Cybersecurity

Cybersecurity Ppt PowerPoint Presentation Complete With Slides
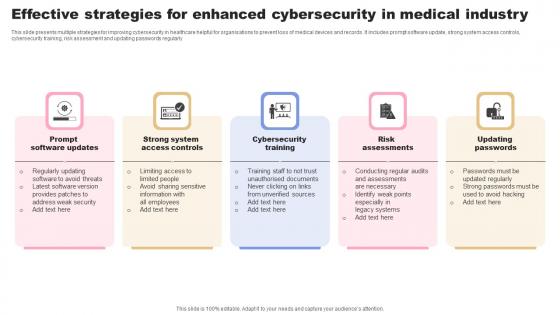
Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf
This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly Pitch your topic with ease and precision using this Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf. This layout presents information on Cybersecurity Training, Risk Assessments, Updating Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly
Icons Slide Cybersecurity Operations Cybersecops Slides PDF
Introducing our well designed Icons Slide Cybersecurity Operations Cybersecops Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Cybersecurity Awareness Communication Plan Icon Pictures Pdf
Pitch your topic with ease and precision using this Cybersecurity Awareness Communication Plan Icon Pictures Pdf This layout presents information on Cybersecurity Awareness, Communication Plan Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cybersecurity Awareness Communication Plan Icon Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cybersecurity Guidelines IT Cybersecurity Awareness Training For Staff Portrait PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Guidelines IT Cybersecurity Awareness Training For Staff Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Guidelines IT Cybersecurity Awareness Training For Staff Portrait PDF today and make your presentation stand out from the rest.
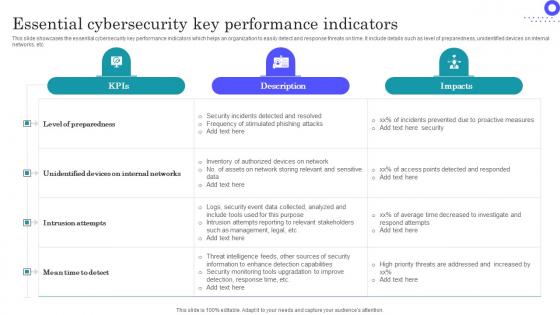
Essential Cybersecurity Key Performance Indicators Download Pdf
Showcasing this set of slides titled Essential Cybersecurity Key Performance Indicators Download Pdf The topics addressed in these templates are Level Preparedness, Internal Networks, Intrusion Attempts All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the essential cybersecurity key performance indicators which helps an organization to easily detect and response threats on time. It include details such as level of preparedness, unidentified devices on internal networks, etc.

NIST Cybersecurity Framework Best Practices Topics PDF
The slide highlights the best practices to be followed in order to overcome various implementation challenges of Nist framework for cyber security. It covers understand, automate, prioritize and talent acquisition. Persuade your audience using this NIST Cybersecurity Framework Best Practices Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Automate, Talent Acquisition. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cybersecurity Icons Slide For Cybersecurity Ppt Show Slide Portrait PDF
Presenting our innovatively structured cybersecurity icons slide for cybersecurity ppt show slide portrait pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Cybersecurity Risk Scorecard Timeline Inspiration PDF
