Endpoint
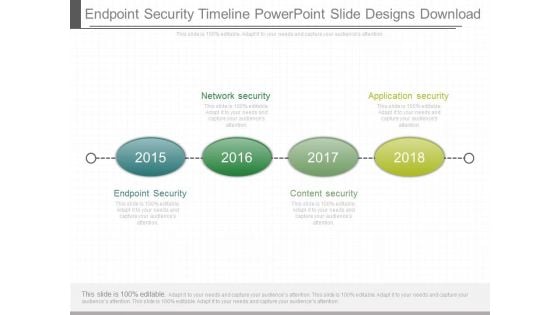
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.

Endpoint Initiated Vs Service Initiated Portrait PDF
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Endpoint Initiated Vs Service Initiated Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Endpoint Security Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Endpoint Security Checklist In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Endpoint Security Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Endpoint Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Automated Endpoint Protection Ppt PowerPoint Presentation Model Icon Cpb
Presenting this set of slides with name automated endpoint protection ppt powerpoint presentation model icon cpb. This is an editable Powerpoint nine stages graphic that deals with topics like automated endpoint protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Automated Endpoint Security Ppt PowerPoint Presentation Ideas Slide Cpb
Presenting this set of slides with name automated endpoint security ppt powerpoint presentation ideas slide cpb. This is an editable Powerpoint three stages graphic that deals with topics like automated endpoint security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Security Management Ppt PowerPoint Presentation Professional Example Cpb
Presenting this set of slides with name endpoint security management ppt powerpoint presentation professional example cpb. This is an editable Powerpoint four stages graphic that deals with topics like endpoint security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Enterprise Endpoint Ppt PowerPoint Presentation Slides Ideas Cpb
Presenting this set of slides with name enterprise endpoint ppt powerpoint presentation slides ideas cpb. This is an editable Powerpoint six stages graphic that deals with topics like enterprise endpoint to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Endpoint Threat Management Ppt PowerPoint Presentation Layouts Slideshow Cpb Pdf
Presenting this set of slides with name endpoint threat management ppt powerpoint presentation layouts slideshow cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like endpoint threat management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Threat Management Ppt PowerPoint Presentation Outline Templates Cpb Pdf
Presenting this set of slides with name endpoint threat management ppt powerpoint presentation outline templates cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like endpoint threat management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
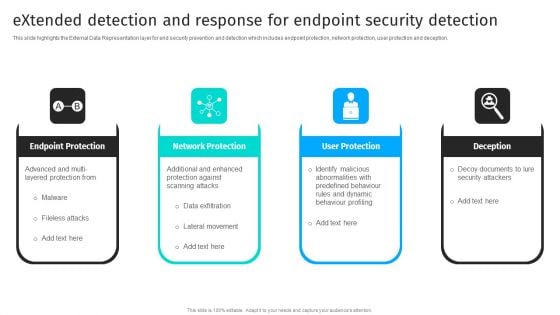
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
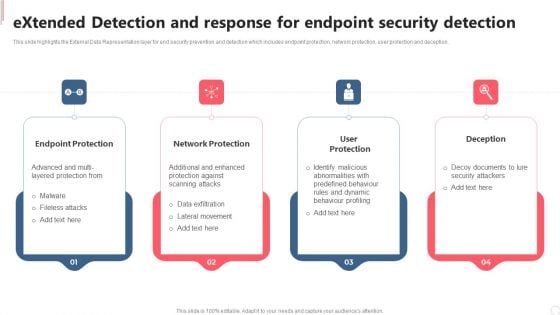
Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.
