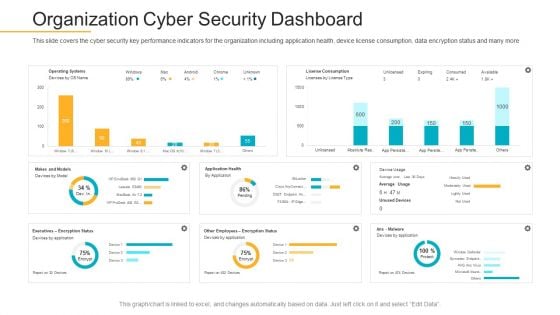
Data Breach Prevention Recognition Organization Cyber Security Dashboard Demonstration PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
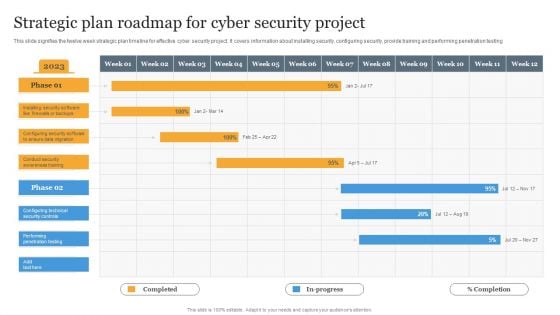
Strategic Plan Roadmap For Cyber Security Project Information PDF
This slide signifies the twelve week strategic plan timeline for effective cyber security project. It covers information about installing security, configuring security, provide training and performing penetration testing Pitch your topic with ease and precision using this Strategic Plan Roadmap For Cyber Security Project Information PDF. This layout presents information on Strategic, Plan, Project. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
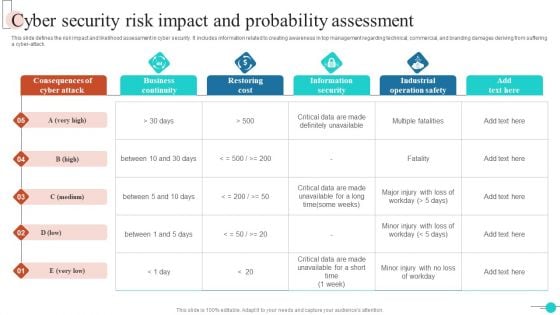
Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
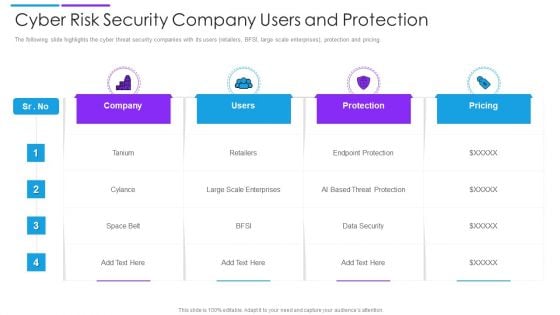
Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
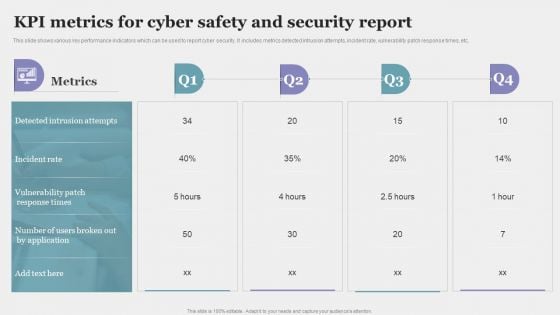
KPI Metrics For Cyber Safety And Security Report Elements PDF
This slide shows various key performance indicators which can be used to report cyber security. It includes metrics detected intrusion attempts, incident rate, vulnerability patch response times, etc. Showcasing this set of slides titled KPI Metrics For Cyber Safety And Security Report Elements PDF. The topics addressed in these templates are Incident Rate, Application, Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
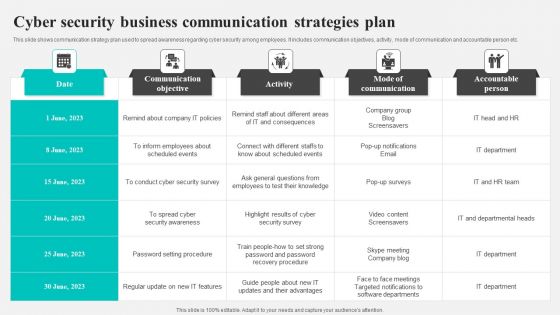
Cyber Security Business Communication Strategies Plan Background PDF
This slide shows communication strategy plan used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person etc. Showcasing this set of slides titled Cyber Security Business Communication Strategies Plan Background PDF. The topics addressed in these templates are Communication Objective, Activity, Mode Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
