Hacker
Online Network Security Against Hackers And Internet Threats Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this online network security against hackers and internet threats ppt powerpoint presentation file show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online network security against hackers and internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Channels Used By Hackers To Launch Internet Threats Ppt PowerPoint Presentation File Show PDF
Presenting various channels used by hackers to launch internet threats ppt powerpoint presentation file show pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including various channels used by hackers to launch internet threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
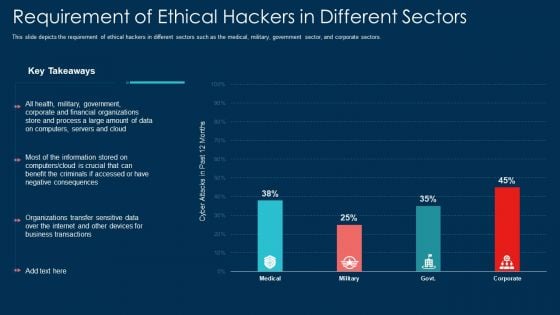
Requirement Of Ethical Hackers In Different Sectors Ppt Model Example File PDF
This slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Deliver and pitch your topic in the best possible manner with this requirement of ethical hackers in different sectors ppt model example file pdf. Use them to share invaluable insights on information, benefit, process, organizations, financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
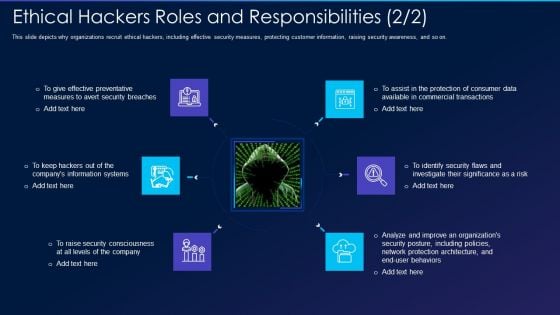
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
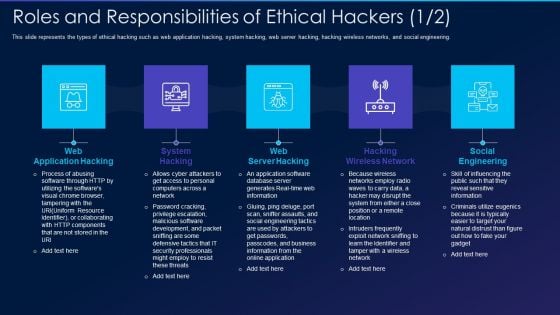
Cyber Exploitation IT Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Presenting cyber exploitation it roles and responsibilities of ethical hackers pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like web application hacking, system hacking, web server hacking, hacking wireless network, social engineering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack US Is Unmasking Russian Hackers Faster Than Ever Mockup PDF
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. This is a data wiper spyware attack us is unmasking russian hackers faster than ever mockup pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like blamed russian operatives, russian main intelligence, emerging technologies You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
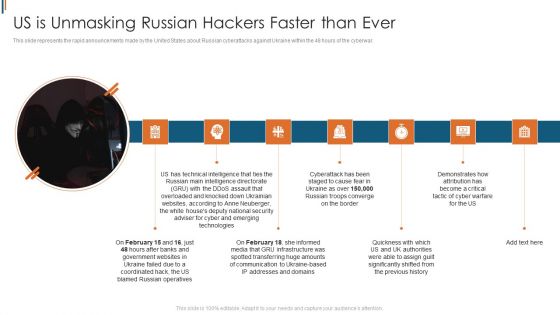
Ukraine Cyberwarfare Us Is Unmasking Russian Hackers Faster Than Ever Rules Pdf
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. This is a ukraine cyberwarfare us is unmasking russian hackers faster than ever rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like demonstrates how attribution has become a critical tactic of cyber warfare, quickness with which us and uk authorities, cyberattack has been staged to cause fear in ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF
This slide represents the rapid announcements made by the united states about russian cyberattacks against ukraine within the 48 hours of the cyberwar. Explore a selection of the finest Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Series Of Cyber Security Atta to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
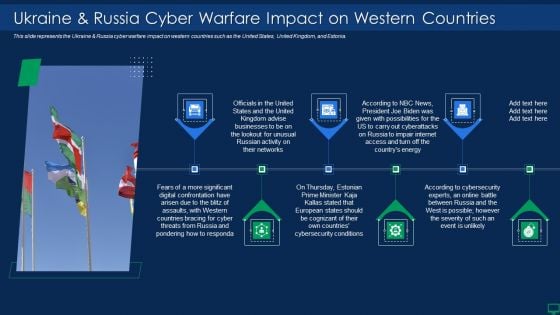
Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Impact Information PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare impact information pdf bundle. Topics like ukraine and russia cyber warfare russian vigilante hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Credit Card Stealing Money PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Hacker's hand trying to steal a credit card Figure out the finances with our Credit Card Stealing Money PowerPoint Backgrounds And Templates 1210. They help you get the calculations correct.

