Hacker
Virtual Security Hazards And Network Hacking Icon Diagrams Pdf
Pitch your topic with ease and precision using this Virtual Security Hazards And Network Hacking Icon Diagrams Pdf. This layout presents information on Virtual Security, Hazards, Network Hacking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Virtual Security Hazards And Network Hacking Icon Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
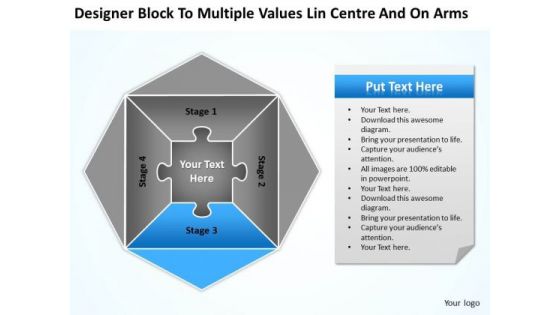
Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides
We present our block to multiple values lin centre and on arms ppt business plan template PowerPoint Slides.Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download our Puzzles or Jigsaws PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Process and Flows PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to abstract, binary, business, code, commerce, communication, computer, concept, connect, connection, corporate, cyberspace, data, digital, download, ecommerce, electronic, futuristic, global, hacker, information, internet, multiple, network, networking, online, program, programming, security, software, tech, technology, values. The prominent colors used in the PowerPoint template are Blue, Gray, White. Get classy with our Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides. They ensure A-list clients.
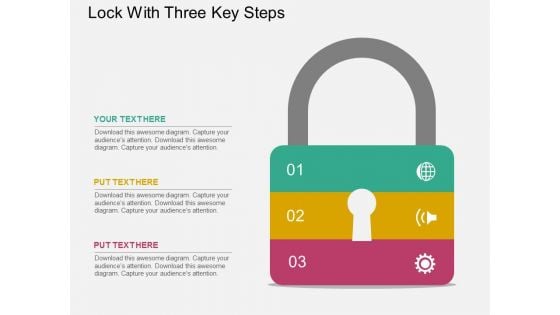
Lock With Three Key Steps Powerpoint Templates
This PowerPoint template has been designed with lock and three key steps. This editable slide helps to display the key concepts for business success. Use this PPT slide for your business and marketing related presentations.
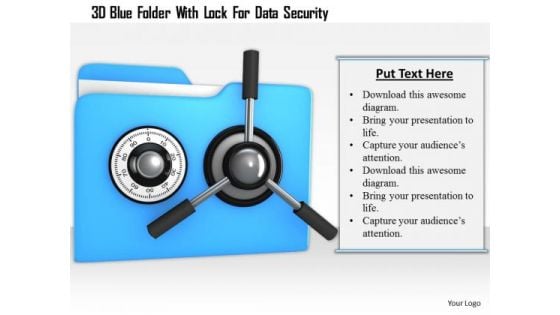
Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.
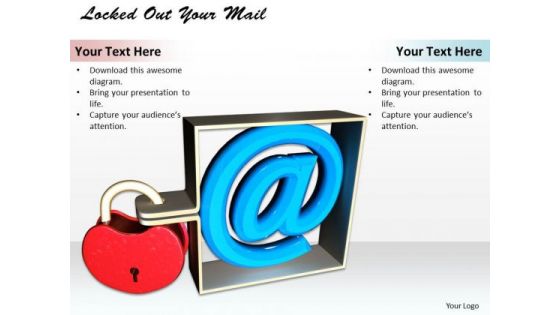
Stock Photo Locked Out Your Mail PowerPoint Template
Draw On The Experience Of Our stock photo Locked Out Your Mail powerpoint template Powerpoint Templates. They Imbibe From Past Masters. Drink The Nectar Of Our Stock Photo Locked Out Your Mail PowerPoint Template Powerpoint Templates. Give Your Thoughts A Long Life.
White And Black Hat Seo Techniques Ppt Slides
This is a white and black hat seo techniques ppt slides. This is a two stage process. The stages in this process are white hat, black hat.
