Password
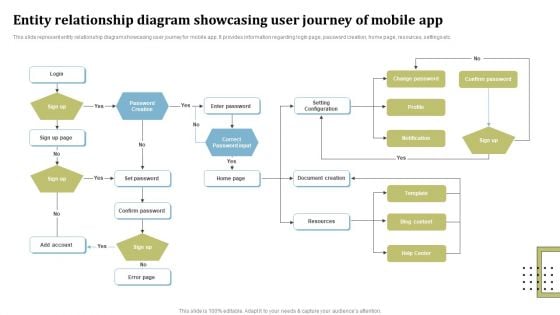
Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF
This slide represent entity relationship diagram showcasing user journey for mobile app. It provides information regarding login page, password creation, home page, resources, settings etc. Presenting Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Password Creation, Correct Password Input, Setting Configuration, Document Creation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Dos And Donts Of Cyber Security Awareness Professional PDF
The purpose of this slide is to highlight the major dos and donts of cyber security awareness. The dos covered in the slide are using multi-factor authentication, password manager, frequently changing the password, etc. The donts are using the same password, simple and short passwords, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Dos And Donts Of Cyber Security Awareness Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
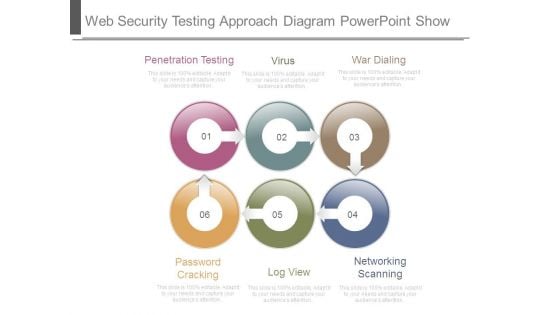
Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.
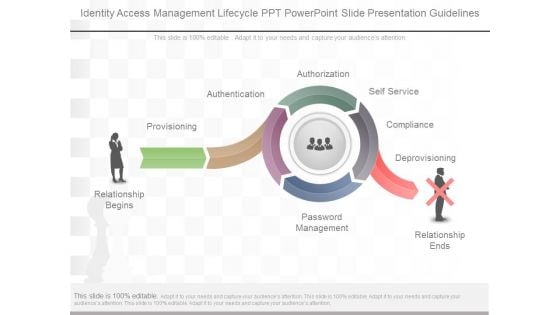
Identity Access Management Lifecycle Ppt Powerpoint Slide Presentation Guidelines
This is a identity access management lifecycle ppt powerpoint slide presentation guidelines. This is a five stage process. The stages in this process are relationship begins, provisioning, authentication, authorization, self service, compliance, deprovisioning, password management, relationship ends.
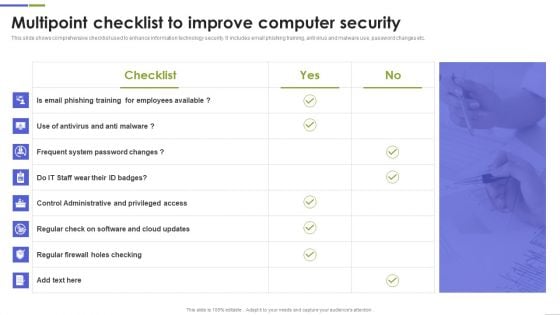
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Authentication Process Flow Of Verification Factors From Client And Server Side Structure PDF
Pitch your topic with ease and precision using thisauthentication process flow of verification factors from client and server side structure pdf This layout presents information on individual enters password, second form of authentication, one time password entered manually. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
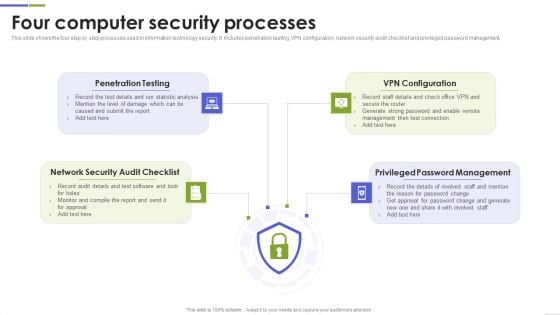
Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
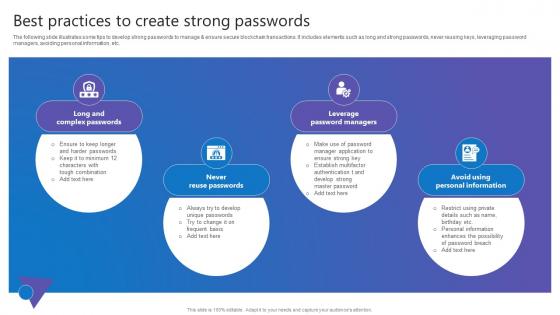
Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. This Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc.
