Technology Security
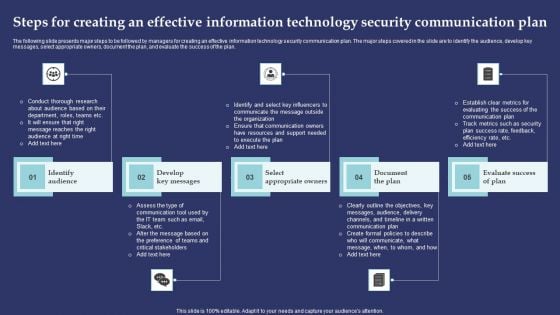
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m

Table Of Contents For Information Technology Security Ppt File Mockup PDF
Presenting table of contents for information technology security ppt file mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security implementation, managing it security, it security budget, it security roadmap timeline . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
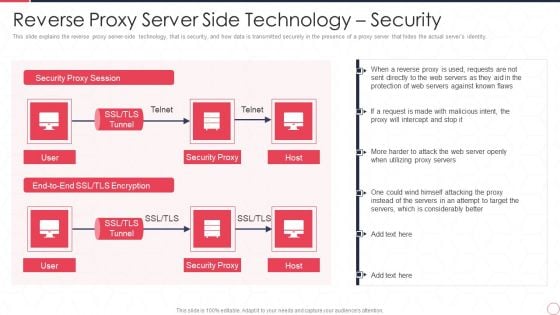
Reverse Proxy Server IT Reverse Proxy Server Side Technology Security Ppt Professional Backgrounds PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. This is a reverse proxy server it reverse proxy server side technology security ppt professional backgrounds pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security proxy session, security proxy, host. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Is Information Technology Security And How Does It Work Ppt Portfolio Sample PDF
This is a what is information technology security and how does it work ppt portfolio sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it risk assessment, it risk identification, key elements it security, steps mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF
Introducing our well designed Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
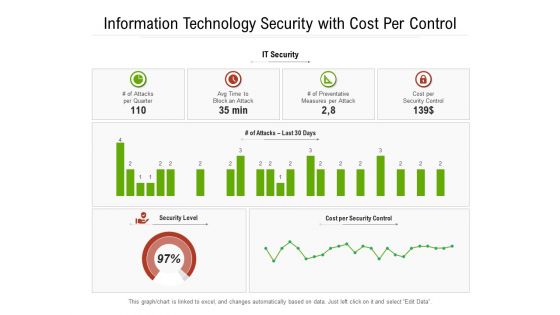
Information Technology Security With Cost Per Control Ppt PowerPoint Presentation Gallery Maker PDF
Presenting this set of slides with name information technology security with cost per control ppt powerpoint presentation gallery maker pdf. The topics discussed in these slides are cost, quarter, measures. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
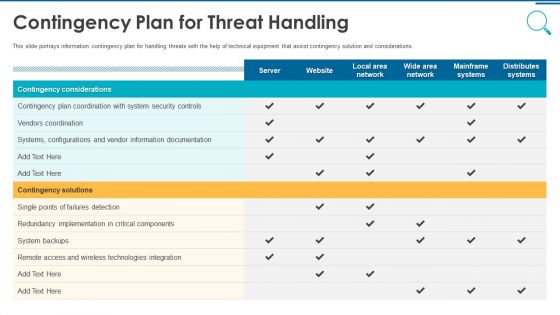
Information And Technology Security Operations Contingency Plan For Threat Handling Clipart PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative information and technology security operations contingency plan for threat handling clipart pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
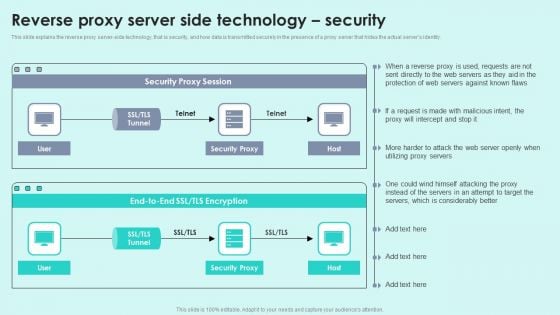
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
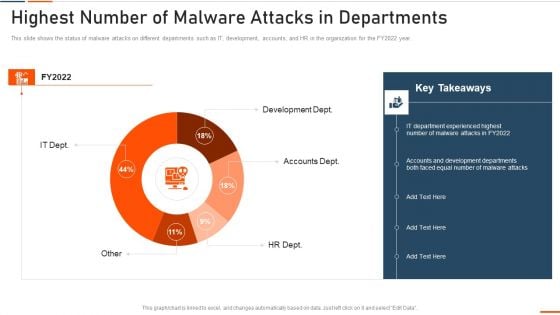
Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
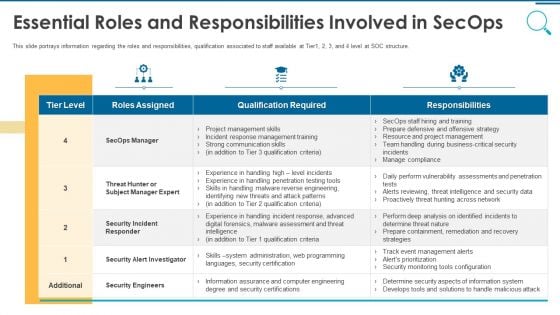