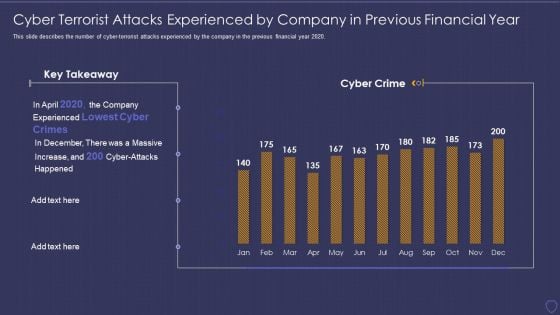
Global Cyber Terrorism Incidents On The Rise IT Cyber Terrorist Attacks Experienced Formats PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it cyber terrorist attacks experienced formats pdf bundle. Topics like cyber terrorist attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
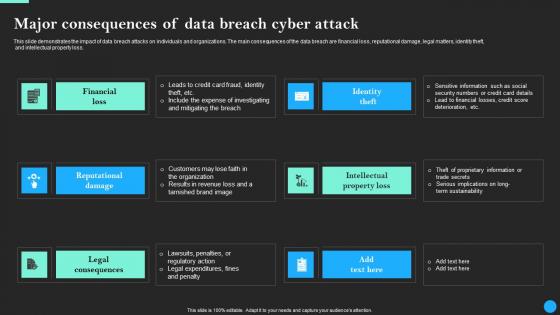
Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.

Comparison Between White Black And Grey Hat SEO Training Ppt
The following slide depicts the comparison of white, black, and grey hat SEO. The multiple parameters used for comparison are search engine guidelines, ideal for long term, time taken to deliver results, cost involved long term, and risk involved.
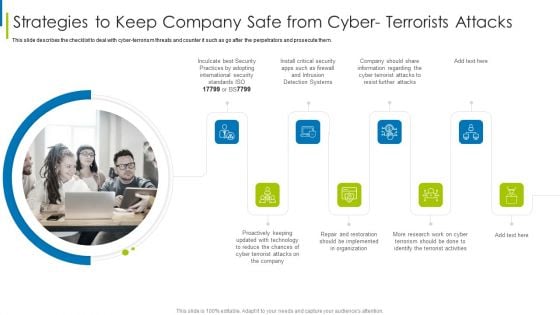
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
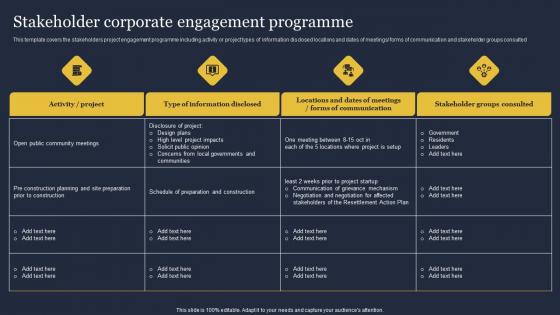
Stakeholder Corporate Engagement Programme Critical Incident Communication Themes Pdf
This template covers the stakeholders project engagement programme including activity or project types of information disclosed locations and dates of meetings forms of communication and stakeholder groups consulted This modern and well arranged Stakeholder Corporate Engagement Programme Critical Incident Communication Themes Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This template covers the stakeholders project engagement programme including activity or project types of information disclosed locations and dates of meetings forms of communication and stakeholder groups consulted

Table Of Contents For White Hat Hacking Ppt Layouts Ideas PDF
Deliver and pitch your topic in the best possible manner with this table of contents for white hat hacking ppt layouts ideas pdf. Use them to share invaluable insights on techniques, system, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
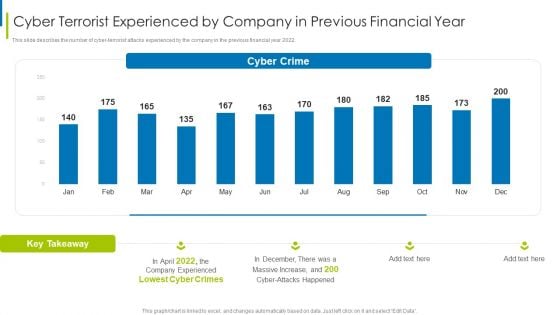
Cyber Terrorism Assault Cyber Terrorist Experienced By Company In Previous Financial Year Sample PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2022.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorist experienced by company in previous financial year sample pdf bundle. Topics like Increased Costs, Reputational Damage, Intellectual Property Theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

White Hat Hacking Whats New In Cehv11 Ppt Pictures Sample PDF
