Data Privacy
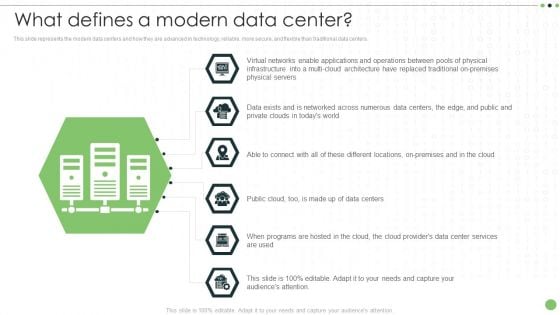
Different Categories Of Data Centers What Defines A Modern Data Center Ideas PDF
This slide represents the modern data centers and how they are advanced in technology, reliable, more secure, and flexible than traditional data centers. Retrieve professionally designed Different Categories Of Data Centers What Defines A Modern Data Center Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
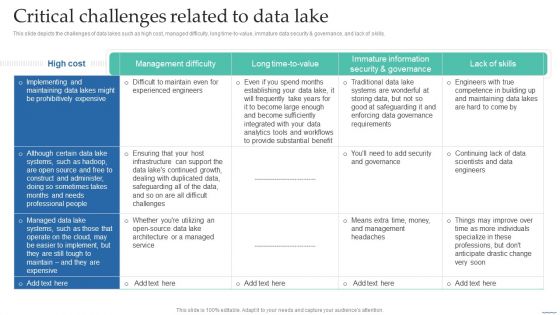
Critical Challenges Related To Data Lake Data Lake Creation With Hadoop Cluster Inspiration PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security governance, and lack of skills.Do you know about Slidesgeeks Critical Challenges Related To Data Lake Data Lake Creation With Hadoop Cluster Inspiration PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

IT Professional Data Certification Program Certified Data Professional Program CDP Summary PDF
This slide covers the CDP course details such as CDP Benefits, Who should become CDP, salary expectations, International Standards for CDP Program etc. This is a IT Professional Data Certification Program Certified Data Professional Program CDP Summary PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Benefits, System Security, Risk Assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
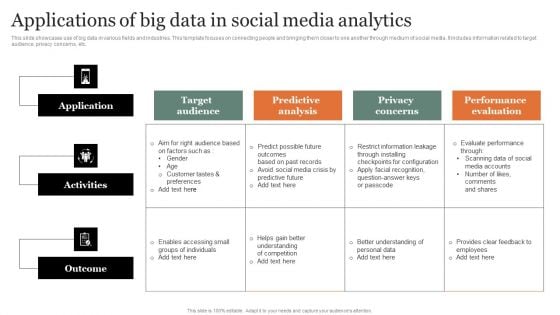
Applications Of Big Data In Social Media Analytics Graphics PDF
This slide showcases use of big data in various fields and industries. This template focuses on connecting people and bringing them closer to one another through medium of social media. It includes information related to target audience, privacy concerns, etc. Showcasing this set of slides titled Applications Of Big Data In Social Media Analytics Graphics PDF Brochure. The topics addressed in these templates are Target Audience, Predictive Analysis, Performance Evaluation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Focus Areas Of Business Data Management Ethics Ppt Infographic Template Vector PDF
This slide shows six elements to be considered by business organizations in data ethics. These are ownership, transaction transparency, consent, privacy, currency and openness. Presenting Key Focus Areas Of Business Data Management Ethics Ppt Infographic Template Vector PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Ownership, Privacy, Currency, Transaction Transparency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
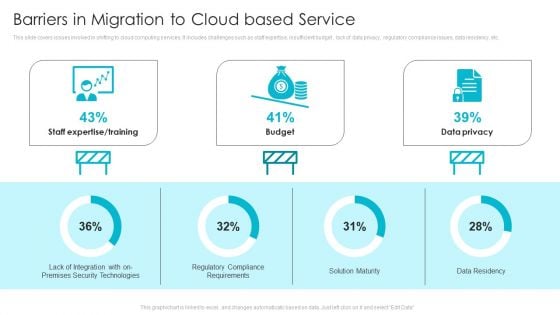
Barriers In Migration To Cloud Based Service Ppt File Templates PDF
