Cyber Security Roadmap
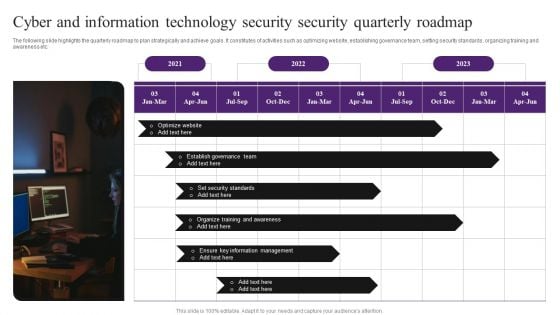
Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF
The following slide highlights the quarterly roadmap to plan strategically and achieve goals. It constitutes of activities such as optimizing website, establishing governance team, setting security standards, organizing training and awareness etc. Presenting Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Optimize Website, Information Management, Organize Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Implementation Framework Roadmap For Process Flow Ppt PowerPoint Presentation File Graphics Tutorials PDF
Presenting this set of slides with name cyber security implementation framework roadmap for process flow ppt powerpoint presentation file graphics tutorials pdf. This is a six stage process. The stages in this process are roadmap, process flow. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Roadmap Inspiration PDF
Presenting case competition overpower the obstacle of cyber security in medicare roadmap inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap, 2017 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
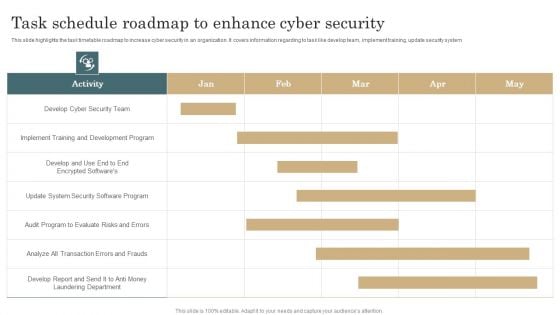
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Global Cyber Terrorism Incidents On The Rise IT Roadmap To Implement Cyber Security Icons PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. This is a global cyber terrorism incidents on the rise it roadmap to implement cyber security icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keep the hardware and software updated, awareness training for employees, creating personal accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
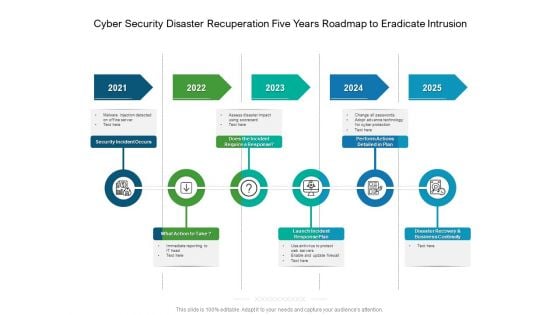
Cyber Security Disaster Recuperation Five Years Roadmap To Eradicate Intrusion Professional
We present our cyber security disaster recuperation five years roadmap to eradicate intrusion professional. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched cyber security disaster recuperation five years roadmap to eradicate intrusion professionalin different formats like PDF, PNG, and JPG to smoothly execute your business plan.
