Hacker

Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a conceptual illustration on the subject of computer hacking Our Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211 never fail to amaze. They catch every eye that comes by.
Vector Illustrating Hacker Launching Internet Threats Through Malware Ppt PowerPoint Presentation Icon Backgrounds PDF
Persuade your audience using this vector illustrating hacker launching internet threats through malware ppt powerpoint presentation icon backgrounds pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustrating hacker launching internet threats through malware. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Hacker With Dark Face In Hoodie Ppt PowerPoint Presentation File Shapes
Presenting this set of slides with name hacker with dark face in hoodie ppt powerpoint presentation file shapes. This is a one stage process. The stage in this process is hacker with dark face in hoodie. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
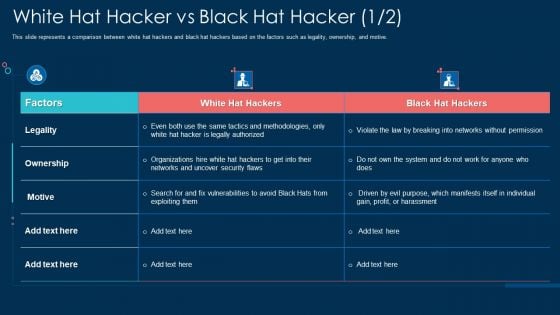
White Hat Hacker Vs Black Hat Hacker Security Ppt File Example PDF
This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver and pitch your topic in the best possible manner with this white hat hacker vs black hat hacker security ppt file example pdf. Use them to share invaluable insights on ownership, networks, organizations, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Hacker Performing Cyber Attack Vector Icon Ppt PowerPoint Presentation Icon Professional PDF
Presenting hacker performing cyber attack vector icon ppt powerpoint presentation icon professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hacker performing cyber attack vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
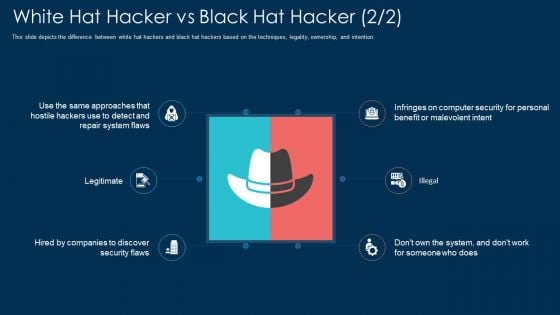
White Hat Hacker Vs Black Hat Hacker Ppt Inspiration Slide Download PDF
This slide depicts the difference between white hat hackers and black hat hackers based on the techniques, legality, ownership, and intention. Presenting white hat hacker vs black hat hacker ppt inspiration slide download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hacker People PowerPoint Template 0810
A business hacker is breaking into a laptop computer and stealing information isolated against a white background Take the fast train to success. Book a berth with our Hacker People PowerPoint Template 0810.

Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with background concept of computer trojan horse Go far and further with our Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811. Add to the distance your thoughts can cover.
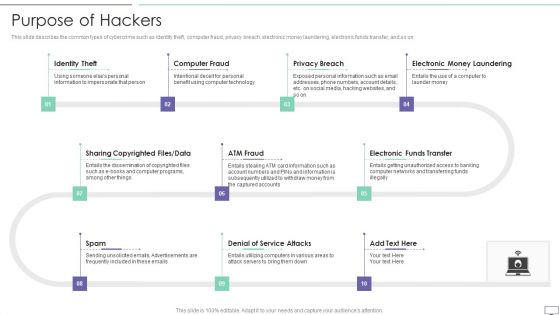
IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
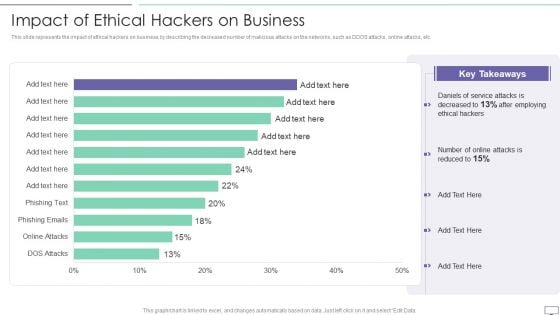
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
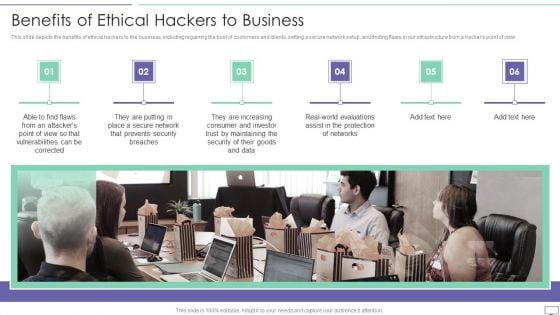
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
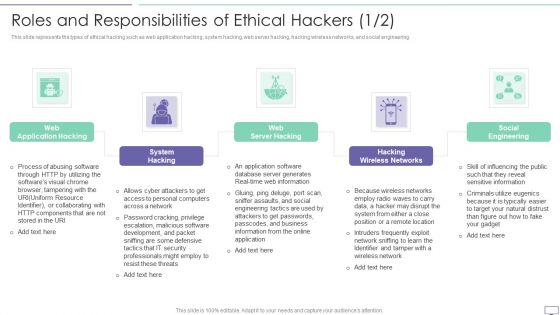
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf
Showcasing this set of slides titled Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf The topics addressed in these templates are Fraud Threat Evaluation, Icon Showcasing Hacker All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Process Hacker In Powerpoint And Google Slides Cpb