Information And Technology Security Operations Essential Roles And Responsibilities Involved In Secops Topics PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this information and technology security operations essential roles and responsibilities involved in secops topics pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
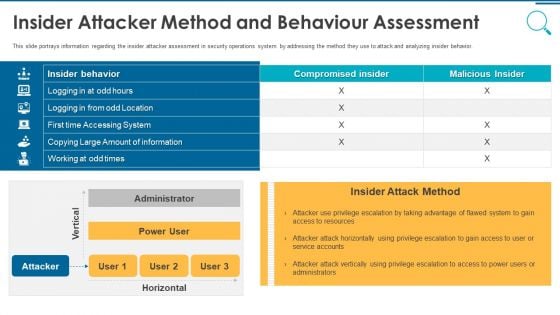
Information And Technology Security Operations Insider Attacker Method And Behaviour Assessment Inspiration PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this information and technology security operations insider attacker method and behaviour assessment inspiration pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
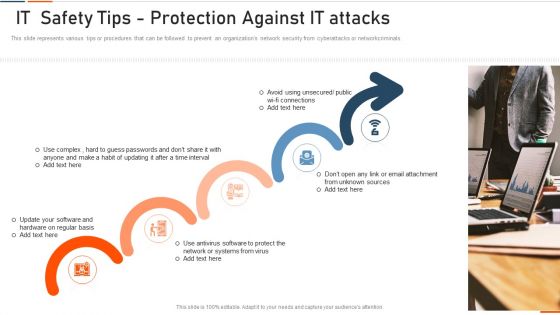
Information Technology Security IT Safety Tips Protection Against IT Attacks Ppt Layouts Outfit PDF
This slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. This is a information technology security it safety tips protection against it attacks ppt layouts outfit pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, antivirus, systems, sources, unsecured. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
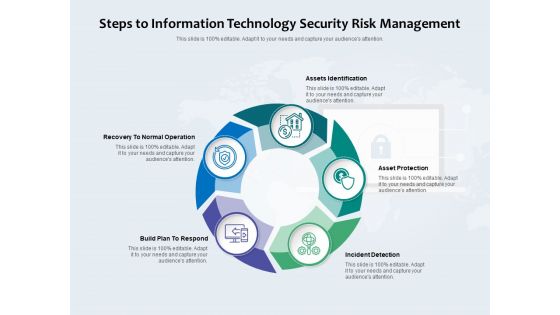
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Design PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this information technology security prepare and deploy strong it policies ppt icon graphics design pdf. Use them to share invaluable insights on v and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
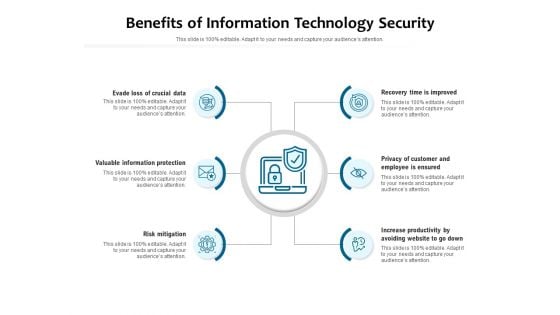
Benefits Of Information Technology Security Ppt PowerPoint Presentation Layouts Layouts PDF
Presenting benefits of information technology security ppt powerpoint presentation layouts layouts pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including evade loss of crucial data, valuable information protection, risk mitigation, recovery time is improved, privacy of customer and employee is ensured, increase productivity by avoiding website to go down. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
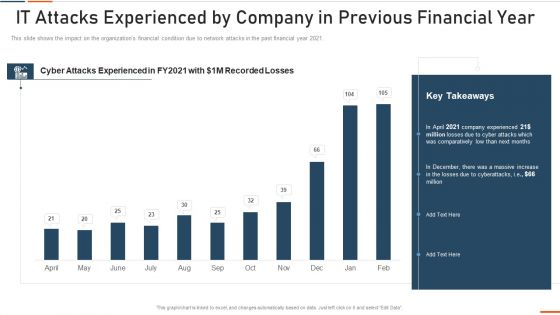
Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
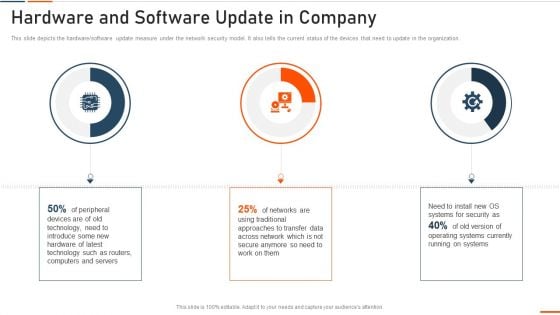
Information Technology Security Hardware And Software Update In Company Ppt Infographic Template Outfit PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Deliver an awe inspiring pitch with this creative information technology security hardware and software update in company ppt infographic template outfit pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