This is a cybersecurity risk scorecard timeline inspiration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
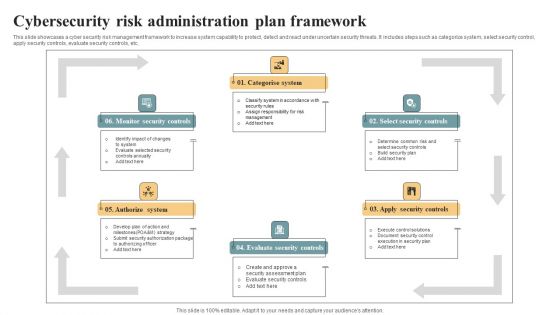
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
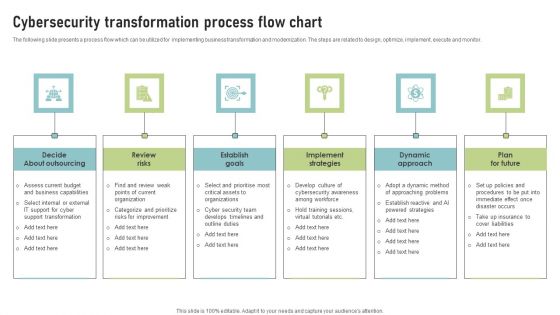
Cybersecurity Transformation Process Flow Chart Structure PDF
The following slide presents a process flow which can be utilized for implementing business transformation and modernization. The steps are related to design, optimize, implement, execute and monitor. Persuade your audience using this Cybersecurity Transformation Process Flow Chart Structure PDF. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Decide About Outsourcing, Review Risks, Establish Goals. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Table Of Contents For Cybersecurity Ppt Styles Graphics Design PDF
This is a cybersecurity table of contents for cybersecurity ppt styles graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, information security, requirement, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Leveraging Big Data Monitoring For Enhancing Cybersecurity Structure pdf
This slide highlights the benefits of leveraging big data analytics for improving cybersecurity within firm. The purpose of this slide is to help the company capitalize on the positive influence of big data analytics in improving cybersecurity. Showcasing this set of slides titled Leveraging Big Data Monitoring For Enhancing Cybersecurity Structure pdf. The topics addressed in these templates are Identifying And Preventing, Assessing Risks, Preventing Employee Breaches. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the benefits of leveraging big data analytics for improving cybersecurity within firm. The purpose of this slide is to help the company capitalize on the positive influence of big data analytics in improving cybersecurity.

Key Challenges To Medical Industry Cybersecurity Performance Background Pdf
This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness Showcasing this set of slides titled Key Challenges To Medical Industry Cybersecurity Performance Background Pdf. The topics addressed in these templates are Data Breaches, Service, Cloud Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cybersecurity Tips Ppt PowerPoint Presentation Gallery Example File
This is a cybersecurity tips ppt powerpoint presentation gallery example file. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.

Cybersecurity Risk Scorecard Roadmap Graphics PDF
This is a cybersecurity risk scorecard roadmap graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
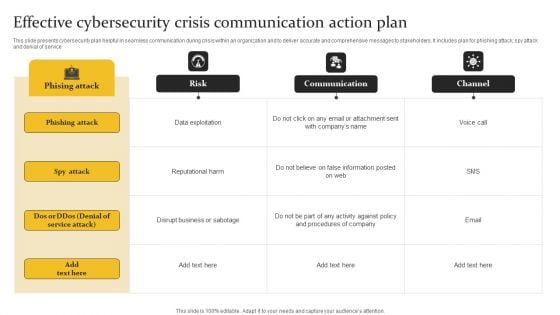
Effective Cybersecurity Crisis Communication Action Plan Graphics PDF
This slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Pitch your topic with ease and precision using this Effective Cybersecurity Crisis Communication Action Plan Graphics PDF. This layout presents information on Phishing Attack, Data Exploitation, Reputational Harm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
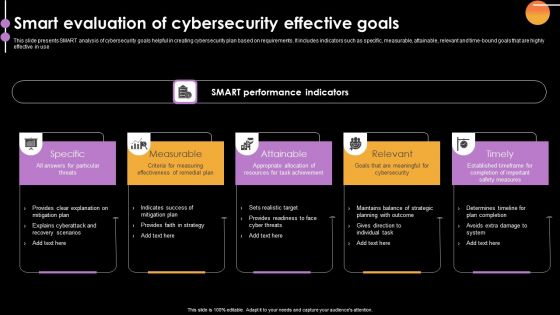
Smart Evaluation Of Cybersecurity Effective Goals Rules PDF
This slide presents SMART analysis of cybersecurity goals helpful in creating cybersecurity plan based on requirements. It includes indicators such as specific, measurable, attainable, relevant and time-bound goals that are highly effective in use. Presenting Smart Evaluation Of Cybersecurity Effective Goals Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Specific, Measurable, Attainable. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
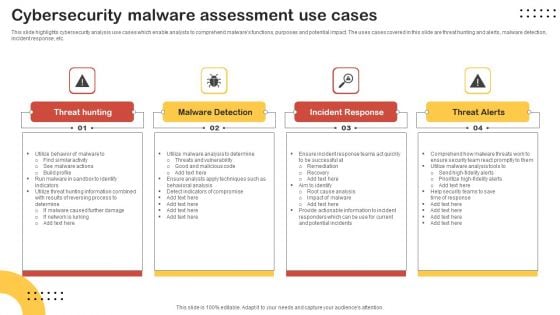
Cybersecurity Malware Assessment Use Cases Download PDF
This slide highlights cybersecurity analysis use cases which enable analysts to comprehend malwares functions, purposes and potential impact. The uses cases covered in this slide are threat hunting and alerts, malware detection, incident response, etc. Presenting Cybersecurity Malware Assessment Use Cases Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Threat Hunting, Malware Detection, Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
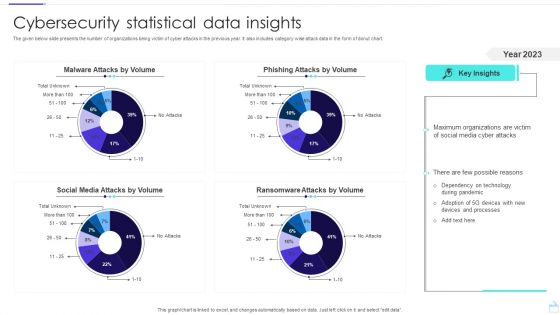
Cybersecurity Statistical Data Insights Sample PDF
The given below slide presents the number of organizations being victim of cyber attacks in the previous year. It also includes category wise attack data in the form of donut chart. Pitch your topic with ease and precision using this Cybersecurity Statistical Data Insights Sample PDF. This layout presents information on Social Media Attacks, Malware Attacks, Phishing Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
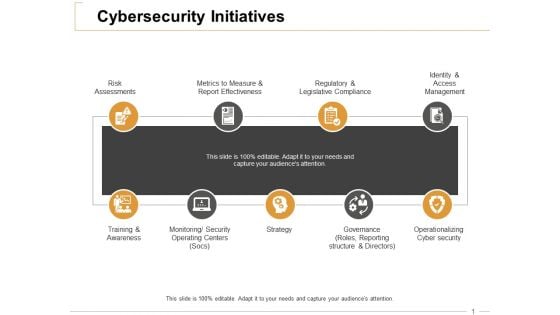
Cybersecurity Initiatives Ppt PowerPoint Presentation Outline Information
This is a cybersecurity initiatives ppt powerpoint presentation outline information. This is a nine stage process. The stages in this process are risk assessments, training and awareness, strategy, operationalizing cyber security, regulatory and legislative compliance.

Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF
Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF.
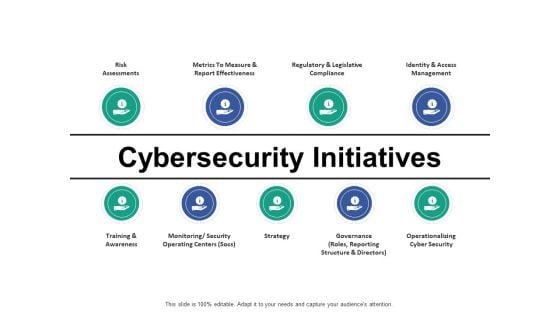
Cybersecurity Initiatives Ppt PowerPoint Presentation Layouts Slideshow
This is a cybersecurity initiatives ppt powerpoint presentation layouts slideshow. This is a nine stage process. The stages in this process are business, management, planning, strategy, marketing.