Introducing our well-designed Process Hacker In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Process Hacker. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Process Hacker In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
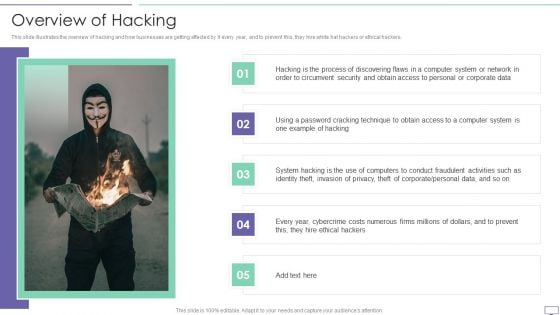
IT Security Hacker Overview Of Hacking Sample PDF
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers.Deliver an awe inspiring pitch with this creative IT Security Hacker Overview Of Hacking Sample PDF bundle. Topics like Process Of Discovering, Circumvent Security, Example Of Hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
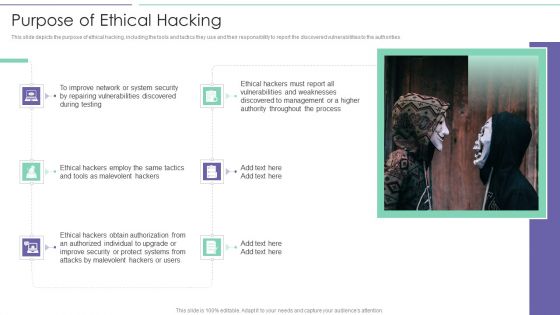
IT Security Hacker Purpose Of Ethical Hacking Slides PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Purpose Of Ethical Hacking Slides PDF. Use them to share invaluable insights on Vulnerabilities Discovered, Malevolent Hackers, Malevolent Hackers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
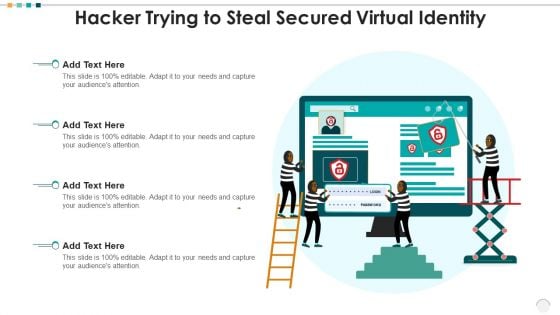
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Certified Ethical Hacker CEH Job Description Sample PDF
This slide covers Certified ethical hacker CEH certifications Training Exam Cost, Job Description, Roles and responsibilities and average salary package etc.Deliver an awe inspiring pitch with this creative Certified Ethical Hacker CEH Job Description Sample PDF bundle. Topics like Roles And Responsibilities, Hacking Destruction, Circumvent Detection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Ethical Hacker Collection Of Information Technology Certifications Structure PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting certified ethical hacker collection of information technology certifications structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like technology, demand, management, developments, strategies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
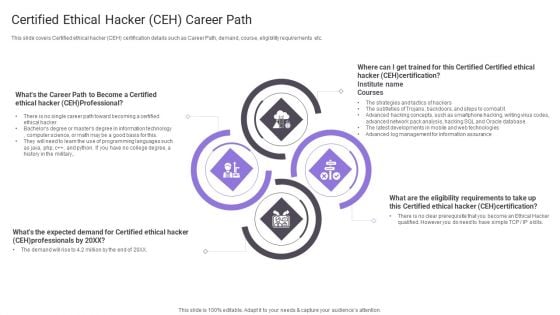
Certified Ethical Hacker CEH Career Path Portrait PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc.Presenting Certified Ethical Hacker CEH Career Path Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Expected Demand, Programming Languages, Eligibility Requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
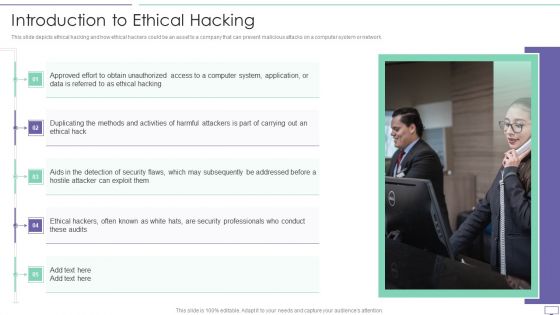
IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
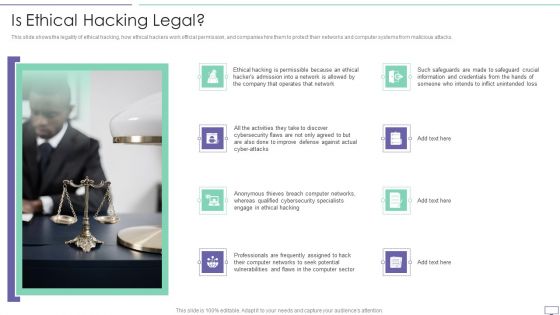
IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Details On Certified Ethical Hacker Ceh Certification Professional PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a details on certified ethical hacker ceh certification professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device, network, analysis, system, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
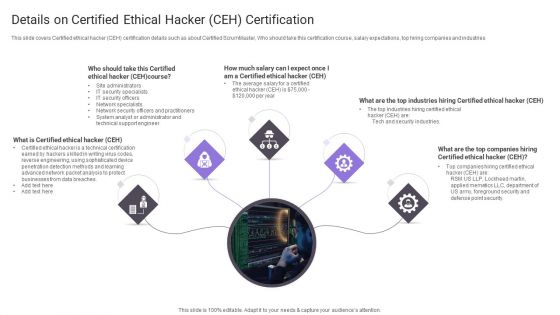
Details On Certified Ethical Hacker CEH Certification Summary PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries.Presenting Details On Certified Ethical Hacker CEH Certification Summary PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Solutions Architect, Certified Solutions, Solutions Architect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For IT Security Hacker Slide Introduction PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For IT Security Hacker Slide Introduction PDF bundle. Topics like Prevent Hacking, Strategies On Business, Implementation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For IT Security Hacker Inspiration PDF