This slide represents the new concepts added to the Certified Ethical Hacking program, including hacking challenges on a higher level, new attack techniques, enumeration, and others. Presenting white hat hacking whats new in cehv11 ppt pictures sample pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like techniques, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
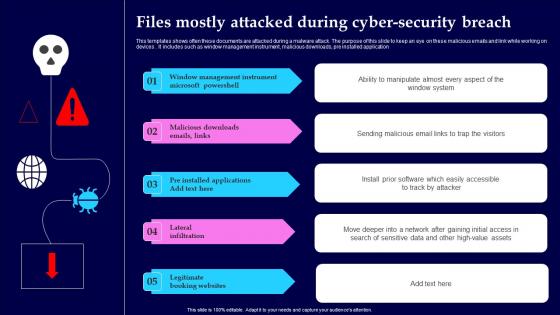
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application
Business Diagram Three Circles With Lock For Safety Presentation Template
Three air balloons with text boxes are used to craft this power point template slide. This PPT slide contains the concept of business text representation. This slide is usable for business and marketing related presentations.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
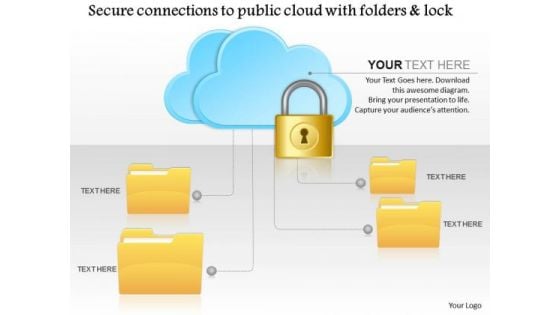
Business Diagram Secure Connections To The Public Cloud With Folders And Lock Ppt Slide
This technical slide has been designed with graphic of folders and cloud with lock. This PPT slide depicts the concept of secure connections. It focuses on the data safety in cloud technology. Use this diagram for data safety related presentations.
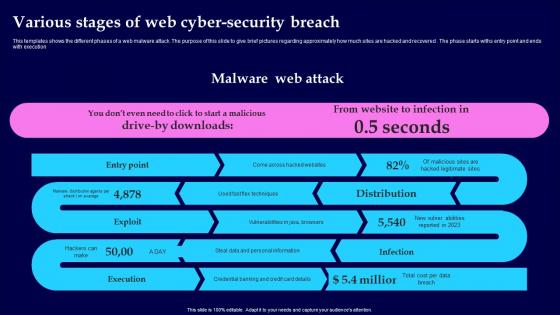
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution

Students Wearing Black And White Hats During Graduation Day Ppt PowerPoint Presentation Inspiration Example File PDF
Presenting this set of slides with name students wearing black and white hats during graduation day ppt powerpoint presentation inspiration example file pdf. This is a three stage process. The stages in this process are students wearing black and white hats during graduation day. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
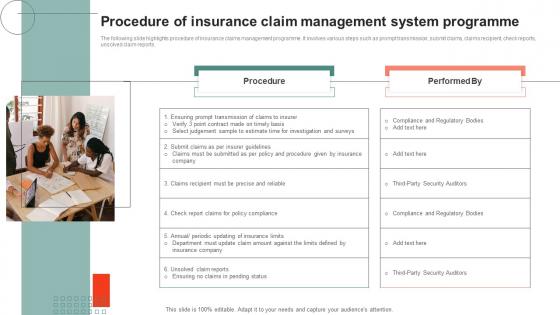
Procedure Of Insurance Claim Management System Programme Demonstration Pdf
The following slide highlights procedure of insurance claims management programme. It involves various steps such as prompt transmission, submit claims, claims recipient, check reports, unsolved claim reports. Showcasing this set of slides titled Procedure Of Insurance Claim Management System Programme Demonstration Pdf The topics addressed in these templates are Procedure, Claim Management System, Programme All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights procedure of insurance claims management programme. It involves various steps such as prompt transmission, submit claims, claims recipient, check reports, unsolved claim reports.

