Password

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
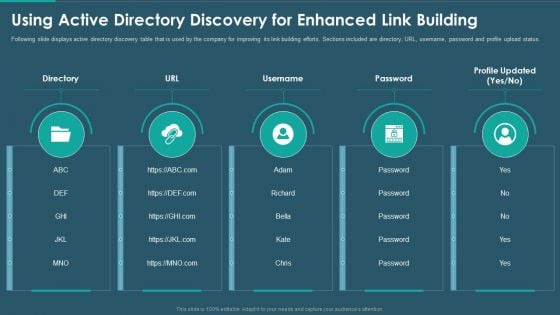
Sales And Promotion Playbook Using Active Directory Discovery For Enhanced Link Building Rules PDF
Following slide displays active directory discovery table that is used by the company for improving its link building efforts. Sections included are directory, URL, username, password and profile upload status. Presenting sales and promotion playbook using active directory discovery for enhanced link building rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like using active directory discovery for enhanced link building. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Brochure PDF
Following slide displays active directory discovery table that is used by the company for improving its link building efforts. Sections included are directory, URL, username, password and profile upload status. This is a Organizational Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Brochure PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Using Active Directory Discovery For Enhanced Link Building You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
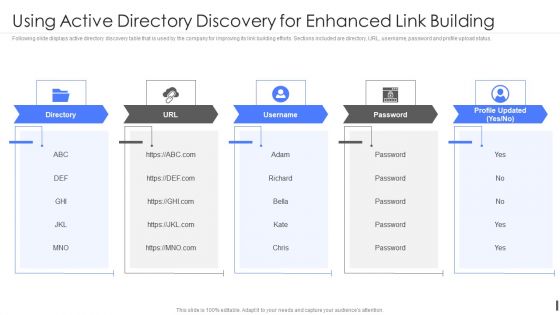
Product Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Rules PDF
Following slide displays active directory discovery table that is used by the company for improving its link building efforts. Sections included are directory, URL, username, password and profile upload status.This is a Product Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Rules PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Using Active, Directory Discovery, Enhanced Building You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
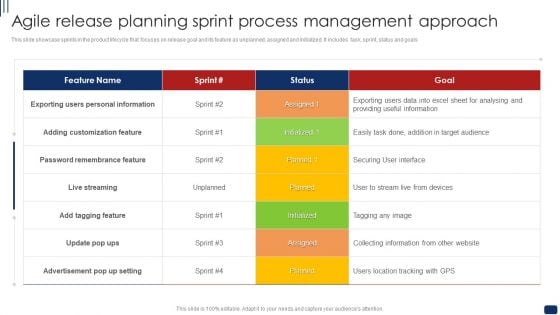
Agile Release Planning Sprint Process Management Approach Ppt Layouts Infographics PDF
This slide showcase sprints in the product lifecycle that focuses on release goal and its feature as unplanned, assigned and initialized. It includes task, sprint, status and goals. Pitch your topic with ease and precision using this Agile Release Planning Sprint Process Management Approach Ppt Layouts Infographics PDF. This layout presents information on Adding Customization Feature, Password Remembrance Feature, Planned. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF
This slide covers checklist to provide employees information about different companys policies. It includes policies such as no password sharing, company BYOD, working hours, overtime pay, insurance policies, pension, etc. Presenting Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Checklist, Completed, Working Hours Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Virtual Assistant Onboarding Checklist Report Pictures PDF
This slide covers checklist for onboarding virtual assistant for a company. It includes requisities such as providing company background, vision and values, company policies, performance dashboard, chat software, KPIs, feedback, deadlines, etc.Showcasing this set of slides titled Virtual Assistant Onboarding Checklist Report Pictures PDF. The topics addressed in these templates are Company Background, Password Management, Performance Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Project Issues Tracker Progress Scorecard Infographics PDF
This slide covers issues detected by while executing an IT project by tracker tool. It includes report based on output including issue details reporting date, assigned person along with its impact on project and current resolution status.Pitch your topic with ease and precision using this IT Project Issues Tracker Progress Scorecard Infographics PDF. This layout presents information on Hard Disk Replacement, Disk Replacement, Password Reset. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Flowchart For Online Car Mortgage Management System Brochure PDF
This slide exhibits process of managing loans reasonably. It helps customer managers to handle and make rational use of their mortgage. It presents information related to aspects such as password resetting, entering receipt, verification , etc. Showcasing this set of slides titled Flowchart For Online Car Mortgage Management System Brochure PDF. The topics addressed in these templates are Flowchart For Online Car, Mortgage Management System . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Continuous Testing Agile Release Plan In Product Life Cycle Portrait PDF
