Cyber Security Strategy
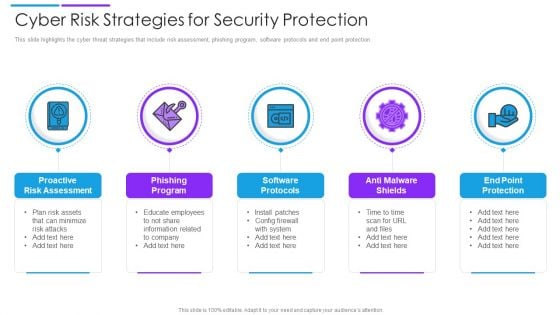
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
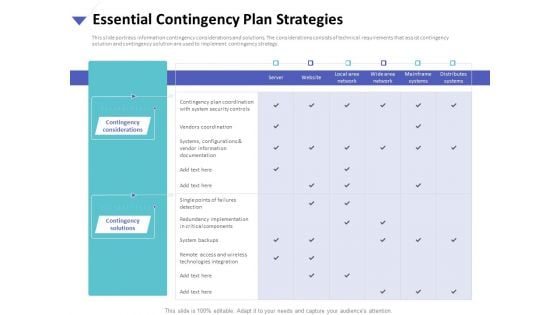
Strategies To Mitigate Cyber Security Risks Essential Contingency Plan Strategies Ppt Pictures Themes PDF
Presenting this set of slides with name strategies to mitigate cyber security risks essential contingency plan strategies ppt pictures themes pdf. The topics discussed in these slides are contingency considerations, contingency solutions, technologies integration, vendors coordination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
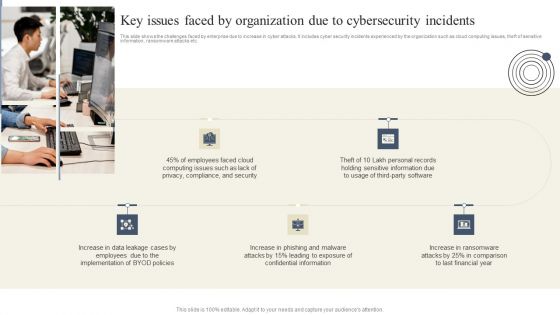
Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
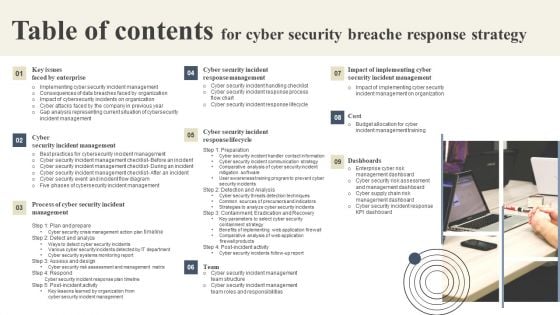
Table Of Contents For Cyber Security Breache Response Strategy Formats PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Cyber Security Breache Response Strategy Formats PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. There are so many reasons you need a CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
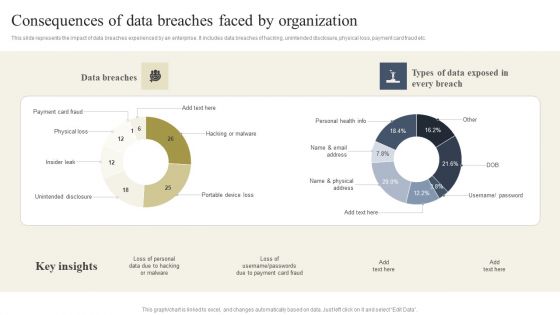
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
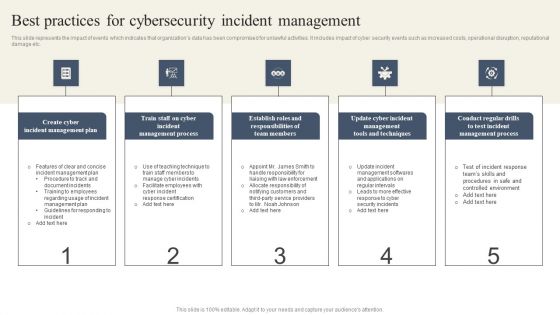
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
