Security Strategy
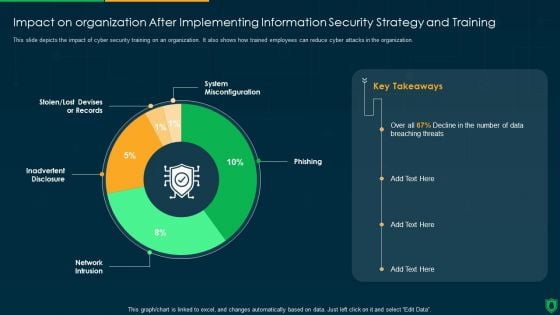
Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
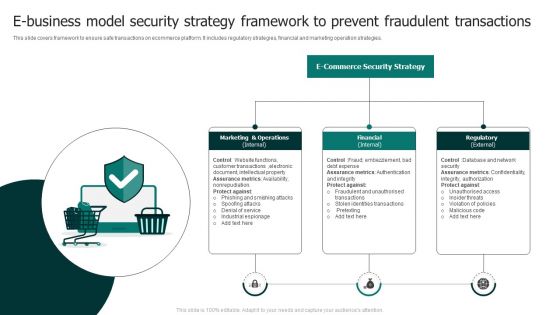
E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
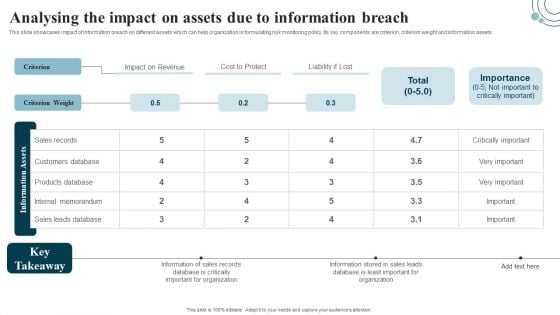
Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Developing Firm Security Strategy Plan Addressing Risk Response Plan For Firms Guidelines PDF
This slide provides information regarding risk response plan for firms in terms of employee safety, development of cross functional team, ensuring liquidity and developing contingency plan, etc. This is a developing firm security strategy plan addressing risk response plan for firms guidelines pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee safety, development of cross functional team, ensuring liquidity, developing contingency plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Addressing Workforce Assistance Program Topics PDF
The workforce assistance program will help firms in enhancing their well being at workplace and enable them to handle critical or emergence situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting developing firm security strategy plan addressing workforce assistance program topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
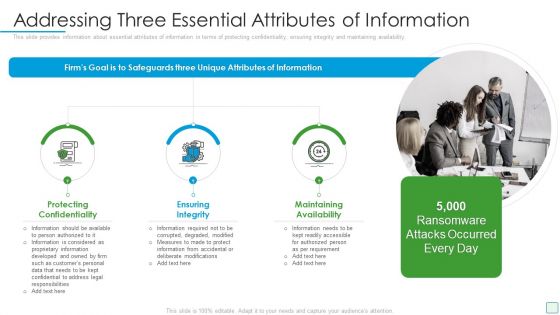
Developing Firm Security Strategy Plan Addressing Three Essential Attributes Of Information Summary PDF
This slide provides information about essential attributes of information in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a developing firm security strategy plan addressing three essential attributes of information summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Potential Risk Management Action Plan Microsoft PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan potential risk management action plan microsoft pdf. Use them to share invaluable insights on potential risk, required resources, communication, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
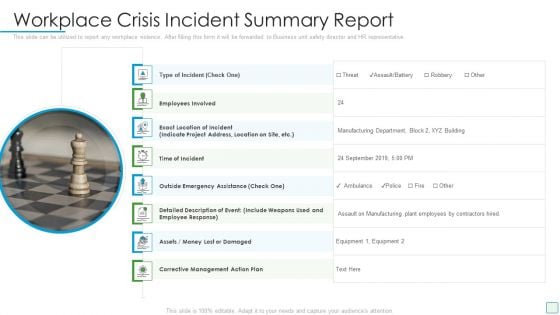
Developing Firm Security Strategy Plan Workplace Crisis Incident Summary Report Professional PDF
This slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting developing firm security strategy plan workplace crisis incident summary report professional pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like management action plan, time of incident, employees involved, outside emergency assistance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Addressing Vital Records Maintenance Centre Inspiration PDF