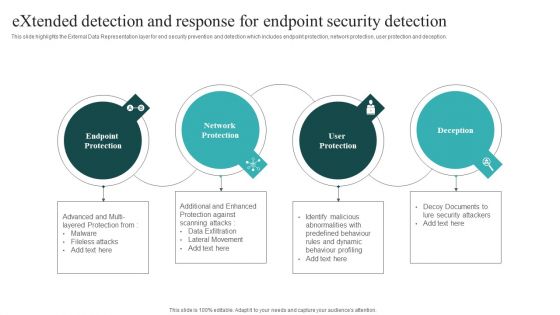
Extended Detection And Response For Endpoint Security Detection Themes PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Boost your pitch with our creative Extended Detection And Response For Endpoint Security Detection Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
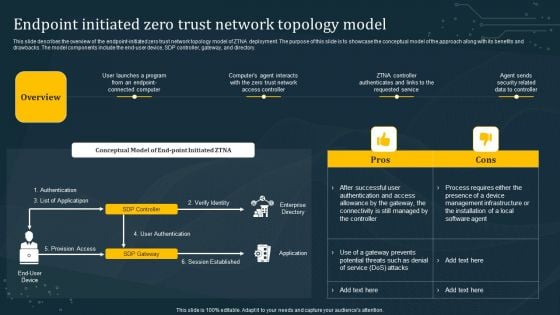
Endpoint Initiated Zero Trust Network Topology Model Sample PDF
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. This modern and well-arranged Endpoint Initiated Zero Trust Network Topology Model Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Phase Endpoint Report Of New Drug In Clinical Trial Structure PDF
Deliver an awe inspiring pitch with this creative Phase Endpoint Report Of New Drug In Clinical Trial Structure PDF bundle. Topics like Phase Endpoint Report Of New Drug In Clinical Trial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. This is a IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Endpoint Protection, Network Protection, User Protection, Deception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
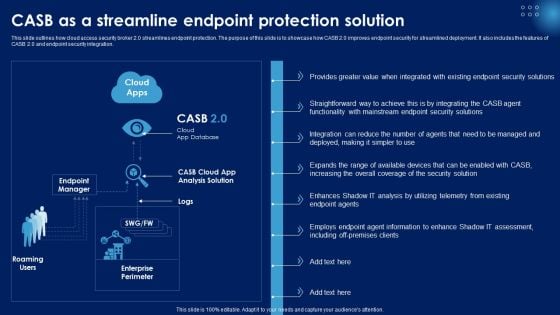
CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Take your projects to the next level with our ultimate collection of CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
Web Service Endpoint Management Ppt PowerPoint Presentation Outline Aids Cpb Pdf
Presenting this set of slides with name web service endpoint management ppt powerpoint presentation outline aids cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like web service endpoint management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Security Protection Services Ppt PowerPoint Presentation Professional Backgrounds Cpb Pdf
Presenting this set of slides with name endpoint security protection services ppt powerpoint presentation professional backgrounds cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like endpoint security protection services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Security Strategy Ppt PowerPoint Presentation Visual Aids Deck Cpb Pdf Pdf
Presenting this set of slides with name endpoint security strategy ppt powerpoint presentation visual aids deck cpb pdf pdf. This is an editable Powerpoint three stages graphic that deals with topics like endpoint security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Healthcare Organization Service Endpoint Ppt PowerPoint Presentation Model Layouts Cpb Pdf
Presenting this set of slides with name healthcare organization service endpoint ppt powerpoint presentation model layouts cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like healthcare organization service endpoint to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Mobile Endpoint Security Testing Ppt PowerPoint Presentation Professional Example Cpb Pdf
Presenting this set of slides with name mobile endpoint security testing ppt powerpoint presentation professional example cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like mobile endpoint security testing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
3 Groups Infographic For Managed Endpoint Detection And Response Ppt PowerPoint Presentation File Graphics PDF
Presenting 3 groups infographic for managed endpoint detection and response ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 groups infographic for managed endpoint detection and response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Phase Endpoint Report Of New Drug In Clinical Trial Clinical Research Trial Phases Microsoft PDF
Create an editable Phase Endpoint Report Of New Drug In Clinical Trial Clinical Research Trial Phases Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Phase Endpoint Report Of New Drug In Clinical Trial Clinical Research Trial Phases Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Phase Endpoint Report Of New Drug In Clinical Trial New Clinical Drug Trial Process Professional PDF
This Phase Endpoint Report Of New Drug In Clinical Trial New Clinical Drug Trial Process Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Phase Endpoint Report Of New Drug In Clinical Trial New Clinical Drug Trial Process Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
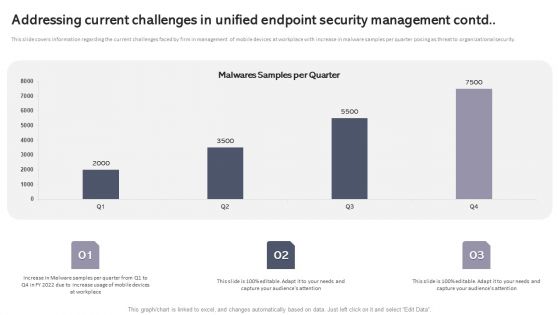
Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.
