Password
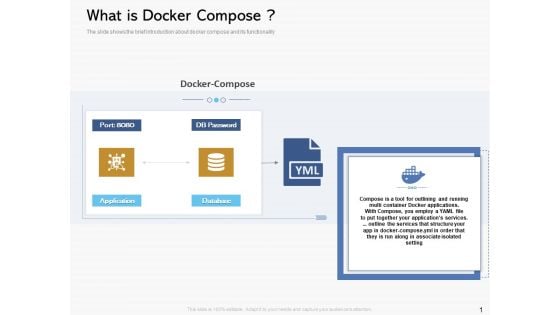
Road Digital Transformation Through Containerization What Is Docker Compose Designs PDF
The slide shows the brief introduction about docker compose and its functionality. Deliver and pitch your topic in the best possible manner with this road digital transformation through containerization what is docker compose designs pdf. Use them to share invaluable insights on docker compose, db password, application, database, docker applications and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Prepare And Deploy Strong IT Policies Ppt Pictures Slides PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this cybersecurity prepare and deploy strong it policies ppt pictures slides pdf. Use them to share invaluable insights on management, device, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Website Development Plan With Key Requirements Chart Ppt Summary Clipart Images PDF
This slide shows website development outline with major requirements table. It provides information such as business, stakeholder, functional, order processing, repeated order, history, password, etc. Showcasing this set of slides titled Website Development Plan With Key Requirements Chart Ppt Summary Clipart Images PDF. The topics addressed in these templates are Business, Requirements, Executives For Evaluating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
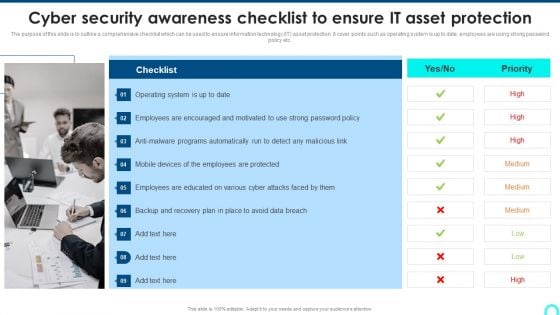
Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password.This is a Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Encouraged, Programs Automatically, Employees Protected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
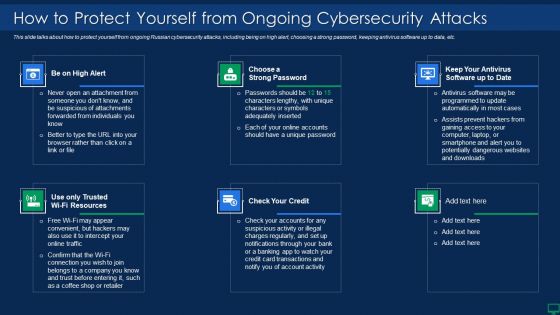
Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
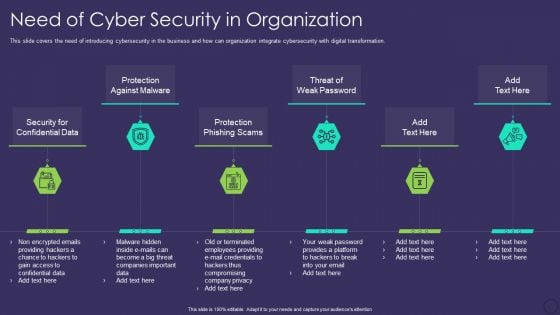
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
