Login

Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates
We present our systematic concentric process diagram business plan outline PowerPoint templates.Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Shapes PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download and present our Business PowerPoint Templates because It can Bubble and burst with your ideas. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity.Use these PowerPoint slides for presentations relating to Login, cyber, radar, protocol, elimination, secure, corporate, future, concept, lan, infrastructure, data, process, scan, viral, technology, security, wan, abstract,creative, illustration, system, up, focus, terrorism, futuristic, recognition, precaution, check, processing, zoom, information, background, virus, conceptual,precautionary, pattern, systematic, measure. The prominent colors used in the PowerPoint template are Blue, Blue light, White. Force out your enemies with our Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates. Just download, type and present.
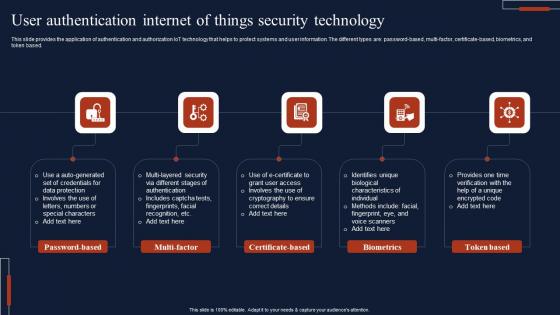
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
Templates Download Diverging Processes Arrows Network Software PowerPoint
We present our templates download diverging processes Arrows Network Software PowerPoint.Use our Circle Charts PowerPoint Templates because this Diagram pinpoints the critical paths and areas in your process and set the timelines for their completion. Download our Arrows PowerPoint Templates because it helps you to inform your team of your innovative ideas. Download our Business PowerPoint Templates because the great Bald headed Eagle embodies your personality. the eagle eye to seize upon the smallest of opportunities. Download and present our Shapes PowerPoint Templates because this diagram depicts the essence of this chain reaction like sequence of events. Use our Flow Charts PowerPoint Templates because this an appropriate template to get your ideas across to your target audience.Use these PowerPoint slides for presentations relating to banner, bar, black, blue, box, business, button, calendar, clock, collection, colorful, corporate, delete, design, download, editable, elements, empty, eps, form, frame, green, icons, illustration, key, list, loading, log, login, mail, objects, orange, ornaments, page, price, ribbons, seal, search, set, sticker, stock, theme, user, vector, warning, web, webdesign, website, white. The prominent colors used in the PowerPoint template are Pink, Red, Yellow. Customers tell us our templates download diverging processes Arrows Network Software PowerPoint will make you look like a winner. PowerPoint presentation experts tell us our black PowerPoint templates and PPT Slides are One-of-a-kind. People tell us our templates download diverging processes Arrows Network Software PowerPoint are Adorable. People tell us our black PowerPoint templates and PPT Slides are Romantic. Customers tell us our templates download diverging processes Arrows Network Software PowerPoint will get their audience's attention. People tell us our button PowerPoint templates and PPT Slides will make you look like a winner. Establish the fundamentals of the venture. Fix the parameters. with our Templates Download Diverging Processes Arrows Network Software PowerPoint.
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security.
Stock Photo Cube With Key And Lock Data Protection Concept PowerPoint Slide
Graphic of cube with lock and key has been used to design this power point image template. This image template contains the concept of data protection. This image template can e used for data related presentations.
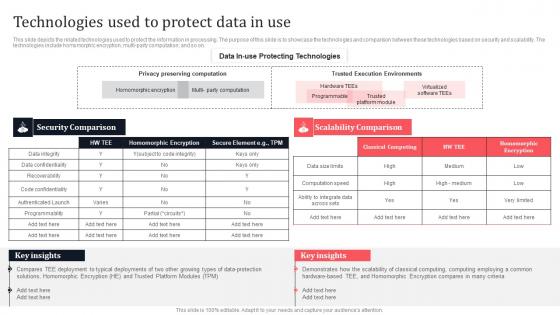
Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
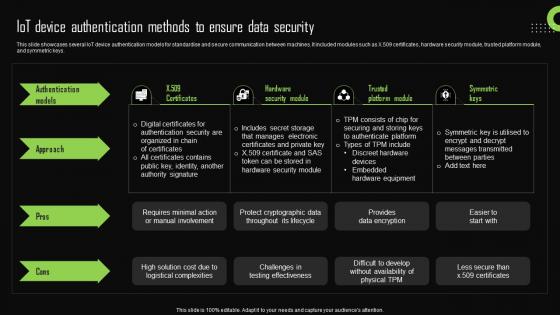
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Emotional Appeal Authenticity that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Approved Probiotics In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Approved Probiotics In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Approved Probiotics that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Approved Probiotics In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
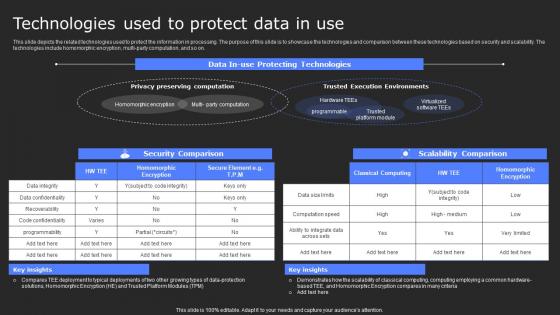
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
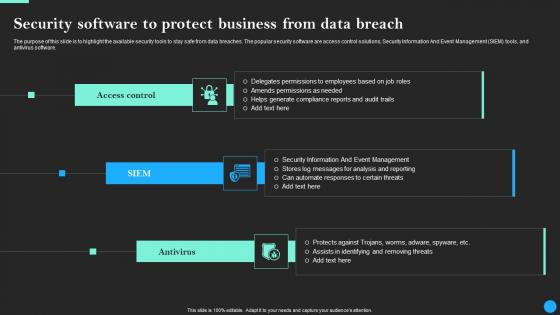
Security Software To Protect Business From Data Breach Prevention Elements Pdf
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.
Password Protection Information Security Icon Ppt Powerpoint Presentation Visual Aids Portfolio
This is a password protection information security icon ppt powerpoint presentation visual aids portfolio. This is a three stage process. The stages in this process are password, access approval, authentication icon.

