Ransomware
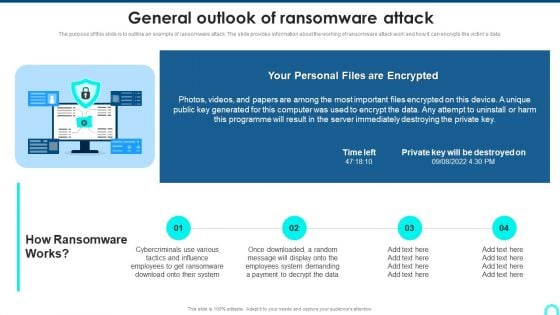
General Outlook Of Ransomware Attack Portrait PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Deliver and pitch your topic in the best possible manner with this General Outlook Of Ransomware Attack Portrait PDF. Use them to share invaluable insights on Tactics Influence, Employees Ransomware, Personal Encrypted and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
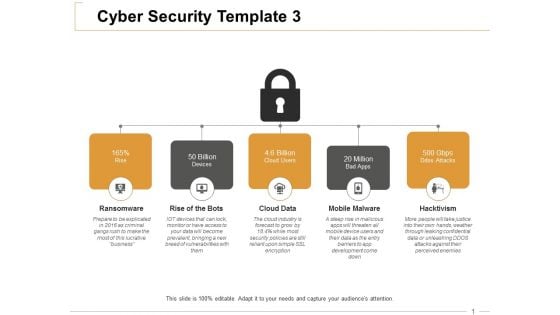
Cyber Security Ransomware Ppt PowerPoint Presentation Summary Graphics Design
This is a cyber security ransomware ppt powerpoint presentation summary graphics design. This is a five stage process. The stages in this process are business, management, planning, strategy, marketing.
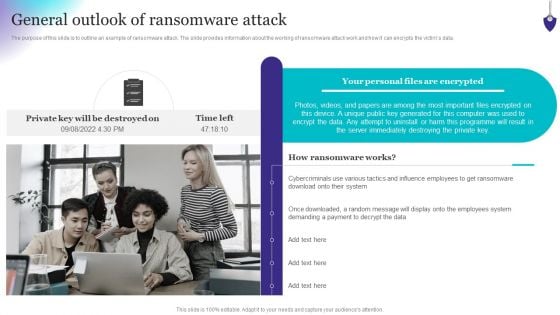
Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Prevention Of Information General Outlook Of Ransomware Attack Summary PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Find highly impressive Prevention Of Information General Outlook Of Ransomware Attack Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Prevention Of Information General Outlook Of Ransomware Attack Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

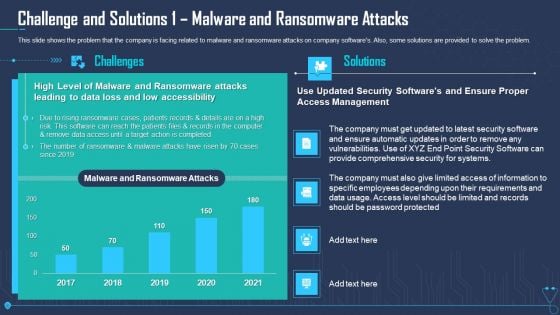
Challenge And Solutions 1 Malware And Ransomware Attacks Icons PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver an awe-inspiring pitch with this creative challenge and solutions 1 malware and ransomware attacks icons pdf. bundle. Topics like challenges, solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
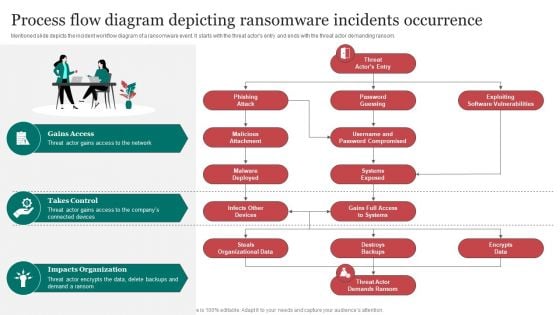
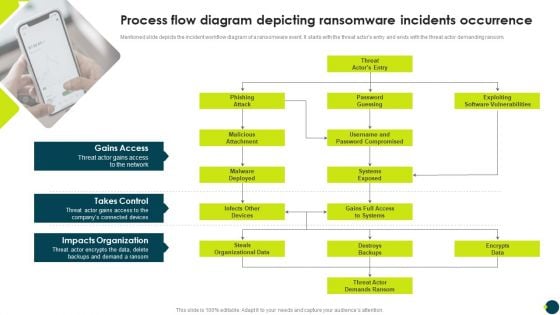
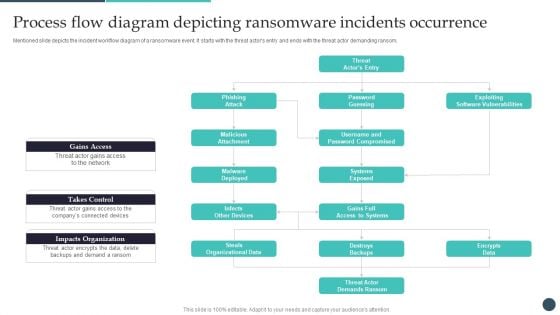
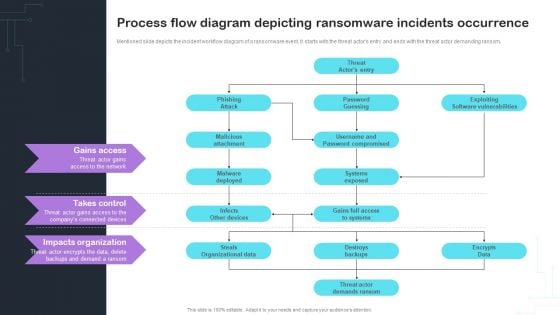
Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom.Explore a selection of the finest Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
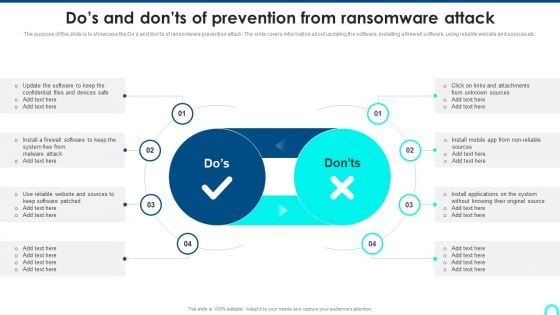
