Cyber Threat
Icons Slide For Handling Cyber Threats In A Digital Era Ppt Pictures Portfolio PDF
Introducing our well designed icons slide for handling cyber threats in a digital era ppt pictures portfolio pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Table Of Contents Handling Cyber Threats In A Digital Era Ppt Summary Files PDF
Deliver an awe inspiring pitch with this creative table of contents handling cyber threats in a digital era ppt summary files pdf bundle. Topics like global market insights, companies digitization levels, defining business priorities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
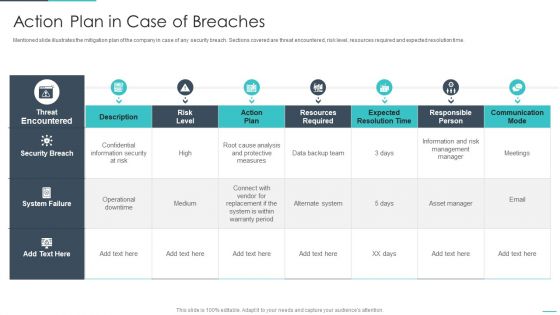
Handling Cyber Threats Digital Era Action Plan In Case Of Breaches Ppt Styles Objects PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative handling cyber threats digital era action plan in case of breaches ppt styles objects pdf bundle. Topics like action plan in case of breaches can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
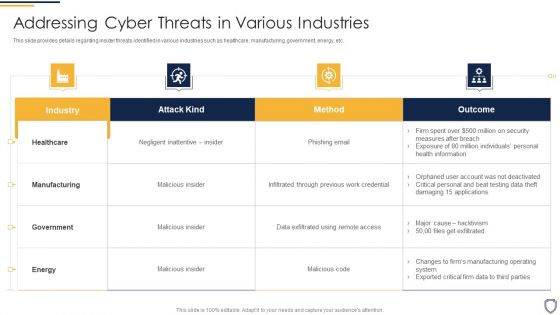
Corporate Security And Risk Management Addressing Cyber Threats In Various Industries Brochure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management addressing cyber threats in various industries brochure pdf. Use them to share invaluable insights on healthcare, manufacturing, government, energy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
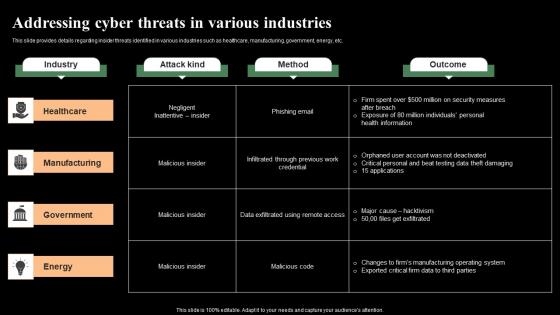
Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Slidegeeks has constructed Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc.