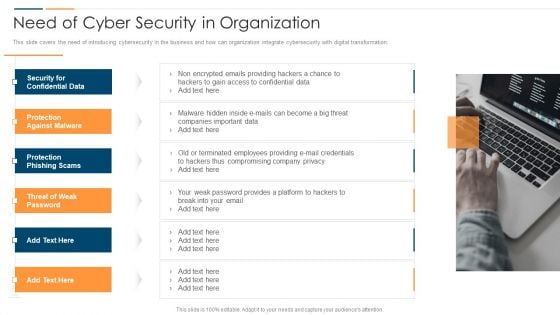
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
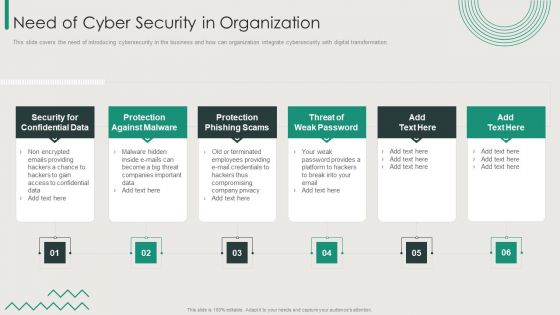
Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
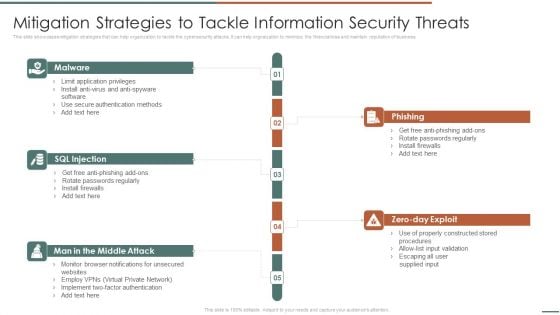
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
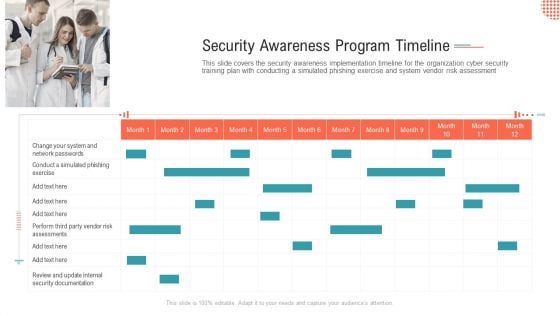
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
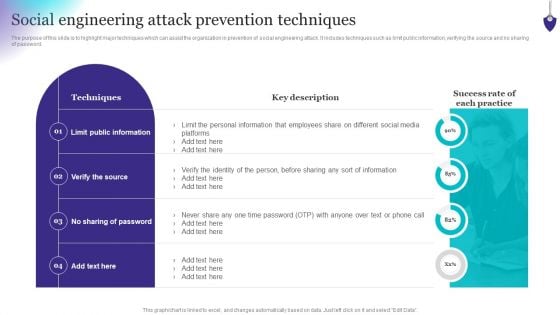
Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Want to ace your presentation in front of a live audience Our Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
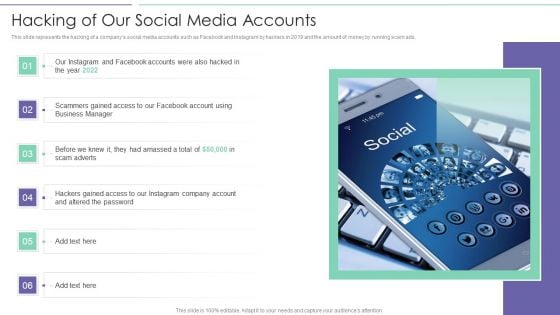
IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
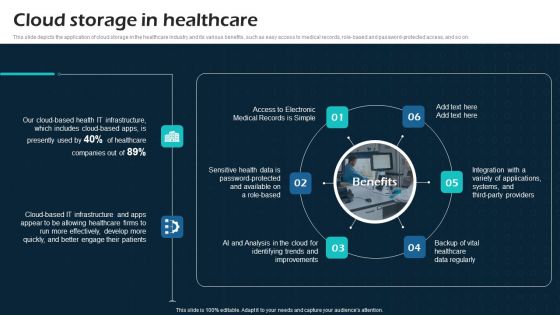
Cloud Storage In Healthcare Virtual Cloud Network IT Ppt Slides Layouts PDF
This slide depicts the application of cloud storage in the healthcare industry and its various benefits, such as easy access to medical records, role based and password-protected access, and so on. Boost your pitch with our creative Cloud Storage In Healthcare Virtual Cloud Network IT Ppt Slides Layouts PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Storage In Healthcare Slides PDF
This slide depicts the application of cloud storage in the healthcare industry and its various benefits, such as easy access to medical records, role based and password-protected access, and so on. Find a pre designed and impeccable Cloud Storage In Healthcare Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
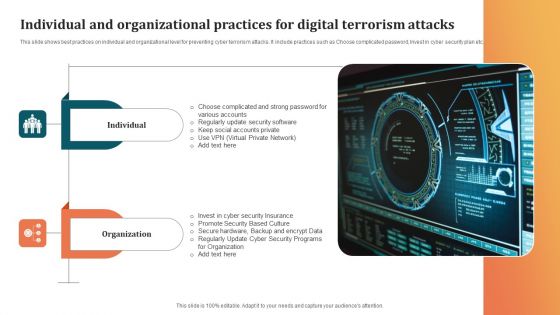
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
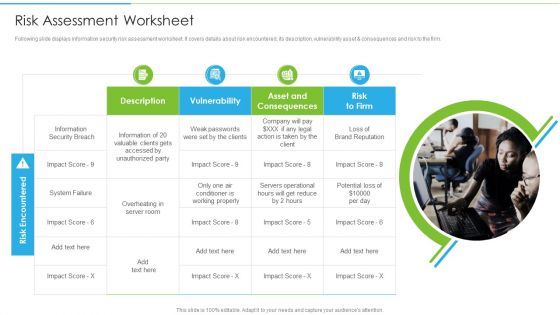
Ways To Accomplish ISO 27001 Accreditation Risk Assessment Worksheet Elements PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. Presenting Ways To Accomplish ISO 27001 Accreditation Risk Assessment Worksheet Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Asset Consequences, Information Security, Weak Passwords. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