Dos And Donts Of Prevention From Ransomware Attack Summary PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc.Deliver and pitch your topic in the best possible manner with this Dos And Donts Of Prevention From Ransomware Attack Summary PDF. Use them to share invaluable insights on Confidential Files, Install Applications, Keep Software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Process Flow Diagram Depicting Ransomware Incidents Occurrence Sample PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom.Presenting Process Flow Diagram Depicting Ransomware Incidents Occurrence Sample PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Gains Access, Takes Control, Impacts Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Challenge And Solutions 1 Malware And Ransomware Attacks Ppt Pictures Background Images PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver an awe inspiring pitch with this creative challenge and solutions 1 malware and ransomware attacks ppt pictures background images pdf bundle. Topics like challenge and solutions 1 malware and ransomware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Find highly impressive Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Internet Security Ransomware Hacking And Data Loss Threat Ppt PowerPoint Presentation File Formats PDF
Persuade your audience using this internet security ransomware hacking and data loss threat ppt powerpoint presentation file formats pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including internet security ransomware hacking and data loss threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Challenge And Solutions 1 Malware And Ransomware Attacks Ppt Slides Themes PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver an awe inspiring pitch with this creative challenge and solutions 1 malware and ransomware attacks ppt slides themes pdf bundle. Topics like challenges, solutions, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF today and make your presentation stand out from the rest.