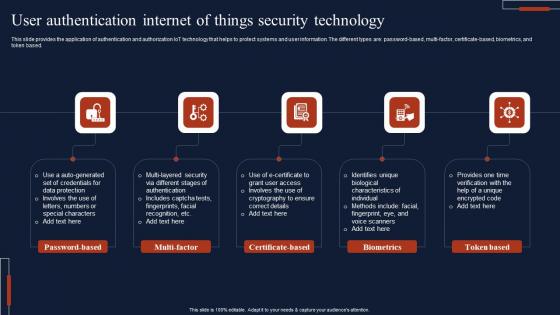
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
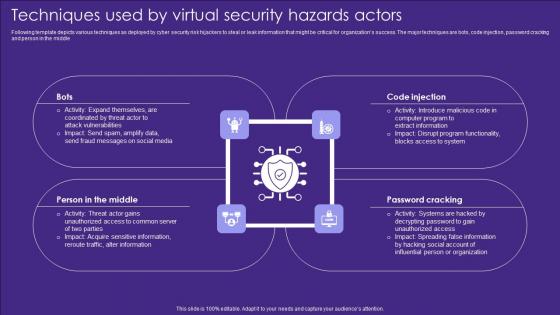
Techniques Used By Virtual Security Hazards Actors Professional Pdf
Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Pitch your topic with ease and precision using this Techniques Used By Virtual Security Hazards Actors Professional Pdf. This layout presents information on Code Injection, Password Cracking, Middle. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle
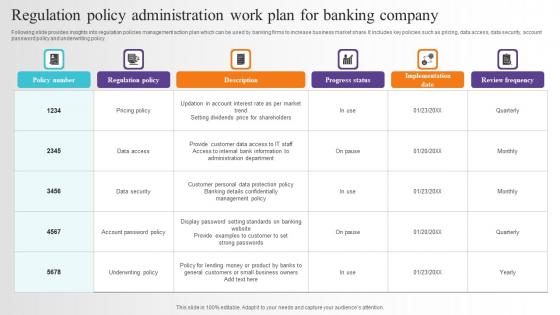
Regulation Policy Administration Work Plan For Banking Company Information Pdf
Following slide provides insights into regulation policies management action plan which can be used by banking firms to increase business market share. It includes key policies such as pricing, data access, data security, account password policy and underwriting policy. Pitch your topic with ease and precision using this Regulation Policy Administration Work Plan For Banking Company Information Pdf. This layout presents information on Data Access, Data Security, Account Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide provides insights into regulation policies management action plan which can be used by banking firms to increase business market share. It includes key policies such as pricing, data access, data security, account password policy and underwriting policy.
