Security Dashboard
Email Security Market Research Report Managed E Mail Security Introduction PDF
Presenting this set of slides with name email security market research report managed e mail security introduction pdf. This is a two stage process. The stages in this process are e mail security is hosted by a cloud server, however is managed by a third party, provides organization both independence and control over the security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
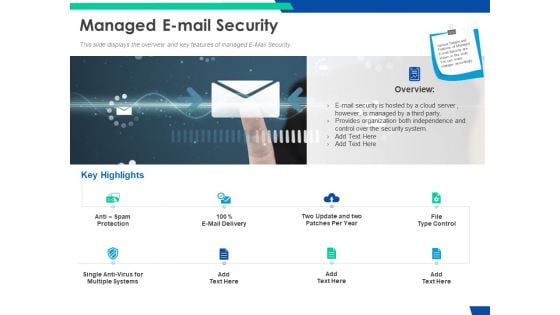
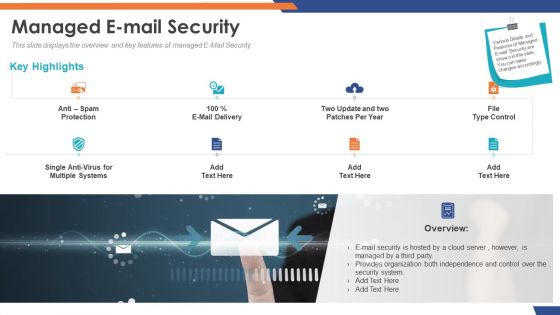
Cloud Based Email Security Market Report Managed E Mail Security Ppt Infographic Template Themes PDF
This slide displays the overview and key features of managed E Mail Security. Presenting cloud based email security market report managed e mail security ppt infographic template themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like managed e mail security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Access Control Cloud Computing Security IT Ppt Show PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Deliver and pitch your topic in the best possible manner with this cloud security checklist access control cloud computing security it ppt show pdf. Use them to share invaluable insights on cloud services, security, privileged credentials, administrative and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
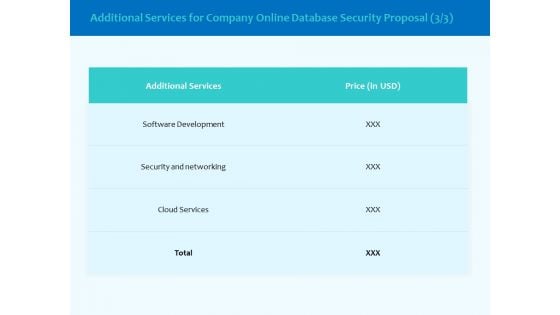
Best Data Security Software Additional Services For Company Online Database Security Proposal Pictures PDF
Presenting this set of slides with name best data security software additional services for company online database security proposal pictures pdf. The topics discussed in these slides are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
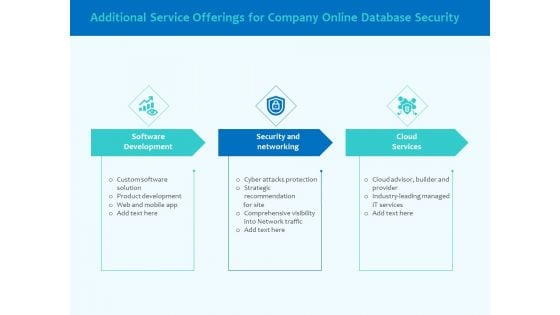
Best Data Security Software Additional Service Offerings For Company Online Database Security Designs PDF