Password Protection Internet Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Cybernetic hand inserting user name and password Create the right environment for prosperity. Fashion the right conditions with our Password Protection Internet Security PowerPoint Backgrounds And Templates 1210.

Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc.
Password Recorder In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Password Recorder In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Password Recorder that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Password Recorder In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IOT Authorization And Authentication For Cybersecurity Management Sample Pdf
This slide provides multiple authorization protocols that helps businesses and organizations to ensure effective and secure management of operations and data transmission. The three protocols are one-way, two-way, and three-way authentication. Showcasing this set of slides titled IOT Authorization And Authentication For Cybersecurity Management Sample Pdf The topics addressed in these templates are One Way Authentication, Two Way Authentication All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides multiple authorization protocols that helps businesses and organizations to ensure effective and secure management of operations and data transmission. The three protocols are one-way, two-way, and three-way authentication.
Security And Identity Platform Ppt Background
This is a security and identity platform ppt background. This is a eight stage process. The stages in this process are big data platform, database platform, data warehouse platform, e commerce platforms, bpm platform, security and identity platform, development platform, integration platforms.
Safety And Authentication Vector Icon Ppt Powerpoint Presentation Model Rules
This is a safety and authentication vector icon ppt powerpoint presentation model rules. This is a one stage process. The stages in this process are password, access approval, authentication icon.
Laptop With Lock Password Authentication Vector Icon Ppt Powerpoint Presentation Icon Summary
This is a laptop with lock password authentication vector icon ppt powerpoint presentation icon summary. This is a one stage process. The stages in this process are password, access approval, authentication icon.
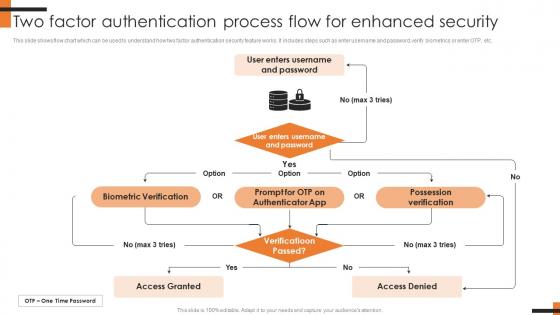
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
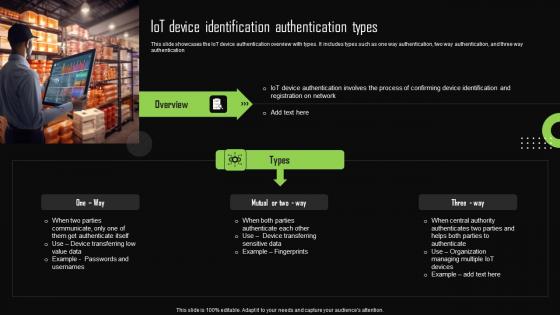
Iot Device Identification Authentication Types Iot Device Management Summary Pdf
This slide showcases the IoT device authentication overview with types. It includes types such as one way authentication, two way authentication, and three way authentication. Do you know about Slidesgeeks Iot Device Identification Authentication Types Iot Device Management Summary Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcases the IoT device authentication overview with types. It includes types such as one way authentication, two way authentication, and three way authentication.
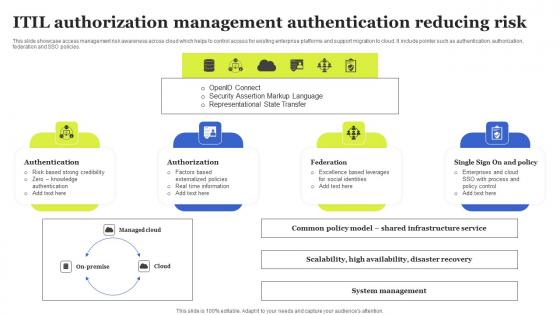
ITIL Authorization Management Authentication Reducing Risk Brochure Pdf