5 Year Action Plan And Advantage Roadmap For Cyber Security Icons
We present our 5 year action plan and advantage roadmap for cyber security icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 5 year action plan and advantage roadmap for cyber security icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
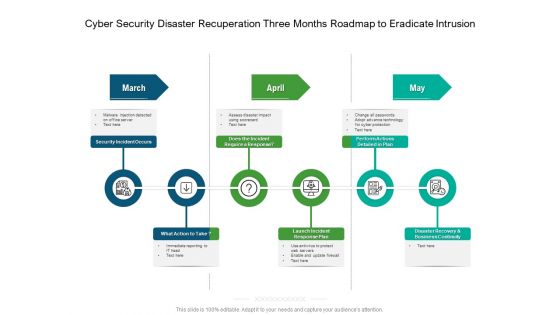
Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Cyber Security Disaster Recuperation Six Months Roadmap To Eradicate Intrusion Icons
Presenting the cyber security disaster recuperation six months roadmap to eradicate intrusion icons. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF
Presenting Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic Plan, Roadmap Improve, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
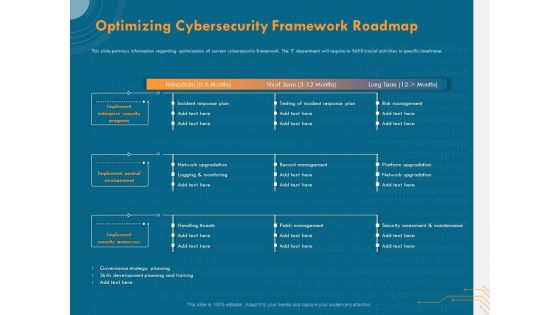
Cyber Security Implementation Framework Optimizing Cybersecurity Framework Roadmap Ppt Outline Background PDF
Presenting this set of slides with name cyber security implementation framework optimizing cybersecurity framework roadmap ppt outline background pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes, incident response plan, testing incident response plan, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