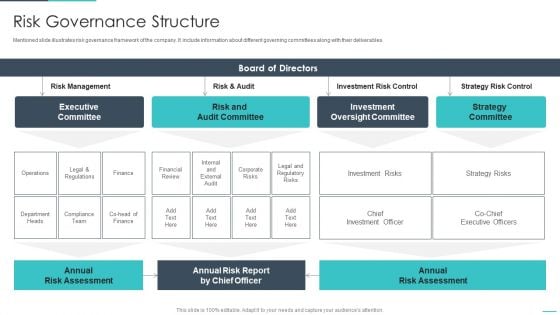
Handling Cyber Threats Digital Era Risk Governance Structure Ppt Slides Examples PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era risk governance structure ppt slides examples pdf. Use them to share invaluable insights on executive committee, risk and audit committee, investment oversight committee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
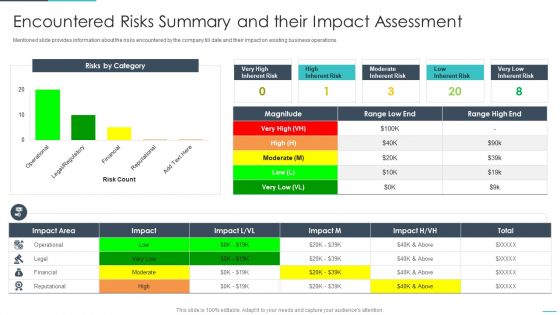
Handling Cyber Threats Digital Era Encountered Risks Summary And Their Impact Ppt Show Professional PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era encountered risks summary and their impact ppt show professional pdf. Use them to share invaluable insights on encountered risks summary and their impact assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Risk Management KPI Dashboard With Loss Ppt Slides PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative handling cyber threats digital era risk management kpi dashboard with loss ppt slides pdf bundle. Topics like gement kpi dashboard with loss events and actions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
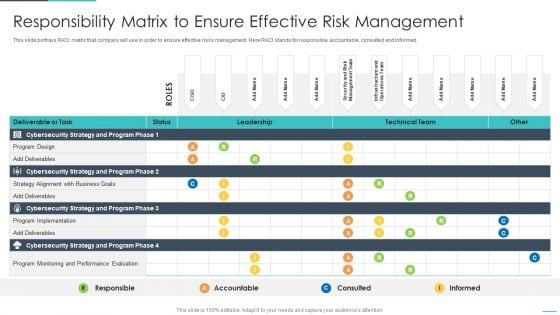
Handling Cyber Threats Digital Era Responsibility Matrix To Ensure Effective Ppt Show Inspiration PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative handling cyber threats digital era responsibility matrix to ensure effective ppt show inspiration pdf bundle. Topics like responsibility matrix to ensure effective risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
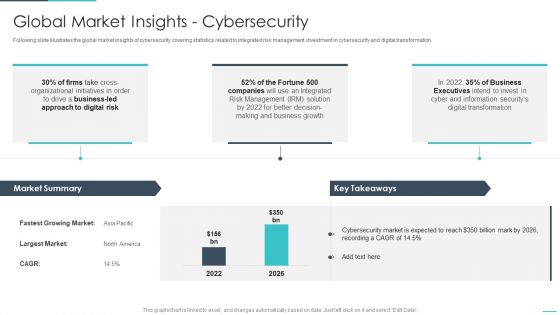
Handling Cyber Threats Digital Era Global Market Insights Cybersecurity Ppt Show Background Image PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative handling cyber threats digital era global market insights cybersecurity ppt show background image pdf bundle. Topics like global market insights cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
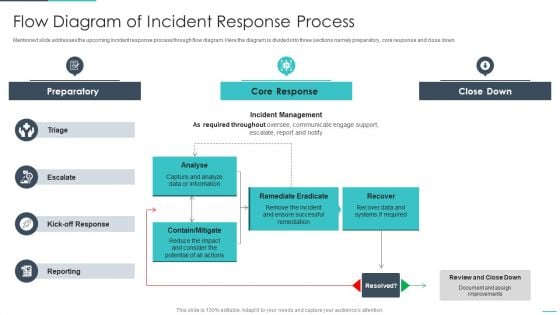