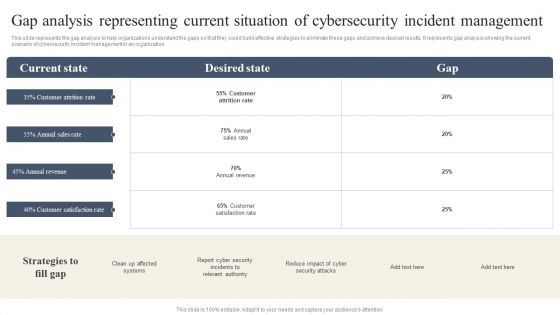
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
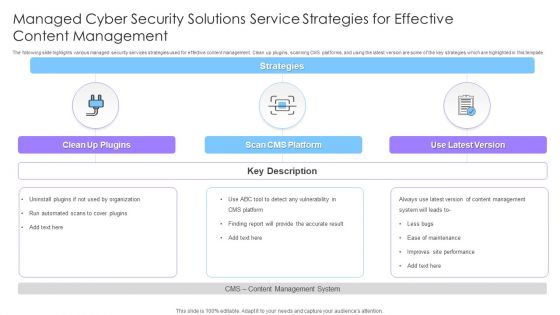
Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
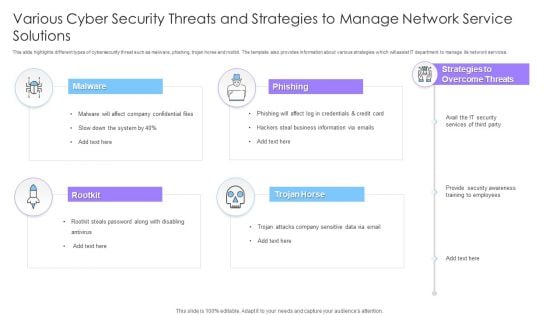
Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Divisional Strategy To Improve Cyber Security Measures Icons PDF
This slide signifies information technology department to enhance cyber security measures. It also includes stages like identify, plan, execute and control. Presenting IT Divisional Strategy To Improve Cyber Security Measures Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Plan, Execute, Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
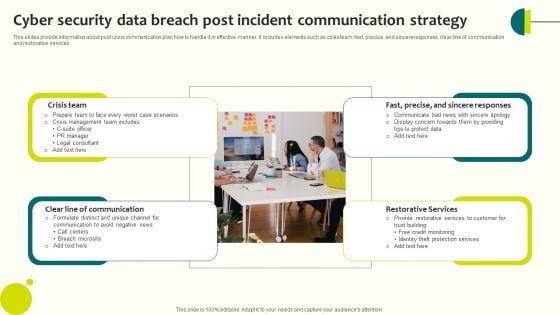
Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
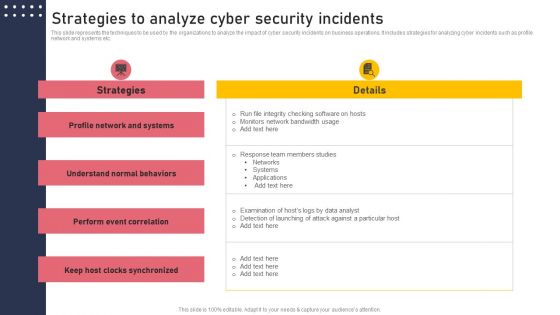
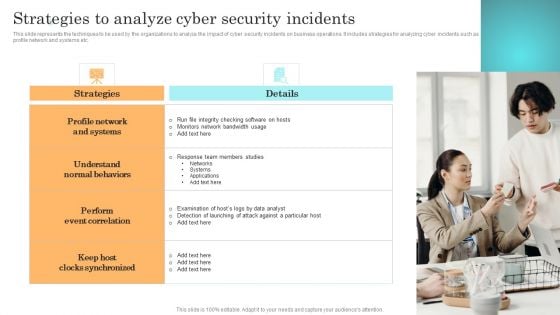
Strategies To Analyze Cyber Security Incidents Structure PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Find highly impressive Strategies To Analyze Cyber Security Incidents Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies To Analyze Cyber Security Incidents Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
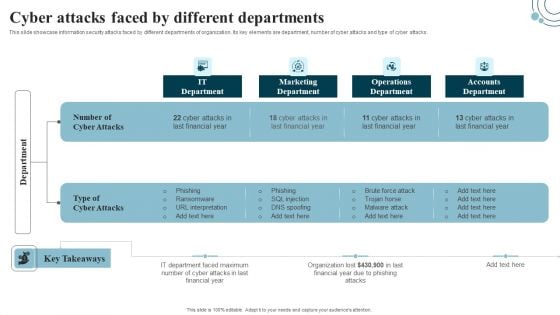
Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.