The team will keep the track of crucial information and the location where these records are kept also the alternate backup location of the records and the other sources through which records can be retrieved. Presenting developing firm security strategy plan addressing vital records maintenance centre inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like description, primary location of records, alternate backup location of records, other sources to obtain records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan How To Handle Financial Crisis At Workplace Themes PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Presenting developing firm security strategy plan how to handle financial crisis at workplace themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like abundant cash requirement, key financial statements, overheads analysis, currency hedging, preparing aged debtors trial balance on monthly basis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
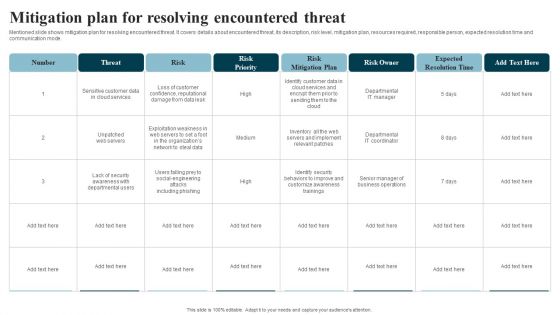
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
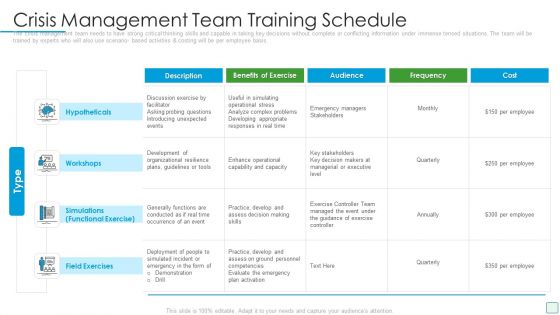
Developing Firm Security Strategy Plan Crisis Management Team Training Schedule Demonstration PDF
The crisis management team needs to have strong critical thinking skills and capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan crisis management team training schedule demonstration pdf. Use them to share invaluable insights on hypotheticals, workshops, simulations, field exercises and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
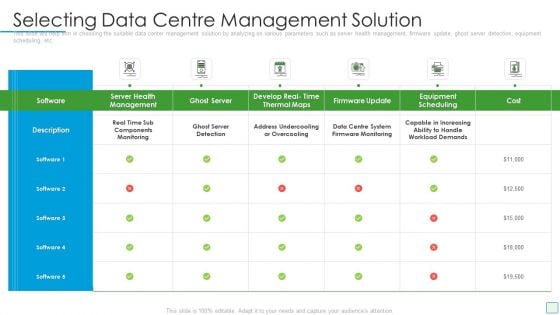
Developing Firm Security Strategy Plan Selecting Data Centre Management Solution Pictures PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan selecting data centre management solution pictures pdf. Use them to share invaluable insights on monitoring, management, develop, ghost server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
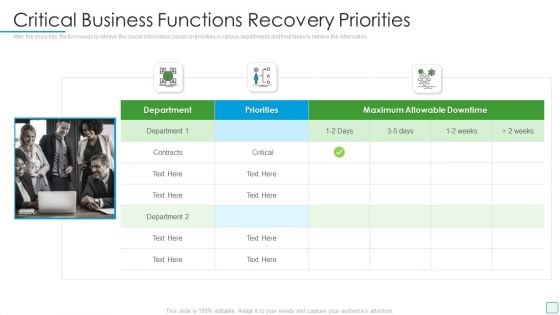
Developing Firm Security Strategy Plan Critical Business Functions Recovery Priorities Infographics PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a developing firm security strategy plan critical business functions recovery priorities infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement Infographics PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting developing firm security strategy plan determine staff training schedule for skills enhancement infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
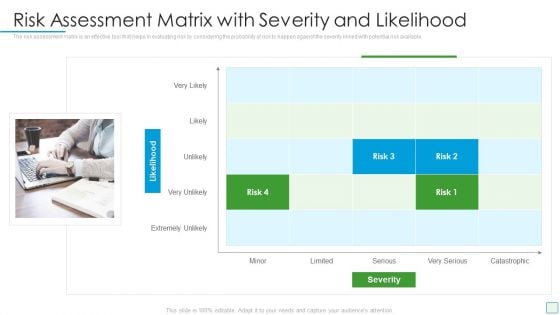
Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF
Slidegeeks has constructed Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF
Do you know about Slidesgeeks Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
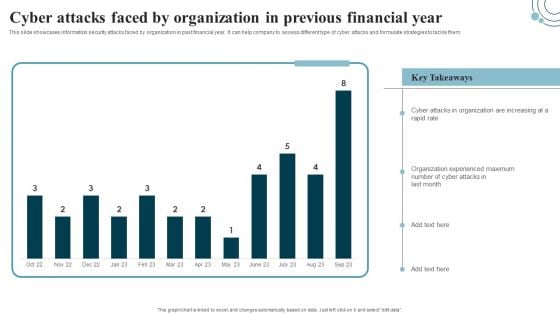
Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
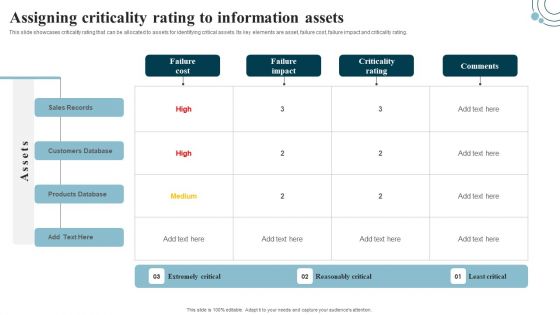
Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. This modern and well-arranged Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Developing Firm Security Strategy Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
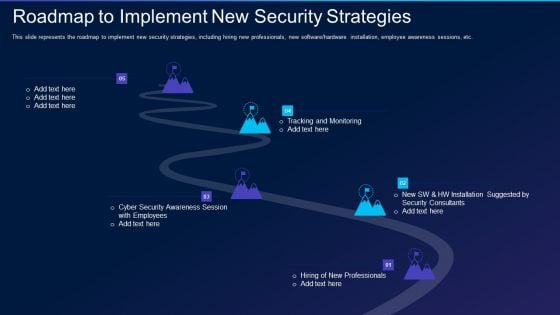
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
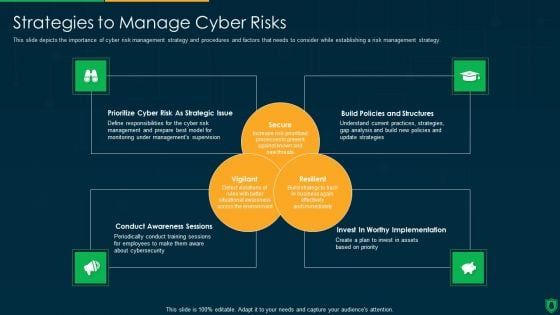
Info Security Strategies To Manage Cyber Risks Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a info security strategies to manage cyber risks ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prioritize cyber risk as strategic issue, build policies and structures, conduct awareness sessions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
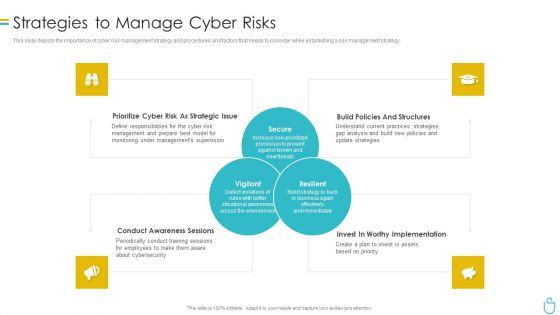
Information Security Strategies To Manage Cyber Risks Ppt Layouts Gridlines PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information security strategies to manage cyber risks ppt layouts gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk, management, strategies, analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Strategies To Manage Cyber Risks Ppt Icon Gallery PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting it security strategies to manage cyber risks ppt icon gallery pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like conduct awareness sessions, prioritize cyber risk as strategic issue, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Impact Of Critical Security Concerns Issues On Overall Firms Performance Pictures PDF
This slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Deliver an awe inspiring pitch with this creative developing firm security strategy plan impact of critical security concerns issues on overall firms performance pictures pdf bundle. Topics like loss in sales, customer dissatisfaction, tarnished reputation, decrease in customer loyalty, increase in expenses can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Administration Strategy Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security administration strategy security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

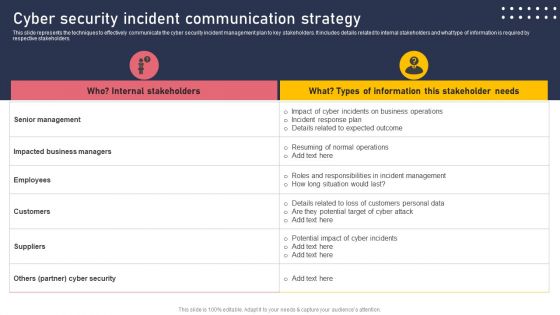
Cyber Security Incident Communication Strategy Information PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Communication Strategy Information PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Communication Strategy Information PDF.
Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
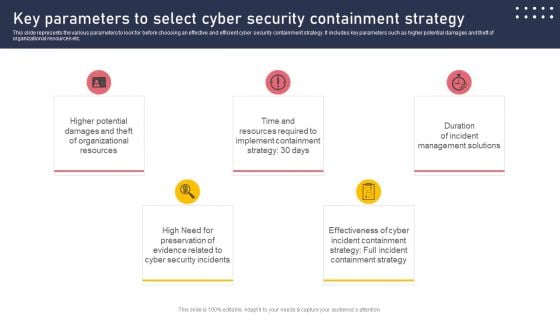
Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Table Of Contents Organizational Assets Security Management Strategy Information PDF
Find highly impressive Table Of Contents Organizational Assets Security Management Strategy Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizational Assets Security Management Strategy Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
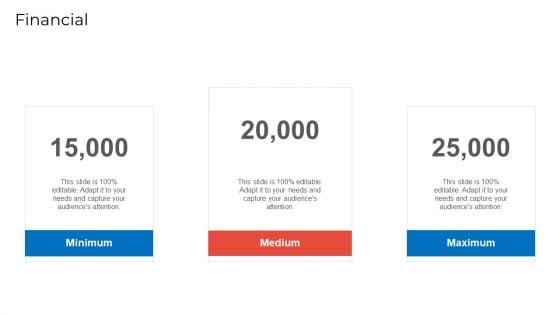
Implementing Security Management Strategy To Mitigate Risk Financial Summary PDF
This is a implementing security management strategy to mitigate risk financial summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
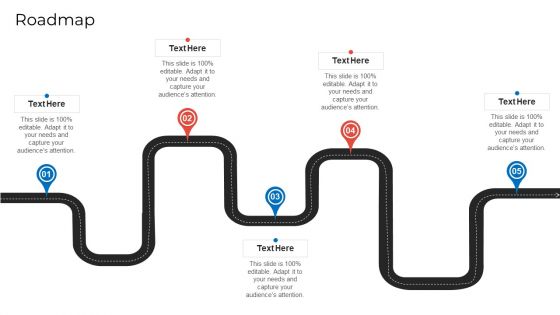
Implementing Security Management Strategy To Mitigate Risk Roadmap Diagrams PDF
Presenting implementing security management strategy to mitigate risk roadmap diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
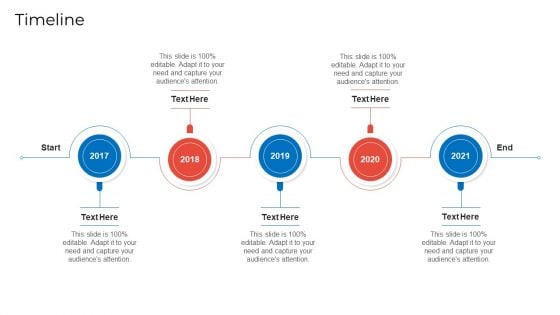
Implementing Security Management Strategy To Mitigate Risk Timeline Rules PDF
Presenting implementing security management strategy to mitigate risk timeline rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Impact On Organization After Implementing Information Technology Security Strategy And Training Ppt Slides Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this it security impact on organization after implementing information technology security strategy and training ppt slides deck pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Technology Security Key Strategies Icon Slides PDF