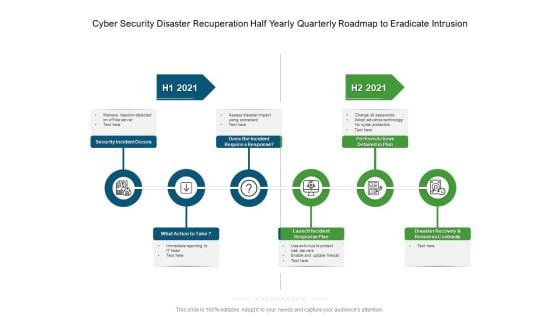
Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
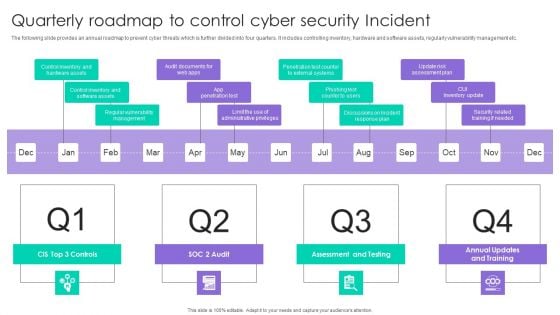
Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
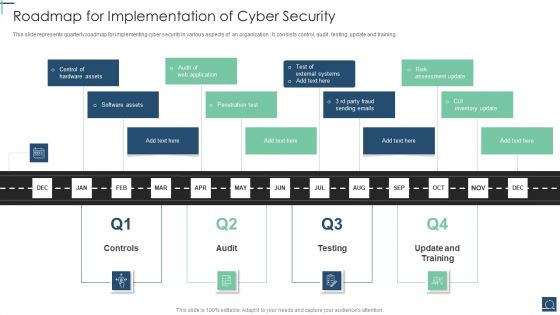
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
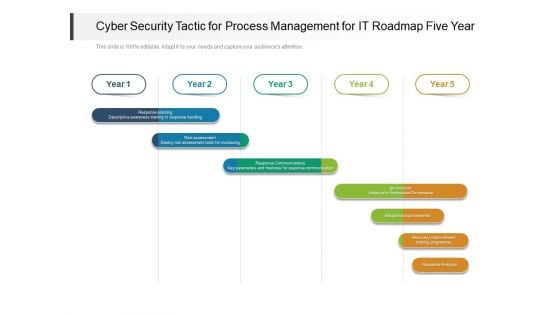
Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
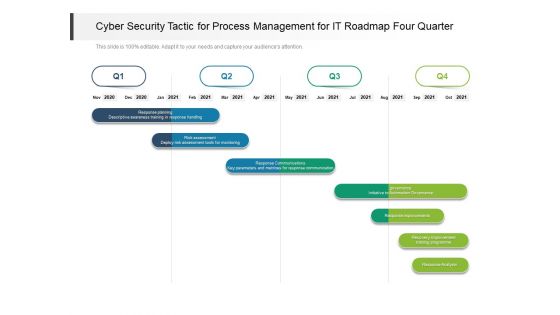
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
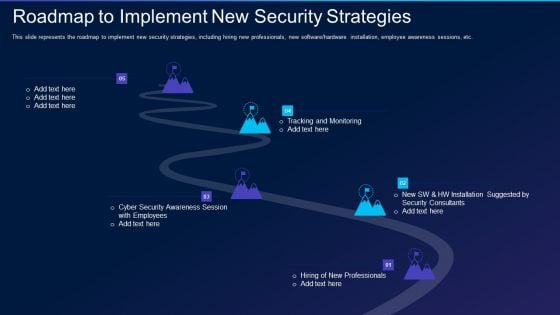
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
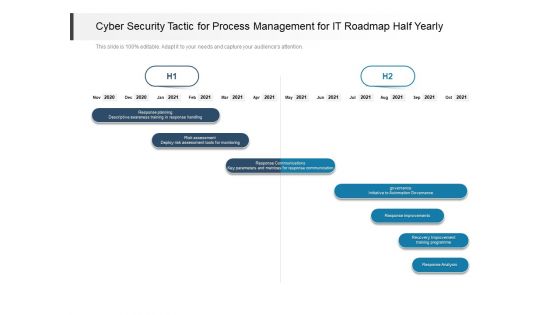
Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
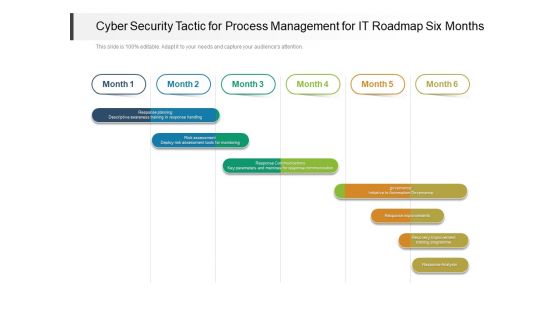
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
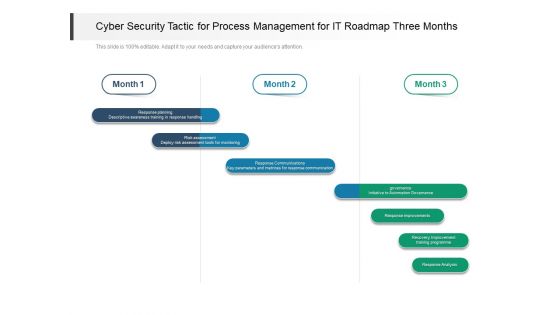
Cyber Security Tactic For Process Management For IT Roadmap Three Months Demonstration
Presenting our jaw dropping cyber security tactic for process management for it roadmap three months demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