IT Career Certifications What Are Certification Ppt PowerPoint Presentation File Files PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description. Deliver and pitch your topic in the best possible manner with this IT Career Certifications What Are Certification Ppt PowerPoint Presentation File Files PDF. Use them to share invaluable insights on Certified ScrumMaster, Certified ethical hacker, ITIL Foundation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Benefits Of Ethical Hacking To Companies Ppt Model Example File PDF
This slide represents the benefits of ethical hacking to the companies, including testing security, identifying weaknesses, understanding hacker methods, and being ready for a hacker attack. Presenting benefits of ethical hacking to companies ppt model example file pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like measures, security, techniques, systems, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
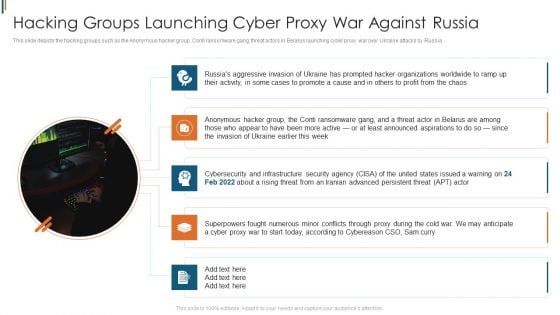
Ukraine Cyberwarfare Hacking Groups Launching Cyber Proxy War Against Russia Guidelines Pdf
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting ukraine cyberwarfare hacking groups launching cyber proxy war against russia guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
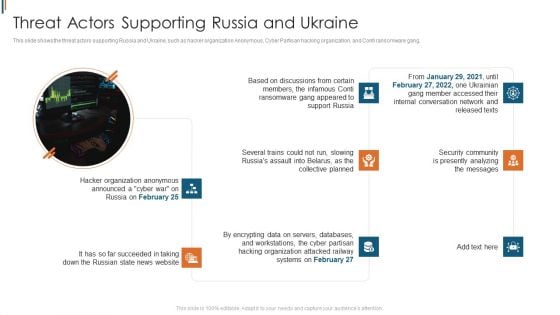
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf
This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer. Showcasing this set of slides titled Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf. The topics addressed in these templates are Data Breaches, Respondents, Mitigation Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer.