Presenting this set of slides with name best data security software additional service offerings for company online database security designs pdf. This is a three stage process. The stages in this process are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Cover Letter For Company Online Database Security Proposal Designs PDF
Presenting this set of slides with name best data security software cover letter for company online database security proposal designs pdf. This is a one stage process. The stages in this process are cover letter, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Best Data Security Software Timeline For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software timeline for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are timeline, company, online database security, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

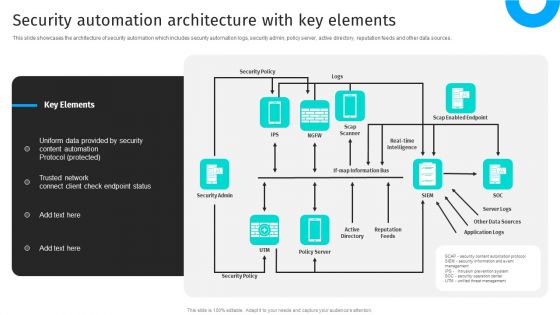
IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources.This modern and well-arranged Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
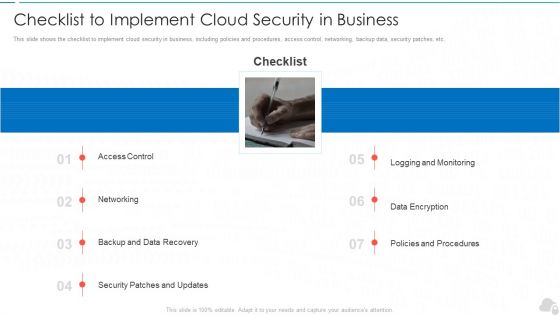
Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
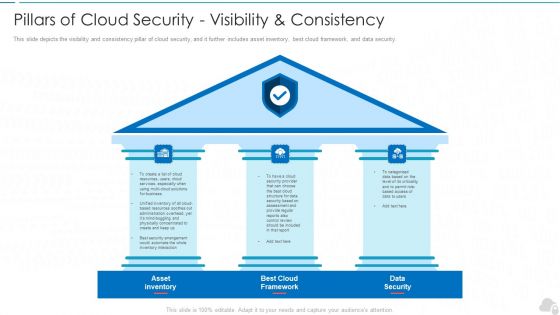
Pillars Of Cloud Security Visibility And Consistency Cloud Computing Security IT Ppt Slide PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting pillars of cloud security visibility and consistency cloud computing security it ppt slide pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like asset inventory, best cloud framework, data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Roadmap For Information Technology Security Training Ppt Layouts Vector PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a it security roadmap for information technology security training ppt layouts vector pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, ensuring data security, mobile and remote computing best practices, safe and computing best practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
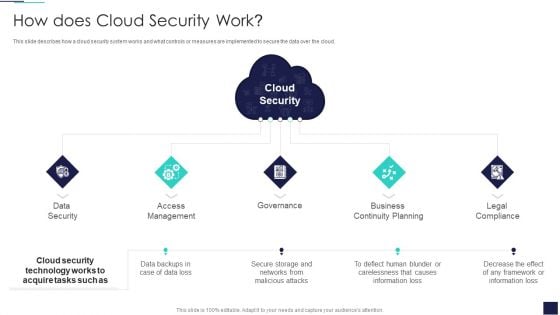
Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Roadmap Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a security awareness training roadmap hacking prevention awareness training for it security template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, physical security, privacy threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
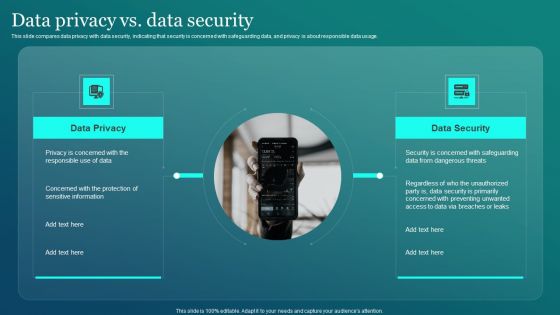
Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
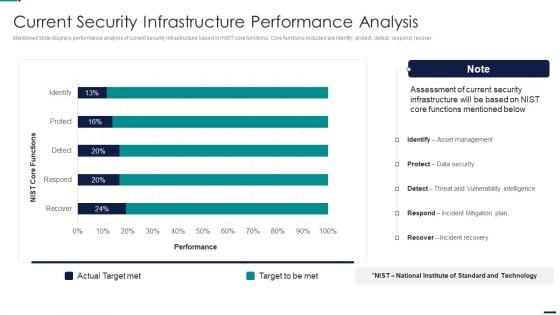
Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. This is a Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost Effective, Diminished Administration, Centralized Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
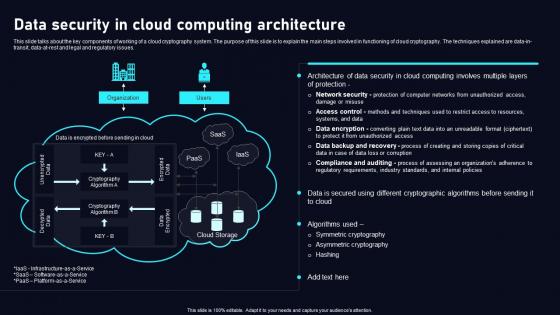
Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
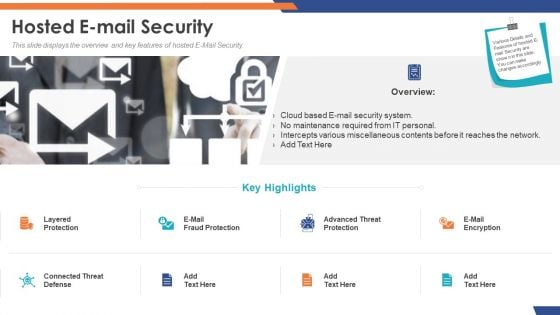
Email Security Market Research Report Hosted E Mail Security Formats PDF
Presenting this set of slides with name email security market research report hosted e mail security formats pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Create an editable Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
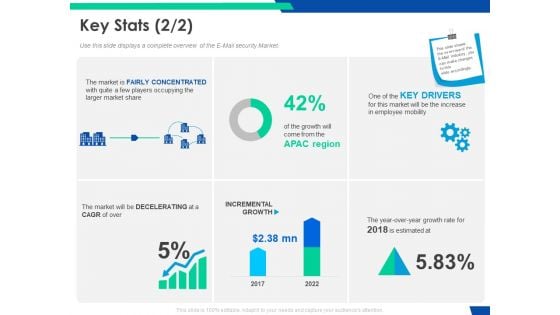
Cloud Based Email Security Market Report Key Stats Security Ppt Slides Demonstration PDF
Use this slide displays a complete overview of the E Mail security Market. Deliver and pitch your topic in the best possible manner with this cloud based email security market report key stats security ppt slides demonstration pdf. Use them to share invaluable insights on key stats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
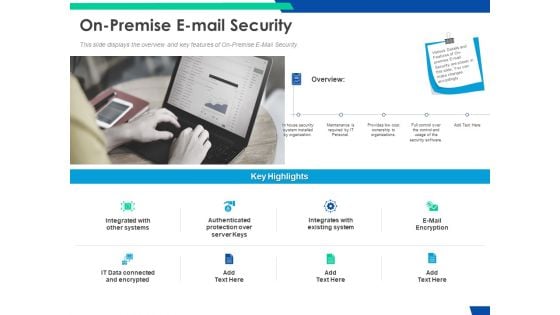
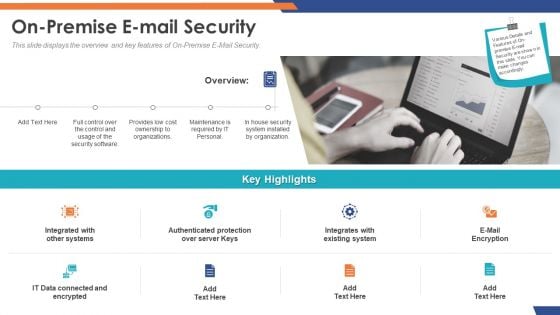
Cloud Based Email Security Market Report On Premise E Mail Security Ppt Ideas Design Inspiration PDF
This slide displays the overview and key features of On Premise E Mail Security. This is a cloud based email security market report on premise e mail security ppt ideas design inspiration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like on premise e mail security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