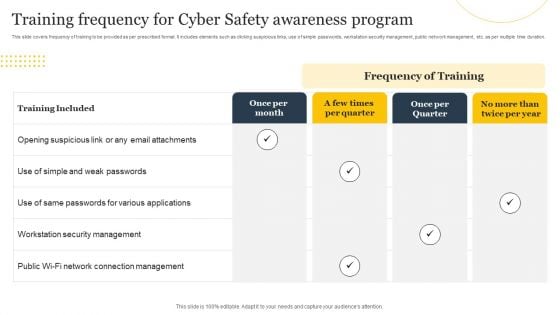
Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF
This slide covers frequency of training to be provided as per prescribed format. It includes elements such as clicking suspicious links, use of simple passwords, workstation security management, public network management, etc. as per multiple time duration. Showcasing this set of slides titled Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF. The topics addressed in these templates are Training Included, Once Per Month, Frequency Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
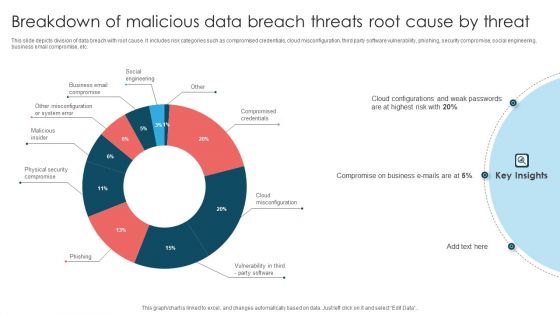
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
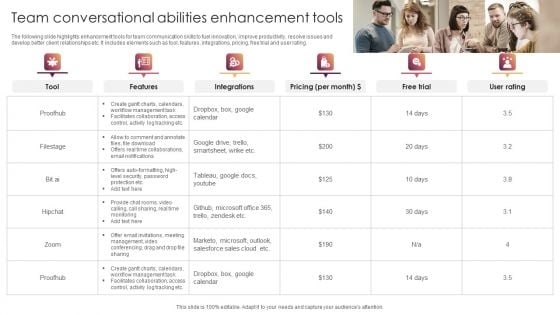
Team Conversational Abilities Enhancement Tools Demonstration PDF
The following slide highlights enhancement tools for team communication skills to fuel innovation, improve productivity, resolve issues and develop better client relationships etc. It includes elements such as tool, features, integrations, pricing, free trial and user rating. Presenting Team Conversational Abilities Enhancement Tools Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security, Password, Management, Salesforce Sales. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
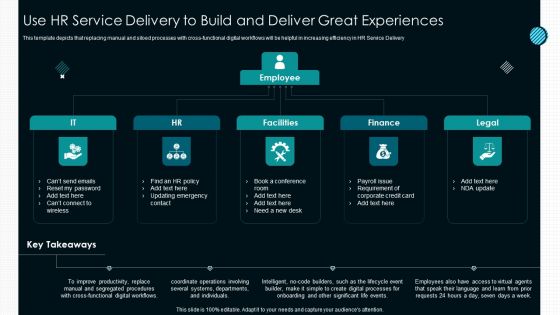
Optimize Service Delivery With Enhanced Use HR Service Delivery To Build And Deliver Rules PDF
This template depicts that replacing manual and siloed processes with cross-functional digital workflows will be helpful in increasing efficiency in HR Service Delivery.This is a Optimize Service Delivery With Enhanced Use HR Service Delivery To Build And Deliver Rules PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reset Password, Emergency Contact, Payroll Requirement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
