Technology Risk
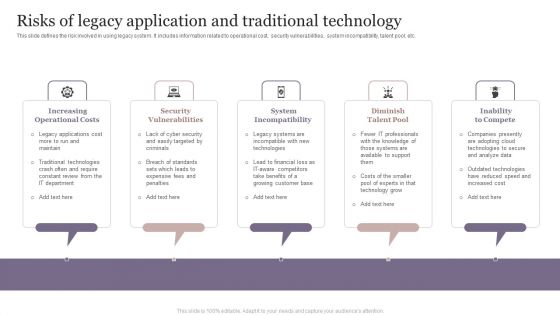
Risks Of Legacy Application And Traditional Technology Mockup PDF
This slide defines the risk involved in using legacy system. It includes information related to operational cost, security vulnerabilities, system incompatibility, talent pool, etc. Persuade your audience using this Risks Of Legacy Application And Traditional Technology Mockup PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Increasing Operational Costs, Security Vulnerabilities, System Incompatibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
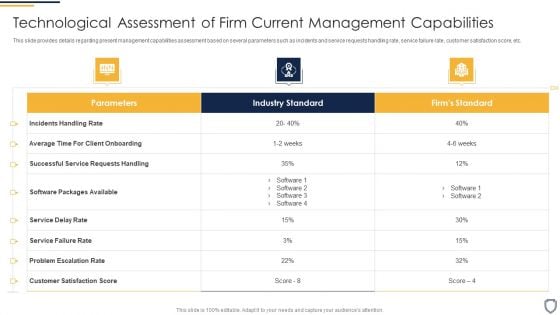
Corporate Security And Risk Management Technological Assessment Of Firm Current Designs PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management technological assessment of firm current designs pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
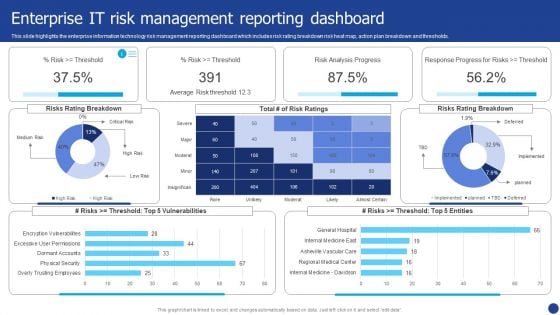
Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF bundle. Topics like Enterprise IT Risk, Management Reporting Dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Integration Of Risk Management Into Sdlc Infographics PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. This is a Information Technology Threat Mitigation Methods Integration Of Risk Management Into Sdlc Infographics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development, Implementation, Risk Management Activities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Technology Guide For Serverless Computing Business Risk Related To Cloud Computing Data Portrait PDF
This is a technology guide for serverless computing business risk related to cloud computing data portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Technology Disaster Resilience Plan Preparation Of Risk Assessment Icons PDF
This slide depicts the preparation of risk assessment, and it includes risk probability and risk severity levels such as catastrophic, hazardous, major, minor, and negligible.Deliver and pitch your topic in the best possible manner with this Information Technology Disaster Resilience Plan Preparation Of Risk Assessment Icons PDF. Use them to share invaluable insights on Extremely Improbable, Improbable, Catastrophic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ethical Technology Utilization Ethical Operating System OS Risk Mitigation Checklist Portrait Pdf
This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ethical Technology Utilization Ethical Operating System OS Risk Mitigation Checklist Portrait Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc.