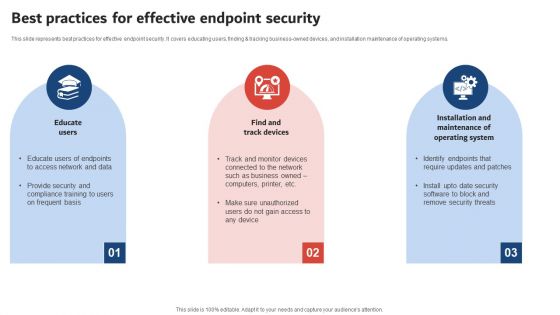
Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF
This slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Phase Endpoint Report Of New Drug In Clinical Trial Medical Research Phases For Clinical Tests Designs PDF
The Phase Endpoint Report Of New Drug In Clinical Trial Medical Research Phases For Clinical Tests Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Microservices Architecture With Endpoints Ppt PowerPoint Presentation Portfolio Designs
Presenting this set of slides with name microservices architecture with endpoints ppt powerpoint presentation portfolio designs. The topics discussed in these slides are boundary endpoint for d1, interior endpoint for d2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
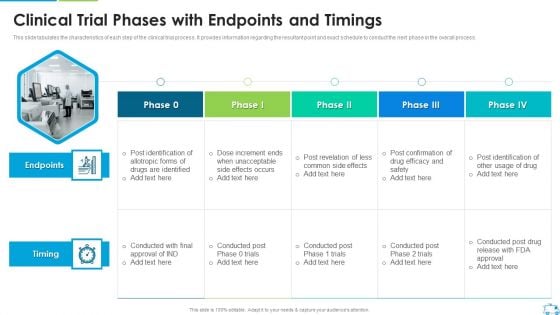
Clinical Trial Phases With Endpoints And Timings Formats PDF
This slide tabulates the characteristics of each step of the clinical trial process. It provides information regarding the resultant point and exact schedule to conduct the next phase in the overall process.Deliver and pitch your topic in the best possible manner with this Clinical Trial Phases With Endpoints And Timings Formats PDF Use them to share invaluable insights on Post Revelation, Less Common Side Effects, Dose Increment Ends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
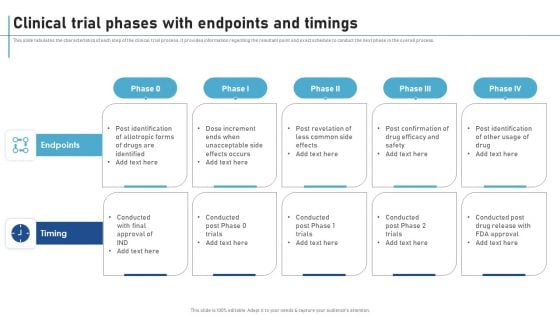
Clinical Trial Phases With Endpoints And Timings New Clinical Drug Trial Process Topics PDF
This slide tabulates the characteristics of each step of the clinical trial process. It provides information regarding the resultant point and exact schedule to conduct the next phase in the overall process. Boost your pitch with our creative Clinical Trial Phases With Endpoints And Timings New Clinical Drug Trial Process Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