Persuade your audience using this Information Technology Security Key Strategies Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology Security, Key Strategies Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
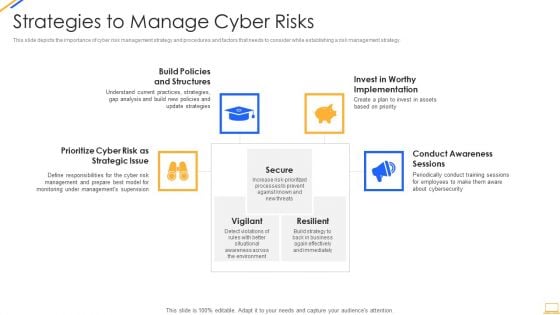
Desktop Security Management Strategies To Manage Cyber Risks Rules PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting desktop security management strategies to manage cyber risks rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strategic, risk, implementation, awareness, invest. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
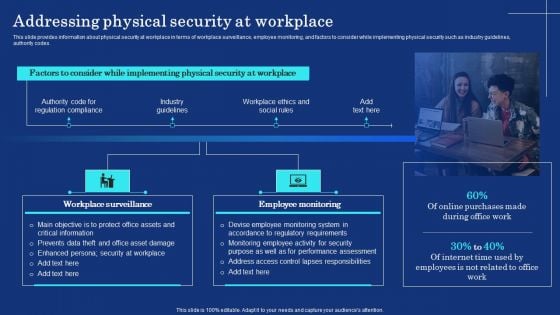
Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Create an editable Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
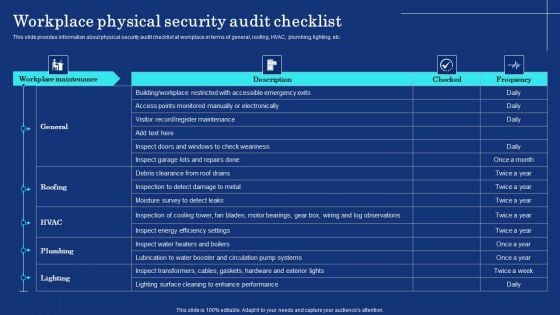
Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present like a pro with Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
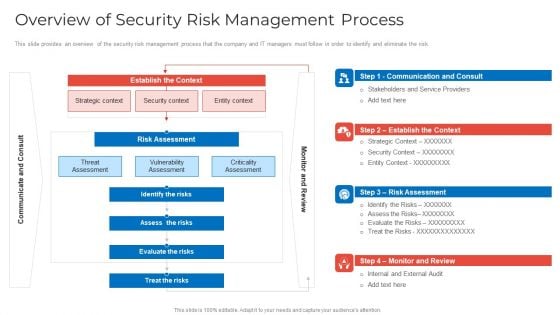
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
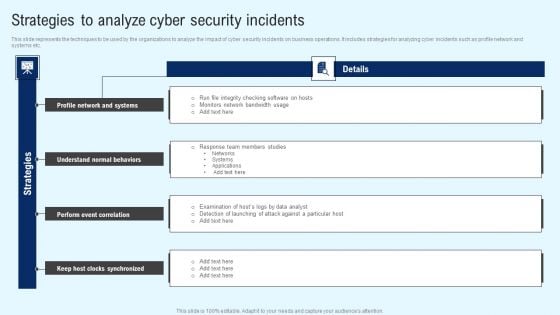
Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
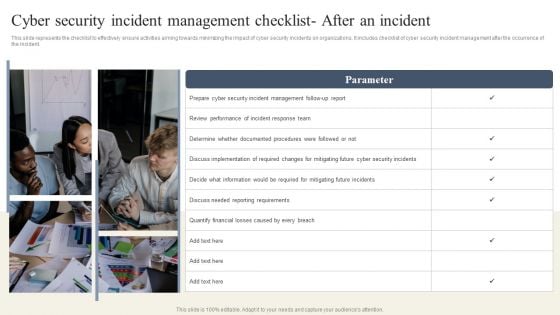
CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF can be your best option for delivering a presentation. Represent everything in detail using CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Find highly impressive CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF
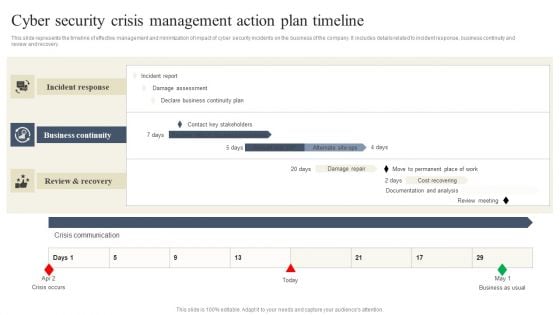
CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Get a simple yet stunning designed CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
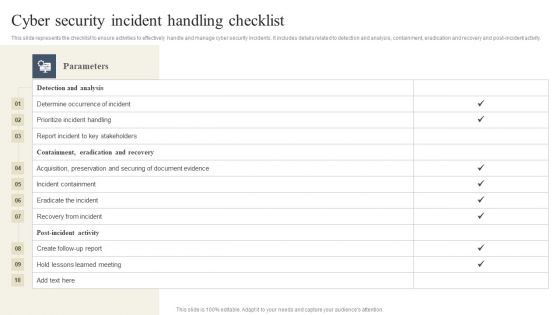
CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.