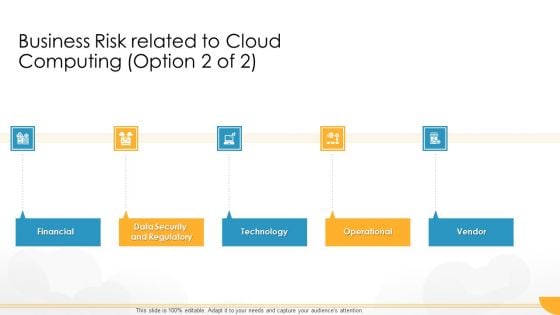
Technology Guide For Serverless Computing Business Risk Related To Cloud Computing Vendor Brochure PDF
Presenting technology guide for serverless computing business risk related to cloud computing vendor brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Technology Adoption In Banking Industry Major Risk And Their Mitigation Strategies Guidelines PDF
This slide shows the various risks credit risk, market risk, operational risk, etc.and their mitigation strategies target market, diversification, people management, etc. with their level of risks.This is a Digital Technology Adoption In Banking Industry Major Risk And Their Mitigation Strategies Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like People Management, Diversify The Investment, Credit Approval Process You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
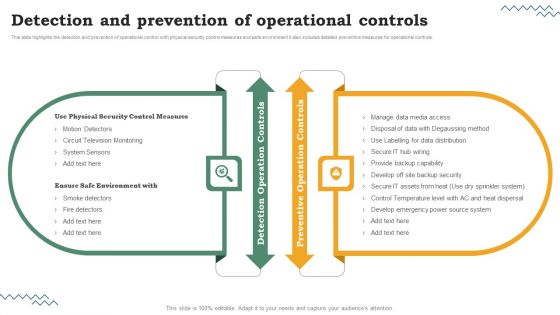
Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Get a simple yet stunning designed Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
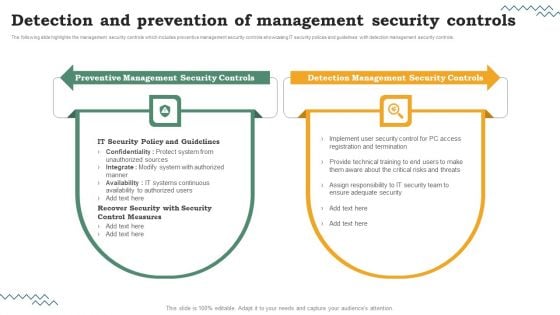
Risk Evaluation Of Information Technology Systems Detection And Prevention Of Management Security Controls Microsoft PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Risk Evaluation Of Information Technology Systems The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Detection And Prevention Of Management Security Controls Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Risk Evaluation Of Information Technology Systems Detection And Prevention Of Management Security Controls Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
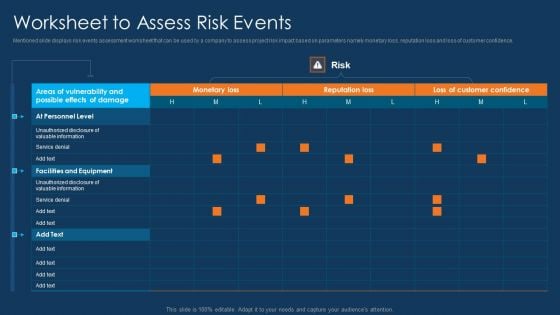
Information Technology Project Initiation Worksheet To Assess Risk Events Infographics PDF
Mentioned slide displays risk events assessment worksheet that can be used by a company to assess project risk impact based on parameters namely monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative information technology project initiation worksheet to assess risk events infographics pdf bundle. Topics like monetary loss, reputation loss, loss of customer confidence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Evaluation Of Information Technology Systems Ppt PowerPoint Presentation Complete Deck With Slides
Use this Risk Evaluation Of Information Technology Systems Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in fifty slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Table Of Contents For Risk Evaluation Of Information Technology Systems Elements PDF