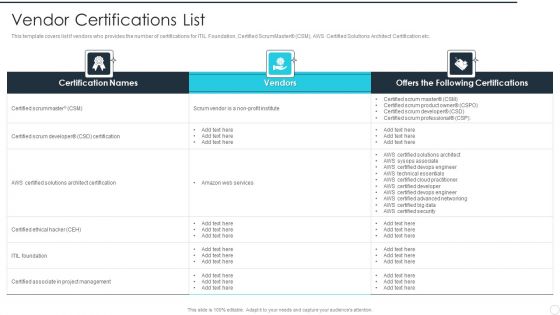
IT Career Certifications Vendor Certifications List Ppt PowerPoint Presentation File Background Designs PDF
This template covers list if vendors who provides the number of certifications for ITIL Foundation, Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification etc. Deliver an awe inspiring pitch with this creative IT Career Certifications Vendor Certifications List Ppt PowerPoint Presentation File Background Designs PDF bundle. Topics like Certified Scrummaster, Certified Scrum Developer, Certified Ethical Hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
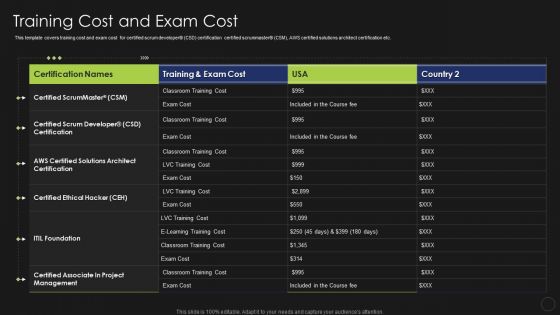
Information Technology Certifications Advantages Training Cost And Exam Cost Demonstration PDF
This template covers training cost and exam cost for certified scrum developer CSD certification certified scrummaster CSM, AWS certified solutions architect certification etc. Deliver an awe inspiring pitch with this creative Information Technology Certifications Advantages Training Cost And Exam Cost Demonstration PDF bundle. Topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Certifications Advantages What Are Certification Themes PDF
This template covers IT certification such as certified scrum master CSM, AWS certified solutions architect certification, certified ethical hacker CEH etc, qualification and job description. Deliver and pitch your topic in the best possible manner with this Information Technology Certifications Advantages What Are Certification Themes PDF. Use them to share invaluable insights on Certified ScrumMaster, Architect Certification, ITIL Foundation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Certifications Advantages IT Certification Career Path Diagrams PDF
This template covers the career path to become a certified professional including available courses for certified scrum developer CSD certification certified scrum master CSM etc. Deliver an awe inspiring pitch with this creative Information Technology Certifications Advantages IT Certification Career Path Diagrams PDF bundle. Topics like Certified Scrum Developer, Certified ScrumMaster, Certified Ethical Hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
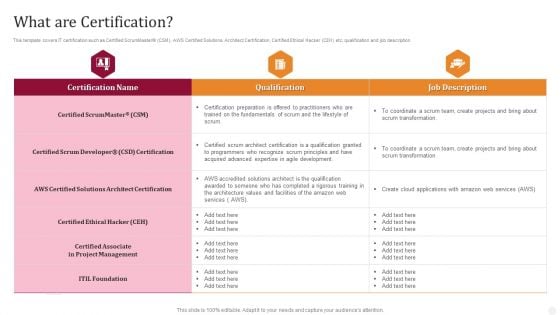