This slide covers issues involved in shifting to cloud computing services. It includes challenges such as staff expertise, insufficient budget , lack of data privacy, regulatory compliance issues, data residency, etc. Showcasing this set of slides titled Barriers In Migration To Cloud Based Service Ppt File Templates PDF. The topics addressed in these templates are Staff Expertise, Training, Budget, Data Privacy, Solution Maturity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Database Marketing Tactics To Optimize Campaigns Ppt Portfolio Maker Pdf
This slide includes effective strategies to optimize database marketing campaigns. It includes identify target market, cooperate with other departments, select optimum software, ensure right balance, and respect customer data privacy. Pitch your topic with ease and precision using this Database Marketing Tactics To Optimize Campaigns Ppt Portfolio Maker Pdf. This layout presents information on Select Optimum Software, Ensure Right Balance, Respect Customer, Data Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide includes effective strategies to optimize database marketing campaigns. It includes identify target market, cooperate with other departments, select optimum software, ensure right balance, and respect customer data privacy.
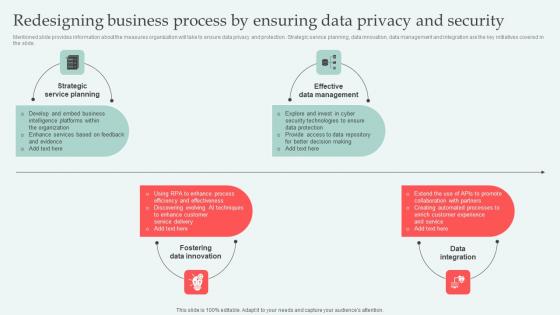
Redesigning Business Process Digital Approaches To Increase Business Growth Mockup Pdf
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Explore a selection of the finest Redesigning Business Process Digital Approaches To Increase Business Growth Mockup Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Redesigning Business Process Digital Approaches To Increase Business Growth Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide.
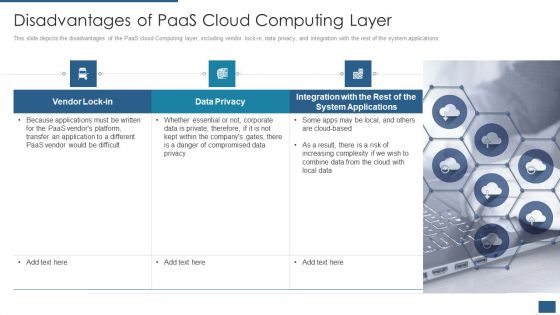
Cloud Computing Service Models IT Disadvantages Of Paas Cloud Computing Layer Rules PDF
This slide depicts the disadvantages of the PaaS cloud Computing layer, including vendor lock-in, data privacy, and integration with the rest of the system applications. This is a cloud computing service models it disadvantages of paas cloud computing layer rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vendor lock in, data privacy, integration with the rest of the system applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Distribution Service Models Disadvantages Of Paas Cloud Computing Layer Icons PDF