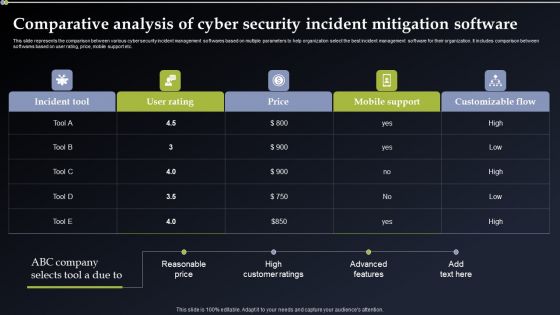
Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Presenting this PowerPoint presentation, titled Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cyber Security Incident Handler Contact Information Information PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Handler Contact Information Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
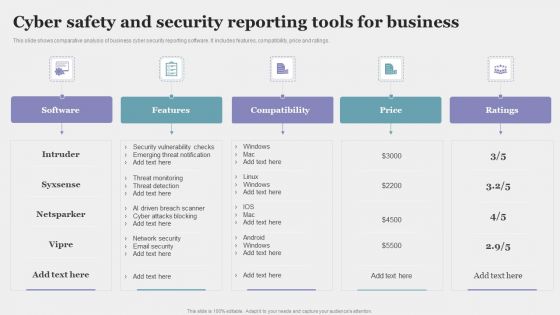
Cyber Safety And Security Reporting Tools For Business Rules PDF
This slide shows comparative analysis of business cyber security reporting software. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Cyber Safety And Security Reporting Tools For Business Rules PDF. This layout presents information on Compatibility, Price, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
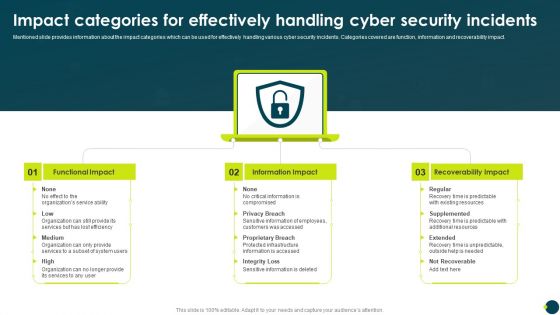
Impact Categories For Effectively Handling Cyber Security Incidents Download PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact.Deliver an awe inspiring pitch with this creative Impact Categories For Effectively Handling Cyber Security Incidents Download PDF bundle. Topics like Functional Impact, Information Impact, Recoverability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
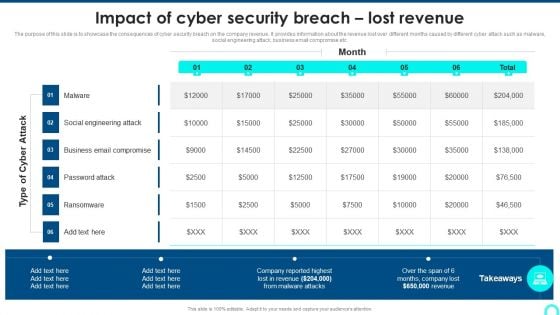
Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
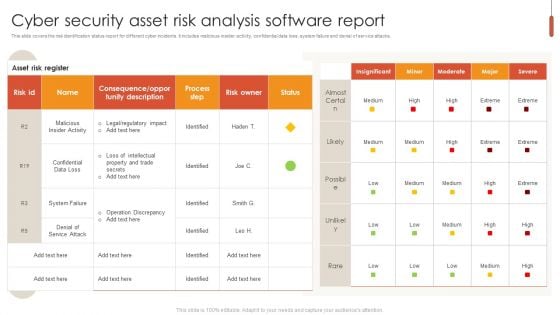
Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
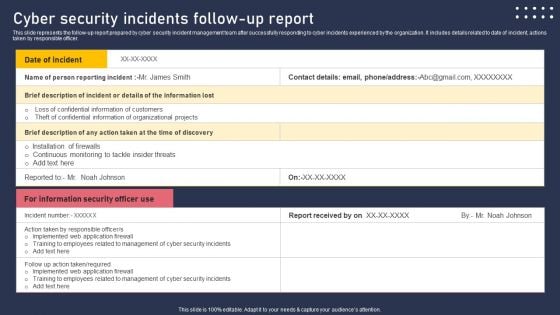
Cyber Security Incidents Follow Up Report Summary PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Take your projects to the next level with our ultimate collection of Cyber Security Incidents Follow Up Report Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
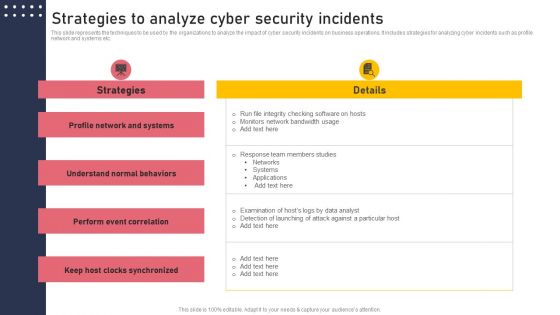