Challenge And Solutions 1 Malware And Ransomware Attacks Ppt Model Objects PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver and pitch your topic in the best possible manner with this challenge and solutions 1 malware and ransomware attacks ppt model objects pdf. Use them to share invaluable insights on access management, security software and ensure, comprehensive security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
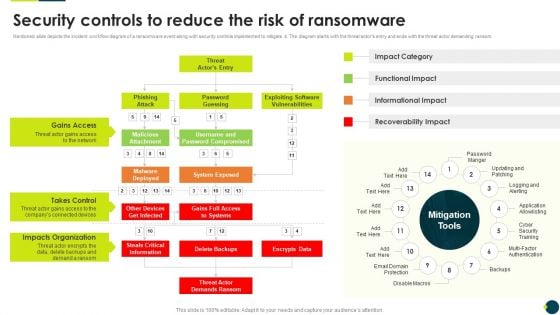
IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. There are so many reasons you need a Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF
The purpose of this slide is to showcase the dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Present like a pro with Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Prevention Of Information Dos And Donts Of Prevention From Ransomware Attack Structure PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Slidegeeks is here to make your presentations a breeze with Prevention Of Information Dos And Donts Of Prevention From Ransomware Attack Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
Cyber Risks And Incident Response Playbook Process Flow Diagram Depicting Ransomware Incidents Occurrence Structure PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Slidegeeks has constructed Cyber Risks And Incident Response Playbook Process Flow Diagram Depicting Ransomware Incidents Occurrence Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
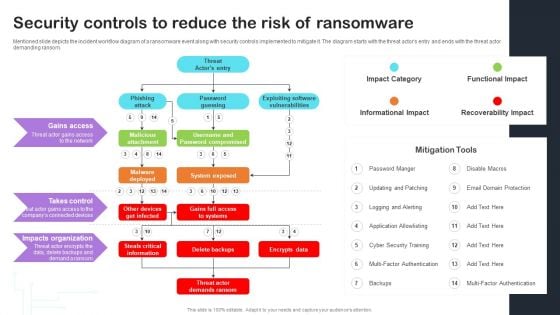
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
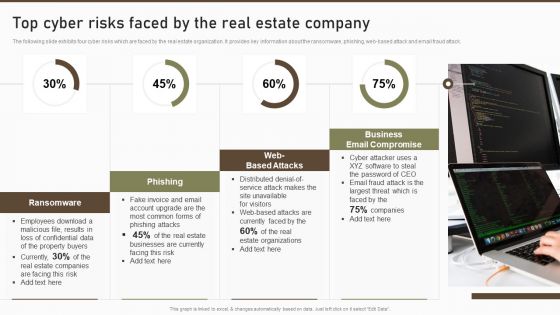