This slide depicts the disadvantages of the PaaS cloud Computing layer, including vendor lock-in, data privacy, and integration with the rest of the system applications. Presenting Cloud Distribution Service Models Disadvantages Of Paas Cloud Computing Layer Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data Privacy, System Applications, Vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
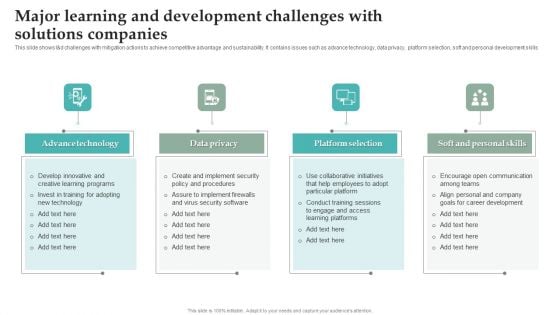
Major Learning And Development Challenges With Solutions Companies Microsoft PDF
This slide shows l and d challenges with mitigation actions to achieve competitive advantage and sustainability. It contains issues such as advance technology, data privacy, platform selection, soft and personal development skills. Presenting Major Learning And Development Challenges With Solutions Companies Microsoft PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Advance Technology, Data Privacy, Platform Selection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
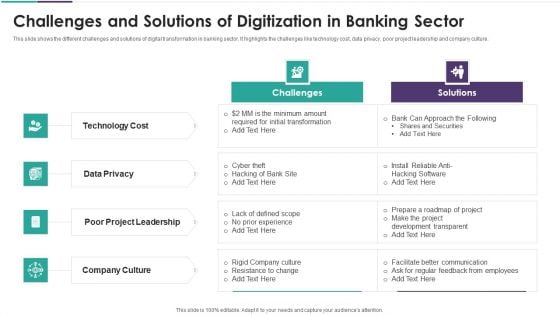
Challenges And Solutions Of Digitization In Banking Sector Background PDF
This slide shows the different challenges and solutions of digital transformation in banking sector. It highlights the challenges like technology cost, data privacy, poor project leadership and company culture. Presenting challenges and solutions of digitization in banking sector background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data privacy, technology cost, company culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
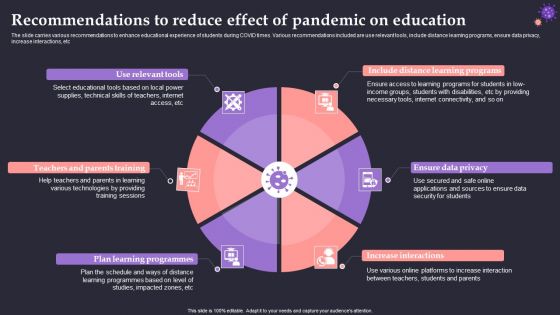
Recommendations To Reduce Effect Of Pandemic On Education Brochure PDF
The slide carries various recommendations to enhance educational experience of students during COVID times. Various recommendations included are use relevant tools, include distance learning programs, ensure data privacy, increase interactions, etc. Persuade your audience using this Recommendations To Reduce Effect Of Pandemic On Education Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Use Relevant Tools, Ensure Data Privacy, Increase Interactions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
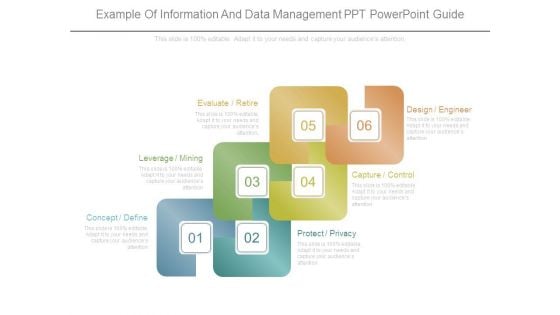
Example Of Information And Data Management Ppt Powerpoint Guide
This is a example of information and data management ppt powerpoint guide. This is a six stage process. The stages in this process are concept define, leverage mining, evaluate retire, design engineer, capture control, protect privacy.
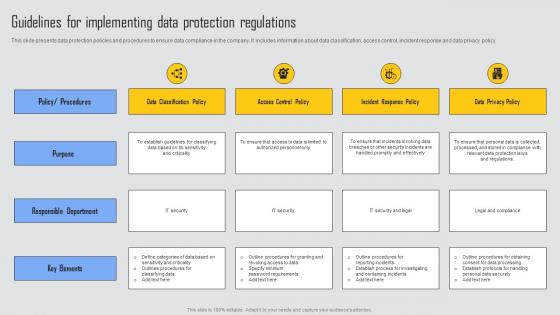
Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf
This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf today and make your presentation stand out from the rest This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy.