What Are Certification Technology License For IT Professional Background PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description.Deliver and pitch your topic in the best possible manner with this What Are Certification Technology License For IT Professional Background PDF. Use them to share invaluable insights on Architect Certification, Accredited Solutions, Project Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
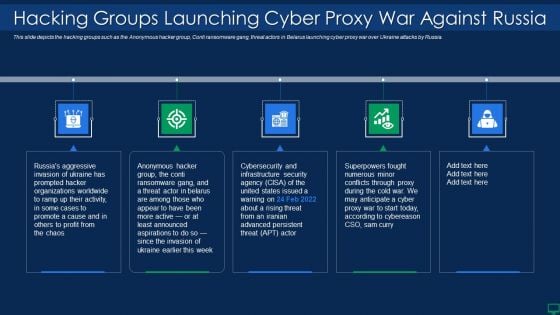
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
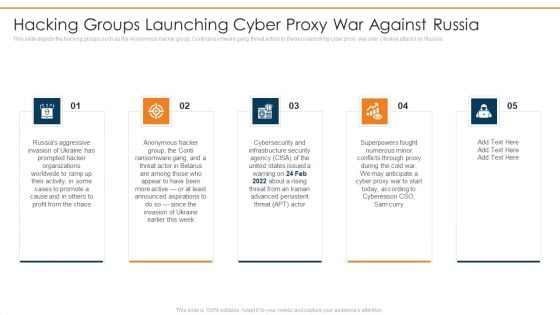
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Advantages Of Ethical Hacking Ppt Slides Microsoft PDF
This slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance, transition to the cloud, and employment. This is a advantages of ethical hacking ppt slides microsoft pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, quality, security, information, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
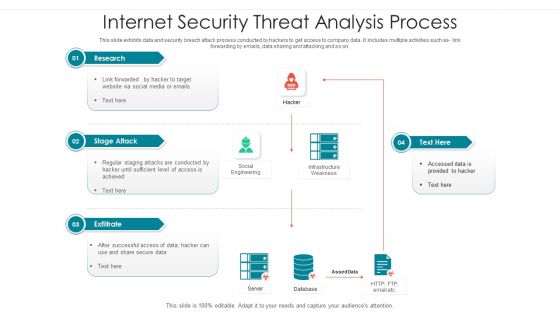
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
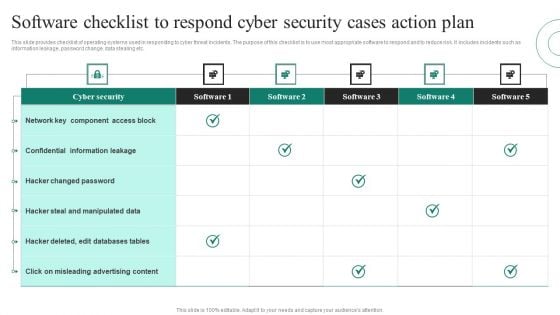
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
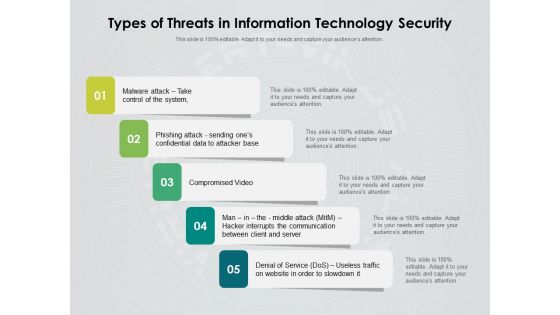
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Process Flow Of Botnet Malware Attack Icons PDF
This slide illustrates flowchart of attack through botnet malware hacking. It includes transmitting specific string to C and C, C and C authorizes bot connection, etc. Persuade your audience using this Process Flow Of Botnet Malware Attack Icons PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware In Victim, Hacker Launches, Malware Reads. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Certification Information Technology Professionals What Are Certification Infographics PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description This is a certification information technology professionals what are certification infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like certification, preparation, fundamentals, practitioners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
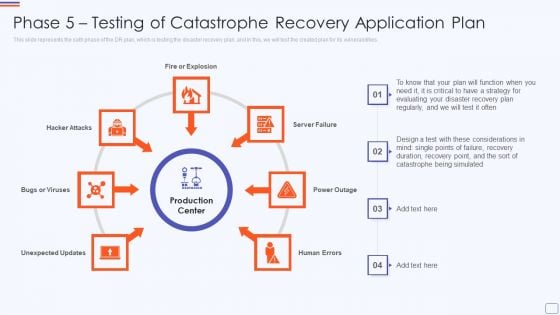
Phase 5 Testing Of Catastrophe Recovery Application Plan Mockup PDF