This slide showcase access management risk awareness across cloud which helps to control access for existing enterprise platforms and support migration to cloud. It include pointer such as authentication, authorization, federation and SSO policies. Showcasing this set of slides titled ITIL Authorization Management Authentication Reducing Risk Brochure Pdf The topics addressed in these templates are Authentication, Authorization, Federation, Common Policy Model All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase access management risk awareness across cloud which helps to control access for existing enterprise platforms and support migration to cloud. It include pointer such as authentication, authorization, federation and SSO policies.
Office Basic Authentication Report In Powerpoint And Google Slides Cpb
Introducing our well designed Office Basic Authentication Report In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Office Basic Authentication Report. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Office Basic Authentication Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.
Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Strategic Agenda For Data Protection Icon Template Pdf
Pitch your topic with ease and precision using this Cyber Security Strategic Agenda For Data Protection Icon Template Pdf. This layout presents information on Cyber Security Strategic, Agenda For Data Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Strategic Agenda For Data Protection Icon Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
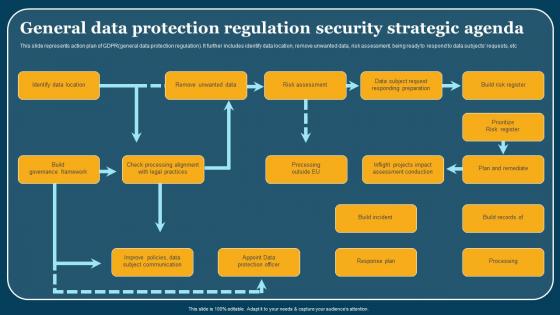
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc.
End To End Scenario Icon For Cloud Protection Brochure Pdf
Showcasing this set of slides titled End To End Scenario Icon For Cloud Protection Brochure Pdf The topics addressed in these templates are End To End Scenario, Icon Cloud Protection All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our End To End Scenario Icon For Cloud Protection Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Business Data Protection Policy Administration Icon Information Pdf
Pitch your topic with ease and precision using this Business Data Protection Policy Administration Icon Information Pdf. This layout presents information on Business Data Protection, Policy Administration, Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Business Data Protection Policy Administration Icon Information Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
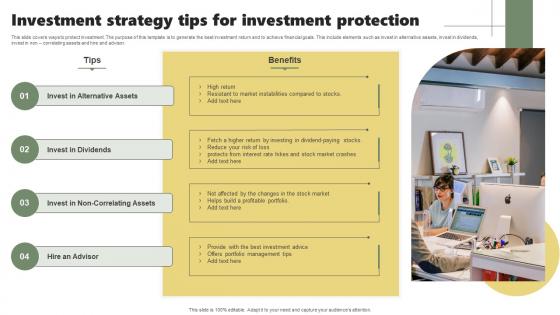
Investment Strategy Tips For Investment Protection Download Pdf
This slide covers ways to protect investment. The purpose of this template is to generate the best investment return and to achieve financial goals. This include elements such as invest in alternative assets, invest in dividends, invest in non correlating assets and hire and advisor. Showcasing this set of slides titled Investment Strategy Tips For Investment Protection Download Pdf. The topics addressed in these templates are Invest Alternative Assets, Invest Dividends, Hire Advisor. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers ways to protect investment. The purpose of this template is to generate the best investment return and to achieve financial goals. This include elements such as invest in alternative assets, invest in dividends, invest in non correlating assets and hire and advisor.