Retrieve professionally designed Table Of Contents For Risk Evaluation Of Information Technology Systems Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Generating Logistics Value Business Risks Involved In Technology Implementation And Mitigation Strategies Structure PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this generating logistics value business risks involved in technology implementation and mitigation strategies structure pdf. Use them to share invaluable insights on technology risk, connectivity risk, inventory management risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Responsible Technology Playbook Ethical Operating System OS Risk Mitigation Checklist Infographics PDF
This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc. Do you know about Slidesgeeks Responsible Technology Playbook Ethical Operating System OS Risk Mitigation Checklist Infographics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
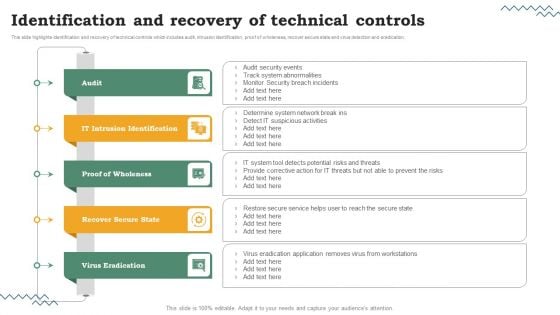
Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Strategies Create Good Proposition Risks Involved In Technology Implementation And Mitigation Demonstration PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this strategies create good proposition risks involved in technology implementation and mitigation demonstration pdf. Use them to share invaluable insights on risks involved in technology implementation and mitigation strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
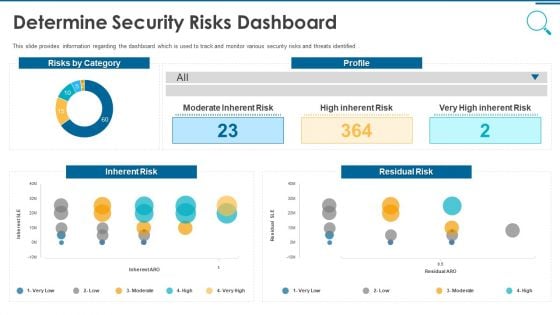
Information And Technology Security Operations Determine Security Risks Dashboard Themes PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations determine security risks dashboard themes pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
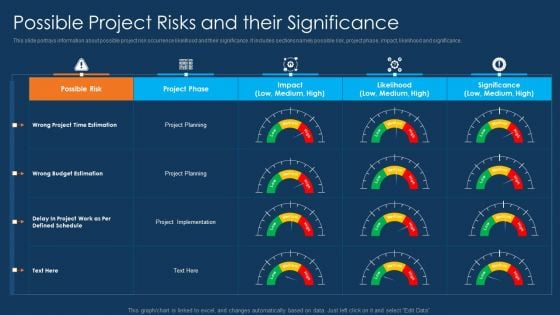
Information Technology Project Initiation Possible Project Risks And Their Significance Clipart PDF
This slide portrays information about possible project risk occurrence likelihood and their significance. It includes sections namely possible risk, project phase, impact, likelihood and significance. Deliver an awe inspiring pitch with this creative information technology project initiation possible project risks and their significance clipart pdf bundle. Topics like possible risk, project phase, project planning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
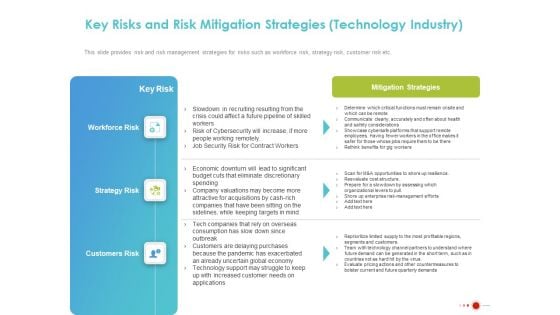
COVID 19 Mitigating Impact On High Tech Industry Key Risks And Risk Mitigation Strategies Technology Industry Professional PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry key risks and risk mitigation strategies technology industry professional pdf. The topics discussed in these slides are workforce risk, strategy risk, customers risk, mitigation strategies, technology support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
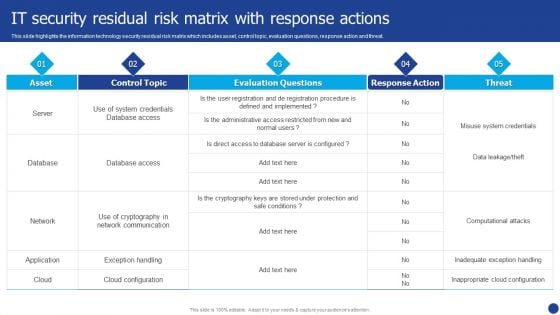
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
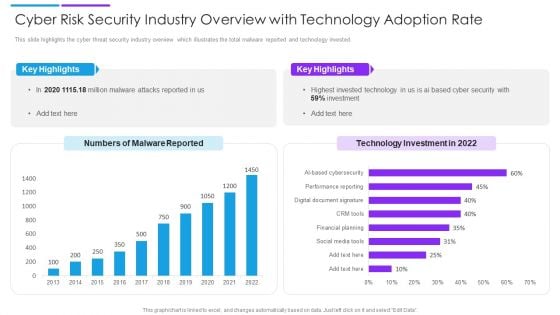
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
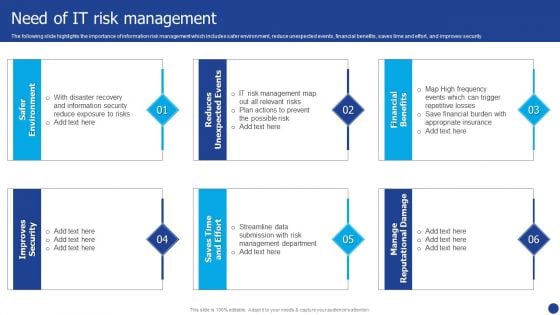
Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF
The following slide highlights the importance of information risk management which includes safer environment, reduce unexpected events, financial benefits, saves time and effort, and improves security. Presenting Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Financial Benefits, Saves Time And Effort, Improves Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
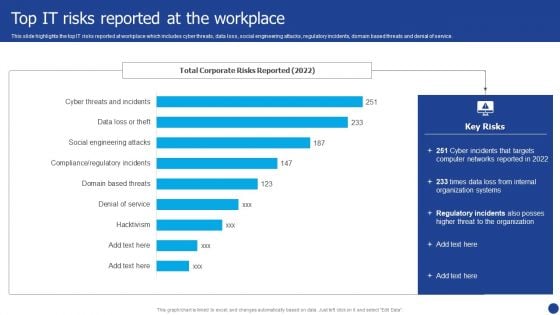
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

COVID 19 Mitigating Impact On High Tech Industry Risks And Risk Management Strategies For Technology Segment Portrait PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry risks and risk management strategies for technology segment portrait pdf. The topics discussed in these slides are hardware, software, it services, semiconductors, network equipment, grow technology capabilities, opportunities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
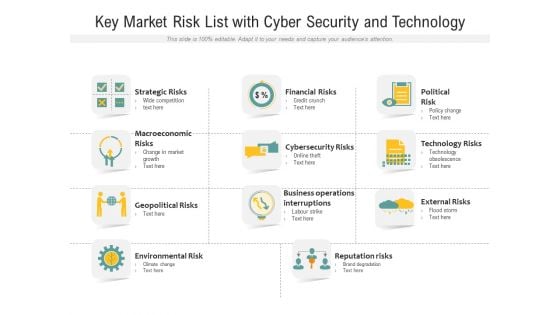
Key Market Risk List With Cyber Security And Technology Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled key market risk list with cyber security and technology ppt powerpoint presentation file show pdf. The topics addressed in these templates are strategic risks, macroeconomic, geopolitical risks, environmental risk, financial risks, cybersecurity risks, political risk, technology risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
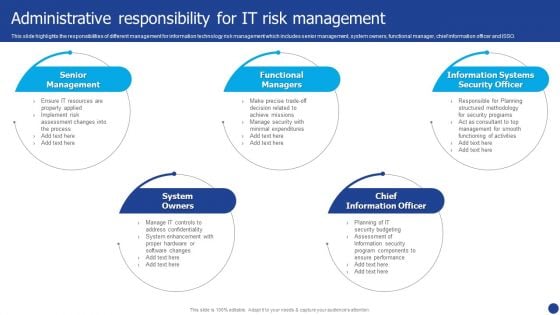
Information Technology Threat Mitigation Methods Administrative Responsibility For IT Risk Management Brochure PDF
This slide highlights the responsibilities of different management for information technology risk management which includes senior management, system owners, functional manager, chief information officer and ISSO. This is a Information Technology Threat Mitigation Methods Administrative Responsibility For IT Risk Management Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Managers, Chief Information Officer, System Owners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying EGIT To Ensure Optimum Risk Management Overview Of Information And Technology Governance Inspiration PDF
This slide represents the overview of information and technology governance that enhances the IT management in the organizations and maximizes the return on investment. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying EGIT To Ensure Optimum Risk Management Overview Of Information And Technology Governance Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ethical Operating System OS Risk Mitigation Checklist Guide For Ethical Technology Inspiration Pdf
This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Ethical Operating System OS Risk Mitigation Checklist Guide For Ethical Technology Inspiration Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc.