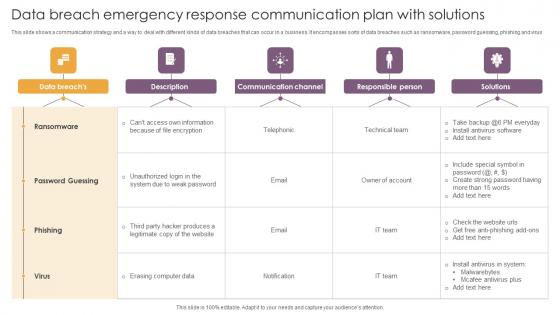
Data Breach Emergency Response Communication Plan With Solutions Introduction Pdf
This slide shows a communication strategy and a way to deal with different kinds of data breaches that can occur in a business. It encompasses sorts of data breaches such as ransomware, password guessing, phishing and virus Showcasing this set of slides titled Data Breach Emergency Response Communication Plan With Solutions Introduction Pdf The topics addressed in these templates are Ransomware, Password Guessing, Communication Channel All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows a communication strategy and a way to deal with different kinds of data breaches that can occur in a business. It encompasses sorts of data breaches such as ransomware, password guessing, phishing and virus

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Tips For Improving Business Cloud Protection Diagrams PDF
This slide shows tips which can be used by IT department to enhance the cloud protection of organization. It includes protects used identity, train employees, improve password protection, etc. Presenting Various Tips For Improving Business Cloud Protection Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Access Management, Improve Password Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
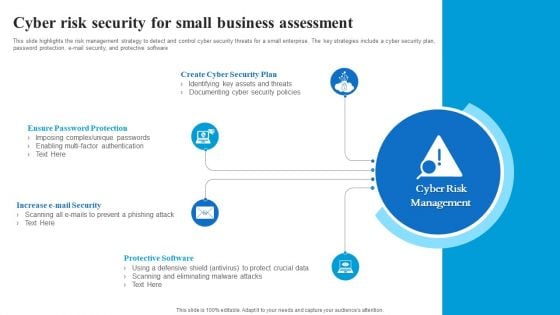
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
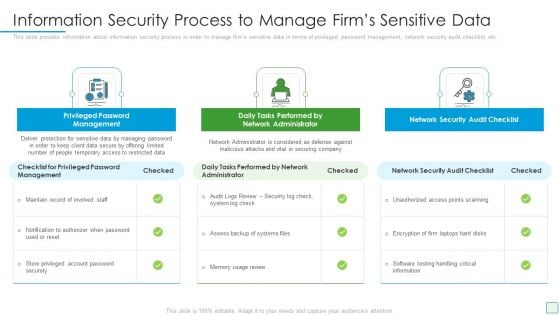
Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
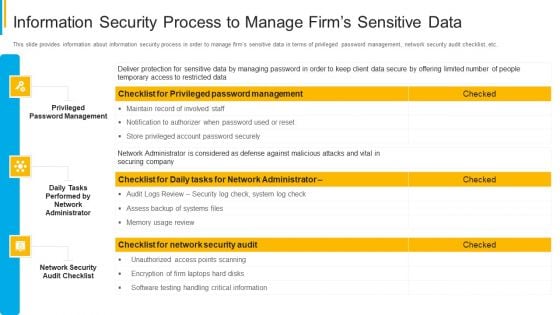
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
