Data Security
Architect Trade Cyber Security Data Ppt PowerPoint Presentation Gallery Layouts
This is a architect trade cyber security data ppt powerpoint presentation gallery layouts. This is a four stage process. The stages in this process are architect trade, cyber security data.

Companys Data Safety Recognition Security Awareness Training Roadmap Themes PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a companys data safety recognition security awareness training roadmap themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical security, data security, personal information, privacy threats, practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
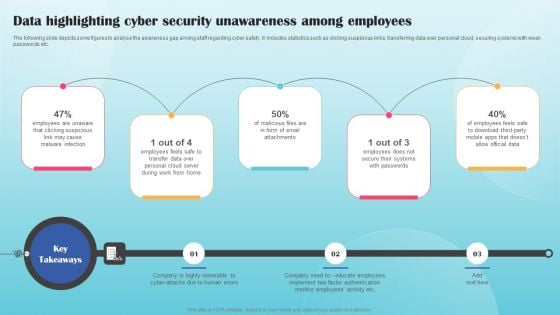
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
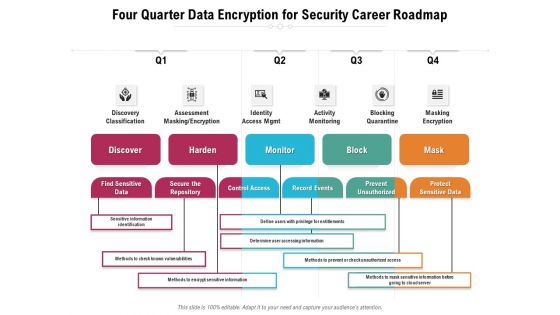
Four Quarter Data Encryption For Security Career Roadmap Sample
We present our four quarter data encryption for security career roadmap sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched four quarter data encryption for security career roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Companys Data Safety Recognition Security Awareness Program Checklist Portrait PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a companys data safety recognition security awareness program checklist portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, security awareness program, sustaining security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
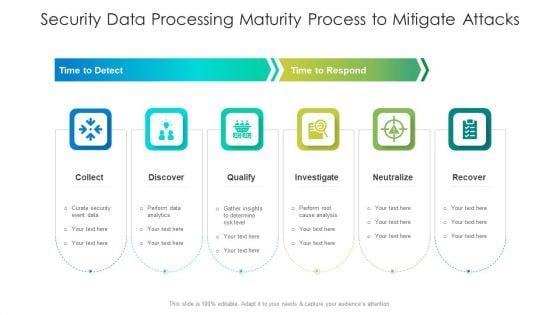
Security Data Processing Maturity Process To Mitigate Attacks Ideas PDF
Persuade your audience using this security data processing maturity process to mitigate attacks ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including qualify, analysis, determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Companys Data Safety Recognition Security Awareness Tracking Kpis Ideas PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
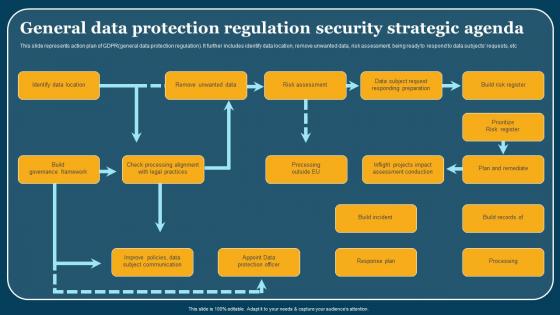