Handling Cyber Threats Digital Era Flow Diagram Of Incident Response Process Ppt Infographics Inspiration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative handling cyber threats digital era flow diagram of incident response process ppt infographics inspiration pdf bundle. Topics like preparatory, remediate eradicate, analyse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
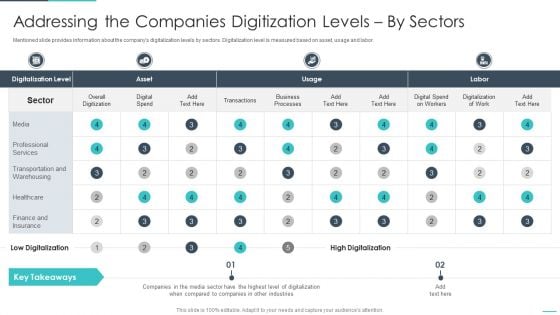
Handling Cyber Threats Digital Era Addressing The Companies Digitization Ppt Portfolio Smartart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver and pitch your topic in the best possible manner with this andling cyber threats digital era addressing the companies digitization ppt portfolio smartart pdf. Use them to share invaluable insights on addressing the companies digitization levels by sectors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
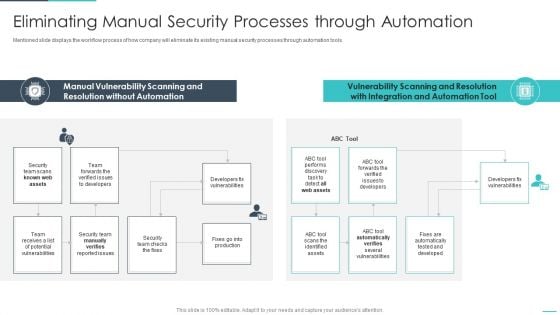
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
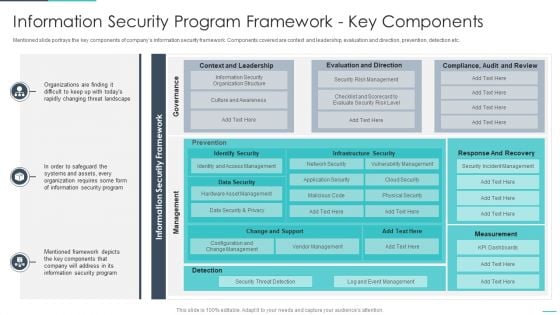
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Introducing New Incidents Logging Process Ppt Slides Graphic Images PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver an awe inspiring pitch with this creative handling cyber threats digital era introducing new incidents logging process ppt slides graphic images pdf bundle. Topics like introducing new incidents logging process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
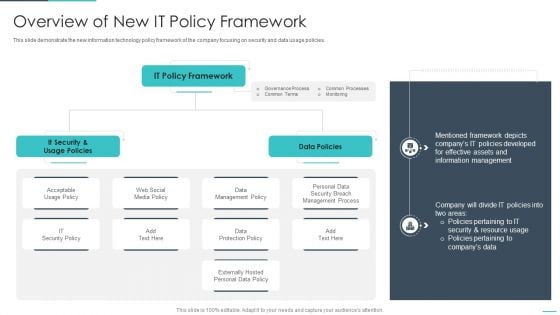
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
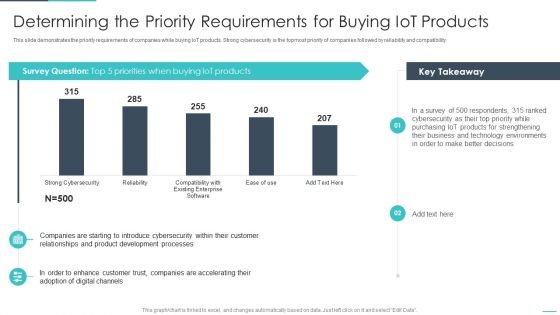
Handling Cyber Threats Digital Era Determining The Priority Requirements Ppt Outline Visual Aids PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative handling cyber threats digital era determining the priority requirements ppt outline visual aids pdf bundle. Topics like determining the priority requirements for buying iot products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