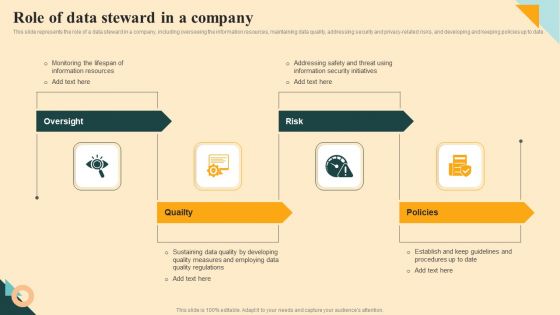
Role Of Data Steward In A Company Guidelines PDF
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy-related risks, and developing and keeping policies up to date. The Role Of Data Steward In A Company Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
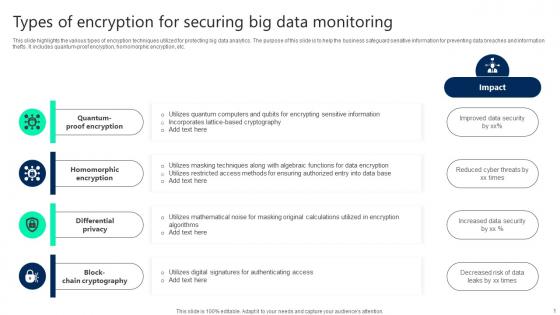
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
Data And Customer Analysis Company Outline Our Values Portrait PDF

Impact Of Big Data In World Ppt PowerPoint Presentation Inspiration
This is a impact of big data in world ppt powerpoint presentation inspiration. This is a four stage process. The stages in this process are healthcare, science, security, business.
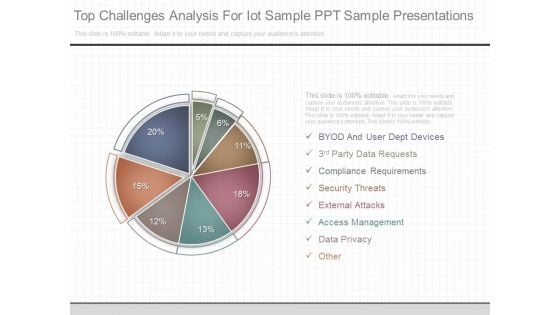
Top Challenges Analysis For Iot Sample Ppt Sample Presentations
This is a top challenges analysis for iot sample ppt sample presentations. This is a eight stage process. The stages in this process are byod and user dept devices, 3rd party data requests, compliance requirements, security threats, external attacks, access management, data privacy, other.
Financial Enterprise Data Governance Plan Ppt Icon Visuals PDF
This slide showcases an ideal structure to utilize data within the organization to ensure security and reliability of data in enterprises according to the data usage policies and standards. The key strategies include identify data source, define data, standardize data and data handling. Persuade your audience using this Financial Enterprise Data Governance Plan Ppt Icon Visuals PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Identify Data Source, Define Data, Standardize Data, Data Handling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
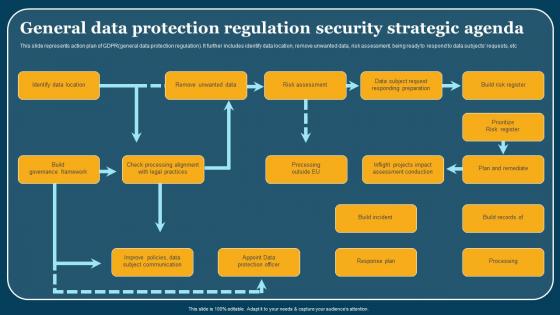
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc.