This slide showcases a sprint testing agile release plan in the product life cycle to concentrate on the releases aim, features, and start end dates. It includes sprints such as streaming capabilities, pop up advertisements, etc. Showcasing this set of slides titled Continuous Testing Agile Release Plan In Product Life Cycle Portrait PDF The topics addressed in these templates are Release Planning, Provide Password Remembrance Feature, Offer Customized Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Incident Communication Strategy With Solutions Themes PDF
This slide illustrate communication plan along with solution to overcome, types of data breaches in an organization. It includes types of data breaches such as ransomware, password guessing, phishing and virus Pitch your topic with ease and precision using this Data Breach Incident Communication Strategy With Solutions Themes PDF. This layout presents information on Description, Communication Channel, Responsible Person. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
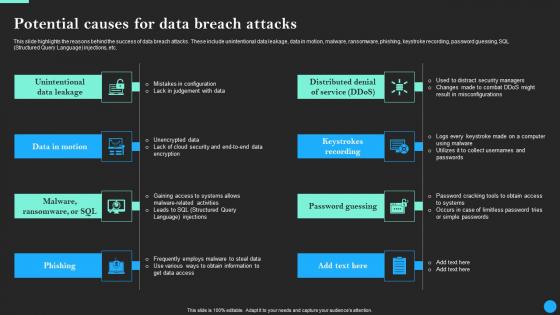
Potential Causes For Data Breach Attacks Data Breach Prevention Ideas Pdf
Boost your pitch with our creative Potential Causes For Data Breach Attacks Data Breach Prevention Ideas Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.
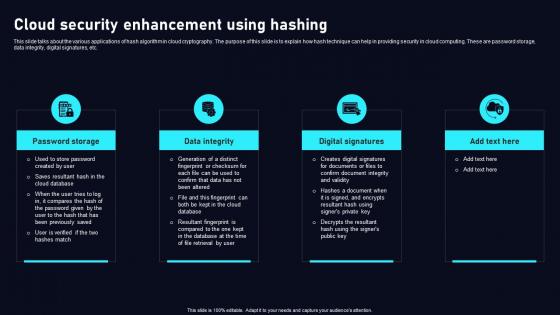
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
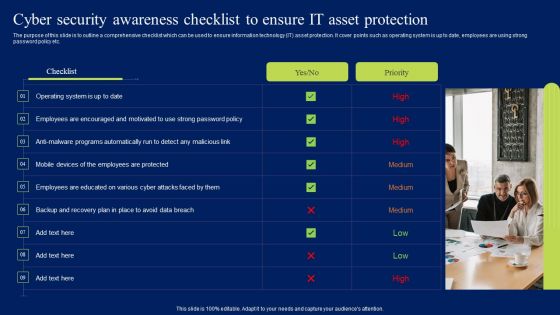
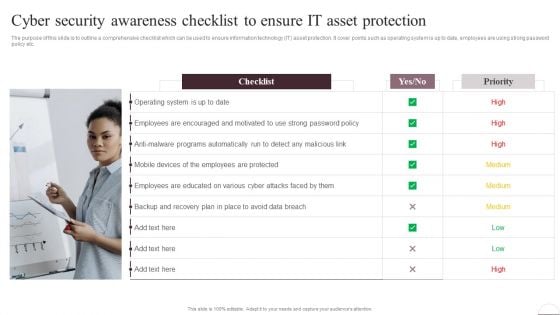
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Awareness Checklist To Ensure IT Asset Protection Structure PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Awareness Checklist To Ensure IT Asset Protection Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
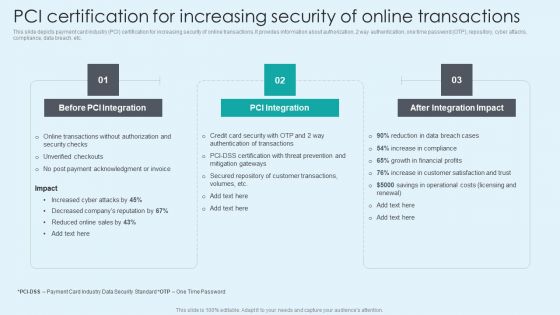
PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
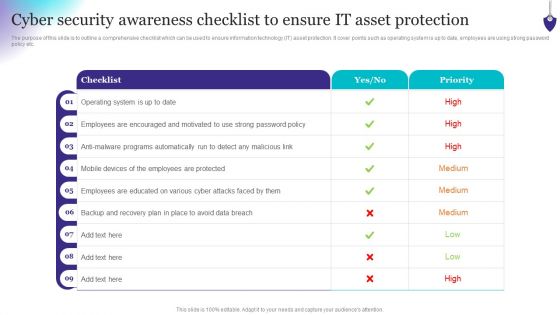
Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
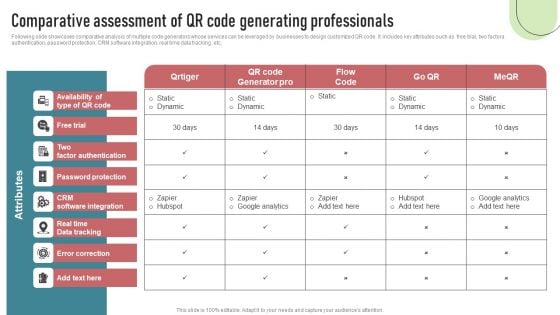
Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF
Following slide showcases comparative analysis of multiple code generators whose services can be leveraged by businesses to design customized QR code. It includes key attributes such as free trial, two factora authentication, password protection, CRM software integration, real time data tracking, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
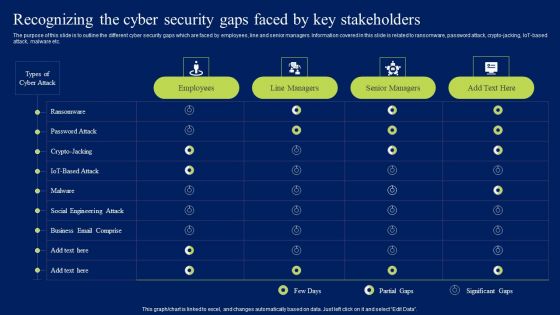
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
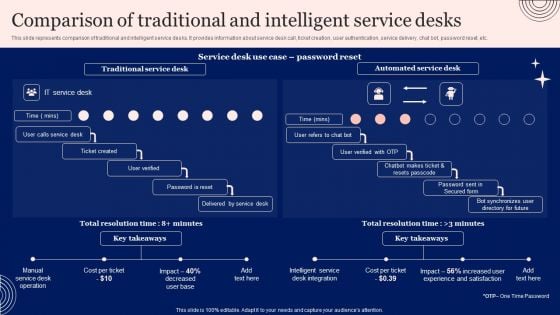