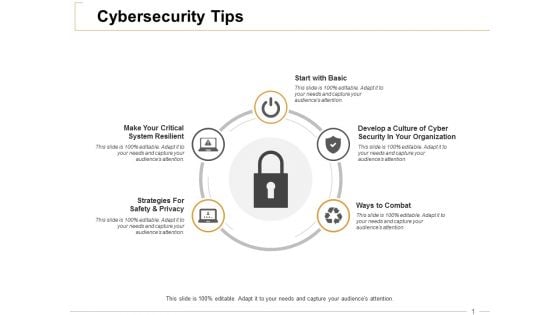
Cybersecurity Tips Ppt PowerPoint Presentation File Outfit
This is a cybersecurity tips ppt powerpoint presentation file outfit. This is a five stage process. The stages in this process are business, management, planning, strategy, marketing.
IOT Biometric Cybersecurity Management Icon Guidelines Pdf
Pitch your topic with ease and precision using this IOT Biometric Cybersecurity Management Icon Guidelines Pdf This layout presents information on IOT Biometric Cybersecurity, Management Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our IOT Biometric Cybersecurity Management Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cybersecurity Framework Ppt PowerPoint Presentation Picture
This is a cybersecurity framework ppt powerpoint presentation picture. This is a five stage process. The stages in this process are business, management, planning, strategy, marketing.

Cybersecurity Framework Ppt PowerPoint Presentation Professional Designs
This is a cybersecurity framework ppt powerpoint presentation professional designs. This is a five stage process. The stages in this process are product, detect, respond, recover, identify.
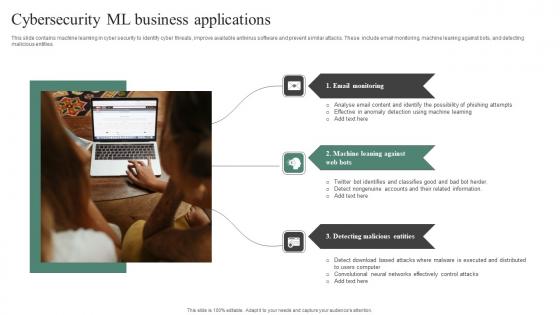
Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities.
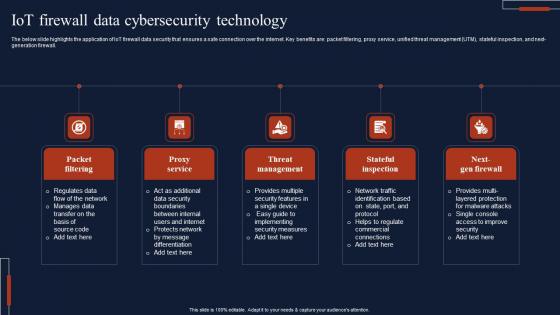
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.