This slide represents the sixth phase of the DR plan, which is testing the disaster recovery plan, and in this, we will test the created plan for its vulnerabilities. Presenting phase 5 testing of catastrophe recovery application plan mockup pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like fire or explosion, hacker attacks, server failure, power outage, human errors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
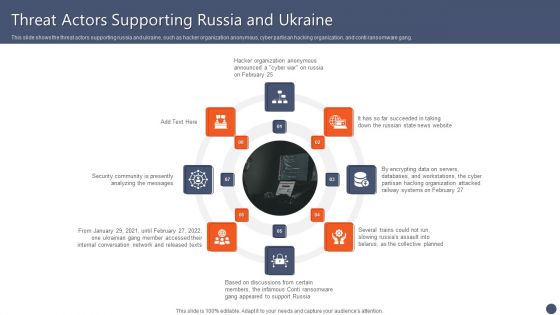
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Importance Of Ethical Hacking Ppt Summary Example PDF
This slide shows the importance of ethical hacking and how ethical hackers can help observe the organizational systems from the hackers viewpoint. Presenting importance of ethical hacking ppt summary example pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organizations, targeted, security, business, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
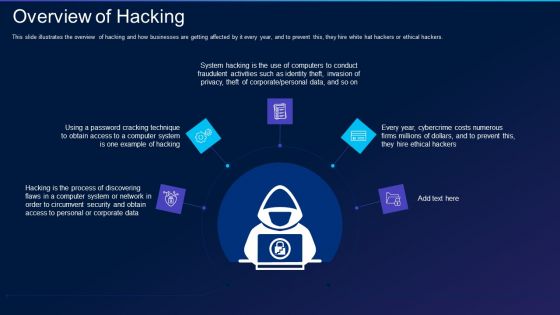
Cyber Exploitation IT Overview Of Hacking Information PDF
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers. This is a cyber exploitation it overview of hacking information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, process, technique. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ukraine Cyberwarfare Cyber Attacks On Ukraine Are Conspicuous By Their Absence Topics Pdf
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. This is a ukraine cyberwarfare cyber attacks on ukraine are conspicuous by their absence topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like government and bank websites of ukraine were momentarily taken offline, team of anti war belarusian hackers claimed that the conflict had affected the countrys railways computer networks, hackers aided by ukraine launched distributed denial of service operations to take down russian websites. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
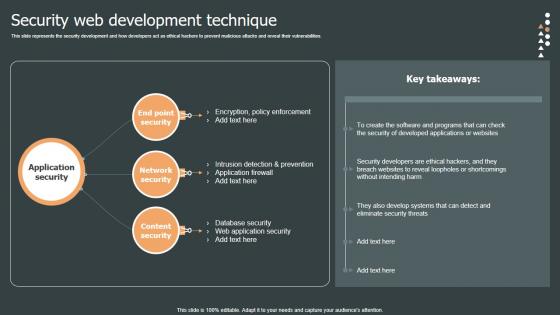
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
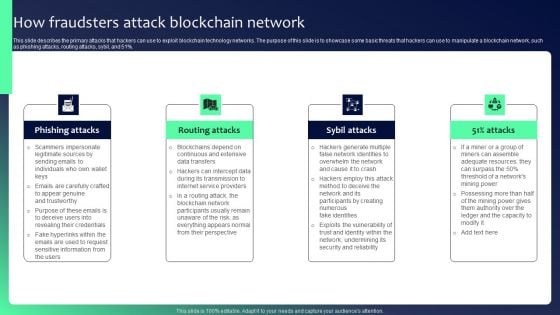
Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
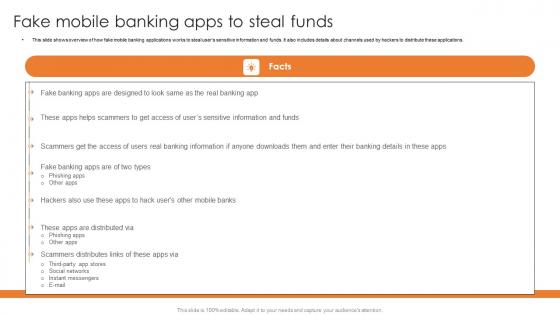
Fake Mobile Banking Apps To Steal Funds Comprehensive Smartphone Banking Ideas Pdf
This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications. Make sure to capture your audiences attention in your business displays with our gratis customizable Fake Mobile Banking Apps To Steal Funds Comprehensive Smartphone Banking Ideas Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications.