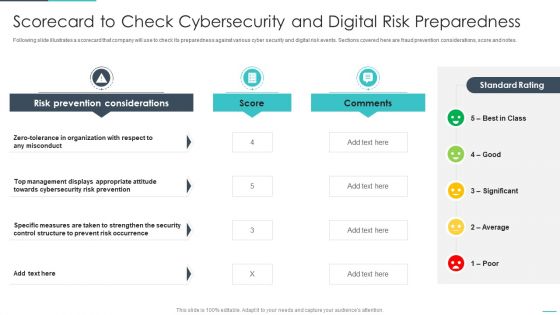
Handling Cyber Threats Digital Era Scorecard To Check Cybersecurity Ppt Model Information PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative dling cyber threats digital era scorecard to check cybersecurity ppt model information pdf bundle. Topics like scorecard to check cybersecurity and digital risk preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
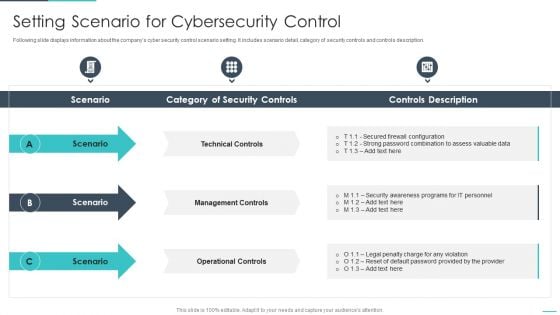
Handling Cyber Threats Digital Era Setting Scenario For Cybersecurity Control Ppt Infographics Brochure PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting handling cyber threats digital era setting scenario for cybersecurity control ppt infographics brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management For Organization Essential Assets Addressing Cyber Threats In Various Industries Structure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a risk management for organization essential assets addressing cyber threats in various industries structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
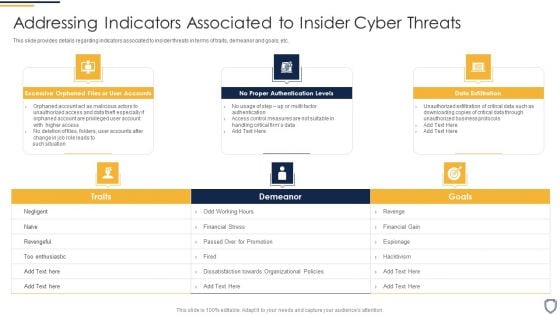
Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
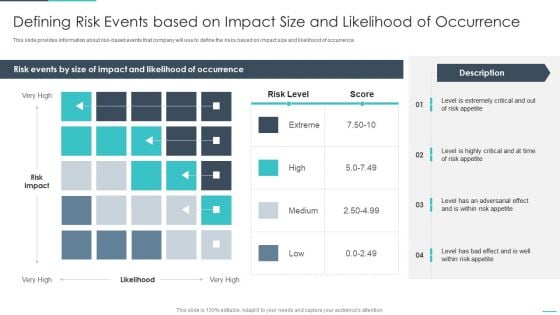
Handling Cyber Threats Digital Era Defining Risk Events Based On Impact Ppt Layouts Show PDF
This slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence. Deliver an awe inspiring pitch with this creative handling cyber threats digital era defining risk events based on impact ppt layouts show pdf bundle. Topics like defining risk events based on impact size and likelihood of occurrence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
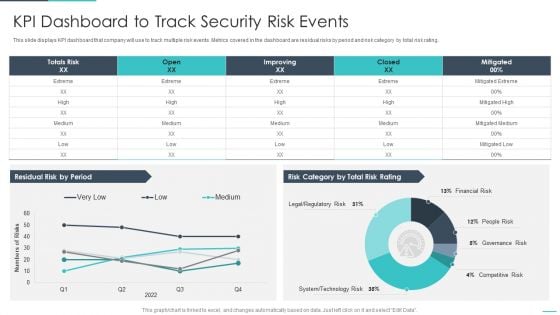
Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
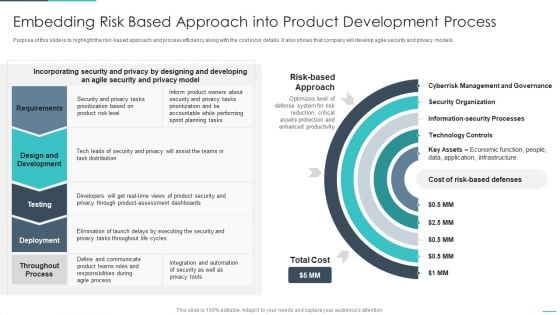