Download our innovative and attention grabbing Icons Slide For IT Security Hacker Inspiration PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
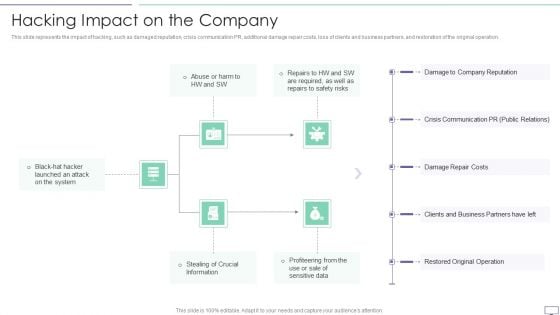
IT Security Hacker Hacking Impact On The Company Information PDF
This slide represents the impact of hacking, such as damaged reputation, crisis communication PR, additional damage repair costs, loss of clients and business partners, and restoration of the original operation. Deliver an awe inspiring pitch with this creative IT Security Hacker Hacking Impact On The Company Information PDF bundle. Topics like Company Reputation, Crisis Communication, Damage Repair can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
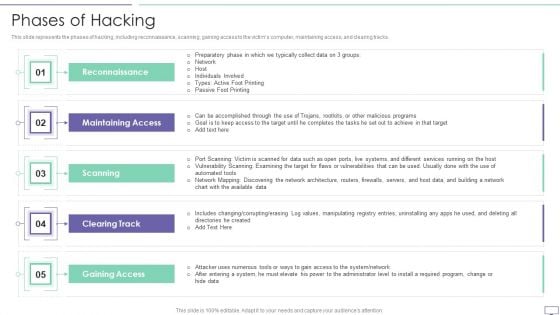
IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
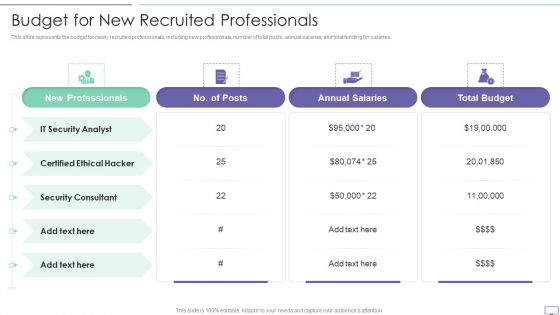
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
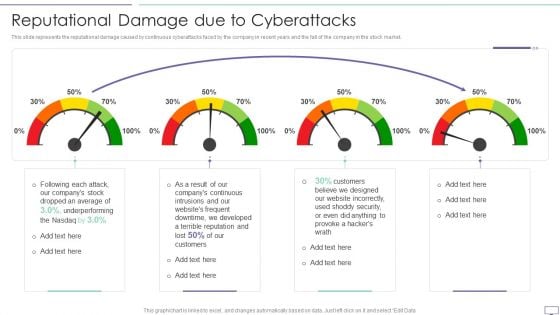
IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF. Use them to share invaluable insights on Website Incorrectly, Underperforming, Dropped An Average and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Use Of Security Programs Professional PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks.Presenting IT Security Hacker Use Of Security Programs Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Requires, Monthly Membership, Elimination Of Malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Regaining Reputation Of Our Company Infographics PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies.This is a IT Security Hacker Regaining Reputation Of Our Company Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers And Clients, Appropriate Service, Database Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Backup Of Sensitive Information Ideas PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization.This is a IT Security Hacker Backup Of Sensitive Information Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Different Service, Emergency Access, Natural Disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fivty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
Russian Cyber Attacks On Ukraine IT Hacker Group Anonymous Has Waged Icons PDF
This slide depicts the anonymous organization and how they have started a cyberwar against Russia by gathering worldwide hackers through Twitter. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it hacker group anonymous has waged icons pdf. Use them to share invaluable insights on hacker group anonymous has waged a cyberwar against russia and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
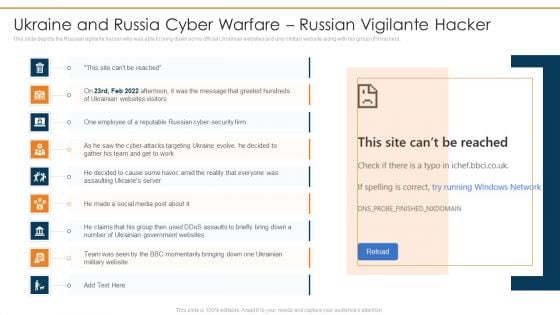
Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Sample PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack ukraine and russia cyber warfare russian vigilante hacker sample pdf Use them to share invaluable insights on ukraine and russia cyber warfare russian vigilante hacker and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Protecting PC Security From Hacker Vector Icon Ppt PowerPoint Presentation File Infographics PDF