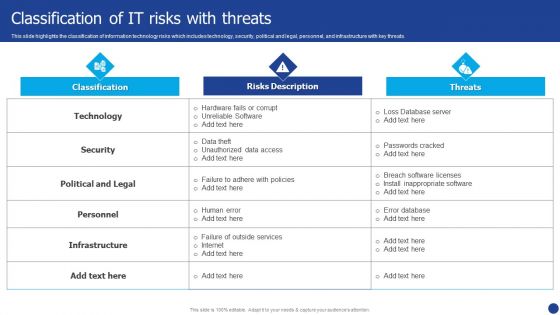
Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF bundle. Topics like Risks Description, Technology, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
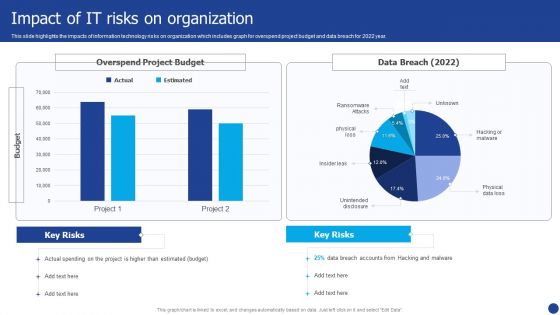
Information Technology Threat Mitigation Methods Impact Of IT Risks On Organization Rules PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2022 year. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Impact Of IT Risks On Organization Rules PDF. Use them to share invaluable insights on Impact Of IT Risks, Organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective Initiation Of Information Technology Project Mitigation Plan To Resolve Project Risks Pictures PDF
Following slide portrays mitigation plan for possibly occurring project risks. It includes sections namely perceived risk, project phase and mitigation plan. This is a effective initiation of information technology project mitigation plan to resolve project risks pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perceived risk, project phase, mitigation plan, wrong budget estimation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
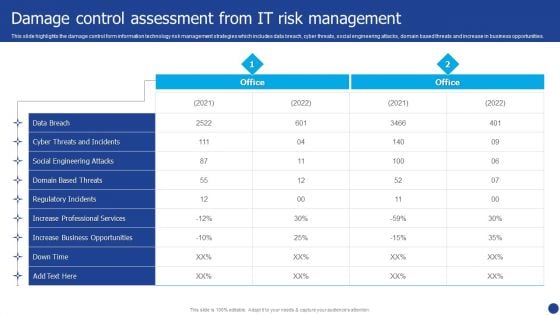
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
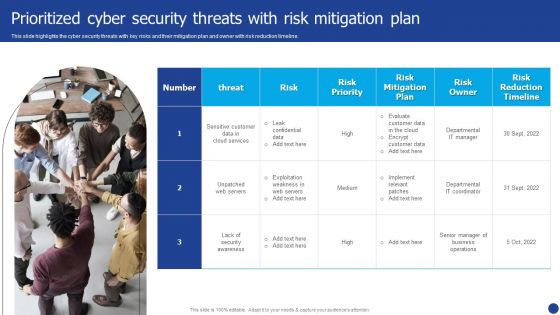
Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
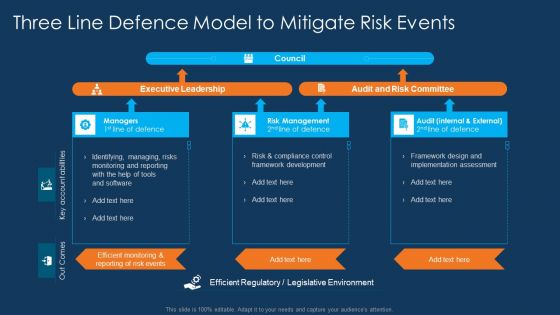
Information Technology Project Initiation Three Line Defence Model To Mitigate Risk Events Clipart PDF
This is a information technology project initiation three line defence model to mitigate risk events clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like three line defence model to mitigate risk events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
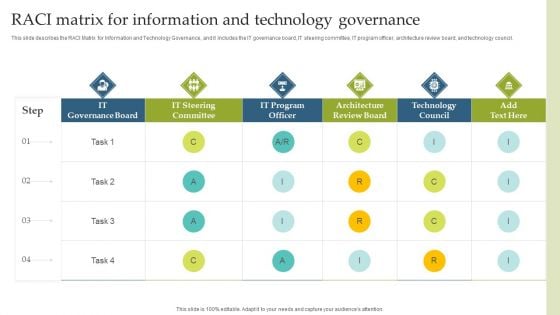
Deploying EGIT To Ensure Optimum Risk Management RACI Matrix For Information And Technology Governance Structure PDF
This slide describes the RACI Matrix for Information and Technology Governance, and it includes the IT governance board, IT steering committee, IT program officer, architecture review board, and technology council. Take your projects to the next level with our ultimate collection of Deploying EGIT To Ensure Optimum Risk Management RACI Matrix For Information And Technology Governance Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