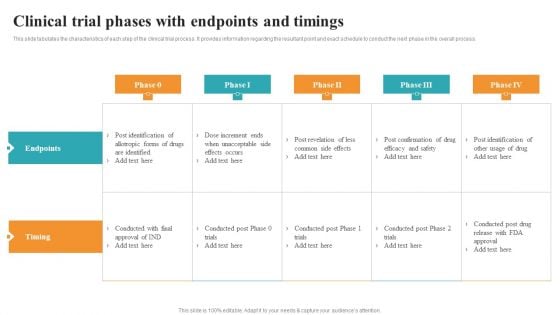
Clinical Trial Phases With Endpoints And Timings Medical Research Phases For Clinical Tests Brochure PDF
This slide tabulates the characteristics of each step of the clinical trial process. It provides information regarding the resultant point and exact schedule to conduct the next phase in the overall process. Do you know about Slidesgeeks Clinical Trial Phases With Endpoints And Timings Medical Research Phases For Clinical Tests Brochure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
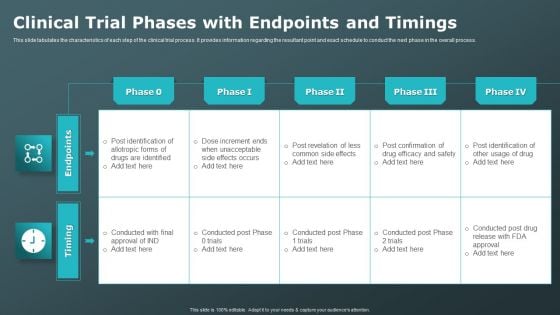
Clinical Trial Phases With Endpoints And Timings Clinical Research Trial Phases Microsoft PDF
This slide tabulates the characteristics of each step of the clinical trial process. It provides information regarding the resultant point and exact schedule to conduct the next phase in the overall process. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Clinical Trial Phases With Endpoints And Timings Clinical Research Trial Phases Microsoft PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Software Safety Example Layout Powerpoint Presentation Templates
This is a software safety example layout powerpoint presentation templates. This is a four stage process. The stages in this process are web server, endpoint security, content security, database.

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.
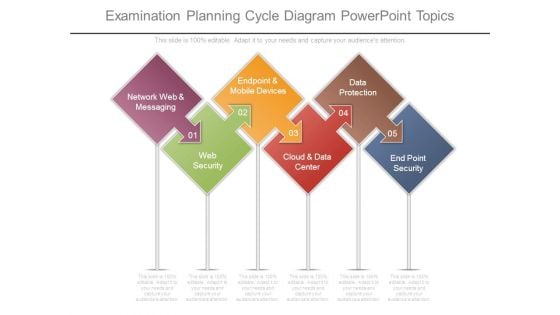
Examination Planning Cycle Diagram Powerpoint Topics
This is a examination planning cycle diagram powerpoint topics. This is a five stage process. The stages in this process are network web and messaging, web security, endpoint and mobile devices, cloud and data center, data protection, end point security.