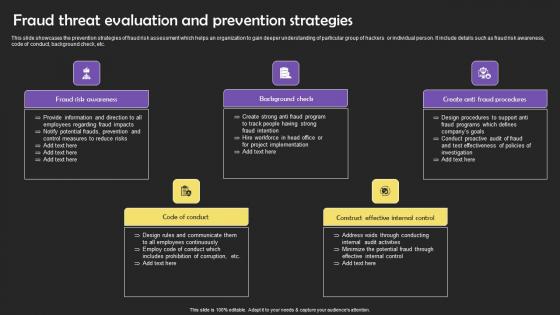
Fraud Threat Evaluation And Prevention Strategies Clipart Pdf
This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc. Showcasing this set of slides titled Fraud Threat Evaluation And Prevention Strategies Clipart Pdf The topics addressed in these templates are Fraud Risk Awareness, Background Check, Code Of Conduct All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc.
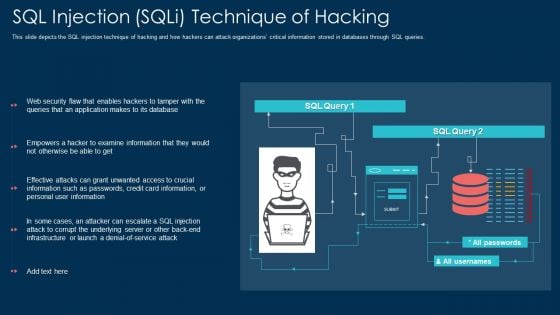
Sql Injection Sqli Technique Of Hacking Ppt Infographic Template Guidelines PDF
This slide depicts the SQL injection technique of hacking and how hackers can attack organizations critical information stored in databases through SQL queries. Deliver and pitch your topic in the best possible manner with this sql injection sqli technique of hacking ppt infographic template guidelines pdf. Use them to share invaluable insights on information, application, database and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
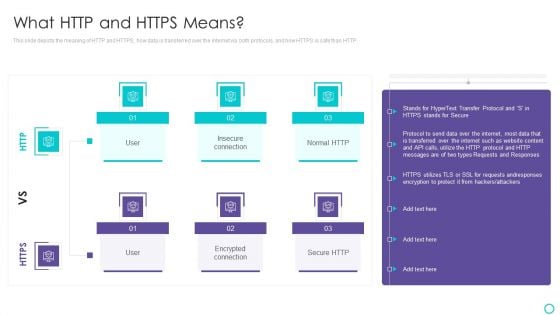
Website Designing And Development Service What HTTP And HTTPS Means Information PDF
This slide depicts the meaning of HTTP and HTTPS, how data is transferred over the internet via both protocols, and how HTTPS is safe than HTTP.Deliver an awe inspiring pitch with this creative Website Designing And Development Service What HTTP And HTTPS Means Information PDF bundle. Topics like Encrypted Connection, Transferred Over The Internet, Hackers Or Attackers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Introduction To Ethical Hacking Introduction PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Is Ethical Hacking Legal Inspiration PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Presenting cyber exploitation it is ethical hacking legal inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like is ethical hacking legal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
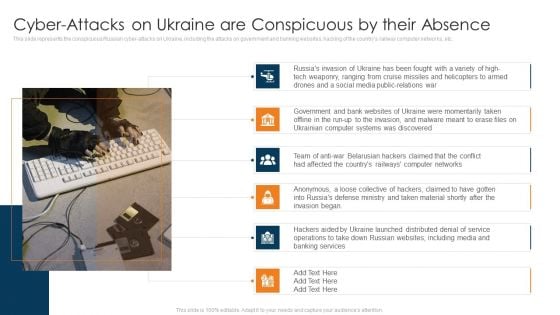
Data Wiper Spyware Attack Cyber Attacks On Ukraine Are Conspicuous Elements PDF