Top Cyber Risks Faced By The Real Estate Company Diagrams PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Deliver an awe inspiring pitch with this creative Top Cyber Risks Faced By The Real Estate Company Diagrams PDF bundle. Topics like Ransomware Business Compromise, Businesses Currently can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
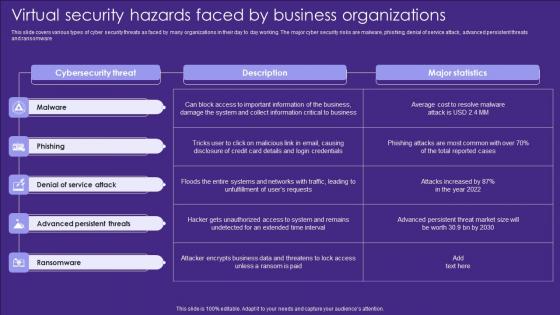
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
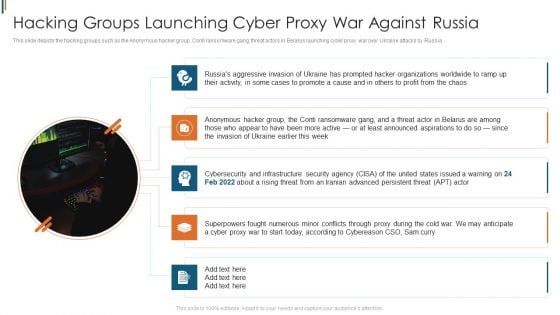
Ukraine Cyberwarfare Hacking Groups Launching Cyber Proxy War Against Russia Guidelines Pdf
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting ukraine cyberwarfare hacking groups launching cyber proxy war against russia guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide.This is a Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Compromise, Ransomware, Malicious Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
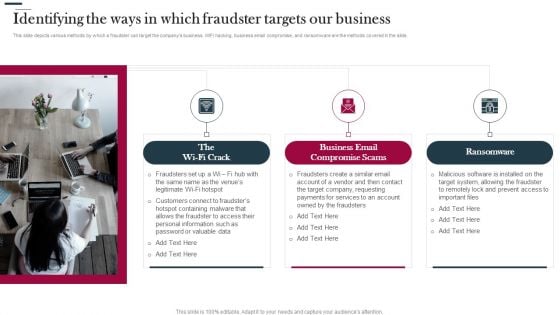
Various Strategies To Prevent Business Identifying The Ways In Which Fraudster Targets Formats PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. This is a Various Strategies To Prevent Business Identifying The Ways In Which Fraudster Targets Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Email, Compromise Scams, Ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
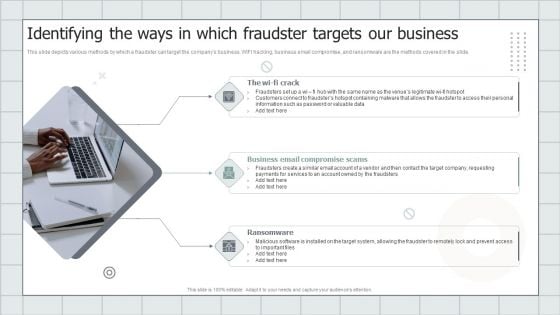
Fraud Avoidance Playbook Identifying The Ways In Which Fraudster Targets Our Business Graphics PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. Presenting Fraud Avoidance Playbook Identifying The Ways In Which Fraudster Targets Our Business Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Wi Fi Crack, Business Email Compromise Scams, Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
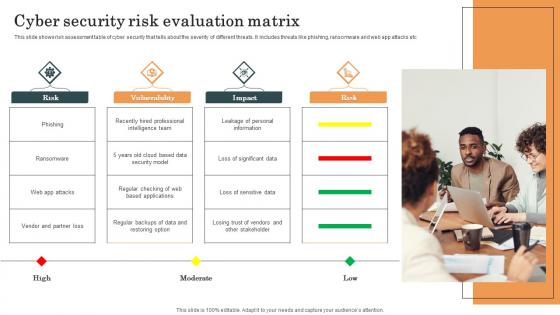
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.