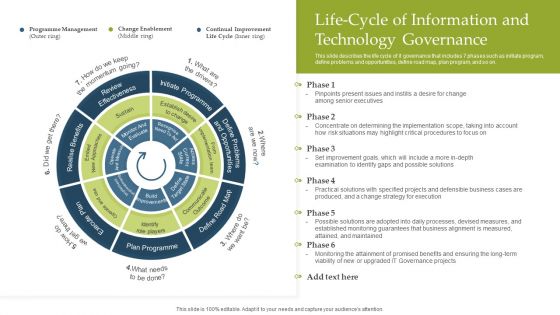
Deploying EGIT To Ensure Optimum Risk Management Life Cycle Of Information And Technology Governance Designs PDF
This slide describes the life cycle of it governance that includes 7 phases such as initiate program, define problems and opportunities, define road map, plan program, and so on. Retrieve professionally designed Deploying EGIT To Ensure Optimum Risk Management Life Cycle Of Information And Technology Governance Designs PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
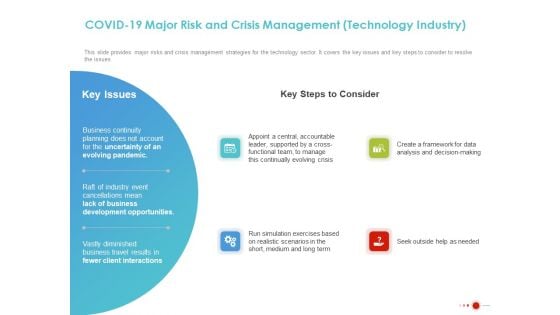
COVID 19 Mitigating Impact On High Tech Industry COVID 19 Major Risk And Crisis Management Technology Industry Demonstration PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry covid 19 major risk and crisis management technology industry demonstration pdf. The topics discussed in these slides are data analysis, decision making, run simulation exercises based, business continuity planning, business development opportunities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
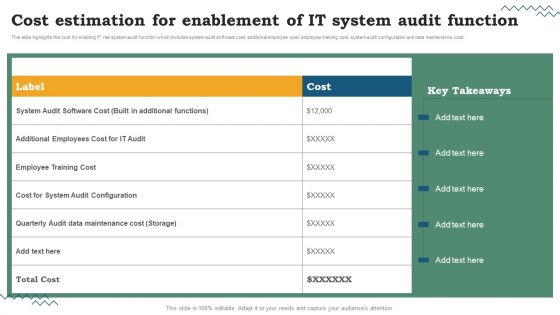
Risk Evaluation Of Information Technology Systems Cost Estimation For Enablement Of IT System Audit Function Clipart PDF
This slide highlights the cost for enabling IT risk system audit function which includes system audit software cost, additional employee cost, employee training cost, system audit configuration and data maintenance cost. Want to ace your presentation in front of a live audience. Our Risk Evaluation Of Information Technology Systems Cost Estimation For Enablement Of IT System Audit Function Clipart PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
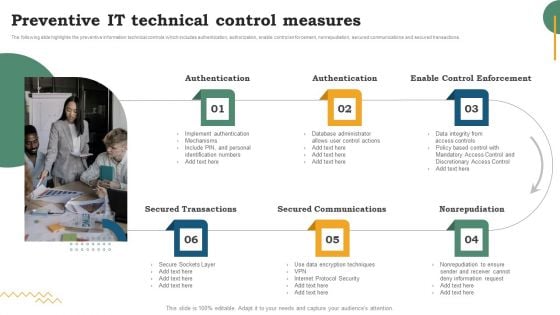
Risk Evaluation Of Information Technology Systems Software Development Life Cycle Planning Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Risk Evaluation Of Information Technology Systems Software Development Life Cycle Planning Preventive IT Technical Control Measures Information PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
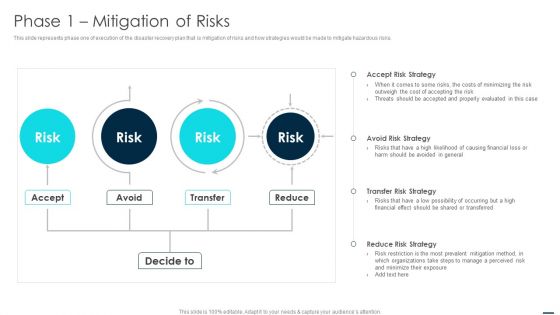
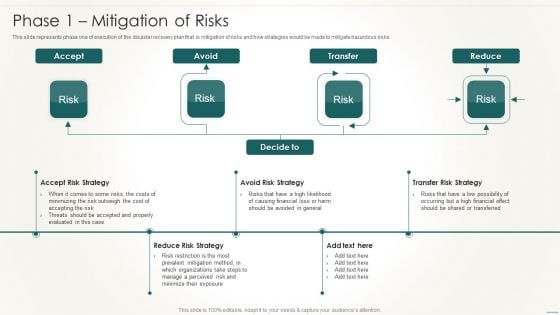
Technology Disaster Recovery Plan Phase 1 Mitigation Of Risks Structure PDF