This slide represents the conspicuous Russian cyber-attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc.This is a data wiper spyware attack cyber attacks on ukraine are conspicuous elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine launched distributed, russian websites, belarusian hackers You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
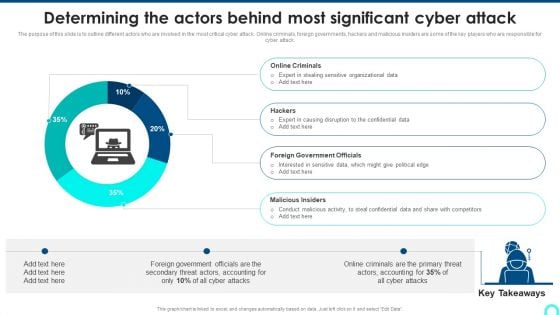
Determining The Actors Behind Most Significant Cyber Attack Download PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver and pitch your topic in the best possible manner with this Determining The Actors Behind Most Significant Cyber Attack Download PDF. Use them to share invaluable insights on Online Criminals, Causing Disruption, Government Officials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
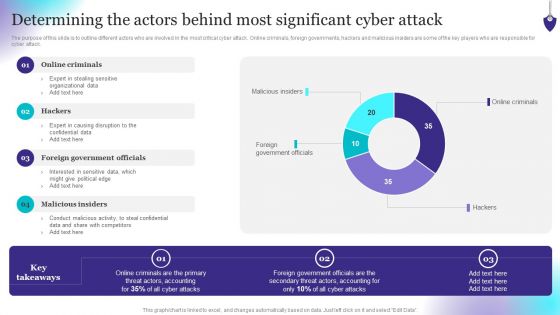
Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
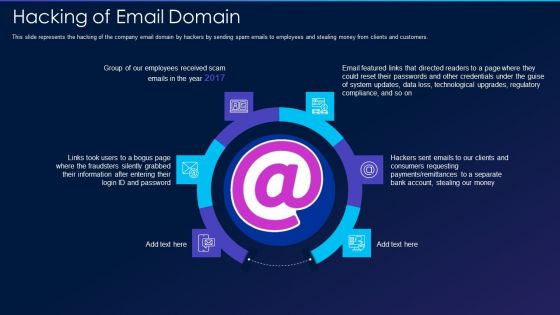
Cyber Exploitation IT Hacking Of Email Domain Professional PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers. Presenting cyber exploitation it hacking of email domain professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hacking of email domain. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ethical Hacking Phase 5 Clearing Tracks Ppt Layouts Files PDF
This slide depicts the clearing tracks phase of ethical hacking and how experienced hackers remove their traces from the system so that no one can follow them. Presenting ethical hacking phase 5 clearing tracks ppt layouts files pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like ethical hacking phase 5 clearing tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Is Ethical Hacking Legal Ppt Gallery Slide PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Presenting is ethical hacking legal ppt gallery slide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network, information, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
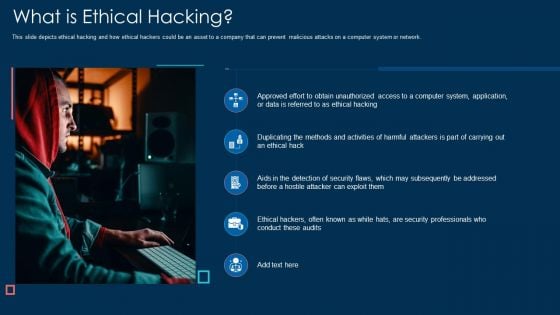