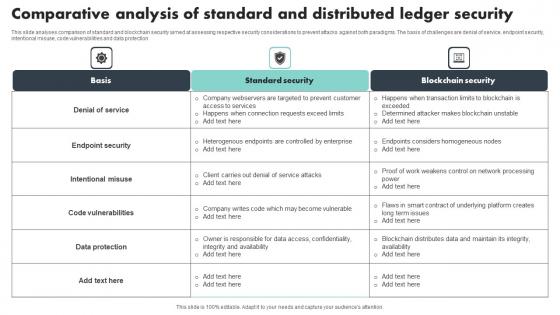
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection
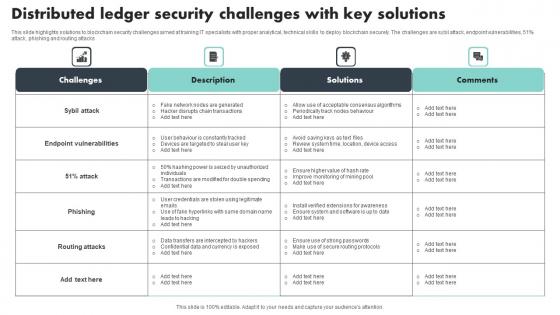
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks
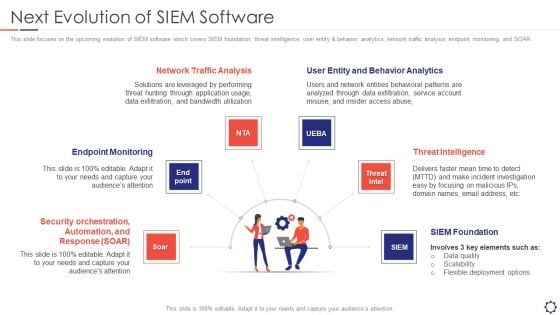
SIEM Next Evolution Of SIEM Software Ppt Styles Picture PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting siem next evolution of siem software ppt styles picture pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, threat intelligence, siem foundation, behavior analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
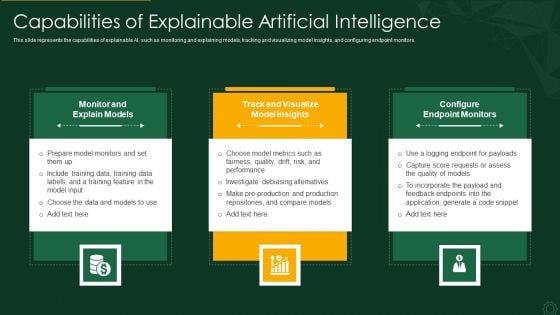
Explainable AI XAI Frameworks IT Capabilities Of Explainable Artificial Intelligence Information PDF
This slide represents the capabilities of explainable AI, such as monitoring and explaining models, tracking and visualizing model insights, and configuring endpoint monitors. Presenting explainable ai xai frameworks it capabilities of explainable artificial intelligence information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like monitor and explain models, track and visualize model insights, configure endpoint monitors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Services Next Evolution Of SIEM Software Ppt Portfolio Clipart PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting siem services next evolution of siem software ppt portfolio clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like traffic analysis, endpoint monitoring, threat intelligence, behavior analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
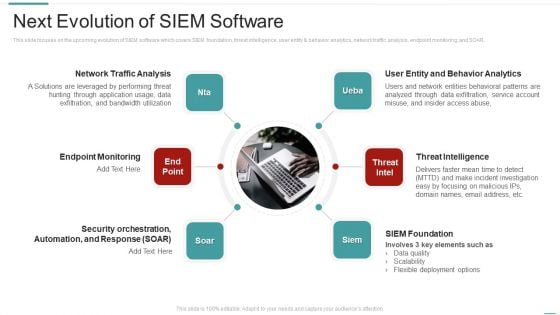
Risk Recognition Automation Next Evolution Of Siem Software Ppt Ideas Objects PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting risk recognition automation next evolution of siem software ppt ideas objects pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, threat intelligence, siem foundation, user entity and behavior analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