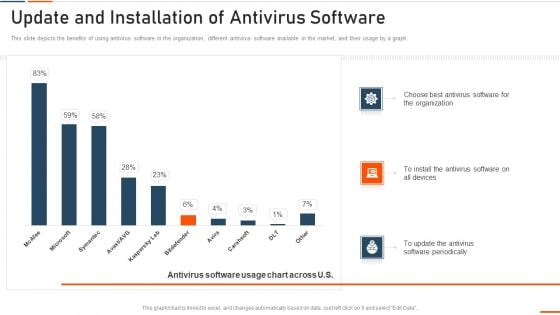
Information Technology Security Update And Installation Of Antivirus Software Ppt Professional Example File PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this information technology security update and installation of antivirus software ppt professional example file pdf. Use them to share invaluable insights on update and installation of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
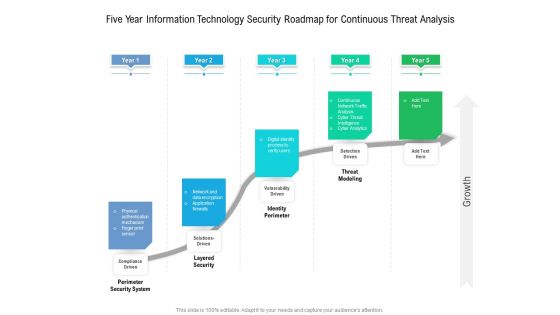
Five Year Information Technology Security Roadmap For Continuous Threat Analysis Summary
Presenting our innovatively structured five year information technology security roadmap for continuous threat analysis summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Information And Technology Security Operations Timeframe For Incident Management Graphics PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting information and technology security operations timeframe for incident management graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
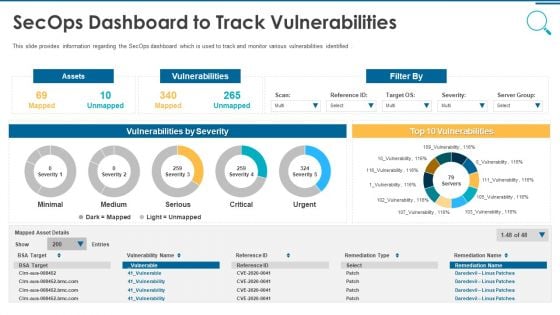
Information And Technology Security Operations Secops Dashboard To Track Vulnerabilities Information PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations secops dashboard to track vulnerabilities information pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security Problems Faced By The Organization Ppt Ideas Visuals PDF
This slide shows the organizations current situation through the total losses ins millionsexperienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative information technology security problems faced by the organization ppt ideas visuals pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
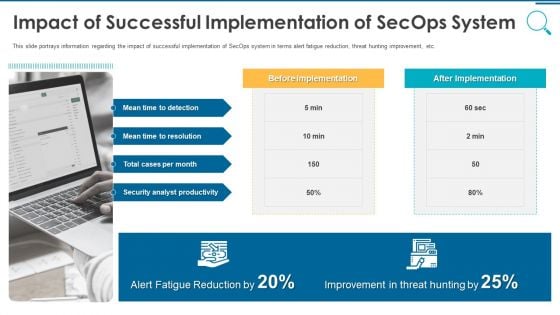
Information And Technology Security Operations Impact Of Successful Implementation Of Secops System Download PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting information and technology security operations impact of successful implementation of secops system download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
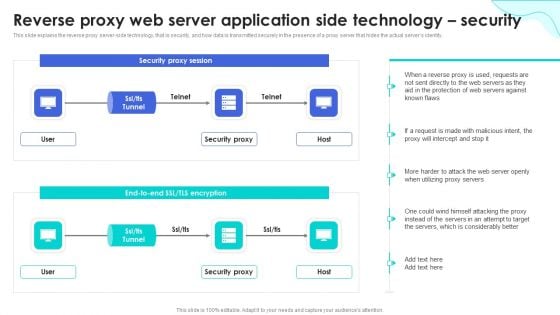
Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
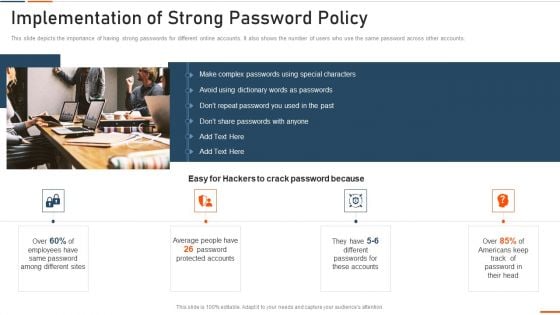