This slide represents phase one of execution of the disaster recovery plan that is mitigation of risks and how strategies would be made to mitigate hazardous risks. This is a Technology Disaster Recovery Plan Phase 1 Mitigation Of Risks Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reduce, Transfer, Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
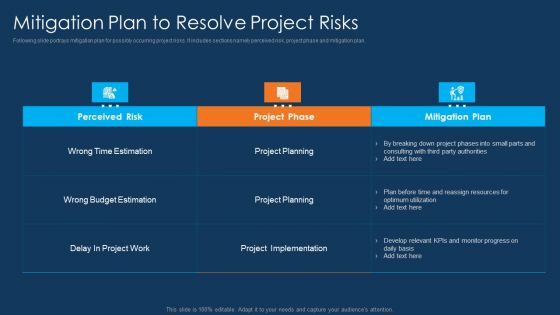
Information Technology Project Initiation Mitigation Plan To Resolve Project Risks Topics PDF
Following slide portrays mitigation plan for possibly occurring project risks. It includes sections namely perceived risk, project phase and mitigation plan. Deliver an awe inspiring pitch with this creative information technology project initiation mitigation plan to resolve project risks topics pdf bundle. Topics like perceived risk, project phase, mitigation plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Technology Disaster Resilience Plan Phase 1 Mitigation Of Risks Guidelines PDF
This slide represents phase one of execution of the disaster recovery plan that is mitigation of risks and how strategies would be made to mitigate hazardous risks. Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan Phase 1 Mitigation Of Risks Guidelines PDF bundle. Topics like Prevalent Mitigation, Manage A Perceived, Minimize Their Exposure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Various Risk Zones Associated With Ethical OS Guide For Ethical Technology Icons Pdf
This slide provides information regarding several risk zones associated with the ethical operating system OS in managing risks such as trust, disinformation and propaganda, economic and dopamine economy, hateful and criminal actors, truth, disinformation, propaganda, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Various Risk Zones Associated With Ethical OS Guide For Ethical Technology Icons Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Various Risk Zones Associated With Ethical OS Guide For Ethical Technology Icons Pdf today and make your presentation stand out from the rest. This slide provides information regarding several risk zones associated with the ethical operating system OS in managing risks such as trust, disinformation and propaganda, economic and dopamine economy, hateful and criminal actors, truth, disinformation, propaganda, etc.