Handling Cyber Threats Digital Era Embedding Risk Based Approach Into Product Ppt Gallery Designs PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative handling cyber threats digital era embedding risk based approach into product ppt gallery designs pdf bundle. Topics like embedding risk based approach into product development process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Defining Business Priorities To Ensure Ppt Gallery Brochure PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting handling cyber threats digital era defining business priorities to ensure ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like efficient risk management, standardized incident management process, transparent communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats In A Digital Era Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This handling cyber threats in a digital era ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
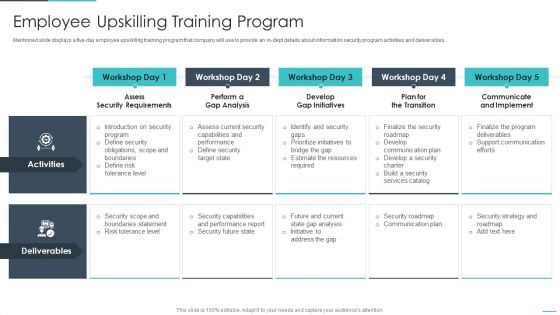
Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
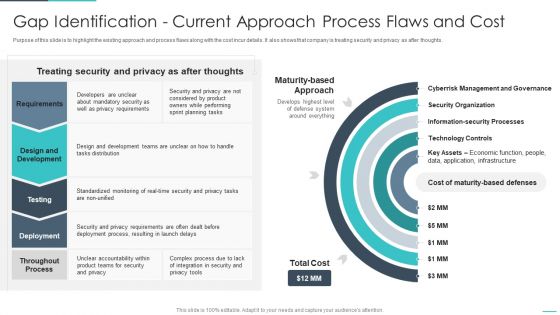
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Criticality Assessment Of Identified Assets Ppt Slides Backgrounds PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a handling cyber threats digital era criticality assessment of identified assets ppt slides backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extremely critical, reasonably critical, least critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
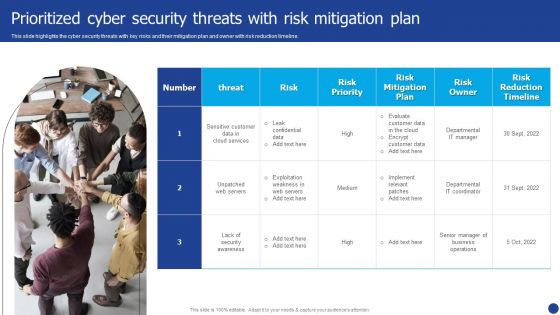
Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
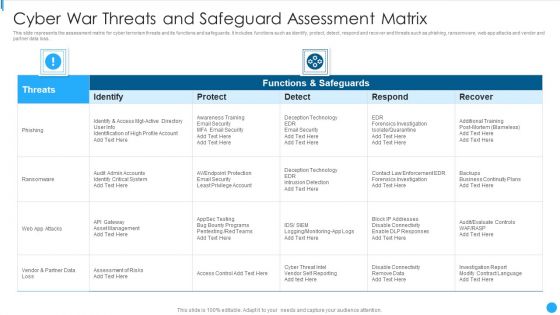
Cyber War Threats And Safeguard Assessment Matrix Summary PDF
This slide represents the assessment matrix for cyber terrorism threats and its functions and safeguards. It includes functions such as identify, protect, detect, respond and recover and threats such as phishing, ransomware, web app attacks and vendor and partner data loss.Showcasing this set of slides titled Cyber War Threats And Safeguard Assessment Matrix Summary PDF The topics addressed in these templates are Functions And Safeguards, Awareness Training, Forensics Investigation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Cyber War Threats With Risk Priority Summary PDF