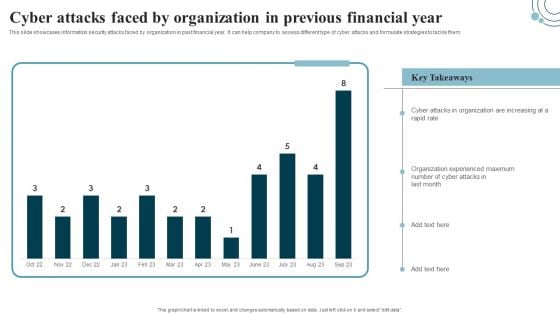
Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
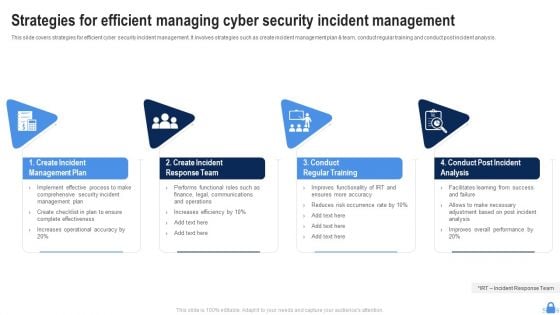
Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF
This slide covers strategies for efficient cyber security incident management. It involves strategies such as create incident management plan and team, conduct regular training and conduct post incident analysis. Presenting Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Incident Management Plan, Create Incident, Response Team, Conduct Regular Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
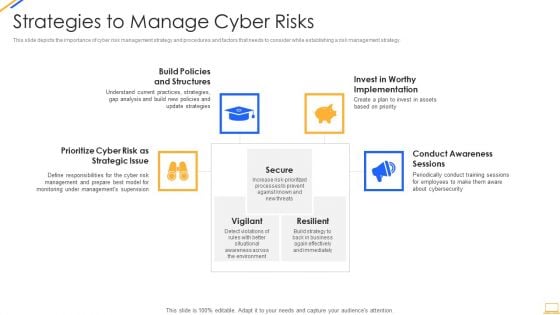
Desktop Security Management Strategies To Manage Cyber Risks Rules PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting desktop security management strategies to manage cyber risks rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strategic, risk, implementation, awareness, invest. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Agenda For Cyber Security Risks Ppt Infographics Graphics Design PDF
Presenting this set of slides with name strategies to mitigate cyber security risks agenda for cyber security risks ppt infographics graphics design pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, senior management, executives responsible, risk management, presenting optimize cybersecurity, risk framework. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Dashboard Cyber Risk Management Ppt Professional Display PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard cyber risk management ppt professional display pdf. The topics discussed in these slides are risks threshold top 5 vulnerabilities, risk rating breakdown, action plan breakdown, risk heat map. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Categorization Of Cyber Risks Ppt Model Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks categorization of cyber risks ppt model designs download pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Incident Reporting By Different Cyber Departments Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks incident reporting by different cyber departments summary pdf. This is a one stage process. The stages in this process are number incidents, person involved incident, average cost per incident, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
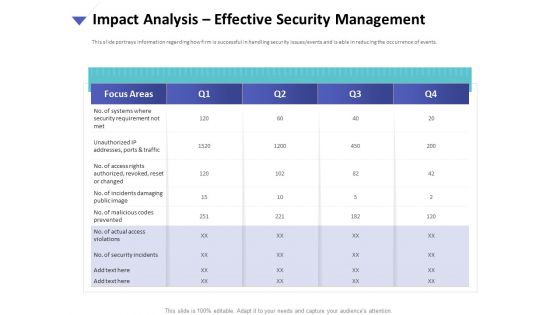
Strategies To Mitigate Cyber Security Risks Impact Analysis Effective Security Management Introduction PDF
Presenting this set of slides with name strategies to mitigate cyber security risks impact analysis effective security management introduction pdf. The topics discussed in these slides are focus areas, security requirement, access rights authorized, incidents damaging, actual access violations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Impact Analysis Implementing Cybersecurity Framework Mockup PDF