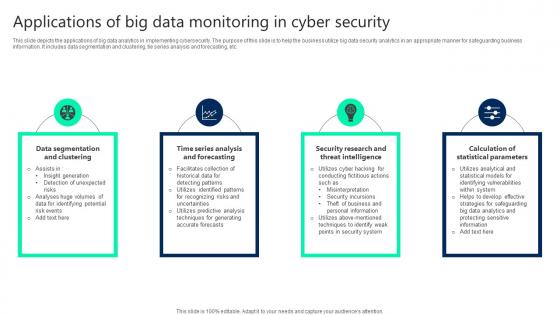
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
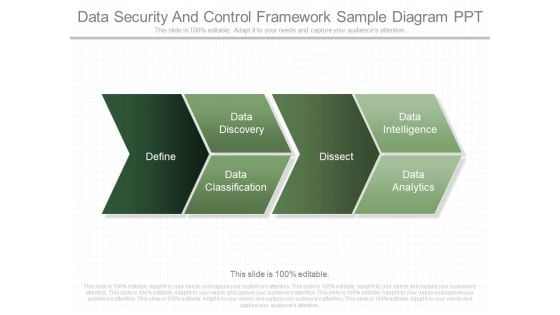
Data Security And Control Framework Sample Diagram Ppt
This is a data security and control framework sample diagram ppt. This is a four stage process. The stages in this process are define, data classification, data discovery, dissect, data intelligence, data analytics.
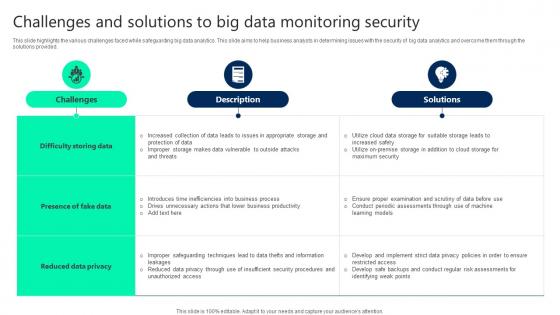
Challenges And Solutions To Big Data Monitoring Security Slides pdf
This slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided. Showcasing this set of slides titled Challenges And Solutions To Big Data Monitoring Security Slides pdf. The topics addressed in these templates are Challenges, Solutions, Difficulty Storing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided.
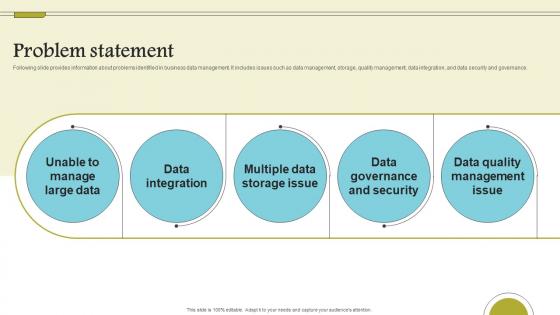
Problem Statement Cloud Data Computing Company Fund Raising Background PDF
Following slide provides information about problems identified in business data management. It includes issues such as data management, storage, quality management, data integration, and data security and governance. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Cloud Data Computing Company Fund Raising Background PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Cloud Data Computing Company Fund Raising Background PDF Following slide provides information about problems identified in business data management. It includes issues such as data management, storage, quality management, data integration, and data security and governance.