Asset Protection In Powerpoint And Google Slides Cpb
Introducing our well designed Asset Protection In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Asset Protection As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Asset Protection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
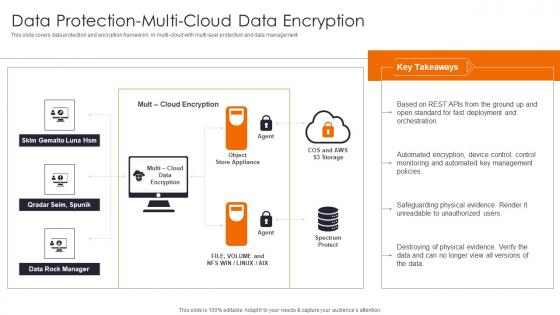
Data Protection Multi Cloud Enhancing Workload Efficiency Through Cloud Architecture Background Pdf
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management The Data Protection Multi Cloud Enhancing Workload Efficiency Through Cloud Architecture Background Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management
Icon For Ensuring Data Protection In Technology Transformation For Local Administration Microsoft pdf
Showcasing this set of slides titled Icon For Ensuring Data Protection In Technology Transformation For Local Administration Microsoft pdf. The topics addressed in these templates are Icon, Ensuring Data Protection, Technology Transformation, Local Administration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Icon For Ensuring Data Protection In Technology Transformation For Local Administration Microsoft pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
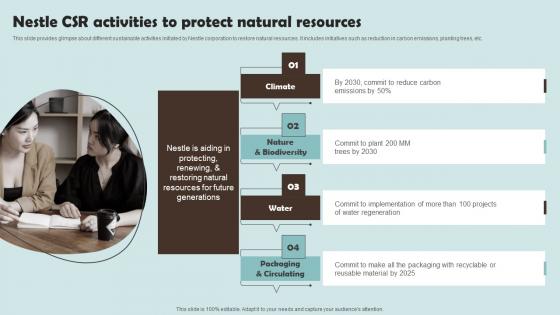
Nestle CSR Activities To Protect Natural Resources Outline Of Nestle Management Portrait Pdf
This slide provides glimpse about different sustainable activities initiated by Nestle corporation to restore natural resources. It includes initiatives such as reduction in carbon emissions, planting trees, etc.This Nestle CSR Activities To Protect Natural Resources Outline Of Nestle Management Portrait Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Nestle CSR Activities To Protect Natural Resources Outline Of Nestle Management Portrait Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides glimpse about different sustainable activities initiated by Nestle corporation to restore natural resources. It includes initiatives such as reduction in carbon emissions, planting trees, etc.

Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Take your projects to the next level with our ultimate collection of Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud.

Anti Virus Computer PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with modern mouse connected to word Anti-Virus Get an exceptional response with our Anti Virus Computer PowerPoint Templates And PowerPoint Backgrounds 0211. Your ideas will be applauded by one and all.

Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with modern mouse connected to word Anti-Virus Award yourself with our Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211. Your thoughts deserve the distinction.
Password Protection For Cyber Security Threat Ppt PowerPoint Presentation Icon Show PDF
Persuade your audience using this password protection for cyber security threat ppt powerpoint presentation icon show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including password protection for cyber security threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Password Protection On Laptop For Security Vector Icon Ppt PowerPoint Presentation Gallery Slide Download PDF
Persuade your audience using this password protection on laptop for security vector icon ppt powerpoint presentation gallery slide download pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including password protection on laptop for security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
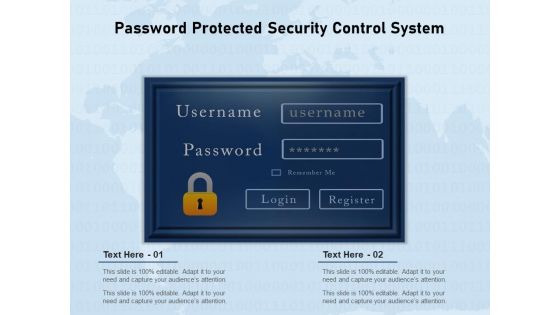
Password Protected Security Control System Ppt PowerPoint Presentation Styles Ideas PDF
Persuade your audience using this password protected security control system ppt powerpoint presentation styles ideas pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including password protected security control system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
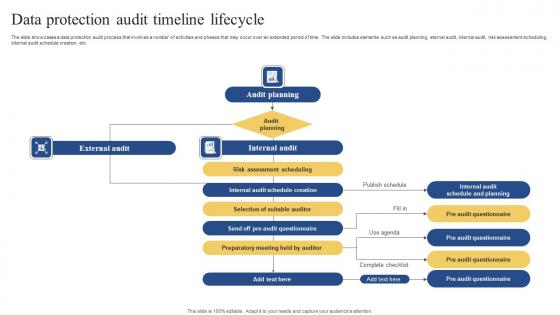
Data Protection Audit Timeline Lifecycle Pictures Pdf
The slide showcases a data protection audit process that involves a number of activities and phases that may occur over an extended period of time. The slide includes elements such as audit planning, eternal audit, internal audit, risk assessment scheduling, internal audit schedule creation, etc. Pitch your topic with ease and precision using this Data Protection Audit Timeline Lifecycle Pictures Pdf. This layout presents information on Audit Planning, Audit Planning, Internal Audit. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcases a data protection audit process that involves a number of activities and phases that may occur over an extended period of time. The slide includes elements such as audit planning, eternal audit, internal audit, risk assessment scheduling, internal audit schedule creation, etc.
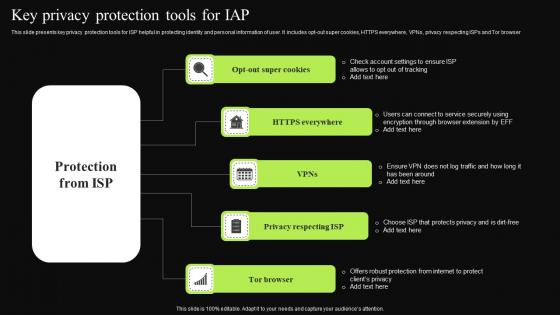
Key Privacy Protection Tools For IAP Designs Pdf
This slide presents key privacy protection tools for ISP helpful in protecting identity and personal information of user. It includes opt out super cookies, HTTPS everywhere, VPNs, privacy respecting ISPs and Tor browser Showcasing this set of slides titled Key Privacy Protection Tools For IAP Designs Pdf. The topics addressed in these templates are Https Everywhere, Privacy Respecting Isp, Tor Browser. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents key privacy protection tools for ISP helpful in protecting identity and personal information of user. It includes opt out super cookies, HTTPS everywhere, VPNs, privacy respecting ISPs and Tor browser
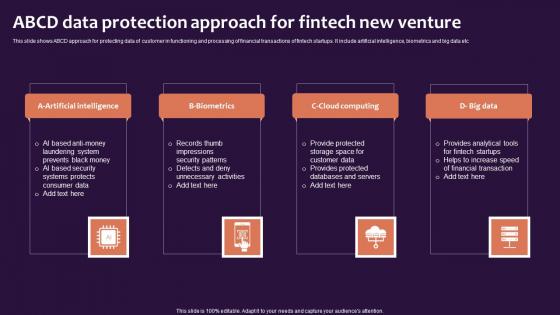
ABCD Data Protection Approach For Fintech New Venture Ideas Pdf
This slide shows ABCD approach for protecting data of customer in functioning and processing of financial transactions of fintech startups. It include artificial intelligence, biometrics and big data etc. Showcasing this set of slides titled ABCD Data Protection Approach For Fintech New Venture Ideas Pdf. The topics addressed in these templates are Biometrics, Cloud Computing, Big Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows ABCD approach for protecting data of customer in functioning and processing of financial transactions of fintech startups. It include artificial intelligence, biometrics and big data etc.
Vaccine Protection Against Omicron In Powerpoint And Google Slides Cpb
Introducing our well designed Vaccine Protection Against Omicron In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Vaccine Protection Against Omicron. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Vaccine Protection Against Omicron In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Child Protective Services In Powerpoint And Google Slides Cpb
Introducing our well designed Child Protective Services In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Child Protective Services. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Child Protective Services In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cathodic Protection In Powerpoint And Google Slides Cpb
Introducing our well designed Cathodic Protection In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cathodic Protection. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cathodic Protection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Service Management Architecture Ppt Slides
This is a security service management architecture ppt slides. This is a five stage process. The stages in this process are architecture, business, communication.