This slide represents the five major threats caused by cyber terrorism along with their risk priorities. It includes threats such as malware, phishing, spear fishing, SQL injection and advanced persistent threats.Showcasing this set of slides titled Various Cyber War Threats With Risk Priority Summary PDF The topics addressed in these templates are Malicious Software, Includes Spywares, Ransomware Viruses All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
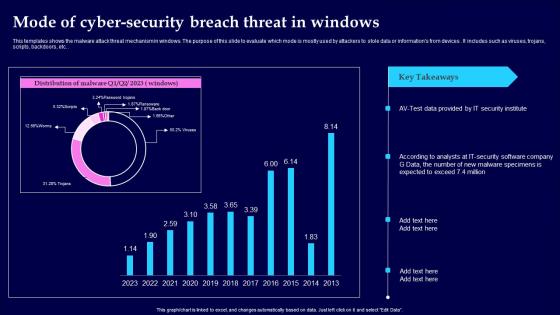
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
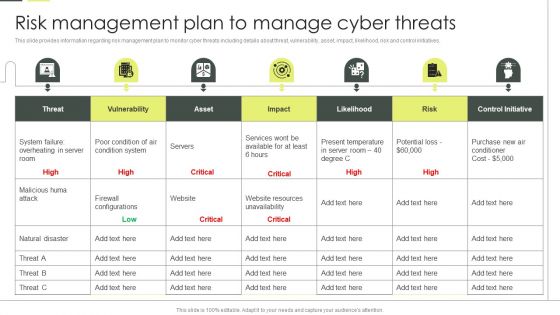
Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
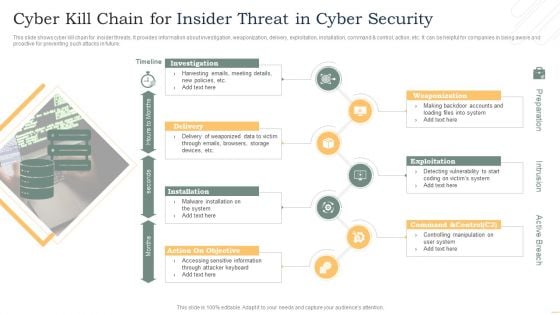
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Safety Incident Management Threat Management Action Plan Sample PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Threat Analysis Ppt PowerPoint Presentation Infographics Clipart Images Cpb
Presenting this set of slides with name cyber security threat analysis ppt powerpoint presentation infographics clipart images cpb. This is an editable Powerpoint three stages graphic that deals with topics like cyber security threat analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cyber Security Threat With Hacker Icon On The Screen Ppt PowerPoint Presentation Infographic Template PDF
Persuade your audience using this cyber security threat with hacker icon on the screen ppt powerpoint presentation infographic template pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security threat with hacker icon on the screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Password Protection For Cyber Security Threat Ppt PowerPoint Presentation Icon Show PDF