Measures And Ways To Mitigate Security Monitoring Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security monitoring challenges formats pdf bundle. Topics like malware attacks, pnishing attacks, ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
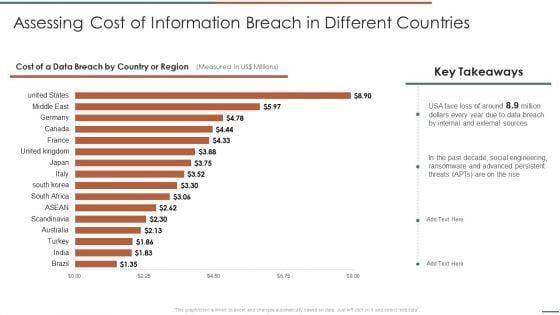
Assessing Cost Of Information Breach In Different Countries Introduction PDF
Deliver and pitch your topic in the best possible manner with this Assessing Cost Of Information Breach In Different Countries Introduction PDF. Use them to share invaluable insights on Internal External, Social Engineering, Ransomware Advanced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Assessment Matrix In Real Estate Project Managing Commercial Property Risks Introduction PDF
Deliver and pitch your topic in the best possible manner with this Risk Assessment Matrix In Real Estate Project Managing Commercial Property Risks Introduction PDF. Use them to share invaluable insights on Employment Issues, Ransomware Attack, Referral Business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
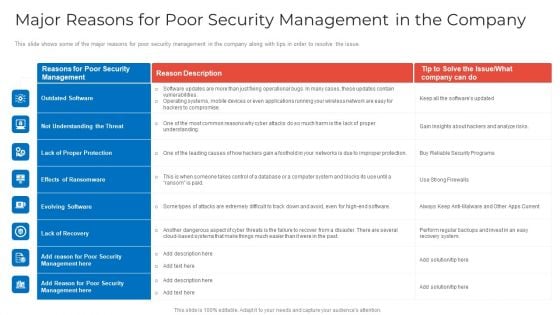
Major Reasons For Poor Security Management In The Company Topics PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company topics pdf bundle. Topics like outdated software, lack of proper protection, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
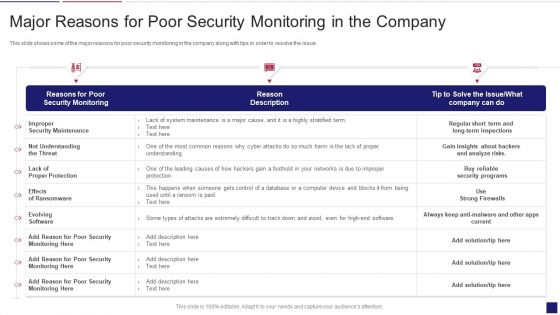
Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
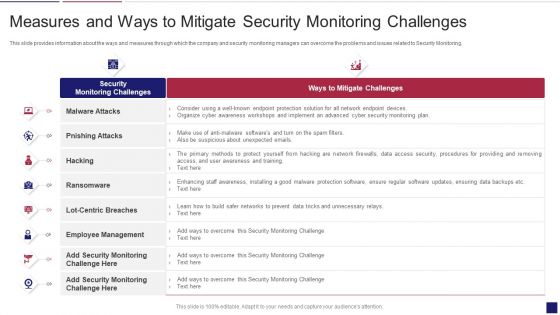
Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
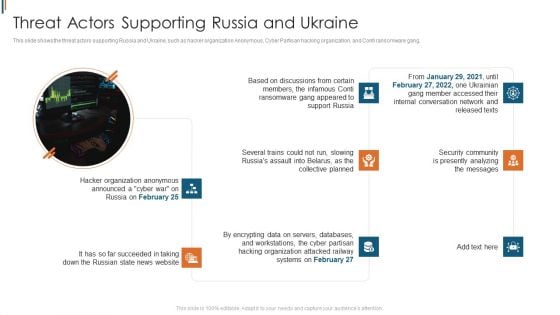
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
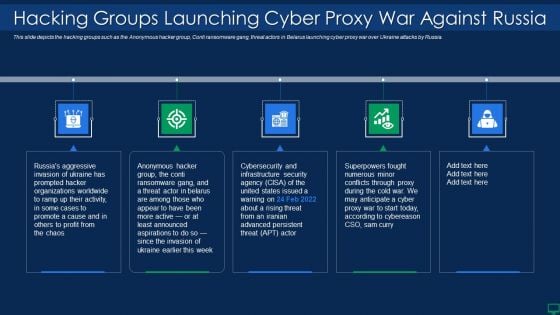
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
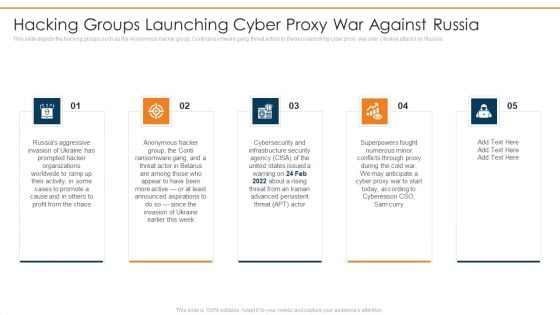