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Companys Data Safety Recognition Security Training Program Frameworks Icons PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative companys data safety recognition security training program frameworks icons pdf bundle. Topics like requirements, target audience, metrics, training materials can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Year Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured five year data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
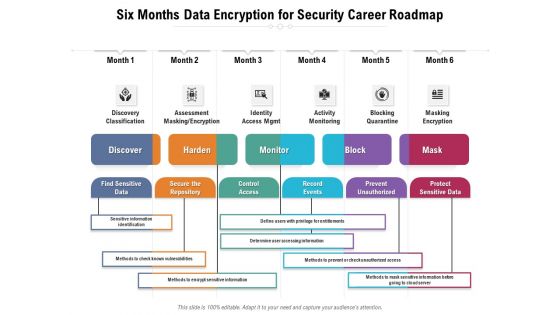
Six Months Data Encryption For Security Career Roadmap Structure
Presenting our innovatively-structured six months data encryption for security career roadmap structure Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
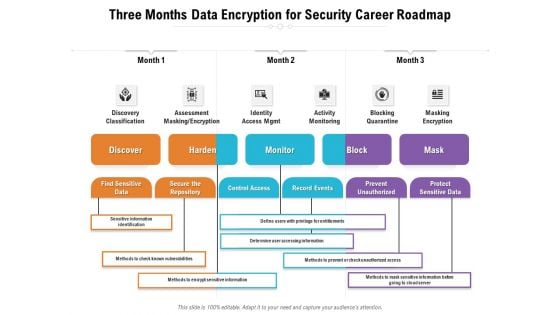
Three Months Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured three months data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly Data Encryption For Security Career Roadmap Structure
Presenting our jaw-dropping half yearly data encryption for security career roadmap structure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Key Drivers Of Data Protection And Security Mechanism Infographics PDF
The following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow.Presenting Key Drivers Of Data Protection And Security Mechanism Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Location, Data Sensitivity, Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Data Privacy In Educational Institutions Introduction PDF
This slide depicts data privacy in educational Information , institutions should issue a notice period of two days for approval before disclosing any information. This modern and well arranged Information Security Data Privacy In Educational Institutions Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
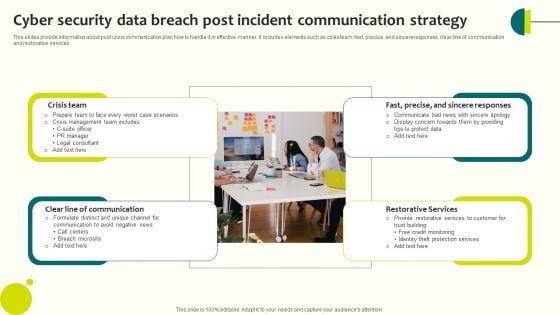
Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