Five Years Timeline Roadmap For White Hat Hacking Structure
We present our five years timeline roadmap for white hat hacking structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five years timeline roadmap for white hat hacking structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
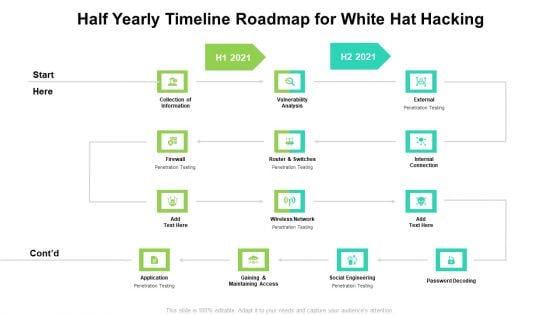
Half Yearly Timeline Roadmap For White Hat Hacking Guidelines
We present our half yearly timeline roadmap for white hat hacking guidelines. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly timeline roadmap for white hat hacking guidelines in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
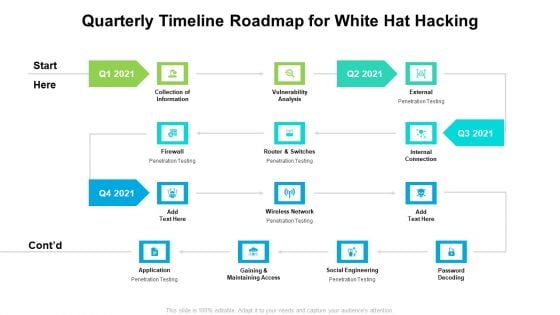
Quarterly Timeline Roadmap For White Hat Hacking Slides
We present our quarterly timeline roadmap for white hat hacking slides. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly timeline roadmap for white hat hacking slides in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
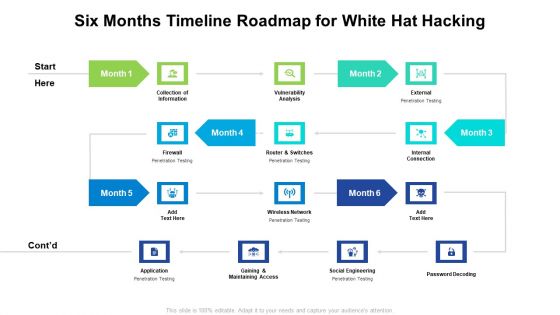
Six Months Timeline Roadmap For White Hat Hacking Themes
We present our six months timeline roadmap for white hat hacking themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months timeline roadmap for white hat hacking themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
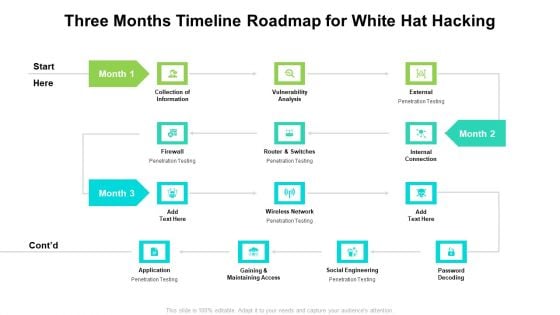
Three Months Timeline Roadmap For White Hat Hacking Topics
We present our three months timeline roadmap for white hat hacking topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months timeline roadmap for white hat hacking topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Icons Slide For White Hat Hacking Ppt Inspiration Sample PDF
Presenting our innovatively structured icons slide for white hat hacking ppt inspiration sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
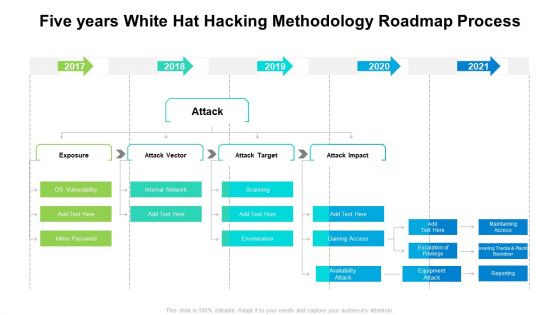
Five Years White Hat Hacking Methodology Roadmap Process Slides
Presenting our innovatively structured five years white hat hacking methodology roadmap process slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