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
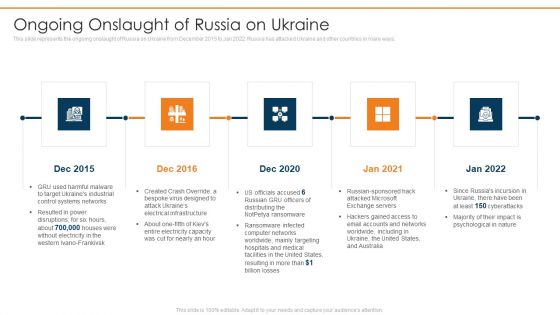
Data Wiper Spyware Attack Ongoing Onslaught Of Russia On Ukraine Inspiration PDF
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways.This is a data wiper spyware attack ongoing onslaught of russia on ukraine inspiration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like entire electricity capacity, electrical infrastructure, ransomware infected You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
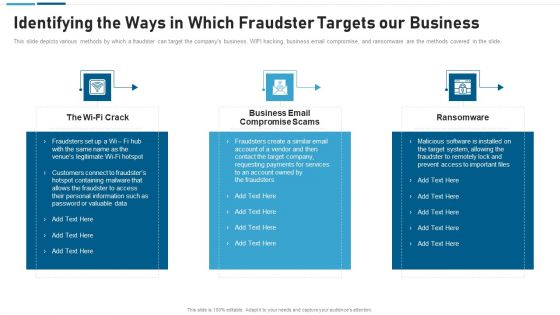
Anti Scam Playbook Identifying The Ways In Which Fraudster Targets Our Business Formats PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. Presenting Anti Scam Playbook Identifying The Ways In Which Fraudster Targets Our Business Formats PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Identifying The Ways In Which Fraudster Targets Our Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Cyber War Threats With Risk Priority Summary PDF
This slide represents the five major threats caused by cyber terrorism along with their risk priorities. It includes threats such as malware, phishing, spear fishing, SQL injection and advanced persistent threats.Showcasing this set of slides titled Various Cyber War Threats With Risk Priority Summary PDF The topics addressed in these templates are Malicious Software, Includes Spywares, Ransomware Viruses All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
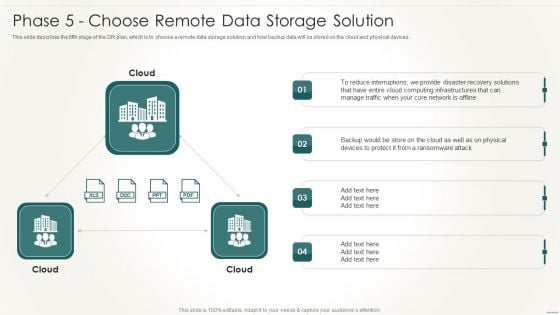
Information Technology Disaster Resilience Plan Phase 5 Choose Remote Data Storage Solution Slides PDF
This slide describes the fifth stage of the DR plan, which is to choose a remote data storage solution and how backup data will be stored on the cloud and physical devices.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan Phase 5 Choose Remote Data Storage Solution Slides PDF bundle. Topics like Reduce Interruptions, Computing Infrastructures, Ransomware Attack can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