Agenda For Cybersecurity Ppt Model Layouts PDF
This is a agenda for cybersecurity ppt model layouts pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, systems, cybersecurity, plan, strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
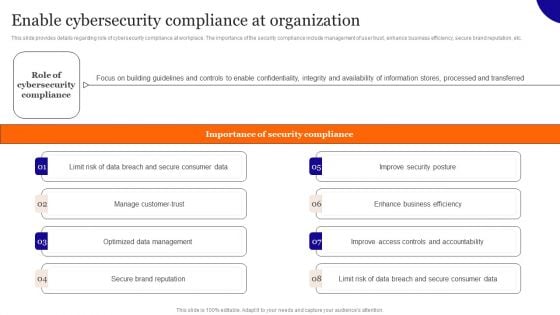
Enable Cybersecurity Compliance At Organization Mockup PDF
This slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enable Cybersecurity Compliance At Organization Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Cybersecurity Risk Scorecard Circular Process Introduction PDF
This is a cybersecurity risk scorecard circular process introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like circular process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Risk Scorecard Comparison Slides PDF
This is a cybersecurity risk scorecard comparison slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Risk Scorecard Financial Formats PDF
This is a cybersecurity risk scorecard financial formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimum, medium, maximum. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Scorecard Linear Process Infographics PDF
This is a cybersecurity risk scorecard linear process infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like linear process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda Cybersecurity Operations Cybersecops Slides PDF
Find a pre designed and impeccable Agenda Cybersecurity Operations Cybersecops Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
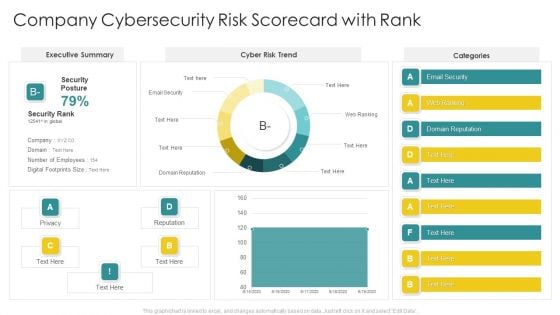
Cybersecurity Risk Scorecard Company Cybersecurity Risk Scorecard With Rank Inspiration PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard company cybersecurity risk scorecard with rank inspiration pdf bundle. Topics like company cybersecurity risk scorecard with rank can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
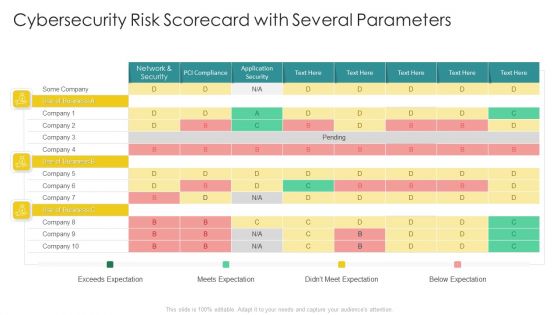
Cybersecurity Risk Scorecard Cybersecurity Risk Scorecard With Several Parameters Elements PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard cybersecurity risk scorecard with several parameters elements pdf bundle. Topics like cybersecurity risk scorecard with several parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Table Of Contents For Cybersecurity Business Ppt Outline Guidelines PDF
Presenting cybersecurity table of contents for cybersecurity business ppt outline guidelines pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like information security, implementing, dashboards, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
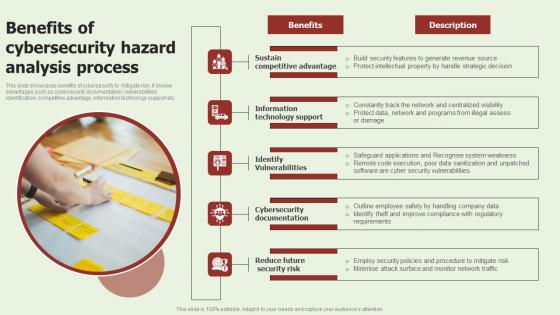
Benefits Of Cybersecurity Hazard Analysis Process Template Pdf
This slide showcases benefits of cybersecurity to mitigate risk. It involve advantages such as cybersecurity documentation, vulnerabilities identification, competitive advantage, information technology support etc. Pitch your topic with ease and precision using this Benefits Of Cybersecurity Hazard Analysis Process Template Pdf. This layout presents information on Sustain Competitive Advantage, Information Technology Support, Identify Vulnerabilities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases benefits of cybersecurity to mitigate risk. It involve advantages such as cybersecurity documentation, vulnerabilities identification, competitive advantage, information technology support etc.