Distributed Ledger Technology Impact On Data Security Infographics Pdf
This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking Pitch your topic with ease and precision using this Distributed Ledger Technology Impact On Data Security Infographics Pdf This layout presents information on Encryption And Validation, Decentralized Data Security, Difficulties In Hacking It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking
Data Security Strategic Agenda Checklist Icon Mockup Pdf
Pitch your topic with ease and precision using this Data Security Strategic Agenda Checklist Icon Mockup Pdf. This layout presents information on Data Security Strategic, Agenda Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Strategic Agenda Checklist Icon Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
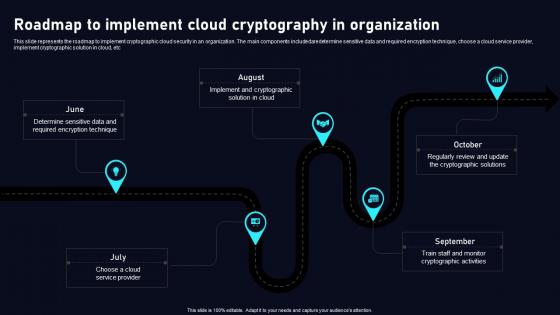
Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf today and make your presentation stand out from the rest This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc
Cloud Computing Engineering Data Security Service Icon Portrait Pdf
Showcasing this set of slides titled Cloud Computing Engineering Data Security Service Icon Portrait Pdf The topics addressed in these templates are Cloud Computing, Engineering Data Security, Service Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Computing Engineering Data Security Service Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
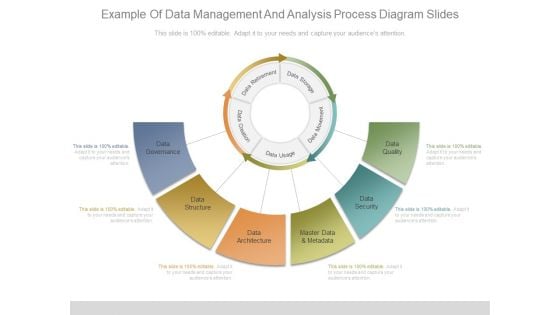
Example Of Data Management And Analysis Process Diagram Slides
Presenting this set of slides with name example of data management and analysis process diagram slides. This is a six stage process. The stages in this process are data governance, data structure, data architecture, master data and metadata, data security, data quality. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
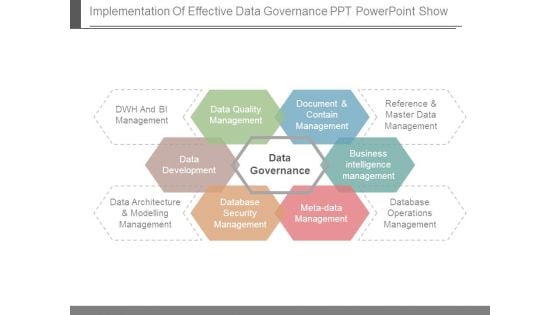
Implementation Of Effective Data Governance Ppt Powerpoint Show
This is a implementation of effective data governance ppt powerpoint show. This is a six stage process. The stages in this process are dwh and bi management, data quality management, document and contain management, reference and master data management, business intelligence management, database operations management, meta data management, database security management, data architecture and modelling management, data development, data governance.
Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf
Showcasing this set of slides titled Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf. The topics addressed in these templates are Effective Use, Big Data Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.
Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf
Introducing our well designed Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
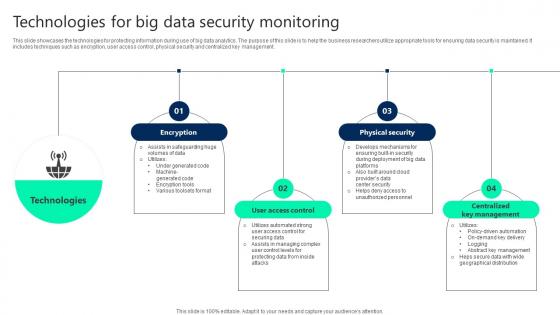
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.
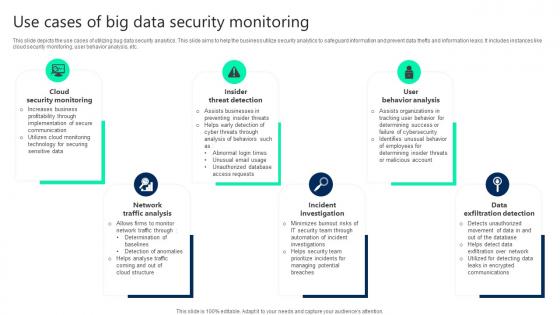
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc.