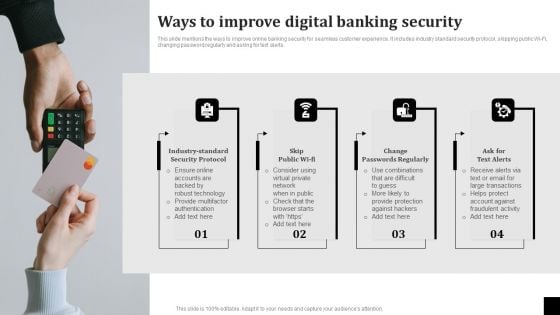
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
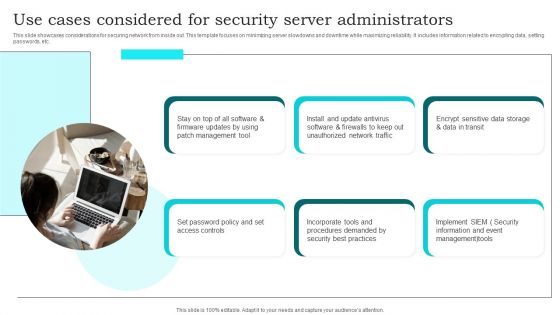
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
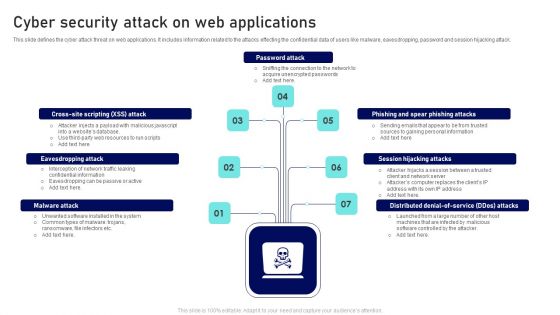
Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
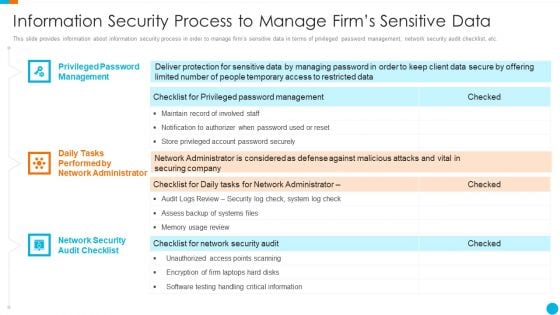
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
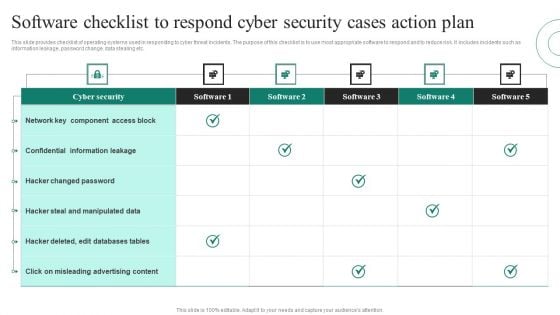
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
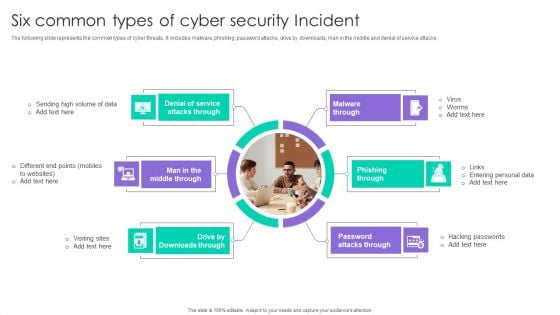
Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
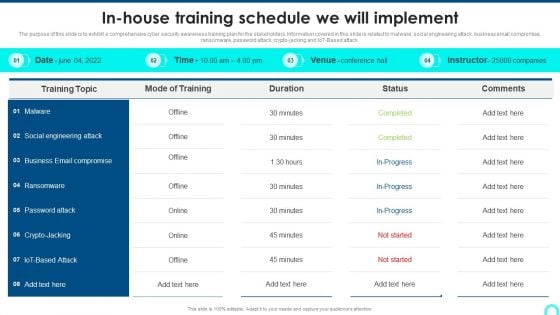
In House Training Schedule We Will Implement Icons PDF
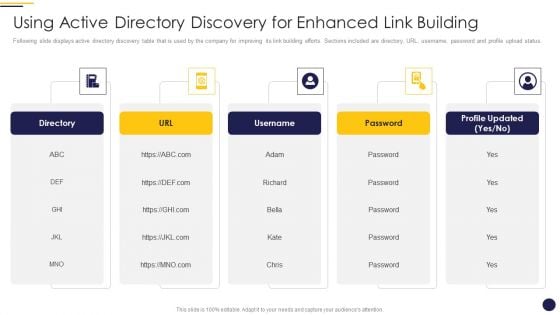
Internet Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Graphics PDF
Following slide displays active directory discovery table that is used by the company for improving its link building efforts. Sections included are directory, URL, username, password and profile upload status. This is a Internet Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Directory URL Username, Password Profile Updated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Client Acquisition Journey Plan Best Practices For Customers Registration Sample PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Client Acquisition Journey Plan Best Practices For Customers Registration Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
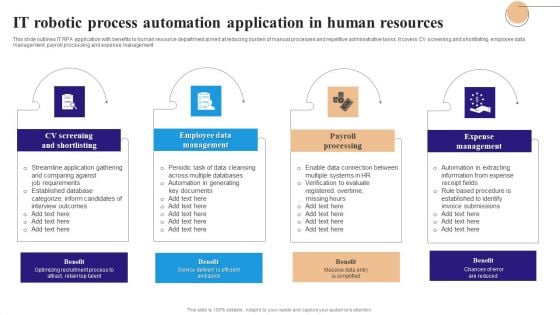
IT Robotic Process Automation Application In Human Resources Topics PDF