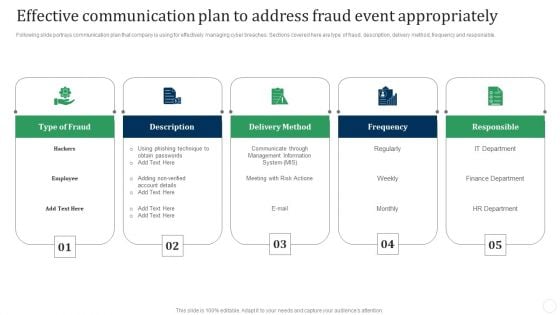
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

New Employee Hire Hr Personnel File Documentation Checklist Ppt Pictures Infographic Template PDF
This slide covers documents required to be submitted to HR personnel at time of joining the company. It includes documents such as no sharing passwords, employee hand book, etc. Presenting New Employee Hire Hr Personnel File Documentation Checklist Ppt Pictures Infographic Template PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Checklist, Completed, Employee Handbook Signed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Social Engineering Attack Prevention Techniques Infographics PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. There are so many reasons you need a Prevention Of Information Social Engineering Attack Prevention Techniques Infographics PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
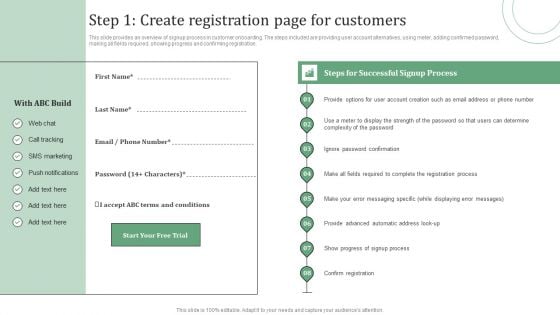
Standard Approaches For Client Onboarding Journey Step 1 Create Registration Elements PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Take your projects to the next level with our ultimate collection of Standard Approaches For Client Onboarding Journey Step 1 Create Registration Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

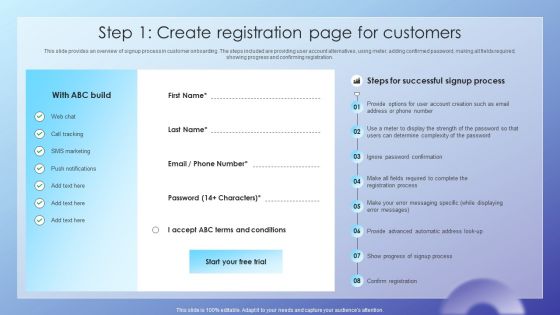
Step 1 Create Registration Page For Customers Rules PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Want to ace your presentation in front of a live audience Our Step 1 Create Registration Page For Customers Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
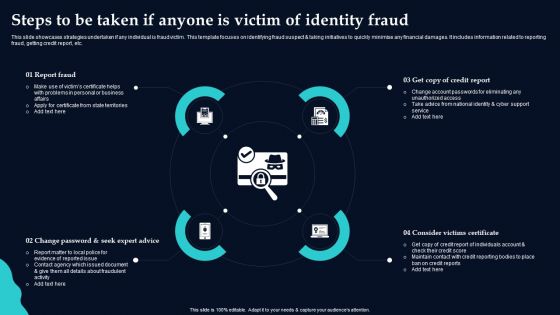
Steps To Be Taken If Anyone Is Victim Of Identity Fraud Template PDF