Persuade your audience using this password protection for cyber security threat ppt powerpoint presentation icon show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including password protection for cyber security threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
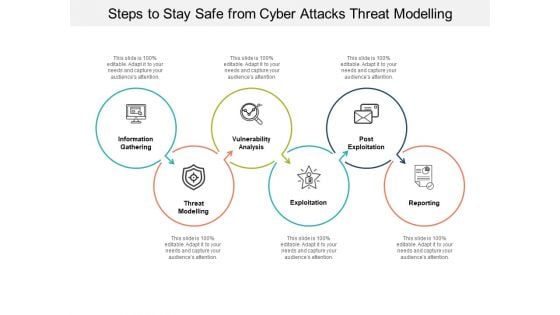
Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF
Introducing our well designed Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
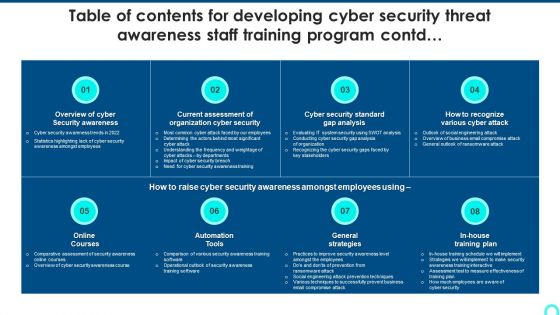
Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
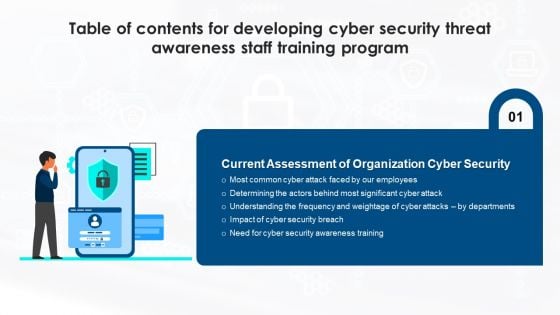
Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF. Use them to share invaluable insights on Current Assessment, Determining Actors, Understanding Frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Terrorism Assault Dashboard For Threat Tracking Of Cyber Terrorism Themes PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault dashboard for threat tracking of cyber terrorism themes pdf Use them to share invaluable insights on Massive Increase, Cyber Attacks Happened, Company Experienced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Cyber Security Threat Awareness Staff Training Program Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the seventy eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
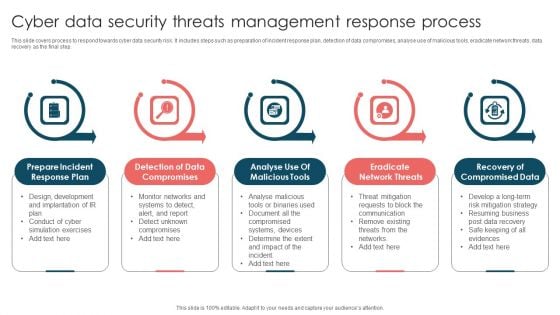
Cyber Data Security Threats Management Response Process Infographics PDF
This slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting Cyber Data Security Threats Management Response Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prepare Incident, Response Plan, Detection Data Compromises, Eradicate Network Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
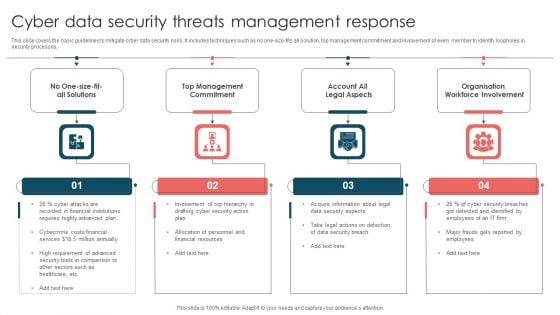
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
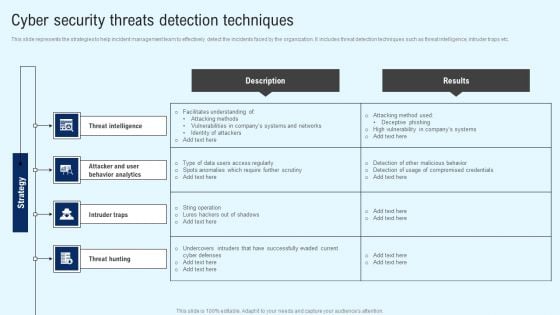
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.
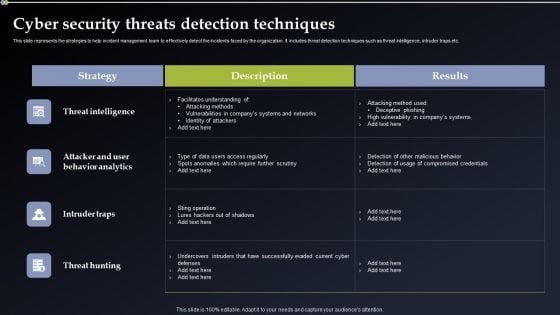
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
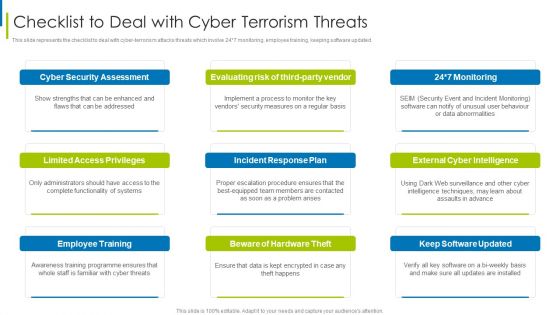
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home