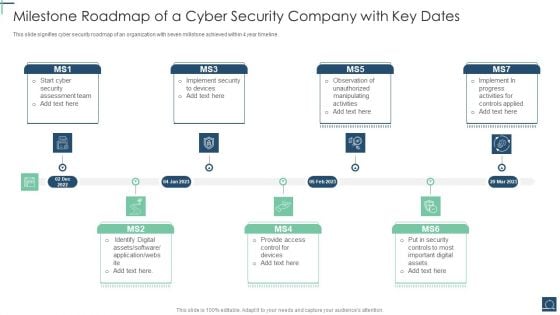
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
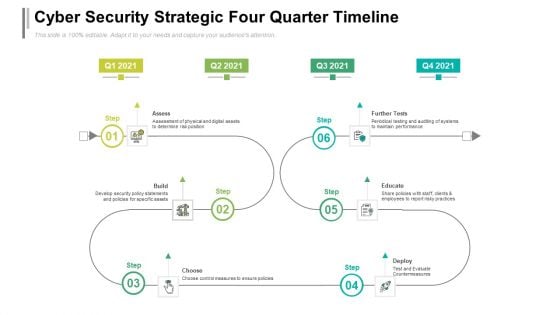
Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
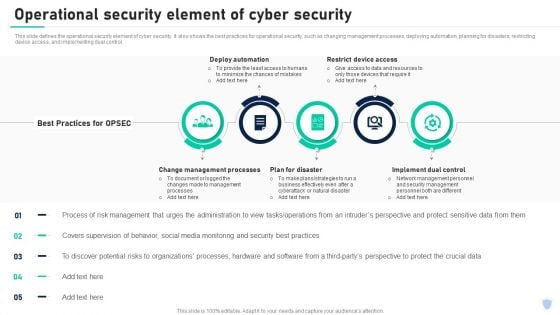
Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
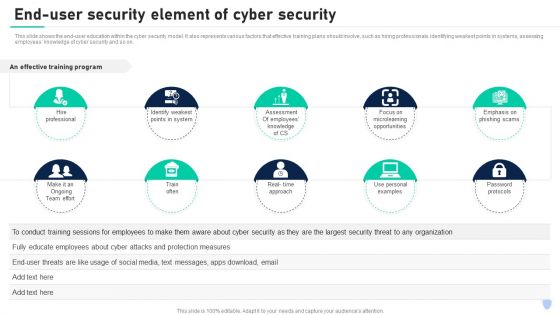
Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Find a pre designed and impeccable Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
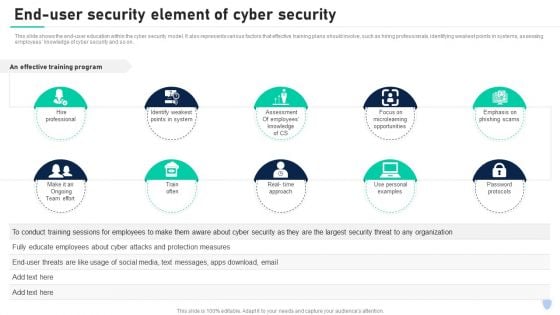
Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
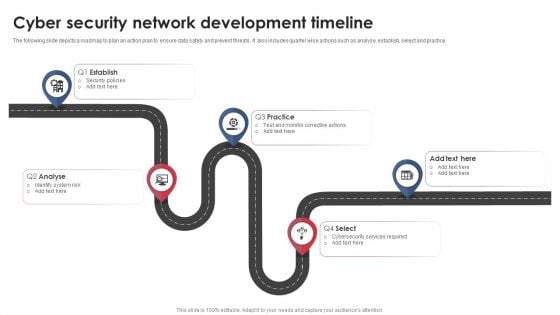
Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
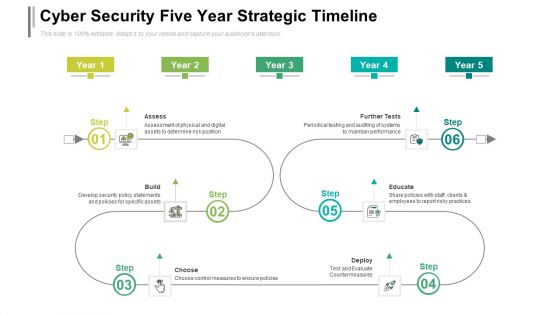
Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
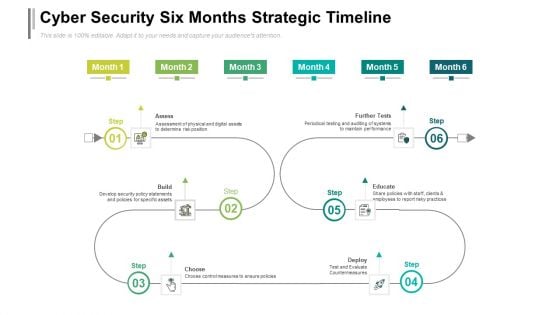
Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
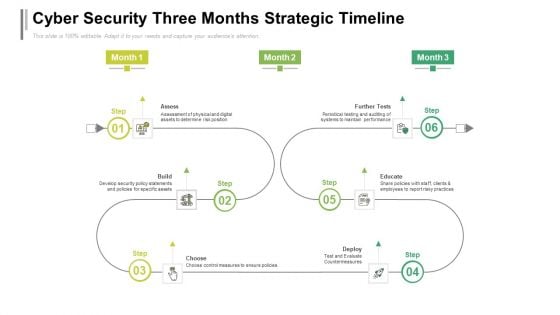
Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
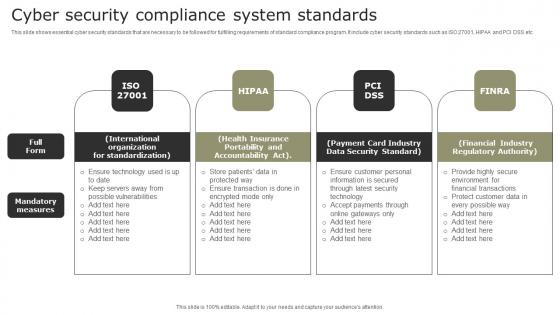
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.