Implementing Advanced Service Help Desk Administration Program Comparison Of Traditional And Intelligent Service Desks Guidelines PDF
This slide represents comparison of traditional and intelligent service desks. It provides information about service desk call, ticket creation, user authentication, service delivery, chat bot, password reset, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Advanced Service Help Desk Administration Program Comparison Of Traditional And Intelligent Service Desks Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Various Techniques To Successfully Prevent Business Email Compromise Attack Guidelines PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Various Techniques To Successfully Prevent Business Email Compromise Attack Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Various Techniques To Successfully Prevent Business Email Compromise Attack Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
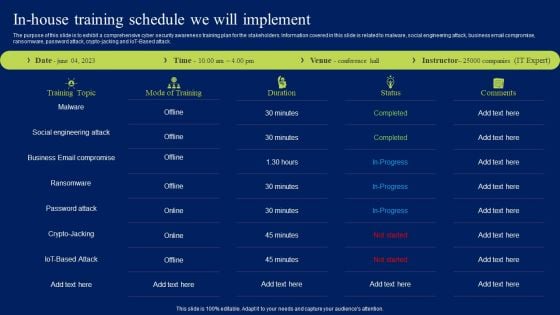
In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
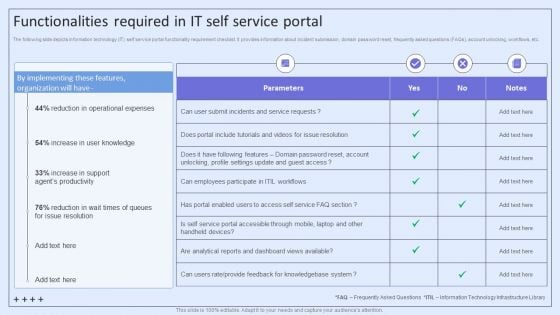
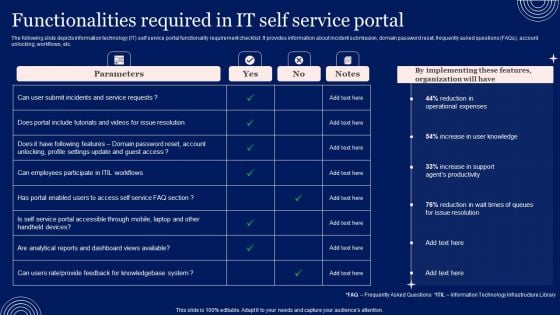
Integrating ITSM To Enhance Service Functionalities Required In IT Self Service Portal Information PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Get a simple yet stunning designed Integrating ITSM To Enhance Service Functionalities Required In IT Self Service Portal Information PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Integrating ITSM To Enhance Service Functionalities Required In IT Self Service Portal Information PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
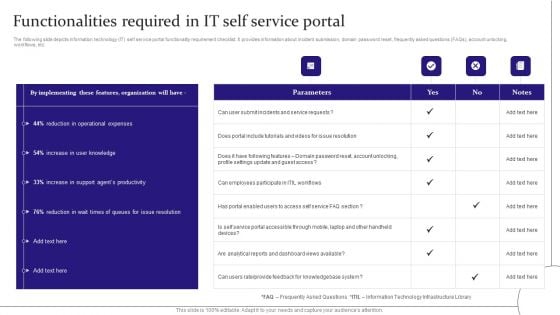
Digitalization Of Service Desk Functionalities Required In IT Self Service Portal Ppt Summary Portfolio PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Get a simple yet stunning designed Digitalization Of Service Desk Functionalities Required In IT Self Service Portal Ppt Summary Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Digitalization Of Service Desk Functionalities Required In IT Self Service Portal Ppt Summary Portfolio PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
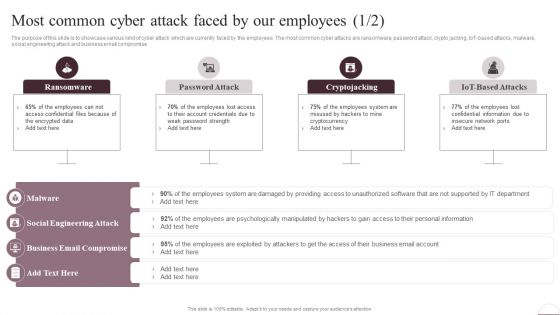
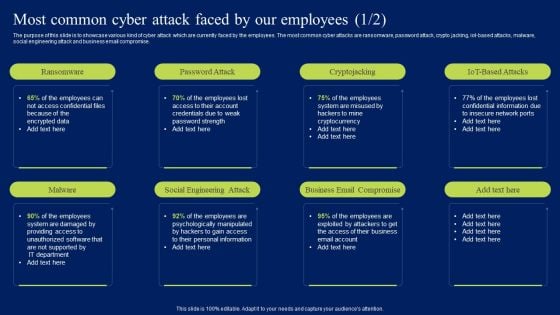
Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF from Slidegeeks today.