Cybersecurity Icon In Medical Industry Insurance Guidelines Pdf
Showcasing this set of slides titled Cybersecurity Icon In Medical Industry Insurance Guidelines Pdf. The topics addressed in these templates are Cybersecurity, Medical Industry, Insurance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cybersecurity Icon In Medical Industry Insurance Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc.
Cybersecurity Emergency Response Communication Plan Icon Inspiration Pdf
Pitch your topic with ease and precision using this Cybersecurity Emergency Response Communication Plan Icon Inspiration Pdf This layout presents information on Cybersecurity Emergency Response, Communication Plan Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cybersecurity Emergency Response Communication Plan Icon Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cybersecurity Icon In Medical Industry Mobile Application Guidelines Pdf
Pitch your topic with ease and precision using this Cybersecurity Icon In Medical Industry Mobile Application Guidelines Pdf. This layout presents information on Cybersecurity, Medical Industry, Mobile Application. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cybersecurity Icon In Medical Industry Mobile Application Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection.
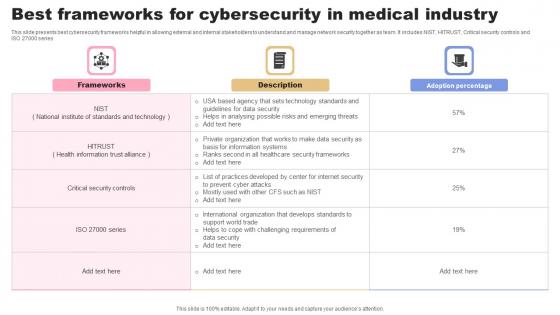
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
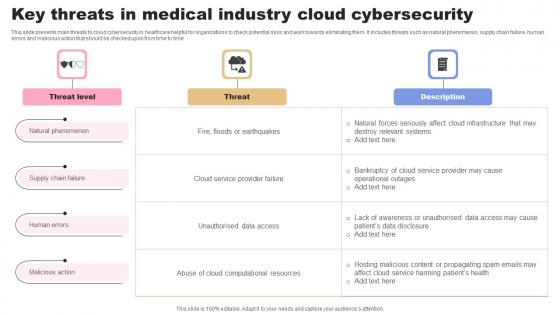
Key Threats In Medical Industry Cloud Cybersecurity Background Pdf
This slide presents main threats to cloud cybersecurity in healthcare helpful for organizations to check potential risks and work towards eliminating them. It includes threats such as natural phenomenon, supply chain failure, human errors and malicious action that should be checked upon from time to time Pitch your topic with ease and precision using this Key Threats In Medical Industry Cloud Cybersecurity Background Pdf. This layout presents information on Threat Level, Threat, Description. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main threats to cloud cybersecurity in healthcare helpful for organizations to check potential risks and work towards eliminating them. It includes threats such as natural phenomenon, supply chain failure, human errors and malicious action that should be checked upon from time to time
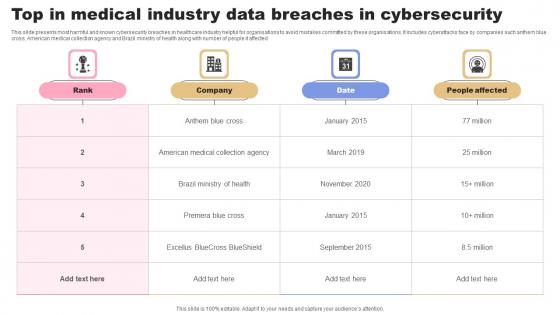
Top In Medical Industry Data Breaches In Cybersecurity Graphics Pdf
This slide presents most harmful and known cybersecurity breaches in healthcare industry helpful for organisations to avoid mistakes committed by these organisations. It includes cyberattacks face by companies such anthem blue cross, American medical collection agency and Brazil ministry of health along with number of people it affected Showcasing this set of slides titled Top In Medical Industry Data Breaches In Cybersecurity Graphics Pdf. The topics addressed in these templates are Rank, Company, Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents most harmful and known cybersecurity breaches in healthcare industry helpful for organisations to avoid mistakes committed by these organisations. It includes cyberattacks face by companies such anthem blue cross, American medical collection agency and Brazil ministry of health along with number of people it affected