This slide highlights use cases of robotic process automation in information technology sector aimed at standardizing key processes to reduce human error. It covers the following cases backup and patch management, password resets, server and app monitoring, routine monitoring and email processing Showcasing this set of slides titled IT Robotic Process Automation Application In Human Resources Topics PDF. The topics addressed in these templates are Backup Patch Management, Password Resets, Server App Monitoring . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
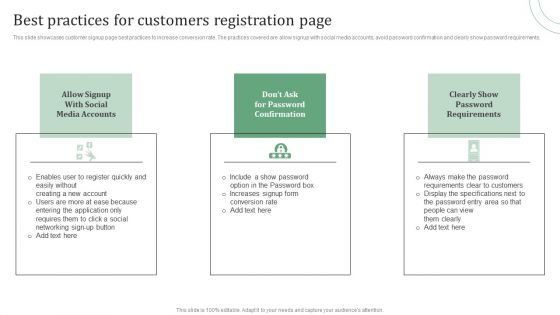
Standard Approaches For Client Onboarding Journey Best Practices For Customers Formats PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Want to ace your presentation in front of a live audience Our Standard Approaches For Client Onboarding Journey Best Practices For Customers Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
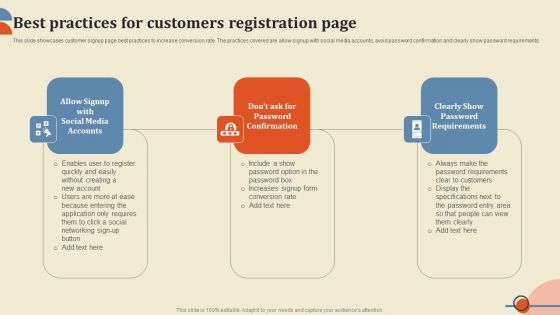
Best Practices For Customers Registration Page Ppt PowerPoint Presentation File Infographics PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Take your projects to the next level with our ultimate collection of Best Practices For Customers Registration Page Ppt PowerPoint Presentation File Infographics PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
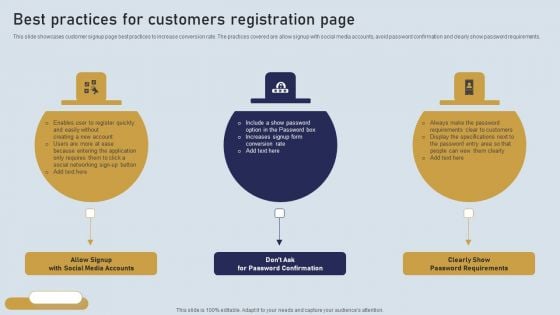
Onboarding Journey For Effective Client Communication Best Practices For Customers Registration Page Pictures PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Onboarding Journey For Effective Client Communication Best Practices For Customers Registration Page Pictures PDF from Slidegeeks and deliver a wonderful presentation.