Presenting this set of slides with name strategies to mitigate cyber security risks impact analysis implementing cybersecurity framework mockup pdf. This is a one stage process. The stages in this process are controls met, csf metric, recover, respond, detect, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Cybersecurity Risks Management Action Plan Resources Portrait PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity risks management action plan resources portrait pdf. The topics discussed in these slides are potential risk, risk level, reason risk rating, action, required resources, responsible person, duration, communication, risk treated. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Cybersecurity Risks Management Action Plan Treatment Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity risks management action plan treatment brochure pdf. The topics discussed in these slides are risk identification, risk treatment, event, action, risk owner, timely manner. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
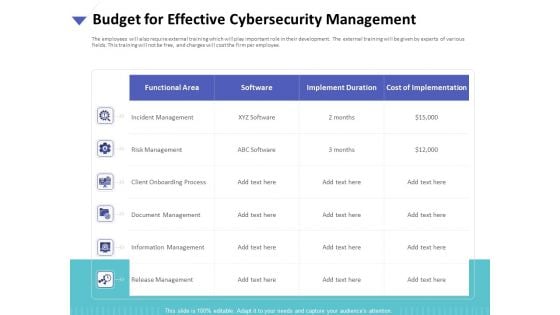
Strategies To Mitigate Cyber Security Risks Budget For Effective Cybersecurity Management Ppt Infographic Template Styles PDF
Presenting this set of slides with name strategies to mitigate cyber security risks budget for effective cybersecurity management ppt infographic template styles pdf. The topics discussed in these slides are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
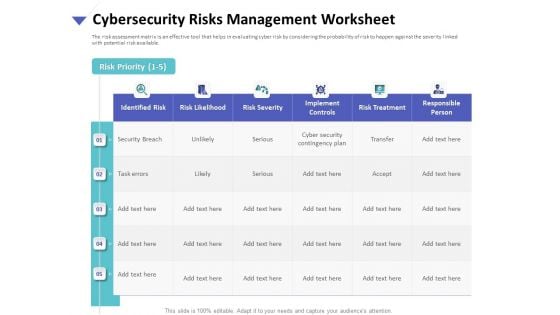
Strategies To Mitigate Cyber Security Risks Cybersecurity Risks Management Worksheet Ppt Gallery Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity risks management worksheet ppt gallery influencers pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
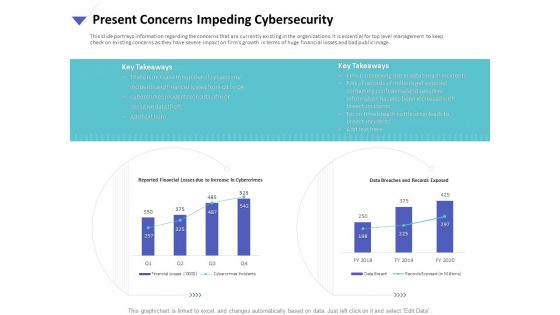
Strategies To Mitigate Cyber Security Risks Present Concerns Impeding Cybersecurity Ppt Show Objects PDF
Presenting this set of slides with name strategies to mitigate cyber security risks present concerns impeding cybersecurity ppt show objects pdf. The topics discussed in these slides are reported financial losses due increase cybercrimes, data breaches and records exposed, key takeaways. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks 30 60 90 Days Plan Ppt Icon Picture PDF
Presenting this set of slides with name strategies to mitigate cyber security risks 30 60 90 days plan ppt icon picture pdf. This is a three stage process. The stages in this process are 30 60 90 days. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Recovery Budget Planning Ppt Ideas Graphic Images
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance recovery budget planning ppt ideas graphic images. This is a one stage process. The stages in this process are vendor costs, hardware costs, software costs, equipment replacement, testing costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Essential Contingency Plan Strategies Ppt Portfolio Introduction PDF