What Is Ethical Hacking Ppt Slides Gridlines PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. Presenting what is ethical hacking ppt slides gridlines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like methods, system, application. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
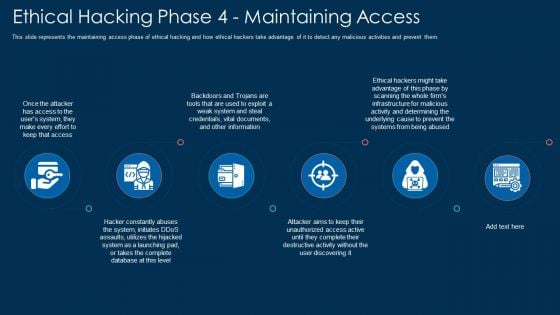
Ethical Hacking Phase 4 Maintaining Access Ppt Professional Grid PDF
This slide represents the maintaining access phase of ethical hacking and how ethical hackers take advantage of it to detect any malicious activities and prevent them. This is a ethical hacking phase 4 maintaining access ppt professional grid pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, determining. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
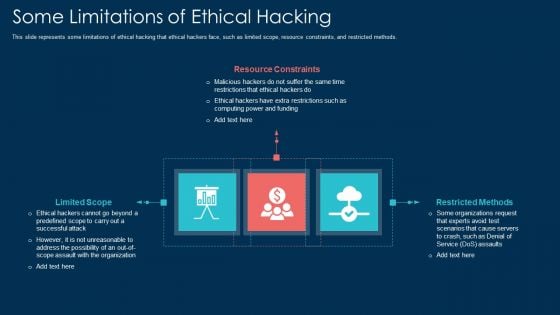
Some Limitations Of Ethical Hacking Ppt Model Pictures PDF
This slide represents some limitations of ethical hacking that ethical hackers face, such as limited scope, resource constraints, and restricted methods. This is a some limitations of ethical hacking ppt model pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like resource constraints, limited scope, restricted methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Hacking Of Our Social Media Accounts Template PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2022 and the amount of money by running scam ads. This is a cyber exploitation it hacking of our social media accounts template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hacking of our social media accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Altered Business Practices Due To Hacking Ideas PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions. Presenting cyber exploitation it altered business practices due to hacking ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like altered business practices due to hacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
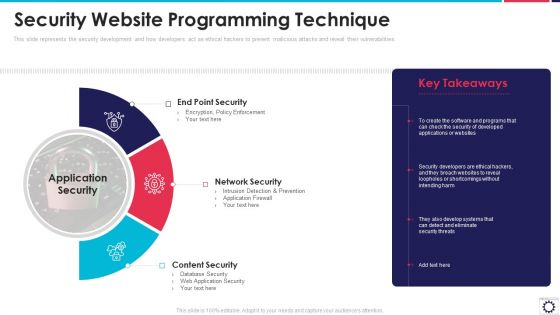
Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
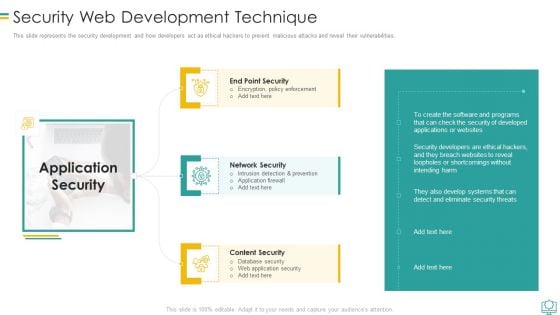
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
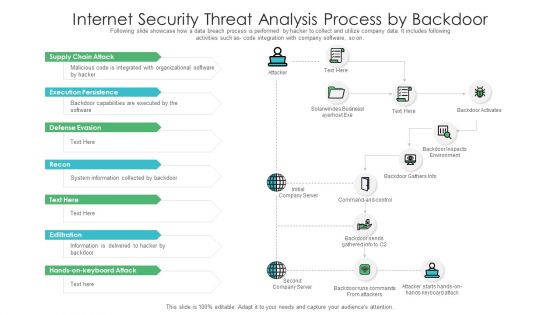
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home