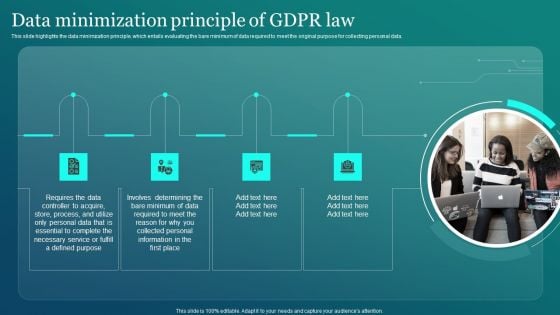
Information Security Data Minimization Principle Of GDPR Law Graphics PDF
This slide highlights the data minimization principle, which entails evaluating the bare minimum of data required to meet the original purpose for collecting personal data. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Security Data Minimization Principle Of GDPR Law Graphics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cloud Security Threats Loss Of Data Cloud Computing Security IT Ppt Infographics Graphic Tips PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a cloud security threats loss of data cloud computing security it ppt infographics graphic tips pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like locations, cloud service, strategies, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
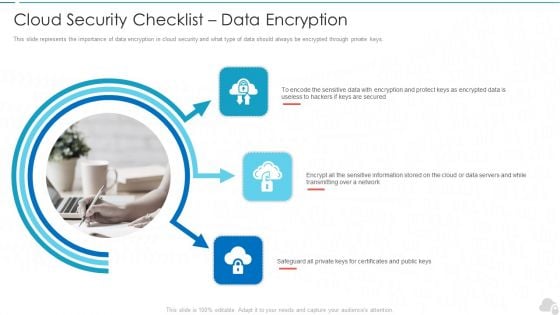
Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
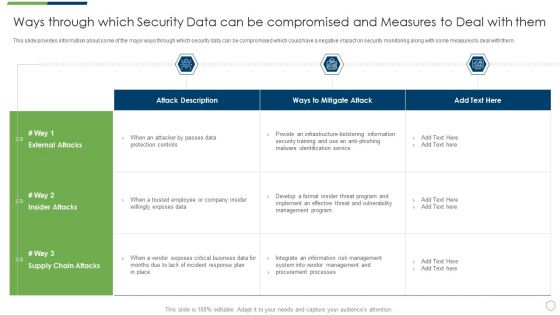
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
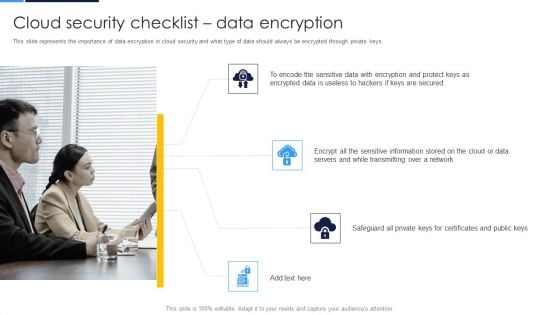
Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
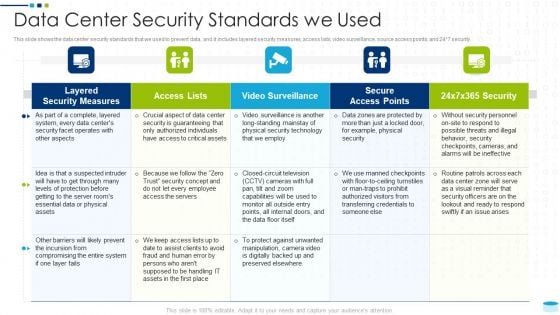
Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
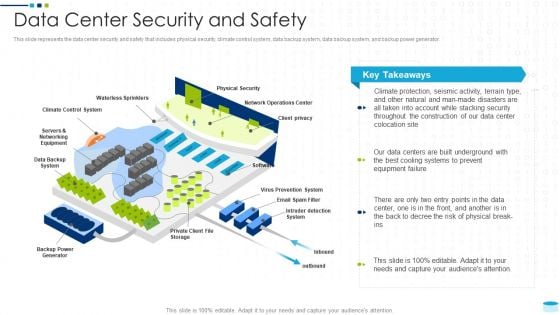
Data Center Infrastructure Management IT Data Center Security And Safety Demonstration PDF
This slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an awe inspiring pitch with this creative data center infrastructure management it data center security and safety demonstration pdf bundle. Topics like client privacy, physical security, waterless sprinklers, data backup system, virus prevention system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
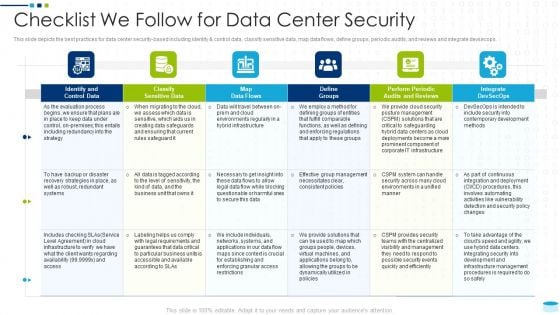
Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
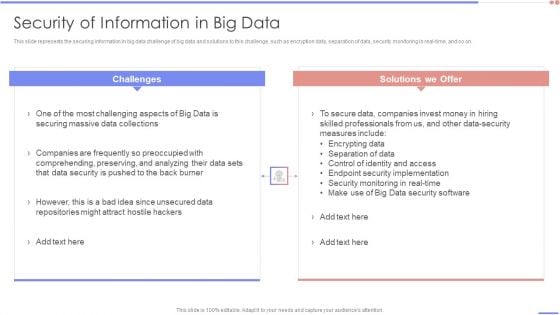
Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
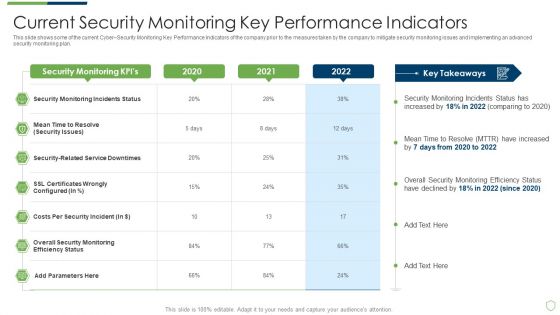