Presenting this set of slides with name cyber security implementation framework essential contingency plan strategies ppt portfolio introduction pdf. The topics discussed in these slides are contingency considerations, contingency solutions, vendors coordination, system backups. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Determining Firm Current Capabilities Ppt Inspiration Smartart PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining firm current capabilities ppt inspiration smartart pdf. The topics discussed in these slides are identify, protect, detect, response, recovery, key enablers, minimum standard, evolving strength. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Recovery Task List Maintenance Ppt Infographics Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks recovery task list maintenance ppt infographics designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments, retrieve business continuity plans. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Strategies To Mitigate Cyber Security Risks Ppt Icon Themes PDF
Presenting this set of slides containing editable icons for topic icons slide for strategies to mitigate cyber security risks ppt icon themes pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
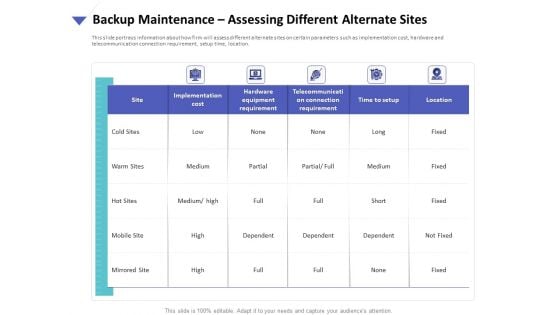
Strategies To Mitigate Cyber Security Risks Backup Maintenance Assessing Different Alternate Sites Ppt Portfolio Background PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance assessing different alternate sites ppt portfolio background pdf. The topics discussed in these slides are implementation cost, hardware equipment requirement, telecommunication connection requirement, time setup, location. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Developing Alternate Sites Ppt Templates PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance developing alternate sites ppt templates pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
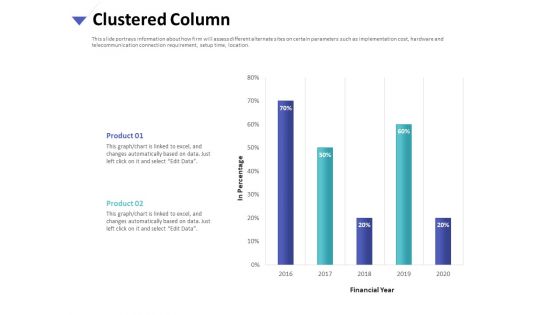
Strategies To Mitigate Cyber Security Risks Clustered Column Ppt Inspiration Example PDF
Presenting this set of slides with name strategies to mitigate cyber security risks clustered column ppt inspiration example pdf. The topics discussed in these slide is clustered column. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Critical Business Functions Recovery Priorities Ppt Gallery Graphics Pictures PDF
Presenting this set of slides with name strategies to mitigate cyber security risks critical business functions recovery priorities ppt gallery graphics pictures pdf. This is a one stage process. The stages in this process are department, priorities, maximum allowable downtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Dashboard Ppt File Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard ppt file brochure pdf. The topics discussed in these slide is dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Financial Ppt Icon Rules PDF
Presenting this set of slides with name strategies to mitigate cyber security risks financial ppt icon rules pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Our Mission Ppt Model Shapes PDF