Consumer Protection Laws Might Result In Powerpoint And Google Slides Cpb
Introducing our well designed Consumer Protection Laws Might Result In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Consumer Protection Laws Might Result. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Consumer Protection Laws Might Result In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Virus Internet PowerPoint Template 0910
Virus alert in web browser address bar with cursor hovering over warning Chip away with our Virus Internet PowerPoint Template 0910. The beauty of your thoughts will soon emerge.

Two Factor Authentication Example Of Ppt Presentation
This is a two factor authentication example of ppt presentation. This is a two stage process. The stages in this process are something you know, something you have.

Searching Password Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with the metallic magnifying glass hovering in front of a flat panel computer display monitor with a large brass metallic key on it on a black reflective surface Conduct yourself creditably with our Searching Password Security PowerPoint Backgrounds And Templates 1210. They will let you dominate the dais.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.
Authentication Process Flow Of Verification Factors For User Profile Authentication Icon Portrait PDF
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
Chemical Eco Responsibility Icon For Environmental Protection Graphics Pdf
Pitch your topic with ease and precision using this Chemical Eco Responsibility Icon For Environmental Protection Graphics Pdf. This layout presents information on Chemical Eco Responsibility Icon, Environmental Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Chemical Eco Responsibility Icon For Environmental Protection Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

 Home
Home