Presenting protecting pc security from hacker vector icon ppt powerpoint presentation file infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protecting pc security from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Of Hacker Launching Cyber Phishing Scams And Attacks Background PDF
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Picture Of Hacker In Mask Hood Ppt PowerPoint Presentation Layouts Inspiration
Presenting this set of slides with name picture of hacker in mask hood ppt powerpoint presentation layouts inspiration. This is a one stage process. The stage in this process is picture of hacker in mask hood. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Online Crime With Hacker And Spider Vector Icon Ppt PowerPoint Presentation Gallery Examples PDF
Showcasing this set of slides titled online crime with hacker and spider vector icon ppt powerpoint presentation gallery examples pdf. The topics addressed in these templates are online crime with hacker and spider vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities Of Ethical Hacker Ppt Infographics Graphics Example PDF
This slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports, repairing the vulnerabilities of the system, etc. This is a roles and responsibilities of ethical hacker ppt infographics graphics example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roles and responsibilities of ethical hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
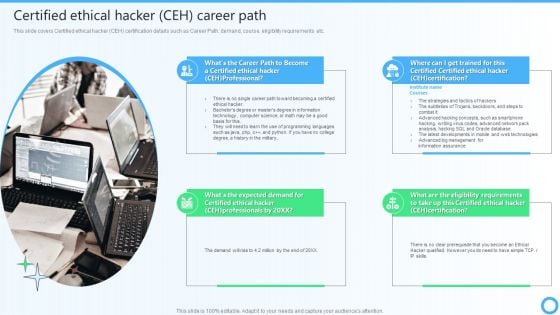
Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc.Get a simple yet stunning designed Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Threat With Hacker Icon On The Screen Ppt PowerPoint Presentation Infographic Template PDF
Persuade your audience using this cyber security threat with hacker icon on the screen ppt powerpoint presentation infographic template pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security threat with hacker icon on the screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virus On Screen Online Crime Threat From Hacker Vector Icon Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting virus on screen online crime threat from hacker vector icon ppt powerpoint presentation gallery smartart pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virus on screen online crime threat from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Skills And Certifications Required For Ethical Hacker Ppt Gallery Icon PDF
This slide describes the skills and certifications required for ethical hacker, such as computer networking skills, computer skills, Linux skills, and so on. Deliver an awe inspiring pitch with this creative skills and certifications required for ethical hacker ppt gallery icon pdf bundle. Topics like technologies, management, security, requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Hacker Stealing Business Confidential Data Base Through Internet Threats Ppt PowerPoint Presentation File Pictures PDF
Persuade your audience using this hacker stealing business confidential data base through internet threats ppt powerpoint presentation file pictures pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hacker stealing business confidential data base through internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home