AIOPS Implementation Artificial Intelligence For IT Operations In Healthcare Industry Formats PDF
This slide depicts the application of AIOps in the healthcare industry that includes maintaining the security of personal health information, defending against ransomware attacks, etc. This is a AIOPS Implementation Artificial Intelligence For IT Operations In Healthcare Industry Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Electronic Personal, Health Information, Medical Practitioners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
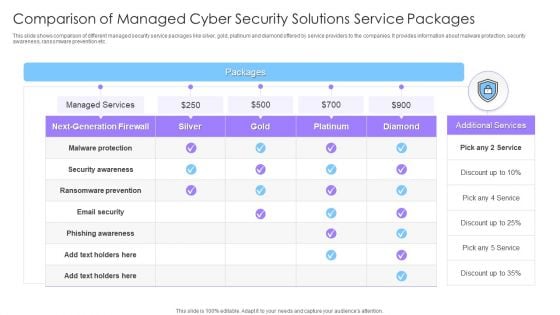
Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
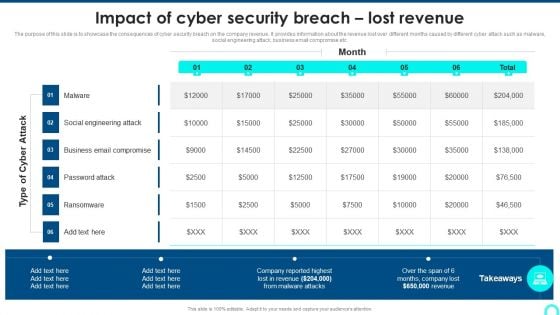
Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
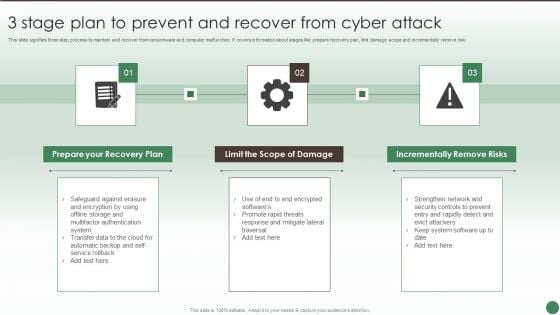
3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
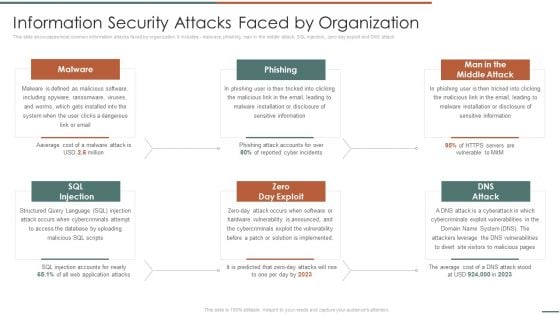
Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack.Presenting Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Malicious Software, Including Spyware, Ransomware Viruses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
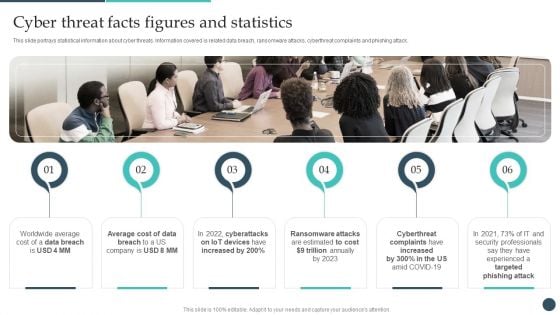
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Identifying The Ways In Which Fraudster Targets Our Business One Pager Sample Example Document
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. Presenting you an exemplary Identifying The Ways In Which Fraudster Targets Our Business One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Identifying The Ways In Which Fraudster Targets Our Business One Pager Sample Example Document brilliant piece now.