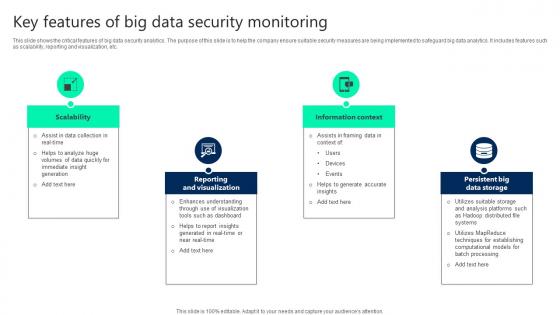
Key Features Of Big Data Security Monitoring Ideas pdf
This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Pitch your topic with ease and precision using this Key Features Of Big Data Security Monitoring Ideas pdf. This layout presents information on Scalability, Reporting And Visualization, Information Context. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc.
Data Breach Security Communication Plan Icon Demonstration Pdf
Showcasing this set of slides titled Data Breach Security Communication Plan Icon Demonstration Pdf The topics addressed in these templates are Data Breach, Security Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Data Breach Security Communication Plan Icon Demonstration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Internet Security And Data Audit Icon Pictures Pdf
Pitch your topic with ease and precision using this Internet Security And Data Audit Icon Pictures Pdf This layout presents information on Internet Security, Data Audit Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Security And Data Audit Icon Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
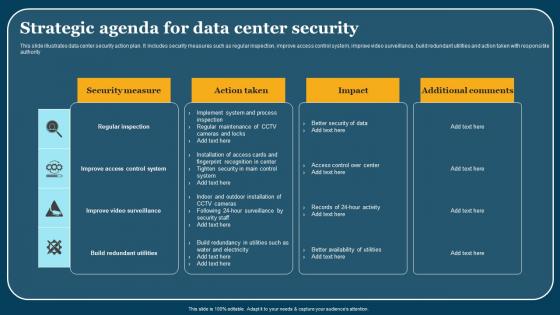
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.
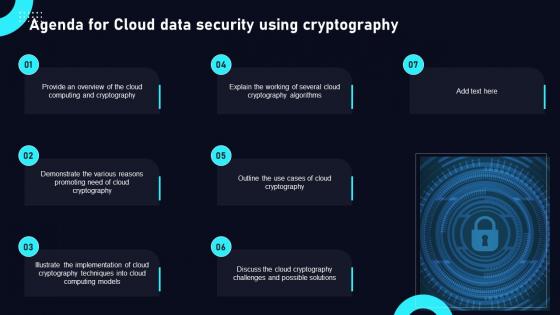
Agenda For Cloud Data Security Using Cryptography Structure Pdf
Find highly impressive Agenda For Cloud Data Security Using Cryptography Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Cloud Data Security Using Cryptography Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Agenda For Cloud Data Security Using Cryptography Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Major Data Quality Control Issues For Organizations Portrait PDF
The following slide highlights the quality control issues which includes duplicate data, unstructured data, security issues, hidden data and inaccurate data. Presenting major data quality control issues for organizations portrait pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including duplicate data, unstructured data, security issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Strategic Agenda For Data Protection Icon Template Pdf
Pitch your topic with ease and precision using this Cyber Security Strategic Agenda For Data Protection Icon Template Pdf. This layout presents information on Cyber Security Strategic, Agenda For Data Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Strategic Agenda For Data Protection Icon Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Enablement Framework And Security Training Program Icons PDF
This slide illustrates three day training workshop for data enablement and data security. It includes audience, objectives, data governance, data security, etc. Presenting Data Enablement Framework And Security Training Program Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Data Foundation, Security Model Introduction, User Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Types Data Security Ppt PowerPoint Presentation Styles Objects Cpb
This is a types data security ppt powerpoint presentation styles objects cpb. This is a ten stage process. The stages in this process are types data security.
Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf
This modern and well arranged Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.
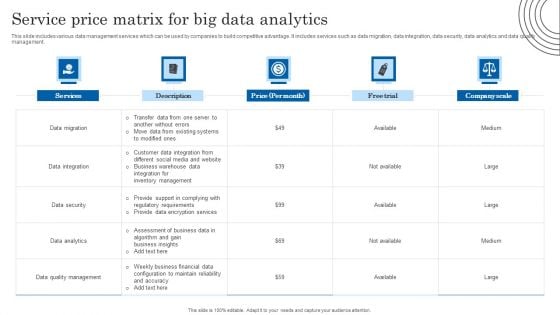
Service Price Matrix For Big Data Analytics Themes PDF
This slide includes various data management services which can be used by companies to build competitive advantage. It includes services such as data migration, data integration, data security, data analytics and data quality management. Pitch your topic with ease and precision using this Service Price Matrix For Big Data Analytics Themes PDF. This layout presents information on Assessment Of Business, Financial Data, Data Quality Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
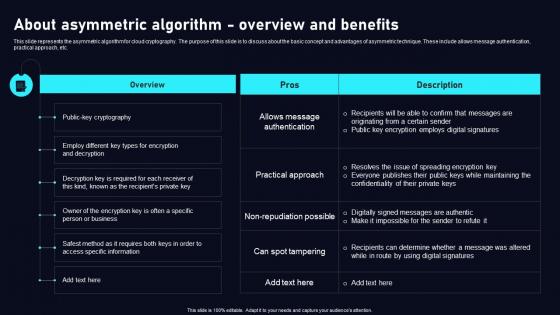
About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Get a simple yet stunning designed About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.
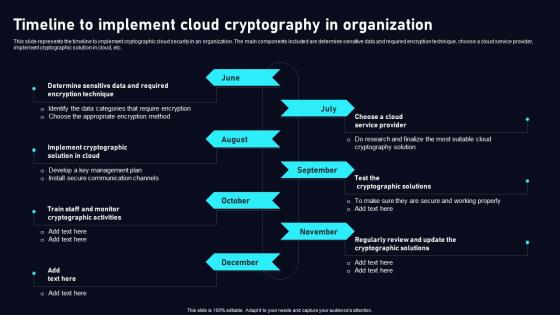
Timeline To Implement Cloud Data Security Using Cryptography Download Pdf
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Timeline To Implement Cloud Data Security Using Cryptography Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
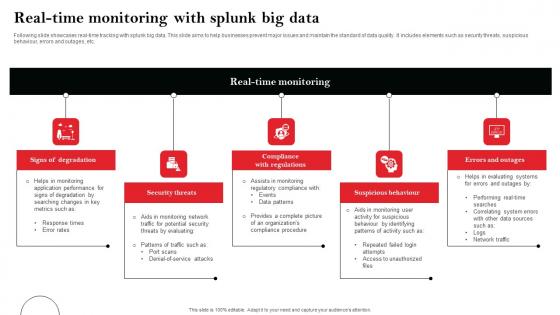
Real Time Monitoring With Splunk Big Data Diagrams Pdf
Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc. Pitch your topic with ease and precision using this Real Time Monitoring With Splunk Big Data Diagrams Pdf This layout presents information on Signs Of Degradation, Security Threats, Errors And Outages It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.

Data Security Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with internet data security with fiber optical Slide Create a flow with our Data Security Internet PowerPoint Themes And PowerPoint Slides 0511. Your thoughts will be coasting along.

Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with internet data security with fiber optical background Our Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511 have just about everything. Just think of it and you'll find it in them.

Key Drivers Of Data Protection And Security Mechanism Infographics PDF
The following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow.Presenting Key Drivers Of Data Protection And Security Mechanism Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Location, Data Sensitivity, Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home