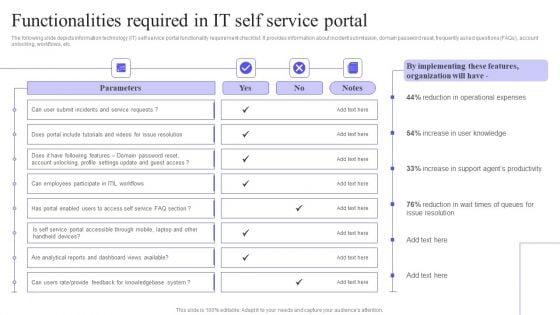
Functionalities Required In It Self Service Portal Ppt PowerPoint Presentation File Professional PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Functionalities Required In It Self Service Portal Ppt PowerPoint Presentation File Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Functionalities Required In It Self Service Portal Ppt PowerPoint Presentation File Professional PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Functionalities Required In IT Self Service Portal Mockup PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Functionalities Required In IT Self Service Portal Mockup PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Functionalities Required In IT Self Service Portal Mockup PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Implementing Advanced Service Help Desk Administration Program Functionalities Required In IT Self Service Portal Clipart PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Advanced Service Help Desk Administration Program Functionalities Required In IT Self Service Portal Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Advanced Service Help Desk Administration Program Functionalities Required In IT Self Service Portal Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.
Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, iot-based attacks, malware, social engineering attack and business email compromise. This Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
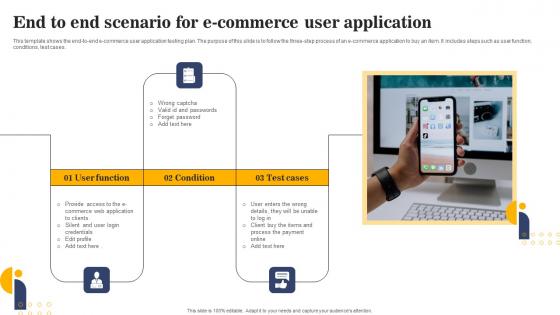
End To End Scenario For E Commerce User Application Elements Pdf
This template shows the end-to-end e-commerce user application testing plan. The purpose of this slide is to follow the three-step process of an e-commerce application to buy an item. It includes steps such as user function, conditions, test cases.Showcasing this set of slides titled End To End Scenario For E Commerce User Application Elements Pdf The topics addressed in these templates are Provide Access, Process Payment, Forget Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the end to end e commerce user application testing plan. The purpose of this slide is to follow the three step process of an e commerce application to buy an item. It includes steps such as user function, conditions, test cases.