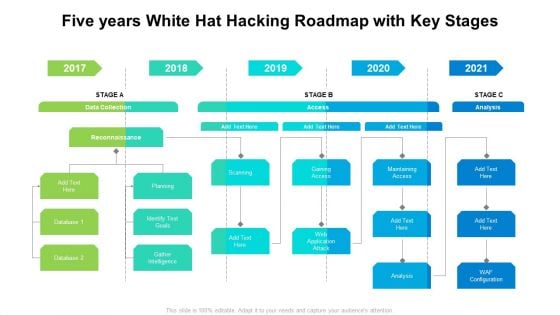
Five Years White Hat Hacking Roadmap With Key Stages Topics
Introducing our five years white hat hacking roadmap with key stages topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
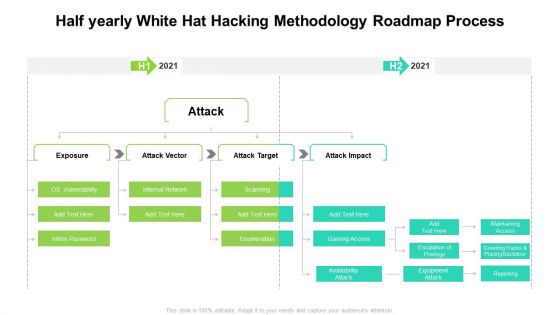
Half Yearly White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured half yearly white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
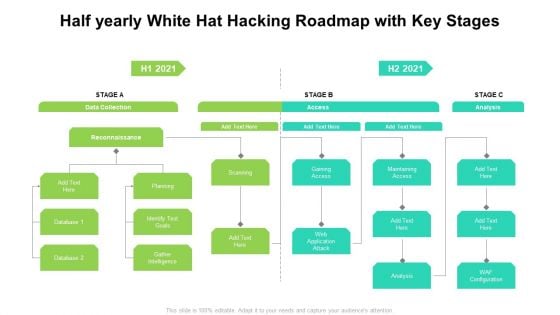
Half Yearly White Hat Hacking Roadmap With Key Stages Brochure
Introducing our half yearly white hat hacking roadmap with key stages brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
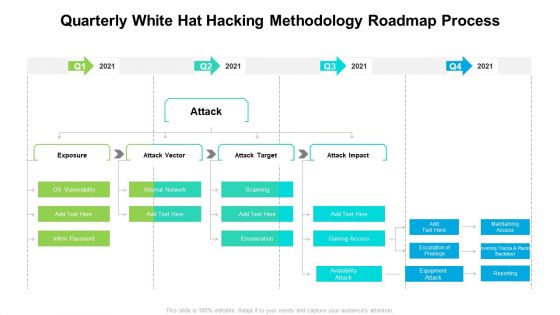
Quarterly White Hat Hacking Methodology Roadmap Process Information
Presenting our innovatively structured quarterly white hat hacking methodology roadmap process information Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
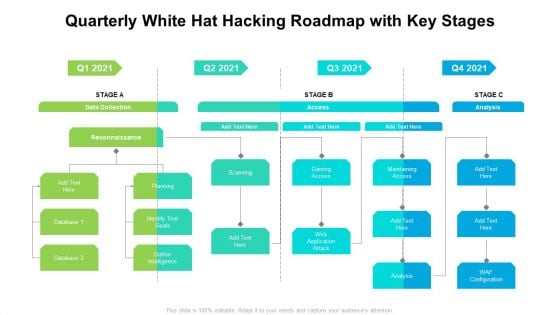
Quarterly White Hat Hacking Roadmap With Key Stages Designs
Introducing our quarterly white hat hacking roadmap with key stages designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
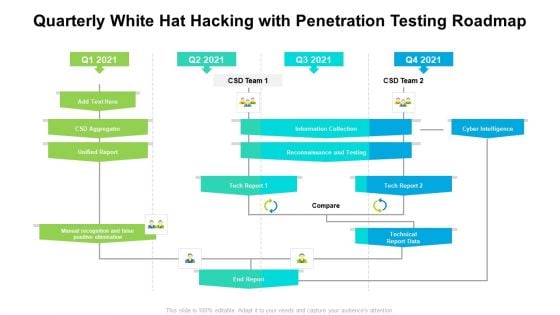
Quarterly White Hat Hacking With Penetration Testing Roadmap Rules
Presenting our jaw dropping quarterly white hat hacking with penetration testing roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Six Months White Hat Hacking Methodology Roadmap Process Infographics
Presenting our innovatively structured six months white hat hacking methodology roadmap process infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
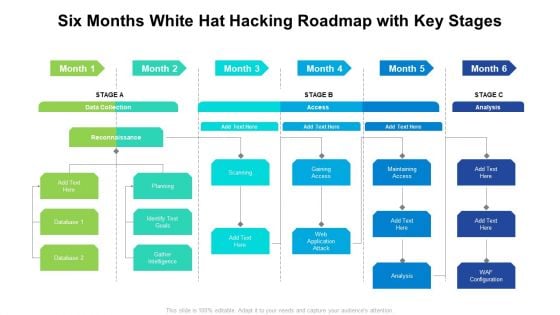
Six Months White Hat Hacking Roadmap With Key Stages Infographics
Introducing our six months white hat hacking roadmap with key stages infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
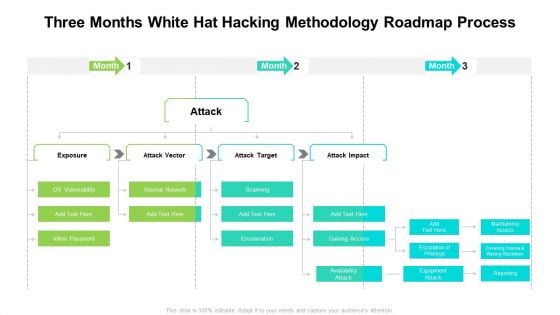