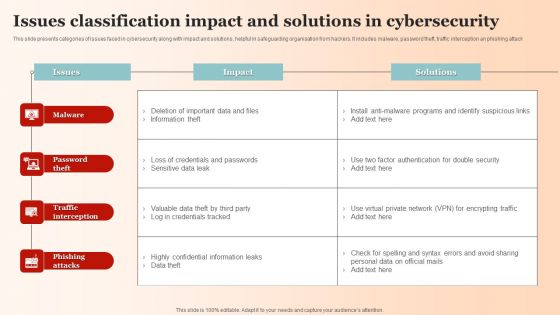
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Techniques To Enhance User Onboarding Journey Best Practices For Customers Registration Page Guidelines PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Techniques To Enhance User Onboarding Journey Best Practices For Customers Registration Page Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
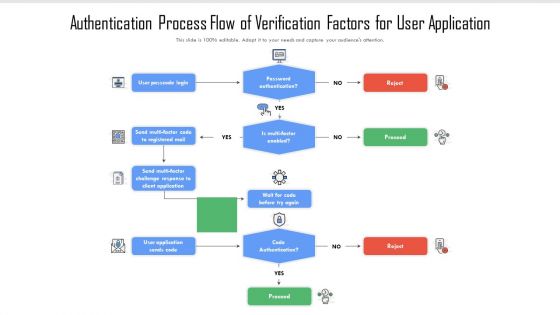
Authentication Process Flow Of Verification Factors For User Application Rules PDF
Pitch your topic with ease and precision using this authentication process flow of verification factors for user application rules pdf. This layout presents information on password authentication, code authentication, user passcode login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Major Statistics Of Cyber Security Awareness Formats PDF
Deliver and pitch your topic in the best possible manner with this Major Statistics Of Cyber Security Awareness Formats PDF. Use them to share invaluable insights on Password Manager, Plaintext, Employees Keep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
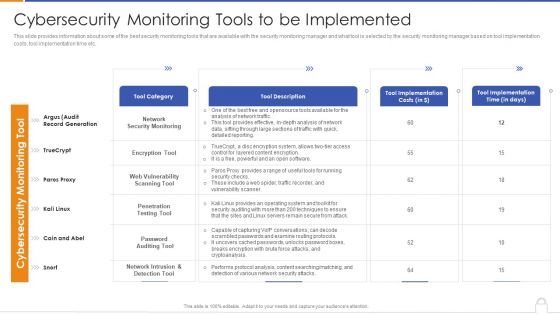
Cybersecurity Monitoring Tools To Be Implemented Topics PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring tools to be implemented topics pdf. Use them to share invaluable insights on security monitoring, password auditing tool, tool implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Sheet To Monitor The Performance Of Employees Demonstration PDF
Deliver an awe inspiring pitch with this creative Tracking Sheet To Monitor The Performance Of Employees Demonstration PDF bundle. Topics like Social Engineering, Ransomware, Password Attack can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
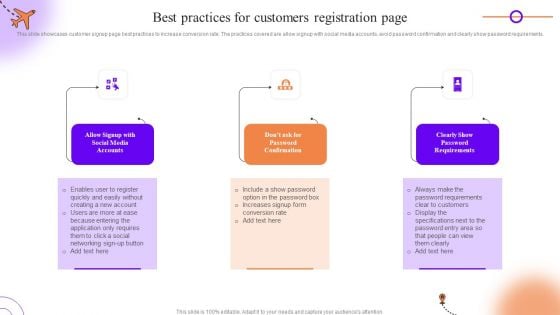
Client Onboarding Journey Impact On Business Best Practices For Customers Registration Page Brochure PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Client Onboarding Journey Impact On Business Best Practices For Customers Registration Page Brochure PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
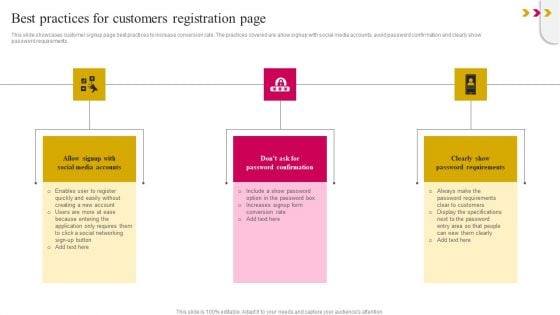
Best Practices For Customers Registration Page Brochure PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Customers Registration Page Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Customers Registration Page Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
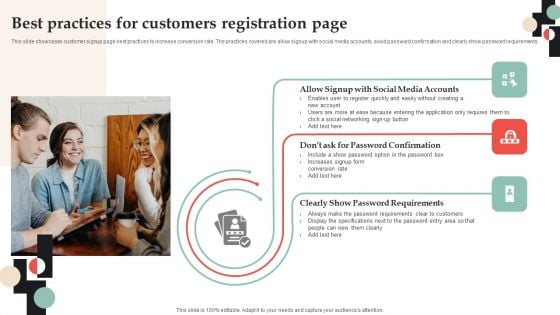
Customer Onboarding Journey Optimization Plan Best Practices For Customers Registration Page Infographics PDF

Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf
This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption Showcasing this set of slides titled Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf. The topics addressed in these templates are Factors, Description, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption
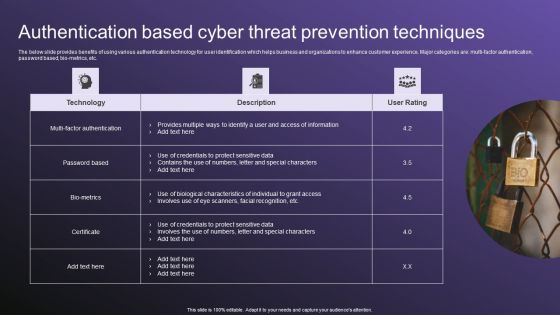
Authentication Based Cyber Threat Prevention Techniques Download PDF
The below slide provides benefits of using various authentication technology for user identification which helps business and organizations to enhance customer experience. Major categories are multi factor authentication, password based, bio-metrics, etc. Showcasing this set of slides titled Authentication Based Cyber Threat Prevention Techniques Download PDF. The topics addressed in these templates are Techniques, Authentication, Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
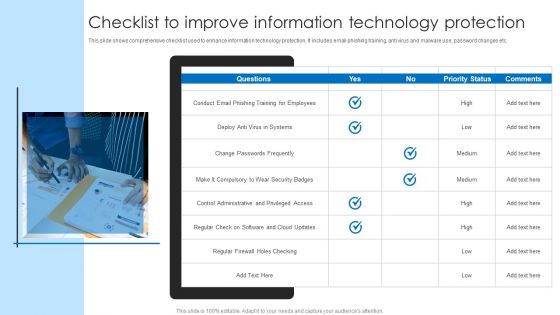
Checklist To Improve Information Technology Protection Inspiration PDF
This slide shows comprehensive checklist used to enhance information technology protection. It includes email phishing training, anti virus and malware use, password changes etc. Presenting Checklist To Improve Information Technology Protection Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security, Employees, Information Technology Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
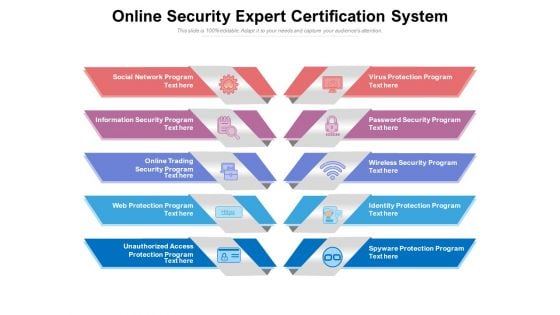
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Learning System For Malware Threat Control Ppt PowerPoint Presentation Layouts Portfolio PDF
Presenting this set of slides with name online security learning system for malware threat control ppt powerpoint presentation layouts portfolio pdf. This is a three stage process. The stages in this process are network protection and control, access control protection, email and web browser protections, virus penetration testing and control fundamentals, password protection, wireless protection, cyber incitement management, ethical hacking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Internet Symbol With Lock PowerPoint Slide
This image slide displays internet symbol with lock. This conceptual image slide has been designed with graphic of blue color at the rate symbol and lock. This image slide depicts online security. Use this PowerPoint template, in your presentations to express views on e-mail, internet, security, safeguard, password and privacy. This image may also be used to exhibit technology protection. This wonderful image is sure to help you achieve your goal of making professional presentations.