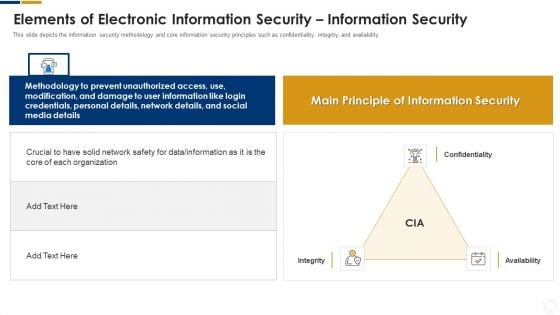
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
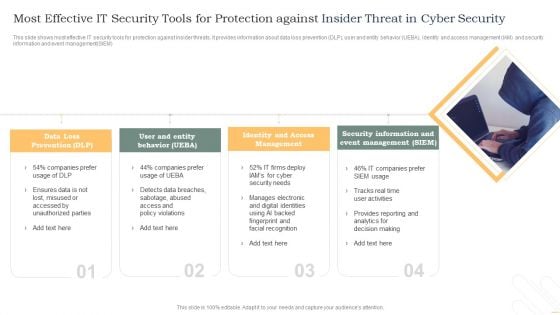
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
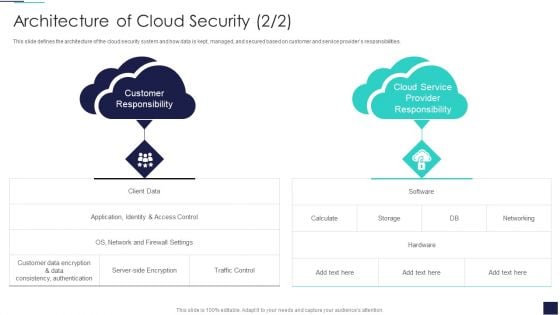
Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Responsibility, Cloud Service, Provider Responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
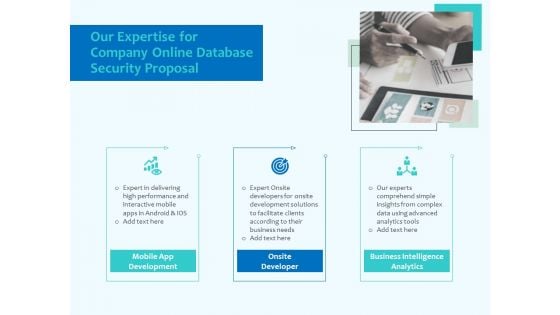
Best Data Security Software Our Expertise For Company Online Database Security Proposal Formats PDF
Presenting this set of slides with name best data security software our expertise for company online database security proposal formats pdf. This is a three stage process. The stages in this process are mobile app development, onsite developer, business intelligence analytics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
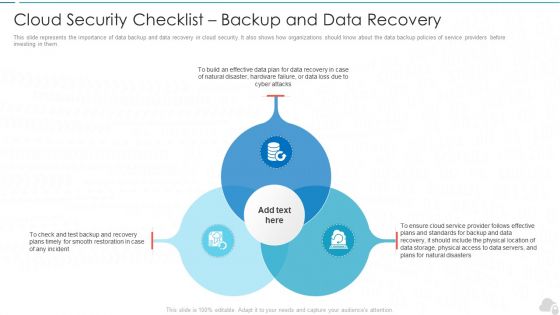
Cloud Security Checklist Backup And Data Recovery Cloud Computing Security IT Ppt Styles Rules PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting cloud security checklist backup and data recovery cloud computing security it ppt styles rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like effective, cloud service, natural disasters, data plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Loss Of Data Cloud Computing Security IT Ppt Infographics Graphic Tips PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a cloud security threats loss of data cloud computing security it ppt infographics graphic tips pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like locations, cloud service, strategies, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Case Study For Company Online Database Security Proposal Template PDF