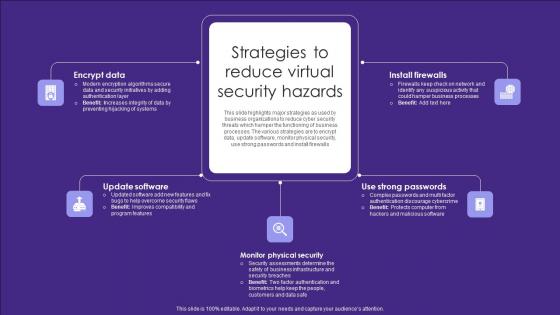
Strategies To Reduce Virtual Security Hazards Summary Pdf
This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Showcasing this set of slides titled Strategies To Reduce Virtual Security Hazards Summary Pdf. The topics addressed in these templates are Install Firewalls, Strong Passwords, Physical Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls
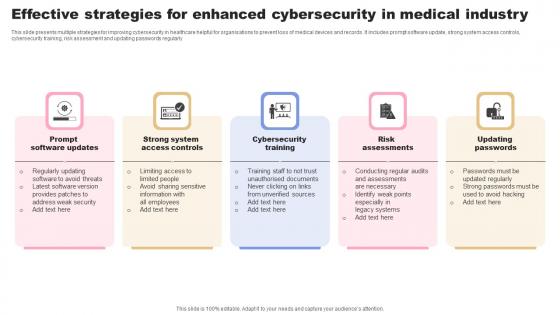
Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf
This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly Pitch your topic with ease and precision using this Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf. This layout presents information on Cybersecurity Training, Risk Assessments, Updating Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly
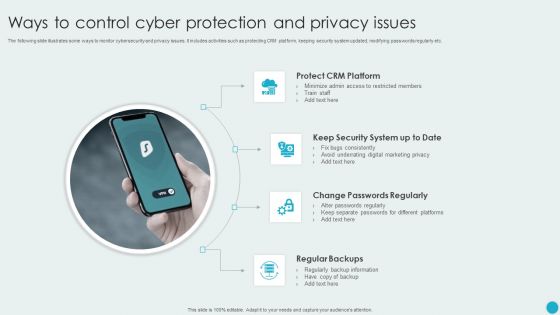
Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
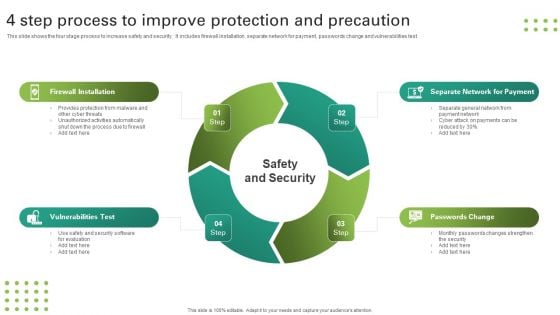
4 Step Process To Improve Protection And Precaution Topics PDF
This slide shows the four stage process to increase safety and security. It includes firewall installation, separate network for payment, passwords change and vulnerabilities test. Persuade your audience using this 4 Step Process To Improve Protection And Precaution Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Firewall Installation, Separate Network For Payment, Passwords Change. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
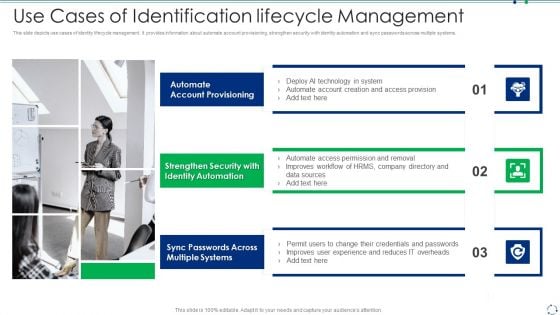
Use Cases Of Identification Lifecycle Management Demonstration PDF
This slide depicts use cases of identity lifecycle management. It provides information about automate account provisioning, strengthen security with identity automation and sync passwords across multiple systems.Presenting use cases of identification lifecycle management demonstration pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including automate account provisioning, strengthen security with identity automation, sync passwords This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
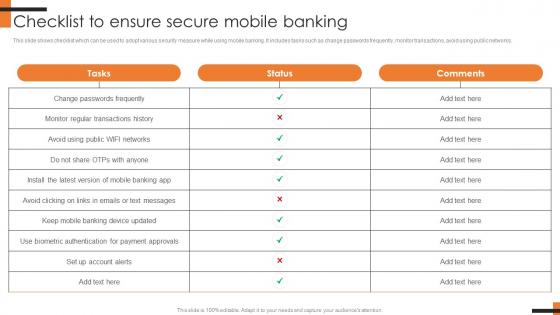
Checklist To Ensure Secure Mobile Banking Comprehensive Smartphone Banking Professional Pdf