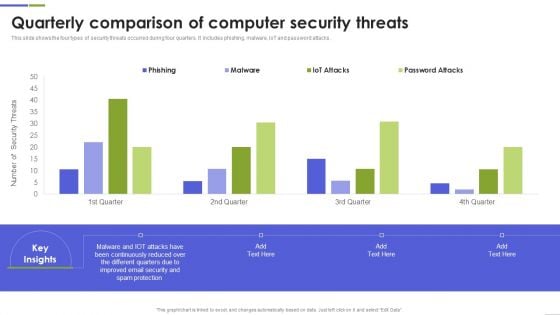
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
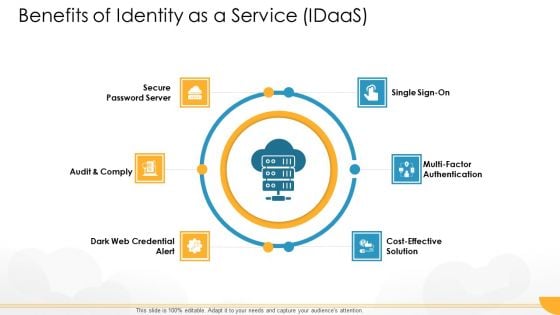
Technology Guide For Serverless Computing Benefits Of Identity As A Service Idaas Summary PDF
This is a technology guide for serverless computing benefits of identity as a service idaas summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure password server, audit and comply, cost effective solution, multi factor authentication, dark web credential alert. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
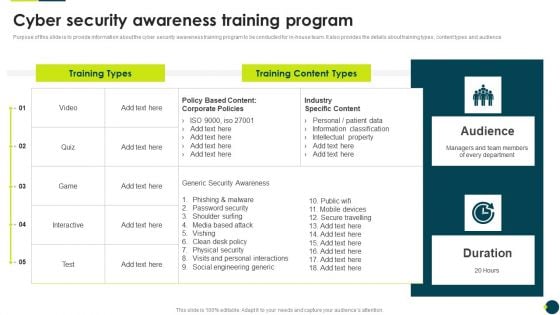
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF
This slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF. This layout presents information on Quarterly Comparison Of Security, Cloud Based Systems Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
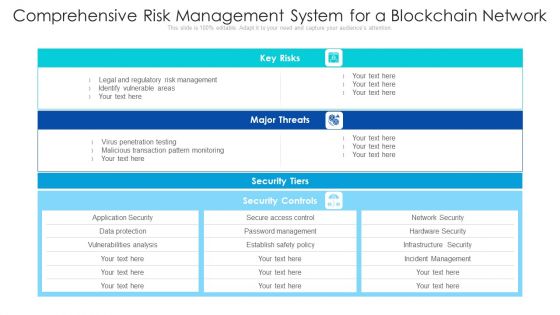
Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Professional Background Images PDF
Pitch your topic with ease and precision using this comprehensive risk management system for a blockchain network ppt powerpoint presentation professional background images pdf. This layout presents information on password management, malicious transaction pattern, identify vulnerable areas. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
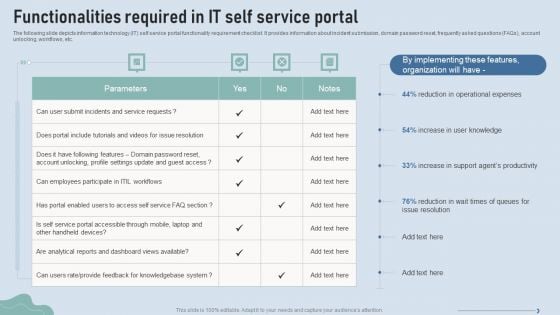
Improve IT Service Desk Functionalities Required In IT Self Service Portal Structure PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Deliver an awe inspiring pitch with this creative Improve IT Service Desk Functionalities Required In IT Self Service Portal Structure PDF bundle. Topics like Operational Expenses, Agents Productivity, Issue Resolution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home