Presenting this set of slides with name best data security software case study for company online database security proposal template pdf. This is a three stage process. The stages in this process are problem, our solution, results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Project Context And Objectives For Cyber Security Services Pictures PDF
Presenting this set of slides with name best data security software project context and objectives for cyber security services pictures pdf. This is a six stage process. The stages in this process are project context, project objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
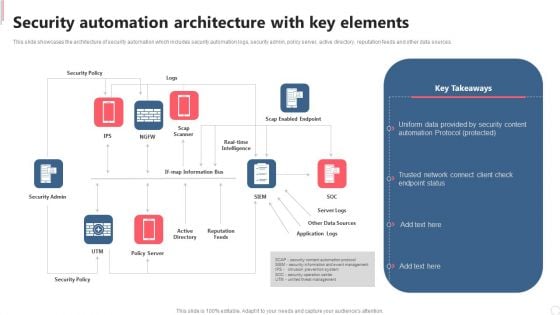
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Best Data Security Software Mode Of Communication For Company Online Database Security Proposal Inspiration PDF
Presenting this set of slides with name best data security software mode of communication for company online database security proposal inspiration pdf. The topics discussed in these slides are communicate medium, description. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
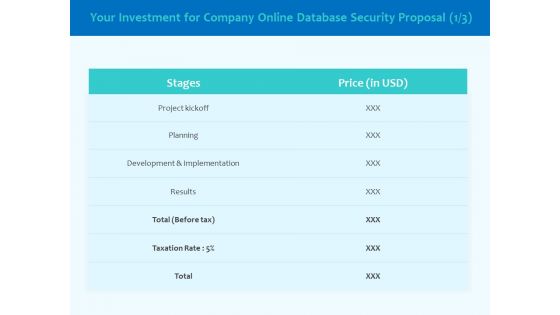
Best Data Security Software Your Investment For Company Online Database Security Proposal Slides PDF
Presenting this set of slides with name best data security software your investment for company online database security proposal slides pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
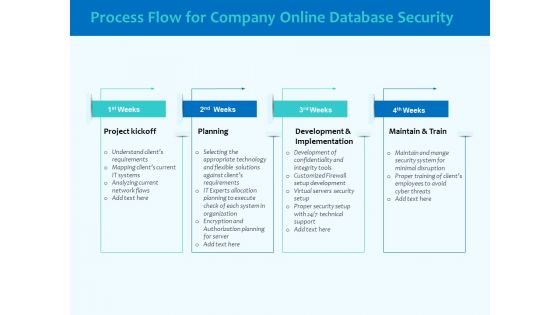
Best Data Security Software Process Flow For Company Online Database Security Elements PDF
Presenting this set of slides with name best data security software process flow for company online database security elements pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeframe For Company Online Database Security Proposal Topics PDF
Presenting this set of slides with name best data security software timeframe for company online database security proposal topics pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
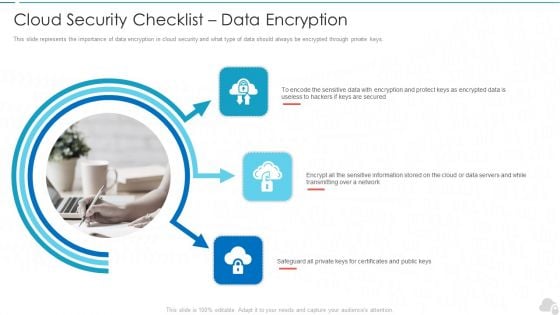
Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