Three Months White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured three months white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
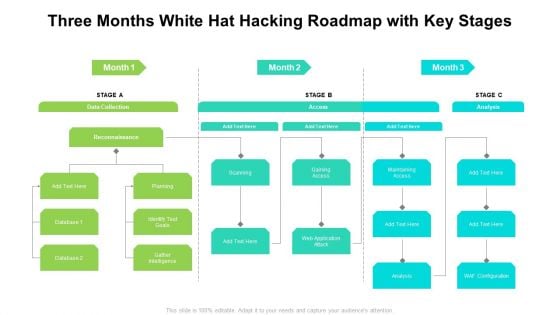
Three Months White Hat Hacking Roadmap With Key Stages Guidelines
Introducing our three months white hat hacking roadmap with key stages guidelines. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Mental Health Hacks Reddit that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Quizlet Match Hack In Powerpoint And Google Slides Cpb
Introducing our well designed Quizlet Match Hack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Quizlet Match Hack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Quizlet Match Hack In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
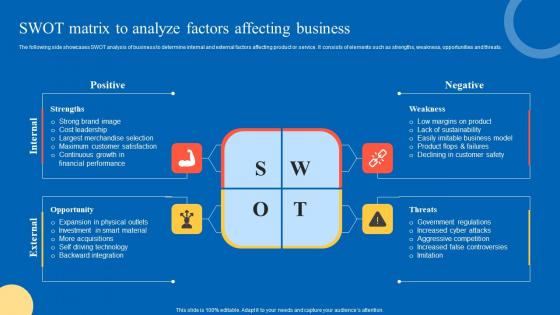
SWOT Matrix To Analyze Strategic Guide For Marketing Program Microsoft Pdf
The following side showcases SWOT analysis of business to determine internal and external factors affecting product or service. It consists of elements such as strengths, weakness, opportunities and threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download SWOT Matrix To Analyze Strategic Guide For Marketing Program Microsoft Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following side showcases SWOT analysis of business to determine internal and external factors affecting product or service. It consists of elements such as strengths, weakness, opportunities and threats.
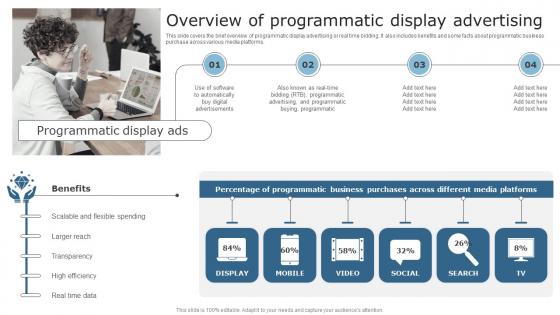
Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf
This slide covers the brief overview of programmatic display advertising or real time bidding. It also includes benefits and some facts about programmatic business purchase across various media platforms. Presenting this PowerPoint presentation, titled Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide covers the brief overview of programmatic display advertising or real time bidding. It also includes benefits and some facts about programmatic business purchase across various media platforms.