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Data Folder Security Vector Icon Ppt PowerPoint Presentation File Rules PDF
Persuade your audience using this data folder security vector icon ppt powerpoint presentation file rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data folder security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Network Security With Lock Showing Online Safety Icon Ppt PowerPoint Presentation Infographic Template Graphics PDF
Presenting this set of slides with name data network security with lock showing online safety icon ppt powerpoint presentation infographic template graphics pdf. This is a two stage process. The stages in this process are data network security with lock showing online safety icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
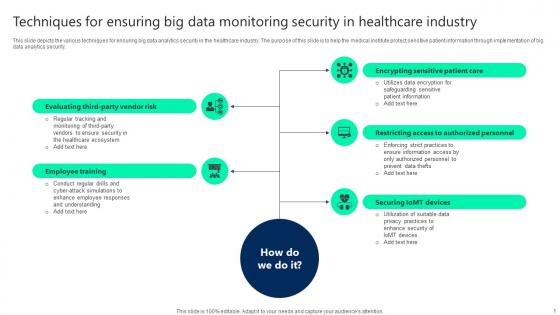
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.
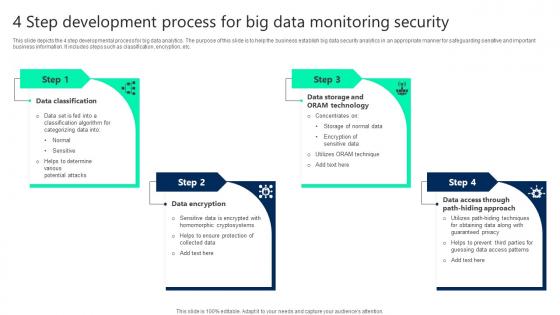
4 Step Development Process For Big Data Monitoring Security Demonstration pdf
This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Showcasing this set of slides titled 4 Step Development Process For Big Data Monitoring Security Demonstration pdf. The topics addressed in these templates are Data Classification, Data Access, Data Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc.
Data Privacy Security And Protection Vector Icon Ppt PowerPoint Presentation File Graphic Tips PDF
Presenting data privacy security and protection vector icon ppt powerpoint presentation file graphic tips pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data privacy security and protection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Case Of Splunk Big Data For Security Intelligence Elements Pdf
Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc. Showcasing this set of slides titled Use Case Of Splunk Big Data For Security Intelligence Elements Pdf The topics addressed in these templates are Security Monitoring, Compliance, Threat Intelligence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc.