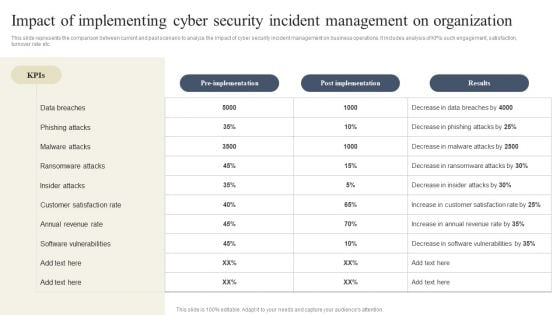
CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.
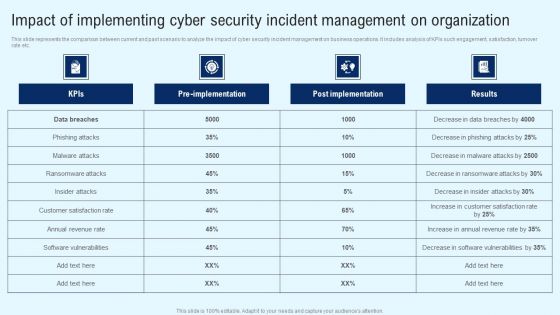
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
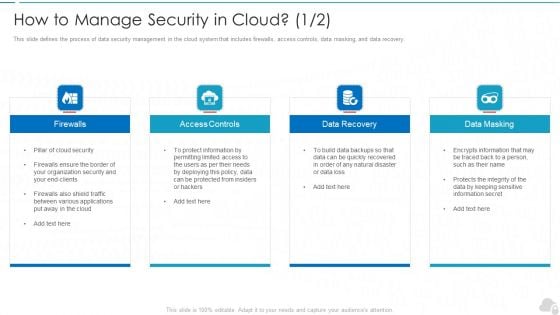
How To Manage Security In Cloud Cloud Computing Security IT Ppt Model Graphic Images PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting how to manage security in cloud cloud computing security it ppt model graphic images pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like firewalls, access controls, data recovery, data masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
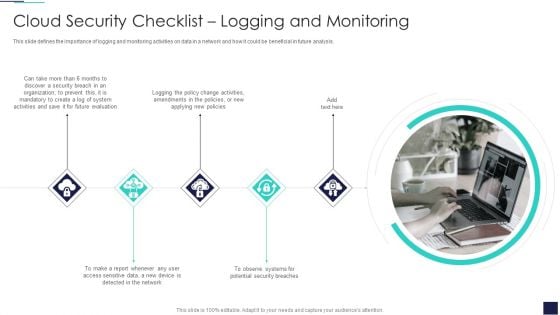
Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
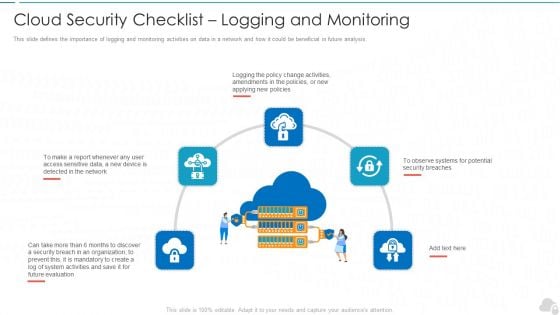
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
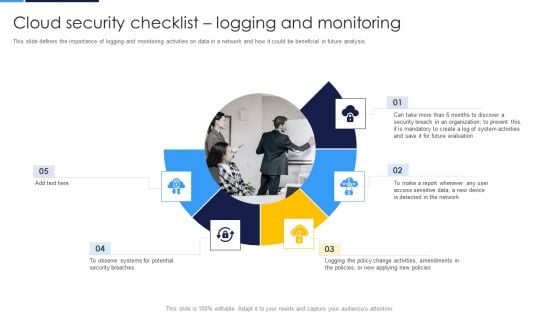
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
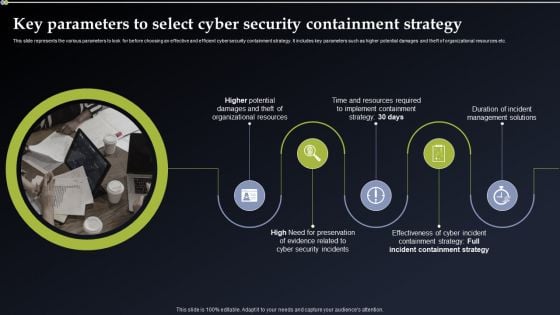
Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
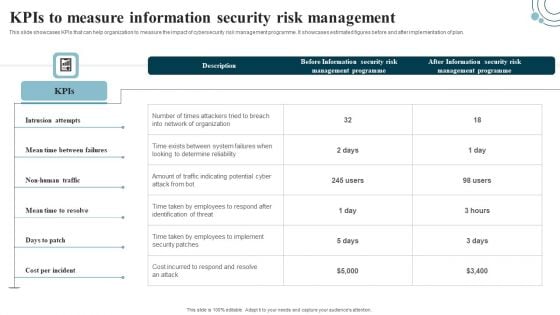
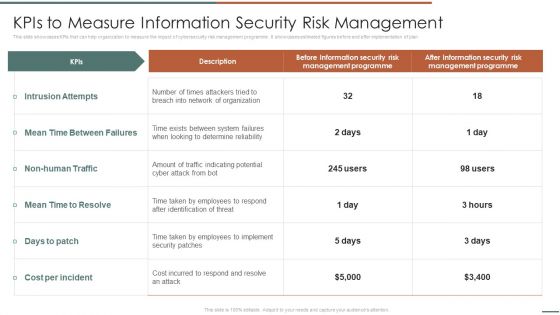
Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Solutions, Advanced Threats, Cipher Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Email Security Market Research Report On Premise E Mail Security Mockup PDF
Presenting this set of slides with name email security market research report on premise e mail security mockup pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Best Data Security Software Next Steps For Company Online Database Security Infographics PDF
Presenting this set of slides with name best data security software next steps for company online database security infographics pdf. This is a two stage process. The stages in this process are discuss the desired changes, accept the proposal, once we get the notification of your proposal acceptance, we will send you the separate copy of the signed contract for your record. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

 Home
Home