Strategies To Analyze Cyber Security Incidents Structure PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Find highly impressive Strategies To Analyze Cyber Security Incidents Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies To Analyze Cyber Security Incidents Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
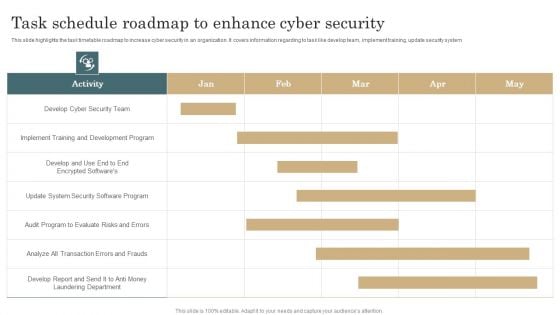
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
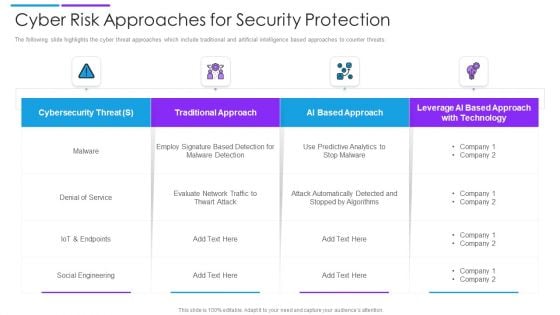
Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Standards Compliance Traceability Matrix Information PDF
This slide represents the cyber security standards compliance matrix. The purpose of this slide is to demonstrate the various cybersecurity standards and their compliance requirements for businesses. The primary standards include ISO27001, PCI DSS, HIPPA, FINRA and GDPR. Showcasing this set of slides titled Cyber Security Standards Compliance Traceability Matrix Information PDF. The topics addressed in these templates are Standards, Requirements, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
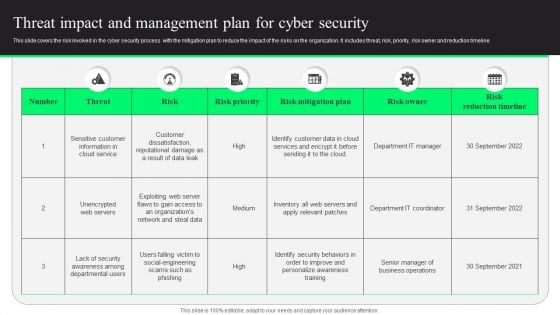
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
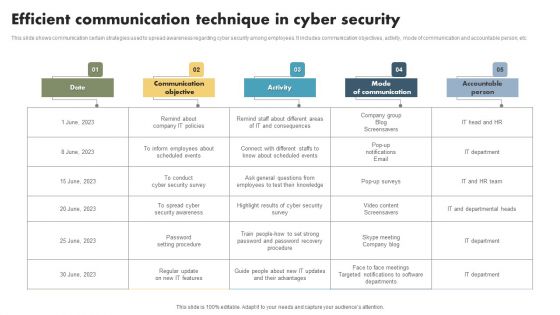
Efficient Communication Technique In Cyber Security Mockup PDF
This slide shows communication certain strategies used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person, etc. Showcasing this set of slides titled Efficient Communication Technique In Cyber Security Mockup PDF. The topics addressed in these templates are Date, Communication Objectives, Activity, Mode Of Communication, Accountable Person. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
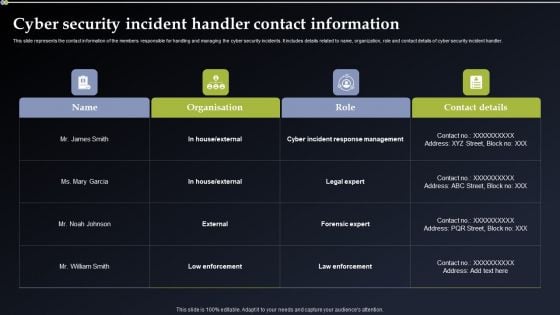
Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
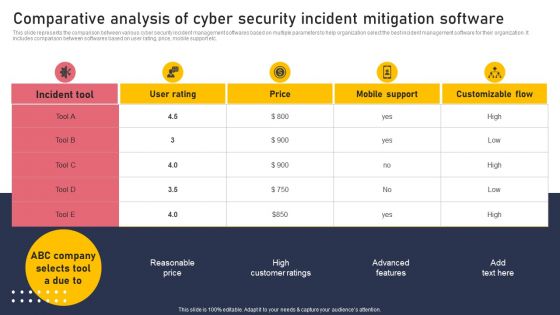