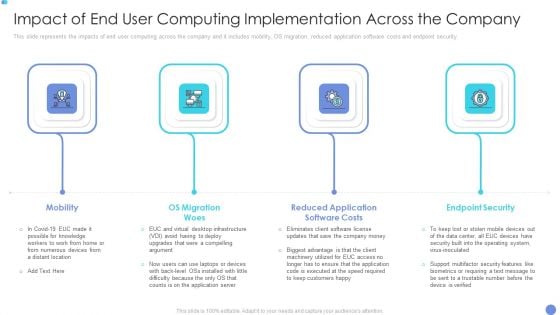
Customer Mesh Computing IT Impact Of End User Computing Implementation Across The Company Pictures PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security. Presenting customer mesh computing it impact of end user computing implementation across the company pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mobility, os migration woes, endpoint security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
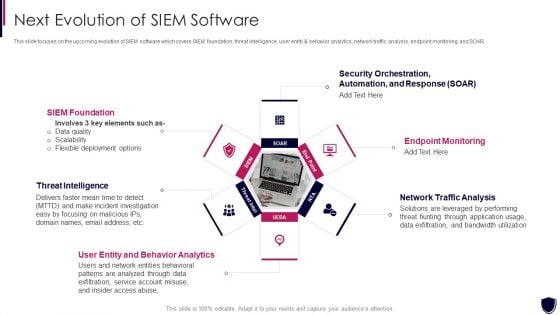
Enhancing Cyber Safety With Vulnerability Administration Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting enhancing cyber safety with vulnerability administration next evolution of siem software sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, user entity and behavior analytics, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

VID Impact Of End User Computing Implementation Across The Company Template PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security.Presenting VID Impact Of End User Computing Implementation Across The Company Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Reduced Application, Endpoint Security, Compelling Argument. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
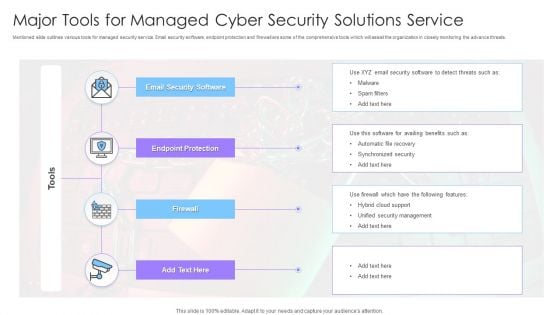
Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Virtualization Impacts Of End User Computing Implementation Across The Company Summary PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security.This is a Computer Virtualization Impacts Of End User Computing Implementation Across The Company Summary PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Biggest Advantage, Support Multifactor, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
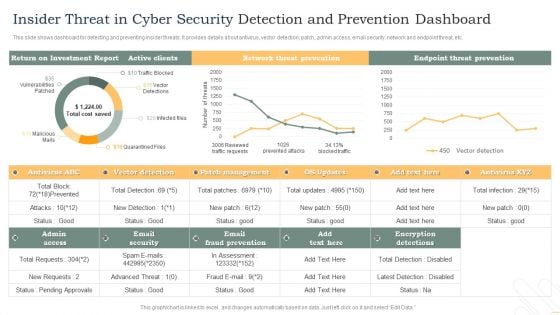
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
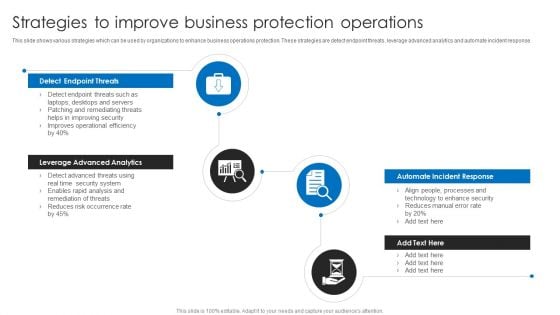