Data Protection Security Controls Ppt PowerPoint Presentation File Designs Cpb Pdf
Presenting this set of slides with name data protection security controls ppt powerpoint presentation file designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Warehouse Security Issues Ppt PowerPoint Presentation Inspiration Master Slide Cpb Pdf
Presenting this set of slides with name data warehouse security issues ppt powerpoint presentation inspiration master slide cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like data services market data pricing analytics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Protecting The Data Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Download and present our shapes PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download and present our Technology PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake.Use these PowerPoint slides for presentations relating to Folder and file security concept, business, shapes, computer, signs, technology. The prominent colors used in the PowerPoint template are Blue, White, Black. PowerPoint presentation experts tell us our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. You can be sure our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are readymade to fit into any presentation structure. PowerPoint presentation experts tell us our concept PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Presenters tell us our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our concept PowerPoint templates and PPT Slides are visually appealing. Edit plans with our Protecting The Data Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
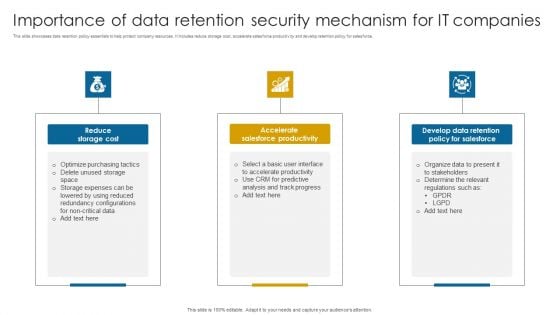
Importance Of Data Retention Security Mechanism For It Companies Professional PDF
This slide showcases data retention policy essentials to help protect company resources. It includes reduce storage cost, accelerate salesforce productivity and develop retention policy for salesforce.Presenting Importance Of Data Retention Security Mechanism For It Companies Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Salesforce Productivity, Develop Data Retention, Determine Relevant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
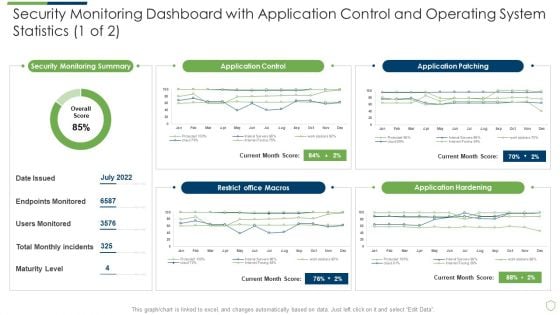
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
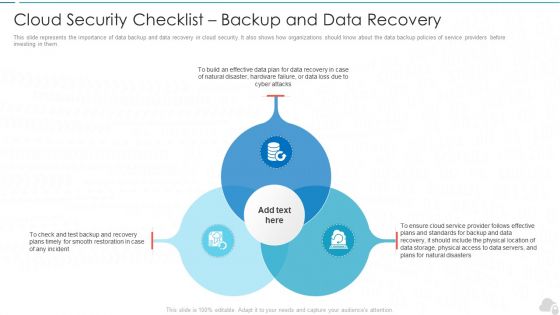
Cloud Security Checklist Backup And Data Recovery Cloud Computing Security IT Ppt Styles Rules PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting cloud security checklist backup and data recovery cloud computing security it ppt styles rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like effective, cloud service, natural disasters, data plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Data Enablement Framework And Security Training Program Icons PDF