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Security Crisis Management Action Plan Timeline Topics PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Crisis Management Action Plan Timeline Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Crisis Management Action Plan Timeline Topics PDF

Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF from Slidegeeks today.
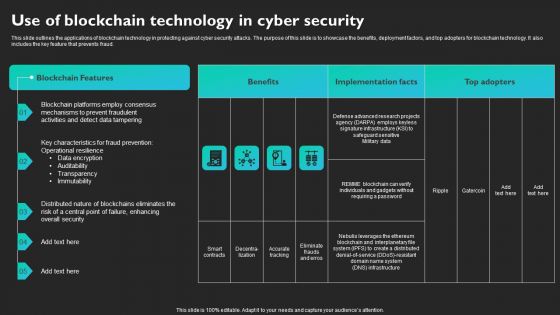
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Framework For Improving Critical Infra Cyber Security Icons PDF
The following slide exhibits framework for protection, resilience of infrastructure and other sectors important to national security. It presents information related to protection, responding, etc. Showcasing this set of slides titled Framework For Improving Critical Infra Cyber Security Icons PDF. The topics addressed in these templates are Identify, Protect, Detect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Qualitative Risk Analysis Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management. This is categorized as certain, likely, possible, unlikely, and rare. Pitch your topic with ease and precision using this Cyber Security Qualitative Risk Analysis Matrix Background PDF. This layout presents information on Risk Matrix, High Severity, Cyber Security Qualitative. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
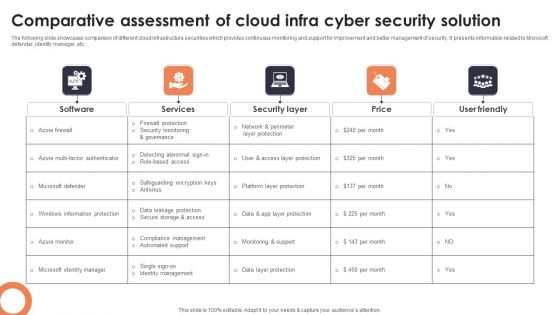
Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF
The following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Showcasing this set of slides titled Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF. The topics addressed in these templates are Software, Services, Security Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
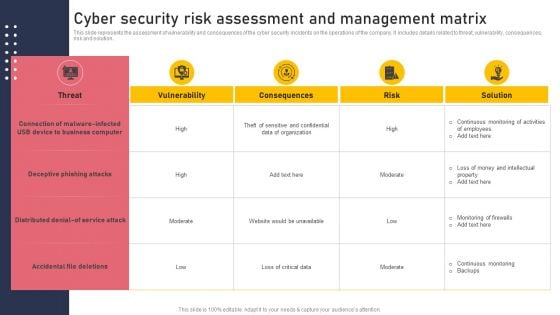
Cyber Security Risk Assessment And Management Matrix Inspiration PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Find a pre designed and impeccable Cyber Security Risk Assessment And Management Matrix Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Risk Management Plan Impact Assessment Matrix Information PDF
Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact assessment matrix information pdf. Use them to share invaluable insights on financial, reputation, regulatory, operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
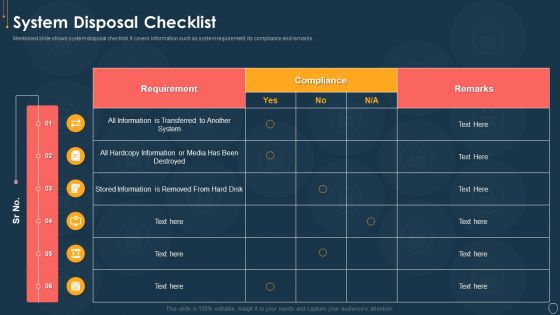
Cyber Security Risk Management Plan System Disposal Checklist Introduction PDF
Mentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks. Deliver an awe inspiring pitch with this creative cyber security risk management plan system disposal checklist introduction pdf bundle. Topics like system disposal checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
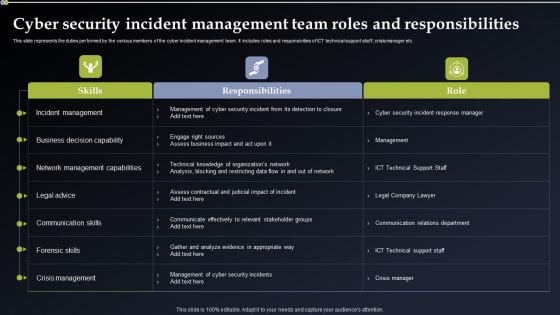
Cyber Security Incident Management Team Roles And Responsibilities Structure PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Incident Management Team Roles And Responsibilities Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Incident Management Team Roles And Responsibilities Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
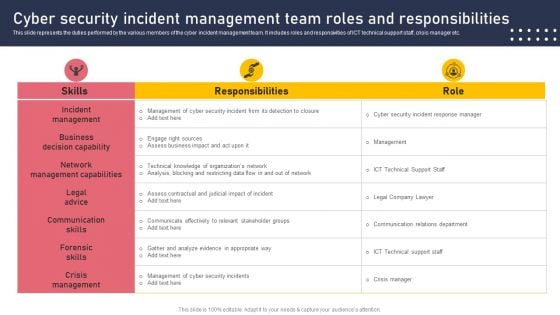
Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Are you searching for a Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF from Slidegeeks today.
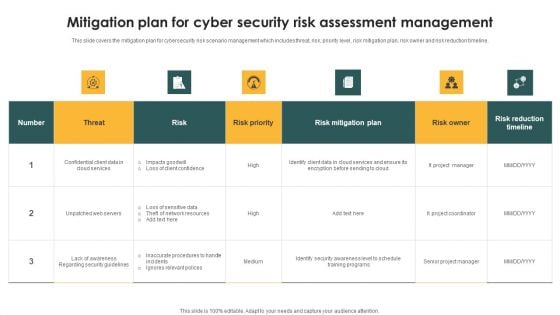
Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
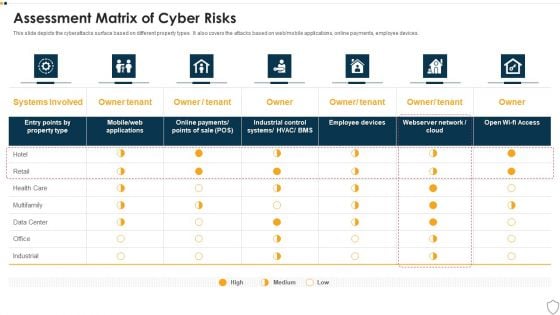
IT Security Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative it security assessment matrix of cyber risks infographics pdf bundle. Topics like data center, industrial, retail, health care can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
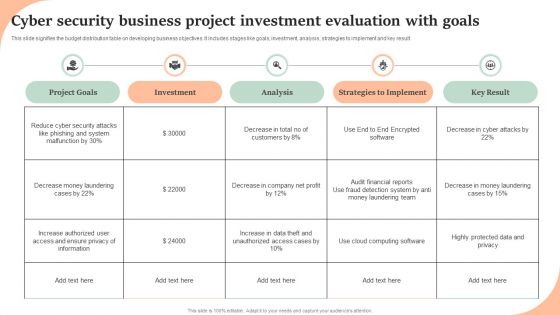
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
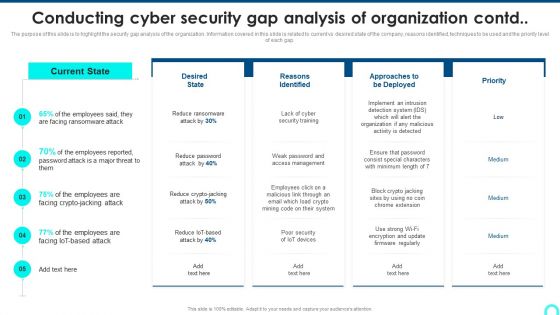
Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Conducting Cyber Security Gap Analysis Of Organization Formats PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
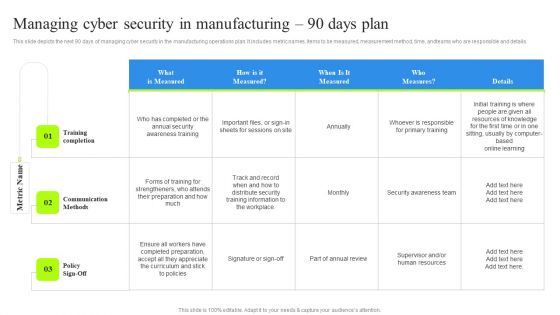
Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
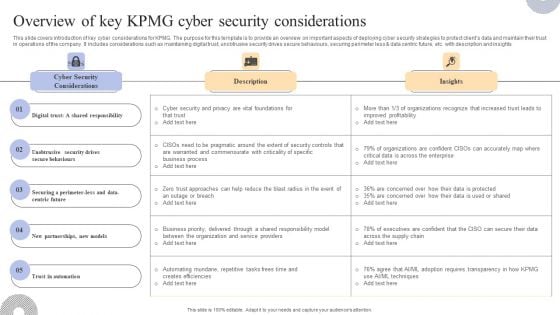
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
Infra Cyber Security Icon For Infrastructure Protection Information PDF
Presenting Infra Cyber Security Icon For Infrastructure Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Infrastructure Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
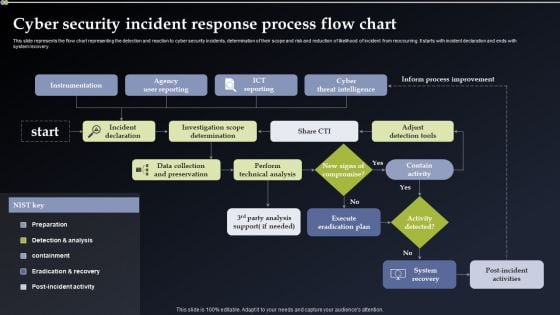
Cyber Security Incident Response Process Flow Chart Information PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Process Flow Chart Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Process Flow Chart Information PDF.
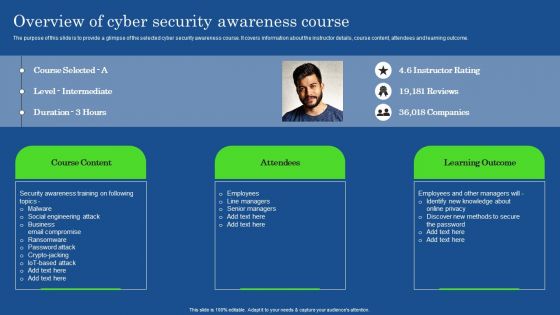
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.
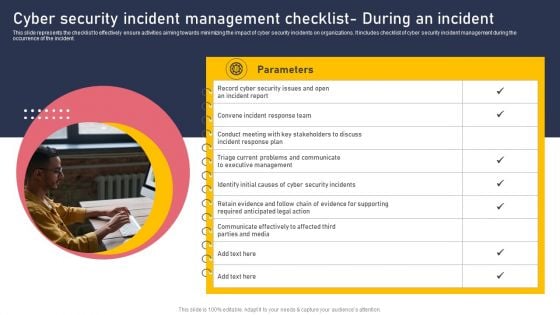
Cyber Security Incident Management Checklist During An Incident Inspiration PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. The Cyber Security Incident Management Checklist During An Incident Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Agenda For Cyber Physical System To Enhance Security Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Agenda For Cyber Physical System To Enhance Security Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Agenda For Cyber Physical System To Enhance Security Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Implementing Cyber Security Incident Management Table Of Contents Clipart PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Management Table Of Contents Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Management Table Of Contents Clipart PDF today and make your presentation stand out from the rest.

 Home
Home