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.Get a simple yet stunning designed Checklist To Ensure Secure Mobile Banking Comprehensive Smartphone Banking Professional Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Ensure Secure Mobile Banking Comprehensive Smartphone Banking Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
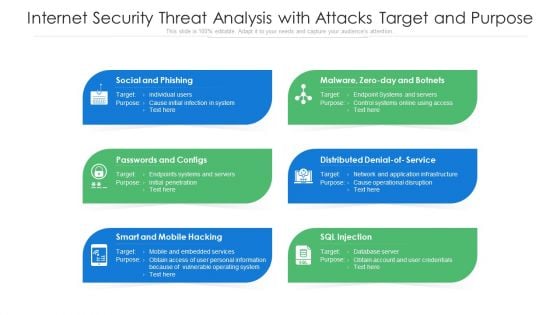
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
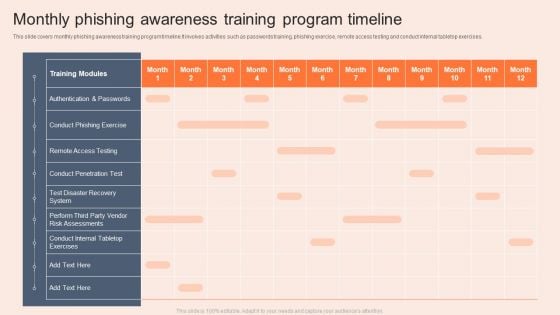
Monthly Phishing Awareness Training Program Timeline Infographics PDF
This slide covers monthly phishing awareness training program timeline.It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Pitch your topic with ease and precision using this Monthly Phishing Awareness Training Program Timeline Infographics PDF. This layout presents information on Risk Assessments, System, Awareness Training Program Timeline. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
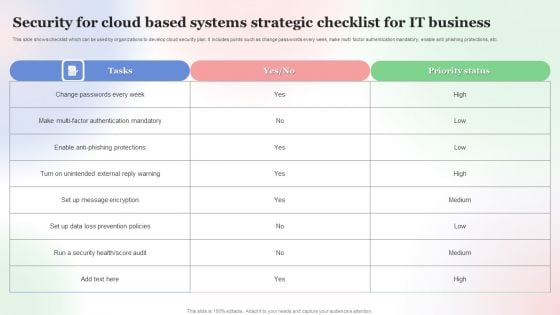
Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Transformation Strategies And Its Implementation On Project Ppt File Designs Download PDF
This slide contains the information related to the best implementation of the strategies used for the transformations in the business. It includes improving cyber security for financial technologies , create digital solutions , increase budget for RandD and developing user friendly systems. Persuade your audience using this Company Transformation Strategies And Its Implementation On Project Ppt File Designs Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Monthly, Digital Solutions, Digital Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
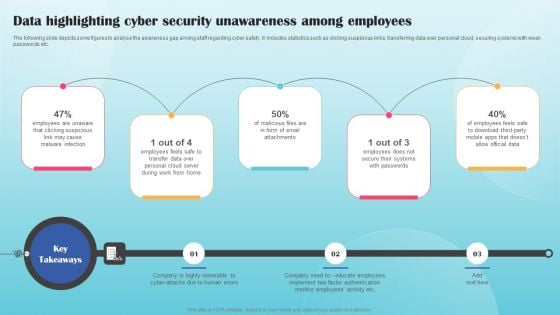
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
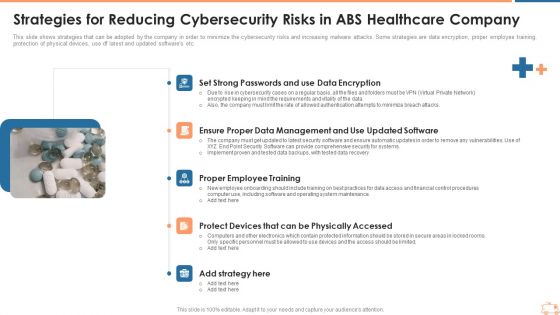
Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
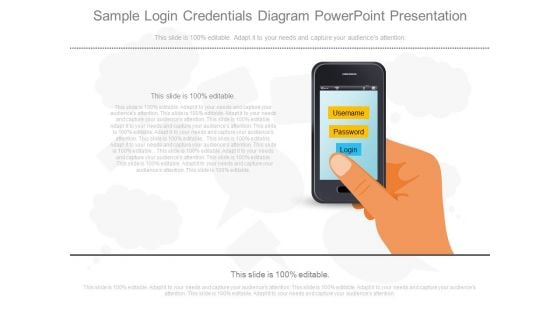
Sample Login Credentials Diagram Powerpoint Presentation
This is a sample login credentials diagram powerpoint presentation. This is a one stage process. The stages in this process are username, password, login.

Internet Security Diagram Template Ppt Slide Styles
This is a internet security diagram template ppt slide styles. This is a five stage process. The stages in this process are search, protection, password, antivirus, firewall.

 Home
Home