This slide showcases strategies undertaken if any individual is fraud victim. This template focuses on identifying fraud suspect and taking initiatives to quickly minimise any financial damages. It includes information related to reporting fraud, getting credit report, etc. Persuade your audience using this Steps To Be Taken If Anyone Is Victim Of Identity Fraud Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Report Fraud, Change Password, Consider Victims Certificate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
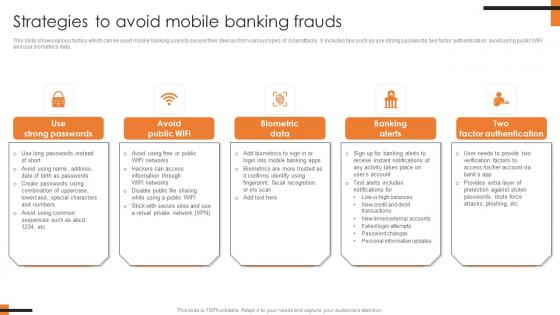
Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.This modern and well-arranged Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.
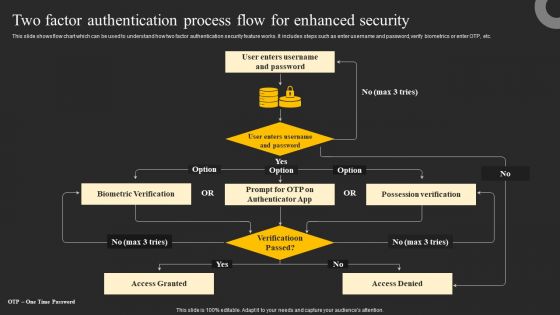
Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
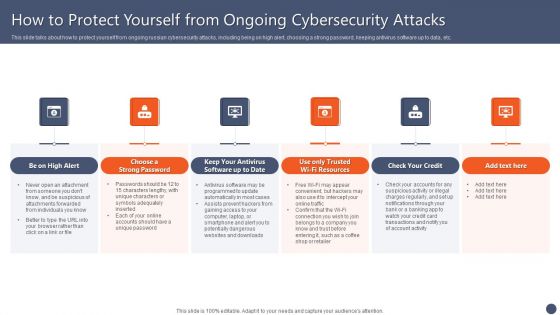
Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates
PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-This PowerPoint Diagram shows you the continual way to prevent manufacture losses in any Business related Activities. It is shown by different shades of Brown color. -PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Review your plans with our Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates. Download without worries with our money back guaranteee.
Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates
PPT successive representation of 7 stages an arrow PowerPoint Templates-This PowerPoint Diagram shows you the Successive Representation of five approaches on the Arrow. It shows the successive concepts used in a procedure. You can change color, size and orientation of any icon to your liking.-PPT successive representation of 7 stages an arrow PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Let the audience decide with our Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates. Make sure your presentation gets the attention it deserves.