This slide illustrates three day training workshop for data enablement and data security. It includes audience, objectives, data governance, data security, etc. Presenting Data Enablement Framework And Security Training Program Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Data Foundation, Security Model Introduction, User Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
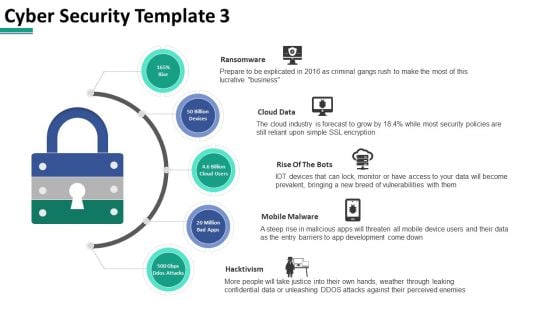
Cyber Security Cloud Data Ppt PowerPoint Presentation Summary Graphics Download
This is a cyber security cloud data ppt powerpoint presentation summary graphics download. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
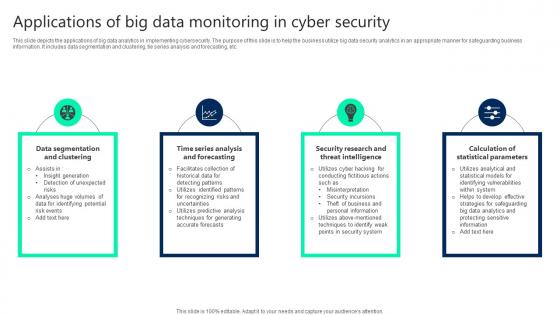
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
Corporate Data Management And Privacy Security Mechanism Icon Slides PDF
Persuade your audience using this Corporate Data Management And Privacy Security Mechanism Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Data, Management Privacy, Security Mechanism Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internet Security And Data Audit Icon Pictures Pdf
Pitch your topic with ease and precision using this Internet Security And Data Audit Icon Pictures Pdf This layout presents information on Internet Security, Data Audit Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Security And Data Audit Icon Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Building Data Analytics And Cyber Security Strategy Framework Icons PDF
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Technology Security And Data Safety Elements Icon Formats PDF
Showcasing this set of slides titled Information Technology Security And Data Safety Elements Icon Formats PDF. The topics addressed in these templates are Information Technology Security, Data Safety Elements Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
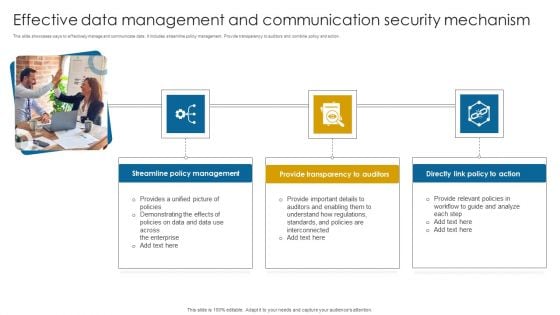
Effective Data Management And Communication Security Mechanism Themes PDF
This slide showcases ways to effectively manage and communicate data. It includes streamline policy management. Provide transparency to auditors and combine policy and action. Presenting Effective Data Management And Communication Security Mechanism Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Streamline Policy Management, Provide Transparency, Directly Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
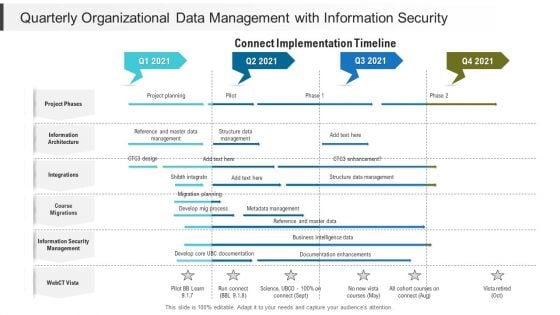
Quarterly Organizational Data Management With Information Security Ideas
Presenting our jaw dropping quarterly organizational data management with information security ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
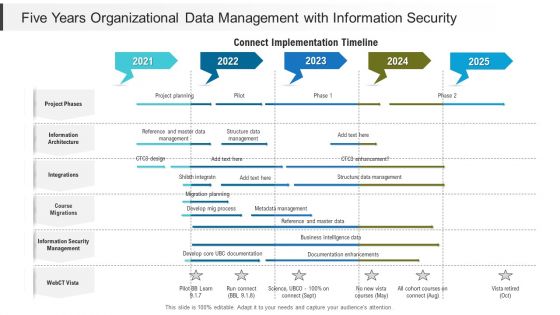
Five Years Organizational Data Management With Information Security Information
Presenting our jaw dropping five years organizational data management with information security information. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months Organizational Data Management With Information Security Information
Presenting our jaw dropping three months organizational data management with information security information. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

 Home
Home