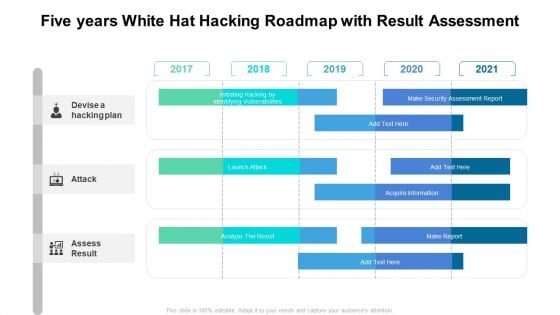
Five Years White Hat Hacking Roadmap With Result Assessment Guidelines
Presenting the five years white hat hacking roadmap with result assessment guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Five Years White Hat Hacking With Penetration Testing Roadmap Icons
Presenting our jaw dropping five years white hat hacking with penetration testing roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
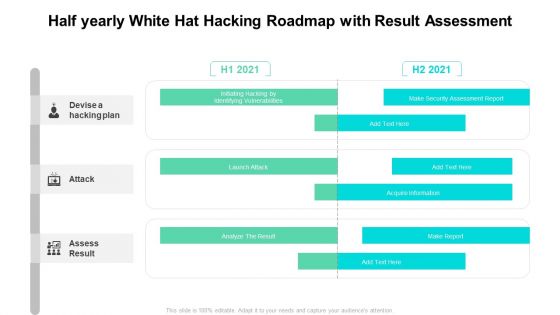
Half Yearly White Hat Hacking Roadmap With Result Assessment Graphics
Presenting the half yearly white hat hacking roadmap with result assessment graphics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
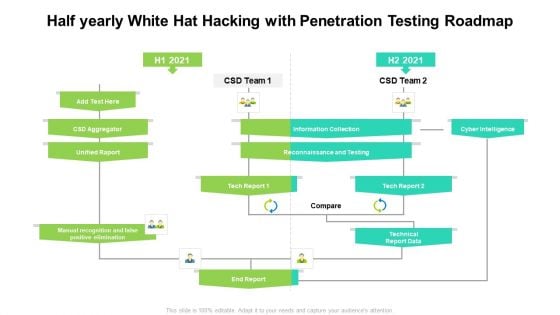
Half Yearly White Hat Hacking With Penetration Testing Roadmap Designs
Presenting our jaw dropping half yearly white hat hacking with penetration testing roadmap designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
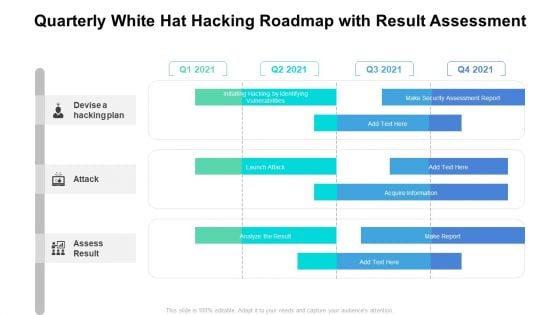
Quarterly White Hat Hacking Roadmap With Result Assessment Microsoft
Presenting the quarterly white hat hacking roadmap with result assessment microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
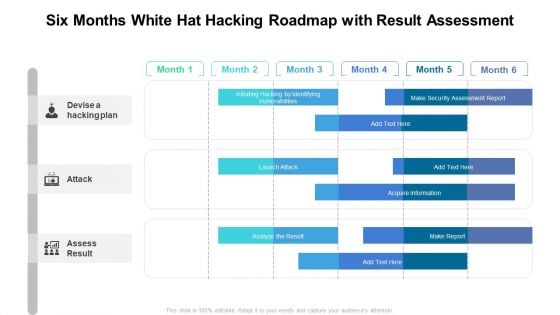
Six Months White Hat Hacking Roadmap With Result Assessment Rules
Presenting the six months white hat hacking roadmap with result assessment rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
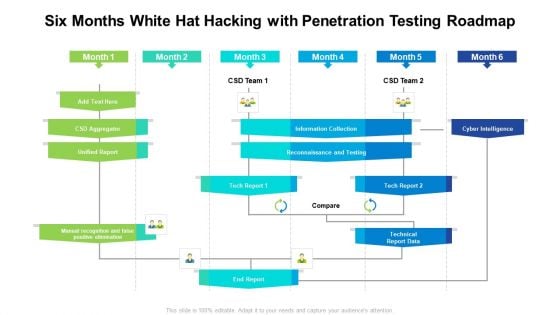
Six Months White Hat Hacking With Penetration Testing Roadmap Infographics
Presenting our jaw dropping six months white hat hacking with penetration testing roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
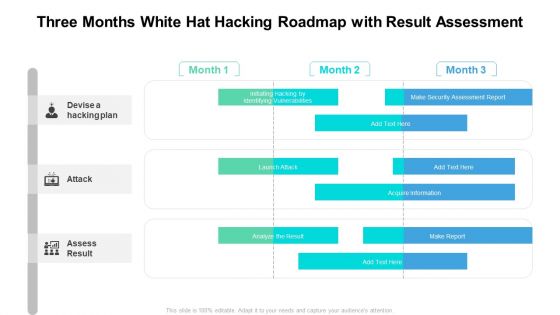
Three Months White Hat Hacking Roadmap With Result Assessment Mockup
Presenting the three months white hat hacking roadmap with result assessment mockup. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
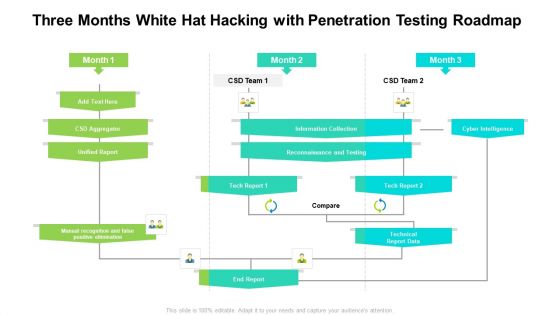