Presenting this set of slides with name strategies to mitigate cyber security risks our mission ppt model shapes pdf. This is a three stage process. The stages in this process are mission, vision, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Our Team Ppt Professional Deck PDF
Presenting this set of slides with name strategies to mitigate cyber security risks our team ppt professional deck pdf. This is a three stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Risk Assessment Matrix Ppt Visuals PDF
Presenting this set of slides with name strategies to mitigate cyber security risks risk assessment matrix ppt visuals pdf. This is a four stage process. The stages in this process are insignificant, minor significant, serious, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Roadmap For Process Flow Ppt Inspiration Icons PDF
Presenting this set of slides with name strategies to mitigate cyber security risks roadmap for process flow ppt inspiration icons pdf. This is a six stage process. The stages in this process are roadmap for process flow. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Staff Training Schedule With Cost Ppt Icon Graphic Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks staff training schedule with cost ppt icon graphic images pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Thank You Ppt Summary Aids PDF
Presenting this set of slides with name strategies to mitigate cyber security risks thank you ppt summary aids pdf. The topics discussed in these slide is thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Timeframe For Incident Management Ppt Inspiration Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks timeframe for incident management ppt inspiration brochure pdf. This is a one stage process. The stages in this process are ticket creation, incident logging, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
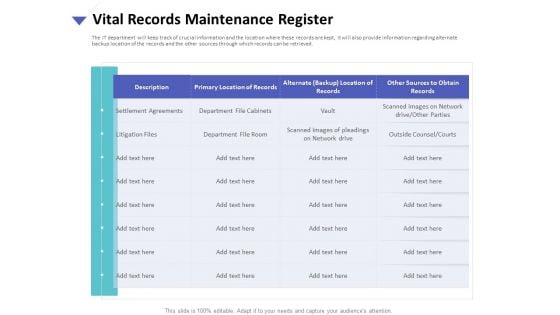
Strategies To Mitigate Cyber Security Risks Vital Records Maintenance Register Ppt Ideas Clipart Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks vital records maintenance register ppt ideas clipart images pdf. The topics discussed in these slides are settlement agreements, litigation files, department file cabinets, department file room, vault. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
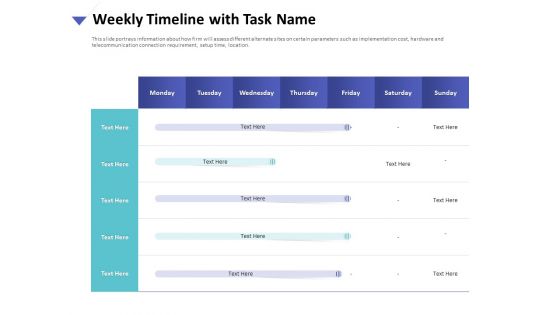
Strategies To Mitigate Cyber Security Risks Weekly Timeline With Task Name Ppt Styles Good PDF
Presenting this set of slides with name strategies to mitigate cyber security risks weekly timeline with task name ppt styles good pdf. The topics discussed in these slide is weekly timeline task. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
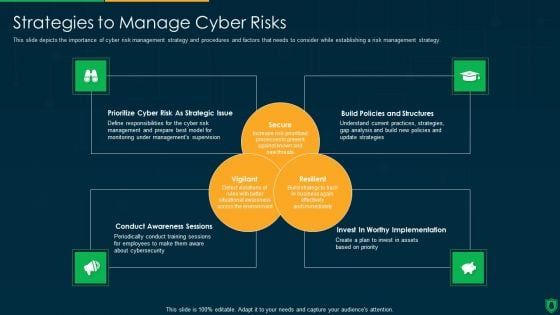
Info Security Strategies To Manage Cyber Risks Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a info security strategies to manage cyber risks ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prioritize cyber risk as strategic issue, build policies and structures, conduct awareness sessions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home