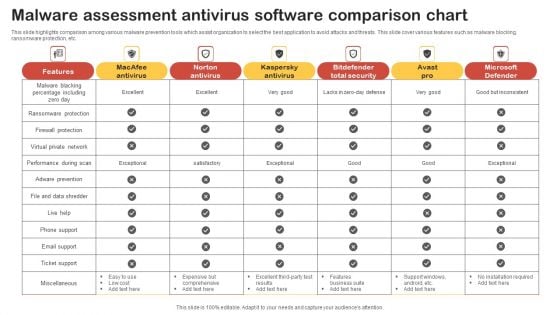
Malware Assessment Antivirus Software Comparison Chart Template PDF
This slide highlights comparison among various malware prevention tools which assist organization to select the best application to avoid attacks and threats. This slide cover various features such as malware blocking, ransomware protection, etc. Showcasing this set of slides titled Malware Assessment Antivirus Software Comparison Chart Template PDF. The topics addressed in these templates are Features, Macafee Antivirus, Norton Antivirus. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
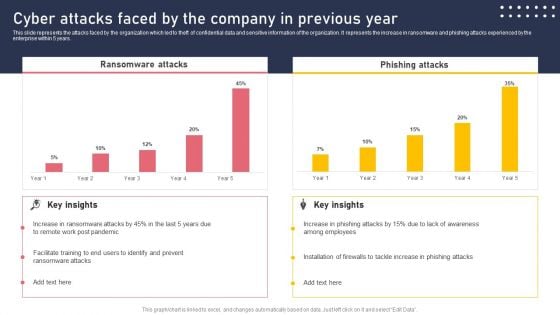
Cyber Attacks Faced By The Company In Previous Year Portrait PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Attacks Faced By The Company In Previous Year Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
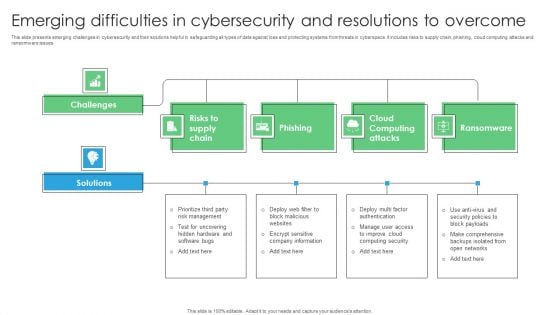
Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF
This slide presents emerging challenges in cybersecurity and their solutions helpful in safeguarding all types of data against loss and protecting systems from threats in cyberspace. It includes risks to supply chain, phishing, cloud computing attacks and ransomware issues. Introducing Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF. to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risks Supply Chain, Phishing, Cloud Computing Attacks, using this template. Grab it now to reap its full benefits.
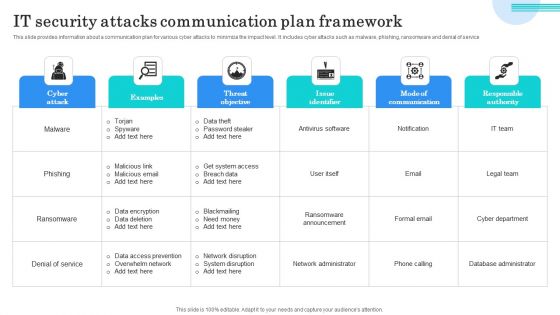
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
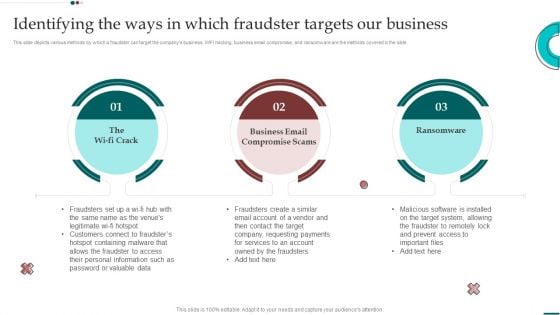
Scam Inquiry And Response Playbook Identifying The Ways In Which Fraudster Targets Our Business Ideas PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. Welcome to our selection of the Scam Inquiry And Response Playbook Identifying The Ways In Which Fraudster Targets Our Business Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

 Home
Home