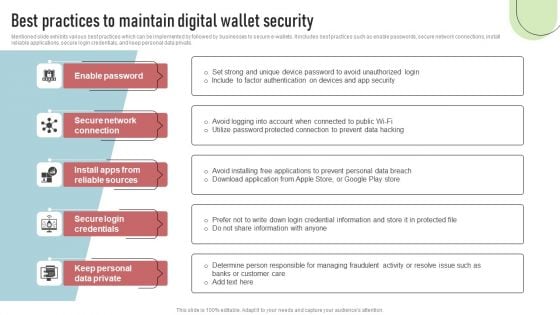
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
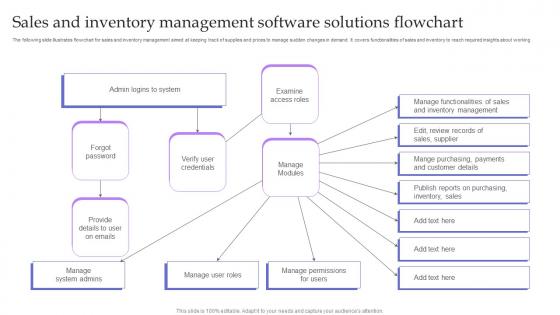
Sales And Inventory Management Software Solutions Flowchart Topics Pdf
The following slide illustrates flowchart for sales and inventory management aimed at keeping track of supplies and prices to manage sudden changes in demand. It covers functionalities of sales and inventory to reach required insights about working Pitch your topic with ease and precision using this Sales And Inventory Management Software Solutions Flowchart Topics Pdf. This layout presents information on Logins System, Forgot Password, Verify User Credentials . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide illustrates flowchart for sales and inventory management aimed at keeping track of supplies and prices to manage sudden changes in demand. It covers functionalities of sales and inventory to reach required insights about working

Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. This modern and well arranged Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Client Acquisition Journey Plan Step 1 Create Registration Page For Customers Pictures PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Welcome to our selection of the Client Acquisition Journey Plan Step 1 Create Registration Page For Customers Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
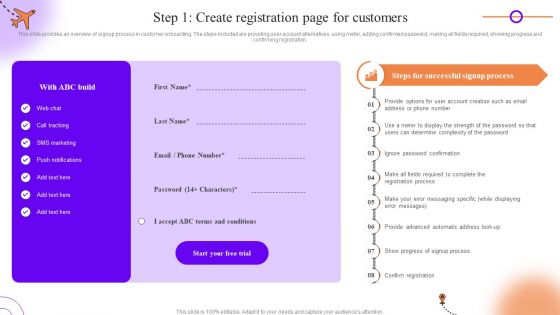
Client Onboarding Journey Impact On Business Step 1 Create Registration Page For Customers Template PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Slidegeeks has constructed Client Onboarding Journey Impact On Business Step 1 Create Registration Page For Customers Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Social Engineering Attack Prevention Techniques Ppt Show Brochure PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Do you know about Slidesgeeks Social Engineering Attack Prevention Techniques Ppt Show Brochure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
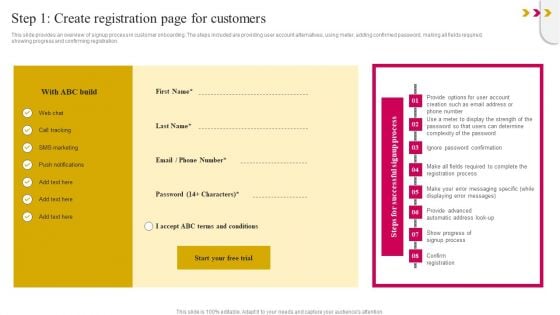
Step 1 Create Registration Page For Customers Guidelines PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. If you are looking for a format to display your unique thoughts, then the professionally designed Step 1 Create Registration Page For Customers Guidelines PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Step 1 Create Registration Page For Customers Guidelines PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