Compliance Standards For Effective Cybersecurity In Medical Industry Guidelines Pdf
This slide presents compliance standards for effective application of cybersecurity in healthcare helpful for providing patients more control over health information and defining baseline of minimum requirements for organisations. It includes HIPAA, GDPR, PIPEDA Pitch your topic with ease and precision using this Compliance Standards For Effective Cybersecurity In Medical Industry Guidelines Pdf. This layout presents information on Compliance Standards, Description, Covered. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents compliance standards for effective application of cybersecurity in healthcare helpful for providing patients more control over health information and defining baseline of minimum requirements for organisations. It includes HIPAA, GDPR, PIPEDA

Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf
This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption Showcasing this set of slides titled Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf. The topics addressed in these templates are Factors, Description, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption

Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf
Showcasing this set of slides titled Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf The topics addressed in these templates are Organizations Network, Security Assessments, Provides Privileged All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the benefits of using cybersecurity key performance indicators which help an organization to provide a snapshot to its relevant stakeholders, managers. It include details such as removes unknown devices on an organizations network, etc.
Cybersecurity Key Performance Indicator And Padlock Icon Clipart Pdf
Showcasing this set of slides titled Cybersecurity Key Performance Indicator And Padlock Icon Clipart Pdf The topics addressed in these templates are Cybersecurity Key, Performance Indicator, Padlock Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cybersecurity Key Performance Indicator And Padlock Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
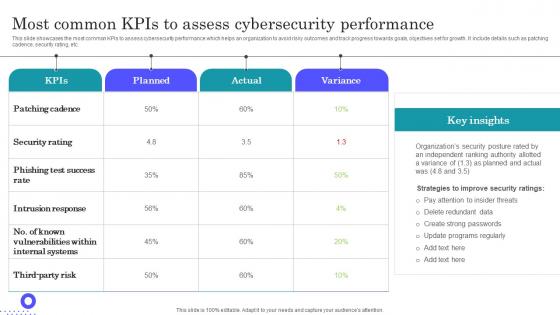
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.

Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf
This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.Showcasing this set of slides titled Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf The topics addressed in these templates are Network Safety, Awareness Education, Secure Construction All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.
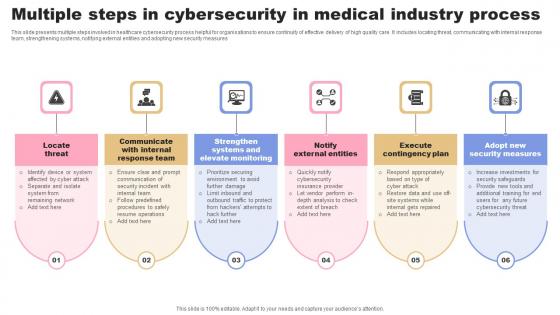
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures
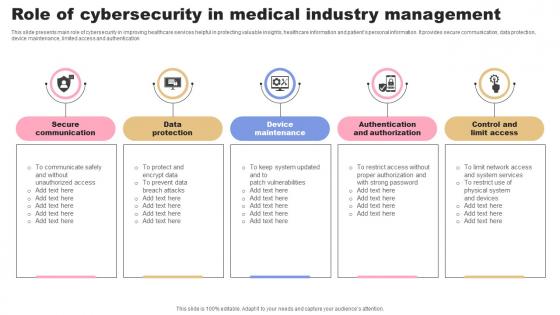
Role Of Cybersecurity In Medical Industry Management Rules Pdf
This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication Pitch your topic with ease and precision using this Role Of Cybersecurity In Medical Industry Management Rules Pdf. This layout presents information on Secure Communication, Data Protection, Maintenance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication

 Home
Home