Three Months White Hat Hacking With Penetration Testing Roadmap Professional
Presenting our jaw dropping three months white hat hacking with penetration testing roadmap professional. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

White Hat Hacking Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty seven slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
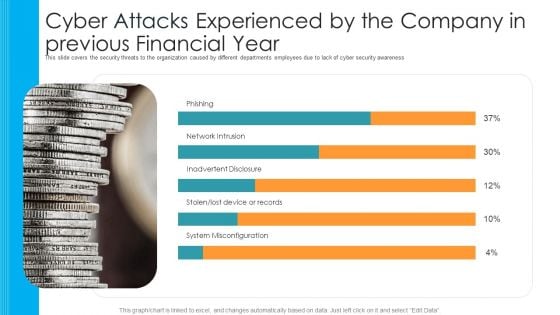
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Brainstorming Session Six Thinking Hats Presentation Images
This is a brainstorming session six thinking hats presentation images. This is a six stage process. The stages in this process are focus, white hat data driven inputs, green hat outside the box thinkers, yellow hat focused on the positives, black hat opposing viewpoints, red hat feelings and intuitions, blue hat idea collector leader.
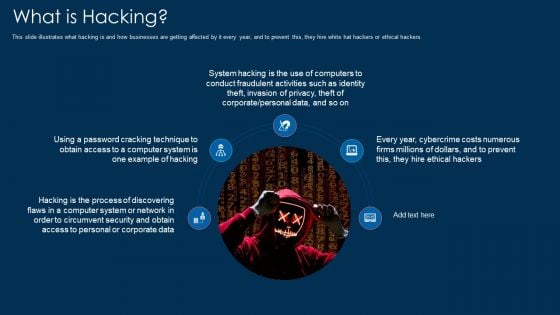
What Is Hacking Ppt Gallery Layouts PDF
Presenting what is hacking ppt gallery layouts pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like system, technique, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Infrastructure Security Budget Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe inspiring pitch with this creative it infrastructure security budget hacking prevention awareness training for it security graphics pdf bundle. Topics like security, services, costs, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
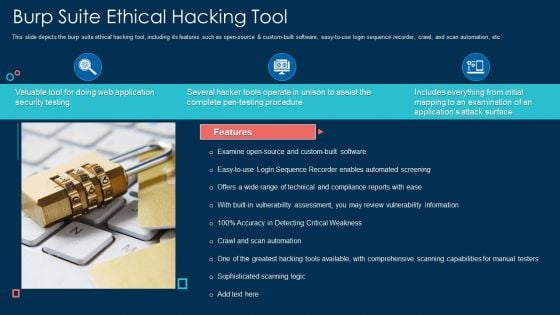
Burp Suite Ethical Hacking Tool Ppt Portfolio Skills PDF
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Hacking Prevention Awareness Training For IT Security Icons Slide Hacking Prevention Awareness Training For IT Security Information PDF
Introducing our well designed hacking prevention awareness training for it security icons slide hacking prevention awareness training for it security information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

 Home
Home