Strategies To Improve Business Protection Operations Formats PDF
This slide shows various strategies which can be used by organizations to enhance business operations protection. These strategies are detect endpoint threats, leverage advanced analytics and automate incident response. Presenting Strategies To Improve Business Protection Operations Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF
This slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Presenting Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
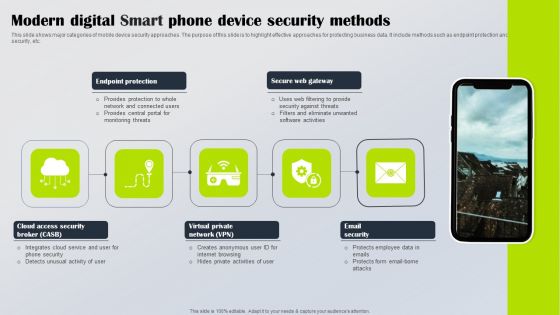
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
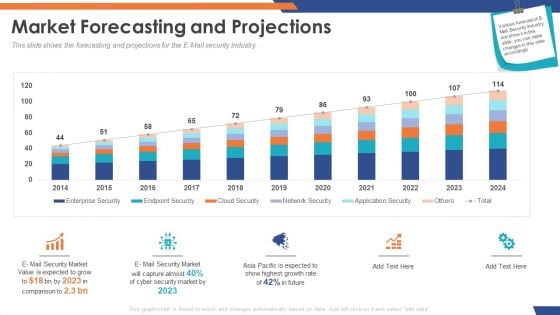
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
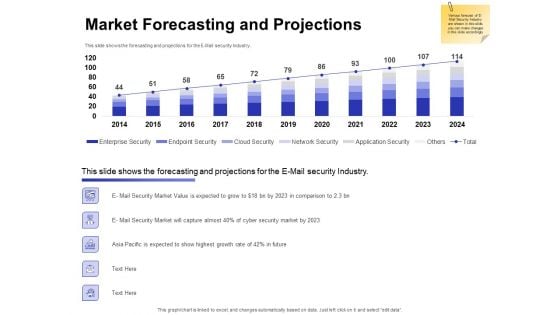
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
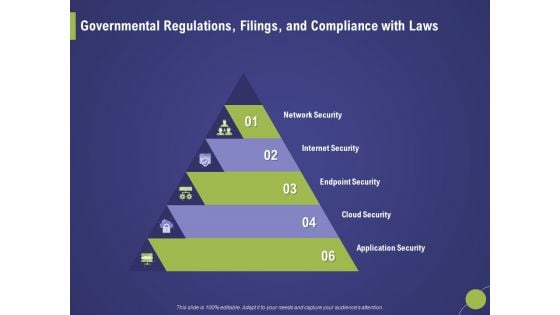
Firm Capability Assessment Governmental Regulations Filings And Compliance With Laws Ppt Outline Slides PDF
Presenting this set of slides with name firm capability assessment governmental regulations filings and compliance with laws ppt outline slides pdf. This is a six stage process. The stages in this process are network security, internet security, endpoint security, cloud security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
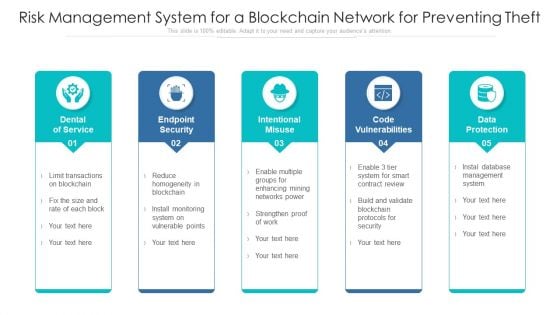
Risk Management System For A Blockchain Network For Preventing Theft Ppt PowerPoint Presentation Layouts Deck PDF
Presenting risk management system for a blockchain network for preventing theft ppt powerpoint presentation layouts deck pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including endpoint security, intentional misuse, code vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
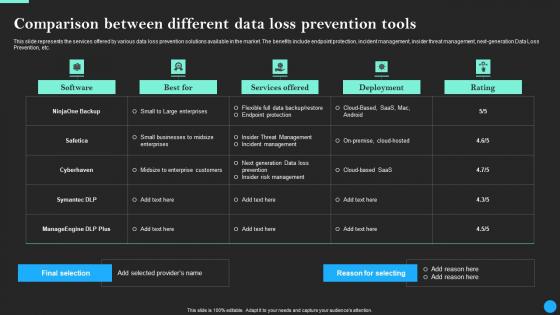
Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf today and make your presentation stand out from the rest This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc.

 Home
Home