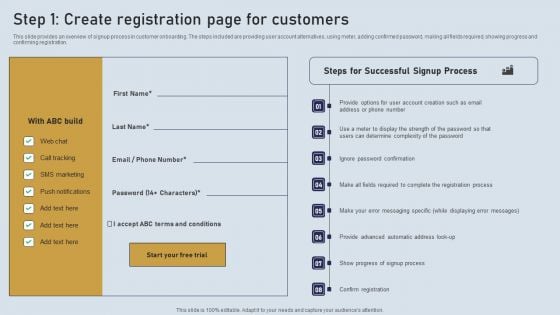
Onboarding Journey For Effective Client Communication Step 1 Create Registration Page For Customers Themes PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Onboarding Journey For Effective Client Communication Step 1 Create Registration Page For Customers Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Onboarding Journey For Effective Client Communication Step 1 Create Registration Page For Customers Themes PDF
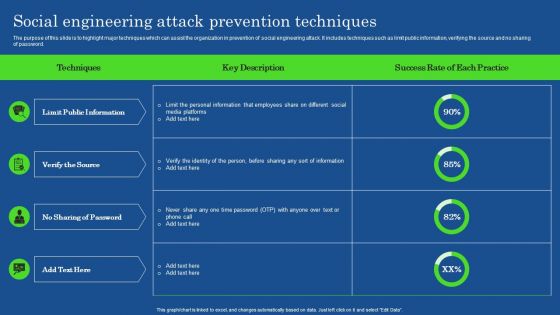
Social Engineering Attack Prevention Techniques Demonstration PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Welcome to our selection of the Social Engineering Attack Prevention Techniques Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
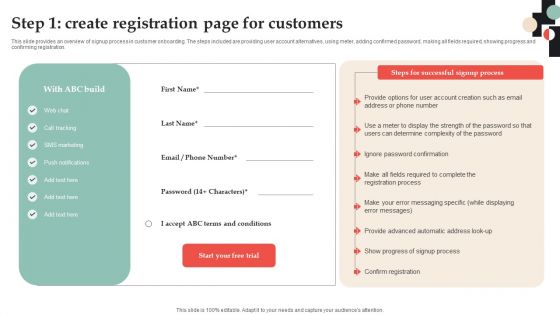
Customer Onboarding Journey Optimization Plan Step 1 Create Registration Page Background PDF
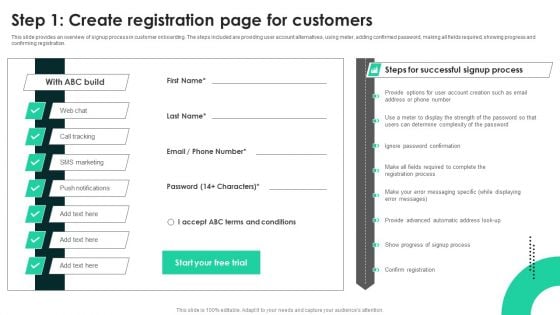
Techniques To Enhance User Onboarding Journey Step 1 Create Registration Page For Customers Themes PDF
This slide provides an overview of signup process in customer onboarding. The steps included are providing user account alternatives, using meter, adding confirmed password, making all fields required, showing progress and confirming registration. Welcome to our selection of the Techniques To Enhance User Onboarding Journey Step 1 Create Registration Page For Customers Themes PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
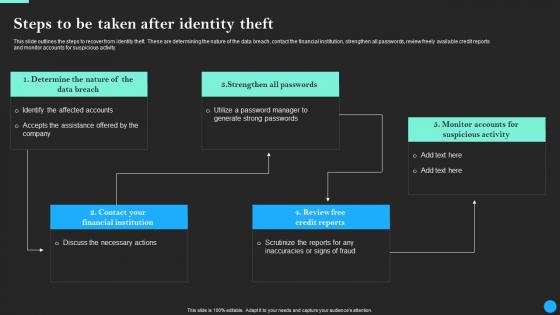
Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the steps to recover from identity theft. These are determining the nature of the data breach, contact the financial institution, strengthen all passwords, review freely available credit reports and monitor accounts for suspicious activity.
Imessage Login Android In Powerpoint And Google Slides Cpb
Introducing our well designed Imessage Login Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Imessage Login Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Imessage Login Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security.