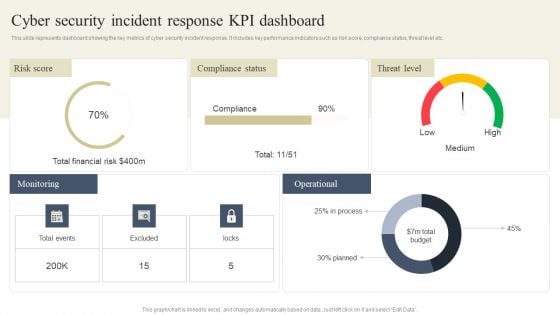
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
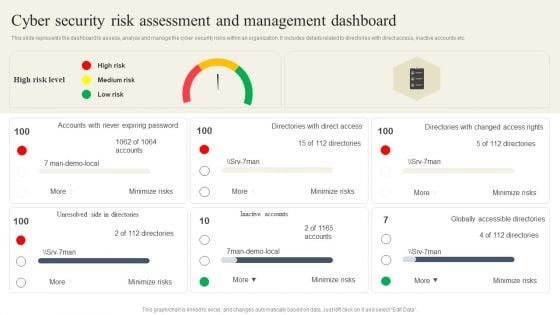
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
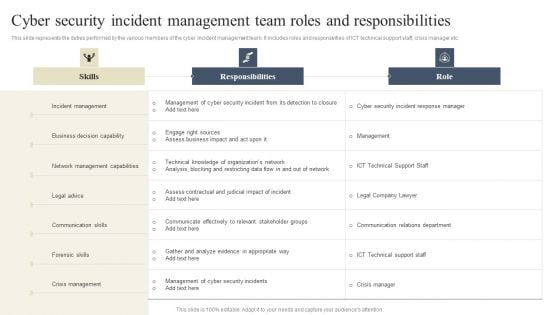
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
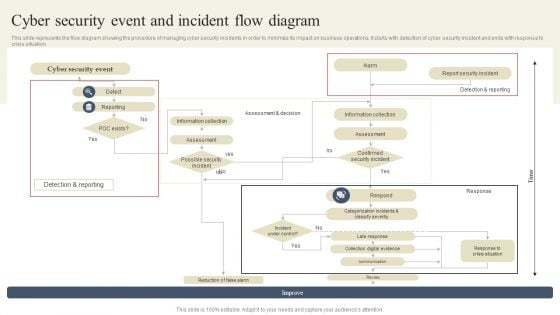
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Slidegeeks is here to make your presentations a breeze with CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
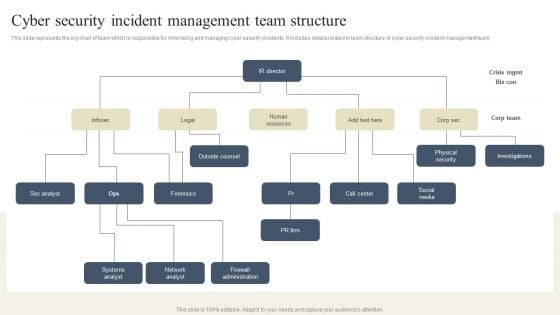
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

 Home
Home