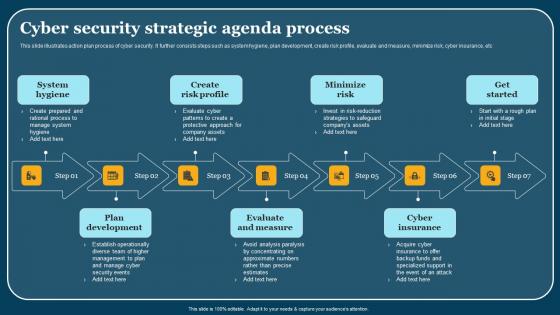
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
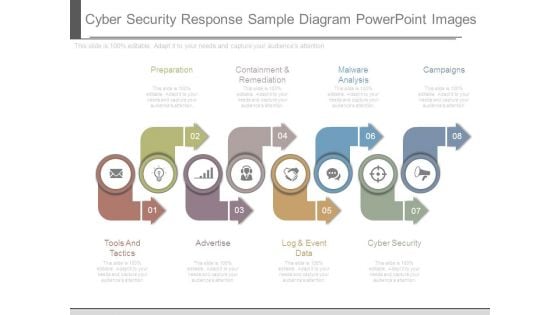
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.
Cyber Security Ppt PowerPoint Presentation Layouts Brochure
This is a cyber security ppt powerpoint presentation layouts brochure. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing.
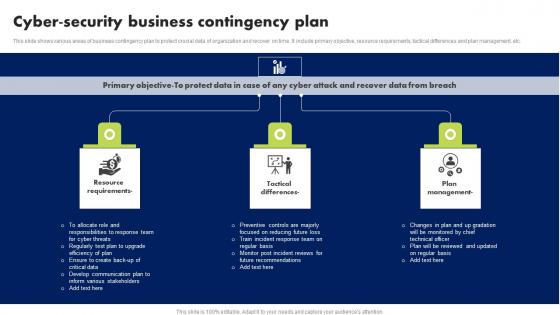
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.

Cyber Security Incident Response Lifecycle Information PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Presenting this PowerPoint presentation, titled Cyber Security Incident Response Lifecycle Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Security Incident Response Lifecycle Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Security Incident Response Lifecycle Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
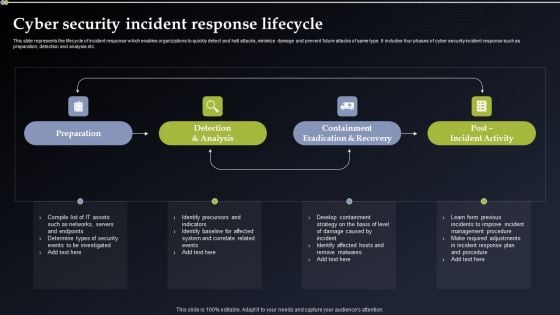
Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
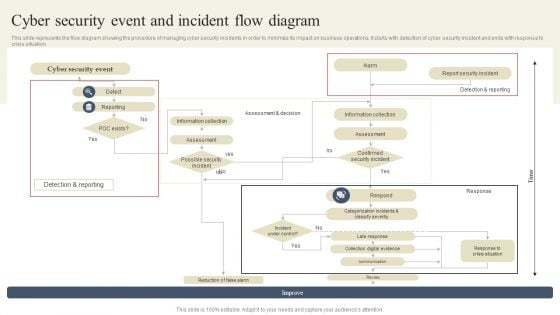
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
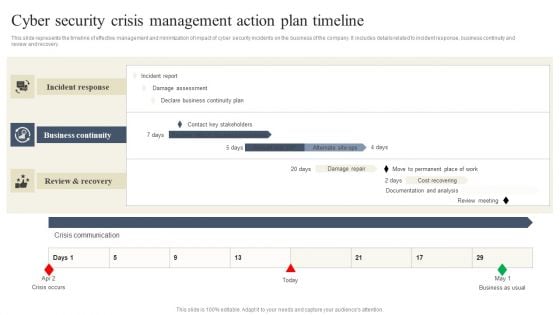
CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Get a simple yet stunning designed CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
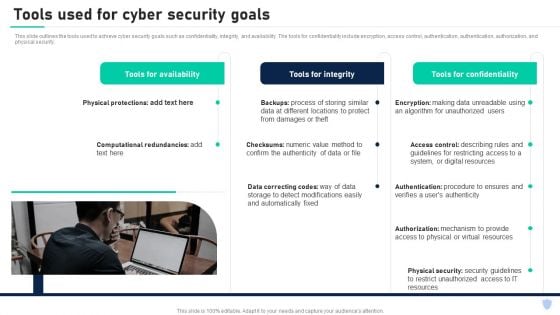
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
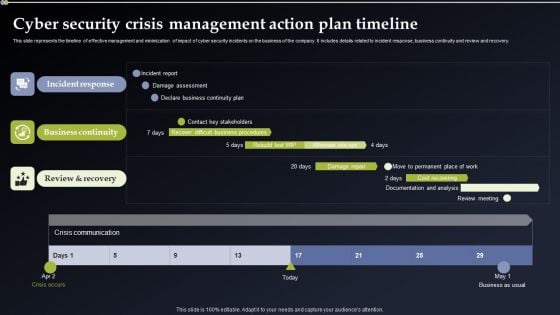
Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
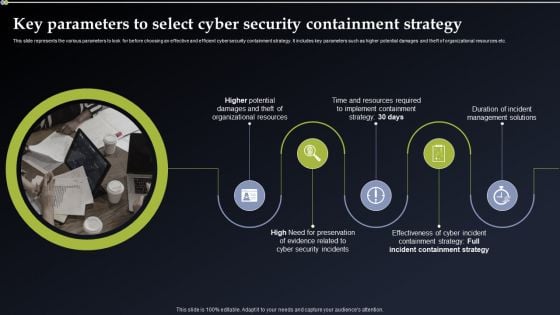
Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
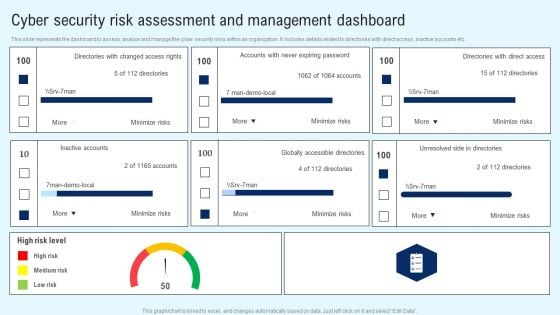
Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
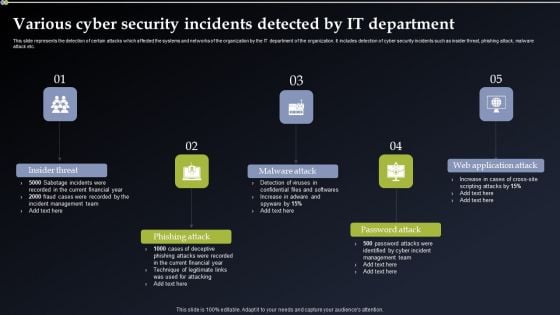
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
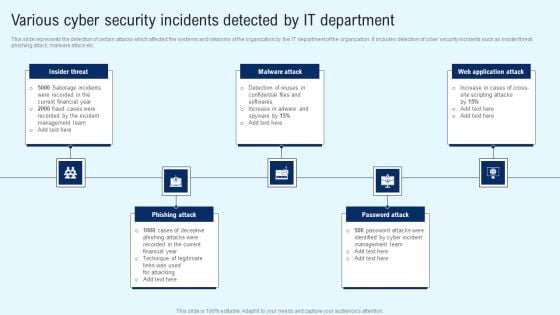
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
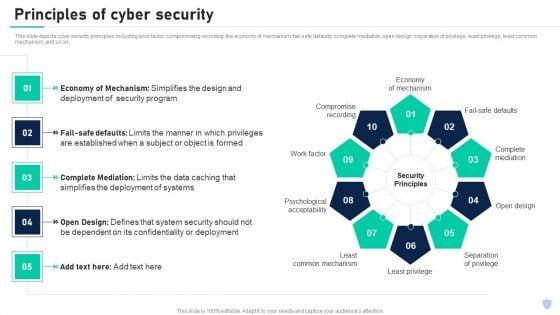
Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF
This slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail-safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Get a simple yet stunning designed Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
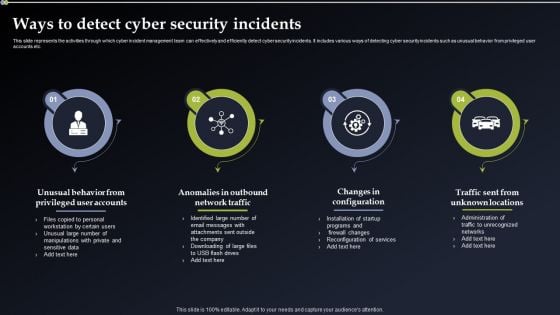
Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
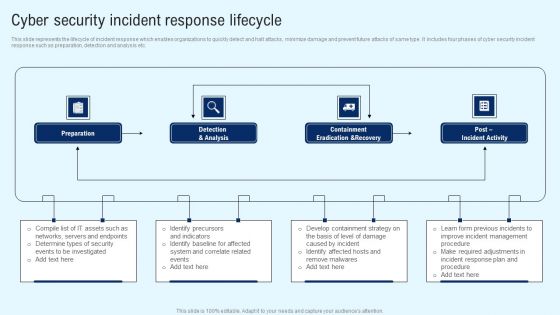
Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
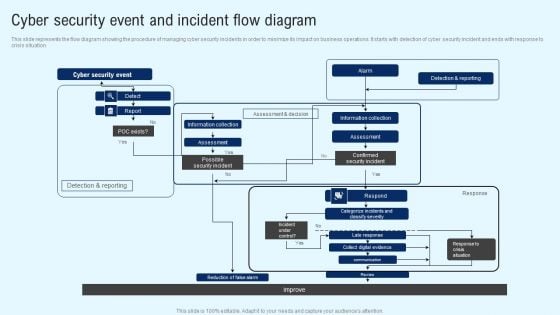
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
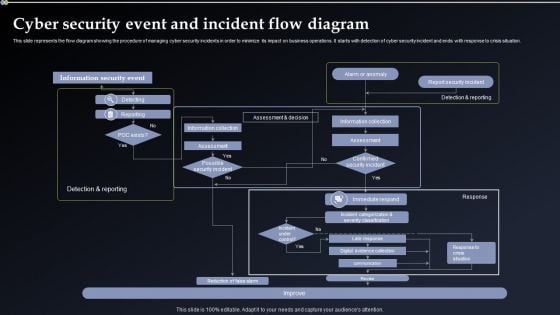
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
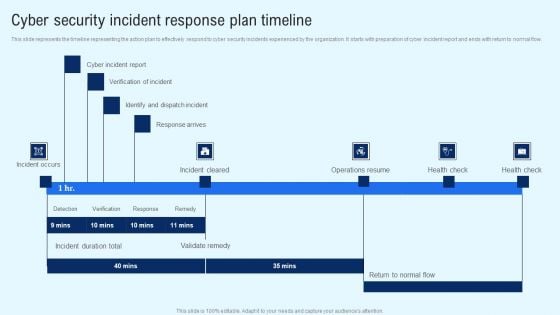
Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Welcome to our selection of the Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
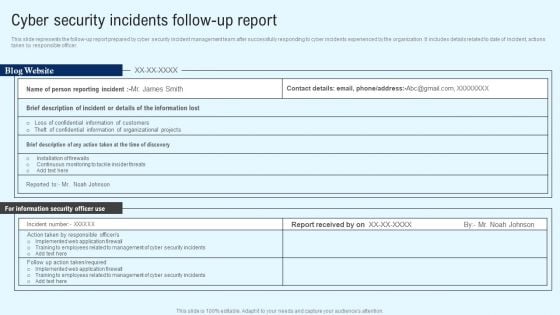
Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

 Home
Home