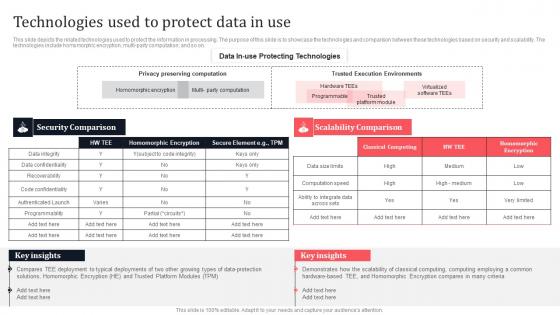
Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
Web Application Login Screen In Powerpoint And Google Slides Cpb
Introducing our well designed Web Application Login Screen In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Web Application Login Screen. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Web Application Login Screen In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
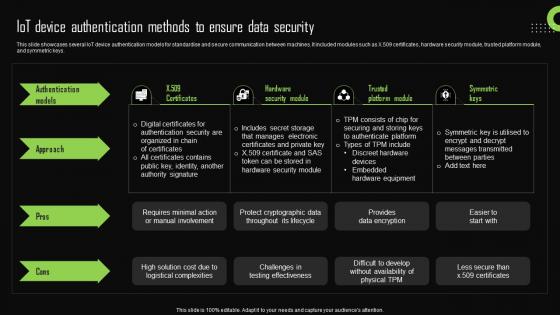
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Emotional Appeal Authenticity that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Emotional Appeal Authenticity In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Business Analyst Diagrams 3d Man Start Up Unlocking PowerPoint Templates
We present our business analyst diagrams 3d man start up unlocking PowerPoint templates.Use our People PowerPoint Templates because These PowerPoint Templates and Slides will give the updraft to your ideas. See them soar to great heights with ease. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Present our Symbol PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Download and present our Shapes PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you Leave a lasting impression to your audiences. They possess an inherent longstanding recall factor.Use these PowerPoint slides for presentations relating to 3d, arrow, back, button, clip, clip-art, direction, down, download, element, end, favorites, front, help, home, house, icon, illustration, info, information, key, lock, loupe, male, marionette, men, modern, next, object, panel, password, pointer, puppet, push, recycle, red, reflection, refresh, right, search, shape, shiny, start, stop, stylish, symbol, up, upload, vector, web. The prominent colors used in the PowerPoint template are Blue, Green , Yellow. Professionals tell us our business analyst diagrams 3d man start up unlocking PowerPoint templates are visually appealing. The feedback we get is that our down PowerPoint templates and PPT Slides will impress their bosses and teams. PowerPoint presentation experts tell us our business analyst diagrams 3d man start up unlocking PowerPoint templates will save the presenter time. You can be sure our back PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. People tell us our business analyst diagrams 3d man start up unlocking PowerPoint templates are designed to make your presentations professional. You can be sure our back PowerPoint templates and PPT Slides will get their audience's attention. Educate your team with a winning presentation with our Business Analyst Diagrams 3d Man Start Up Unlocking PowerPoint Templates. You will come out on top.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
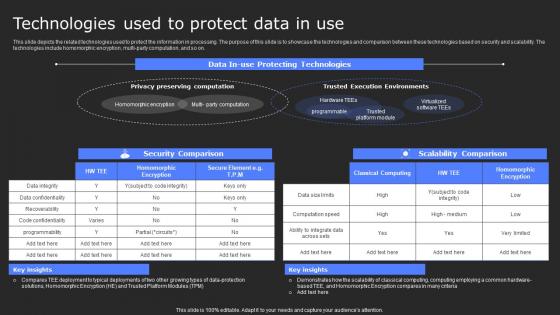
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
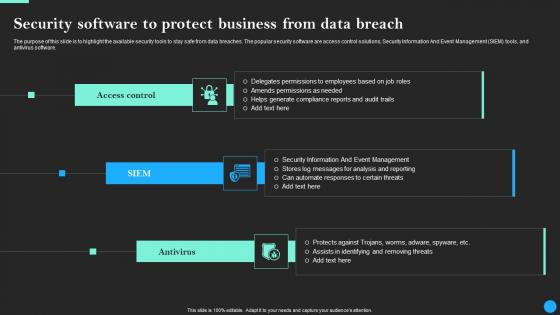
Security Software To Protect Business From Data Breach Prevention Elements Pdf
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.

 Home
Home