Technology Disaster Recovery Plan Identification And Analysis Of Disaster Risks Topics PDF
This slide describes the risk attributes to consider while analyzing the risks, and these attributes are predictability, scope, time of day, time of the week, location impact, likelihood, and advance warning. Presenting Technology Disaster Recovery Plan Identification And Analysis Of Disaster Risks Topics PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Business Operations, Risks, Evaluation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Disaster Resilience Plan Identification And Analysis Of Disaster Risks Pictures PDF
This slide describes the risk attributes to consider while analyzing the risks, and these attributes are predictability, scope, time of day, time of the week, location impact, likelihood, and advance warning.Presenting Information Technology Disaster Resilience Plan Identification And Analysis Of Disaster Risks Pictures PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Advance Warning, Predictability, Business Operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
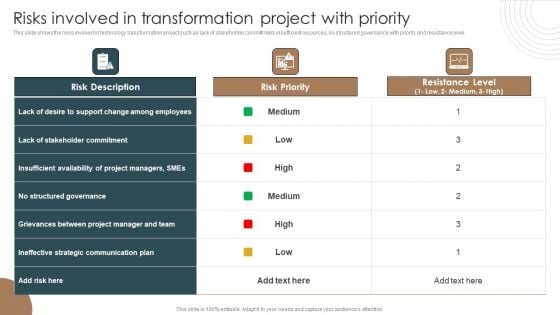
Risks Involved In Transformation Project With Priority Integrating Technology To Transform Change Clipart PDF
This slide shows the risks involved in technology transformation project such as lack of stakeholder commitment, insufficient resources, no structured governance with priority and resistance level.This Risks Involved In Transformation Project With Priority Integrating Technology To Transform Change Clipart PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
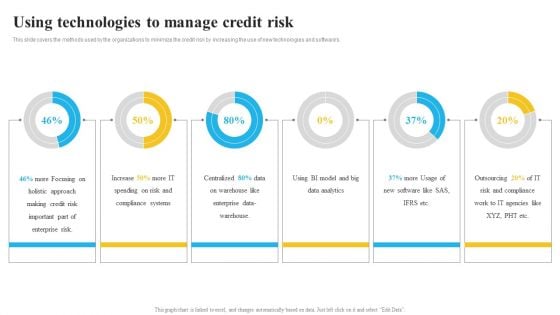
Bank And Finance Risk Management Tools And Methodologies Using Technologies Ideas PDF
This slide covers the methods used by the organizations to minimize the credit risk by increasing the use of new technologies and softwares. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Bank And Finance Risk Management Tools And Methodologies Using Technologies Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Bank And Finance Risk Management Tools And Methodologies Using Technologies Ideas PDF

Risk Management For Organization Essential Assets Technological Assessment Of Firm Current Pictures PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets technological assessment of firm current pictures pdf bundle. Topics like parameters, industry standard, firms standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
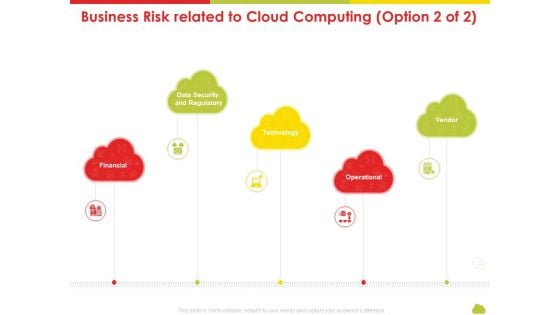
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Vendor Designs PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing vendor designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Data Diagrams PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
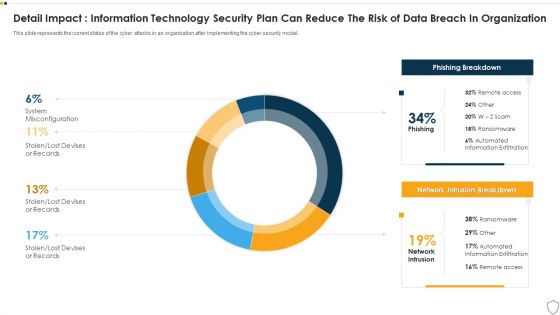
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Construction Sector Project Risk Management Specific Safety Training For Green Technologies Practices Or Products Summary PDF
This slide covers the Firms Providing Specific Safety Training for Green Technologies, Processes and Products. Deliver and pitch your topic in the best possible manner with this construction sector project risk management specific safety training for green technologies practices or products summary pdf. Use them to share invaluable insights on modularization, technology, businesses, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
COVID 19 Risk Analysis And Mitigation Policies For Information And Communications Technology Sector Icons Slide Brochure PDF
Introducing our well designed covid 19 risk analysis and mitigation policies for information and communications technology sector icons slide brochure pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

COVID 19 Risk Analysis And Mitigation Policies For Information And Communications Technology Sector Ppt Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy four slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

 Home
Home