Information Technology Security Implementation Of Strong Password Policy Ppt File Infographic Template PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting information technology security implementation of strong password policy ppt file infographic template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
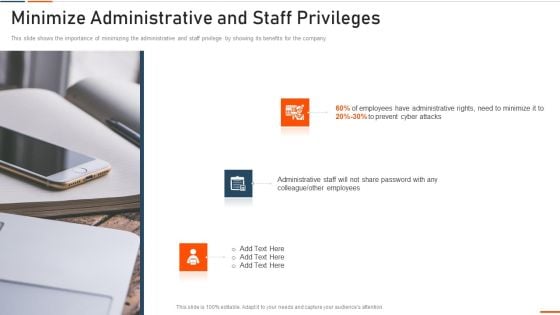
Information Technology Security Minimize Administrative And Staff Privileges Ppt Professional Graphics PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting information technology security minimize administrative and staff privileges ppt professional graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
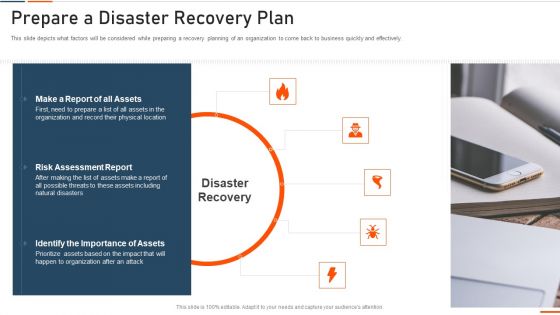
Information Technology Security Prepare A Disaster Recovery Plan Ppt Ideas Inspiration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a information technology security prepare a disaster recovery plan ppt ideas inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment report, identify importance assets, report assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF
This slide signifies the types of security provided through information technology services. It includes surveillance like network, internet, cloud and application for mitigating risk. Pitch your topic with ease and precision using this Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF. This layout presents information on Automated Workflows, Customization Option, Multi Channel Deployment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
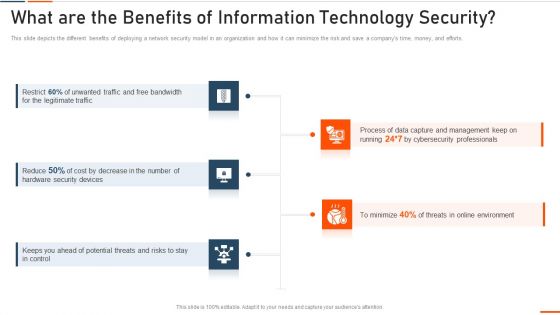
What Are The Benefits Of Information Technology Security Ppt Styles Model PDF
This slide depicts the different benefits of deploying a network security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting what are the benefits of information technology security ppt styles model pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like bandwidth, legitimate, security devices, potential . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
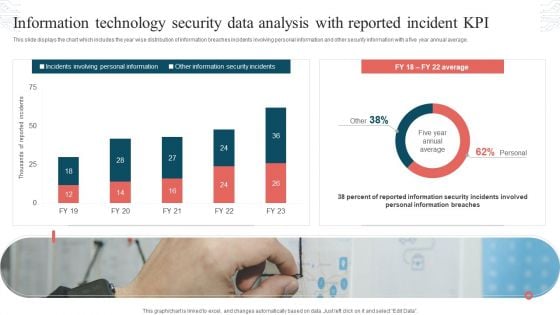
Information Technology Security Data Analysis With Reported Incident KPI Download PDF
This slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Showcasing this set of slides titled Information Technology Security Data Analysis With Reported Incident KPI Download PDF. The topics addressed in these templates are Incidents Involving, Personal Information, Other Information, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
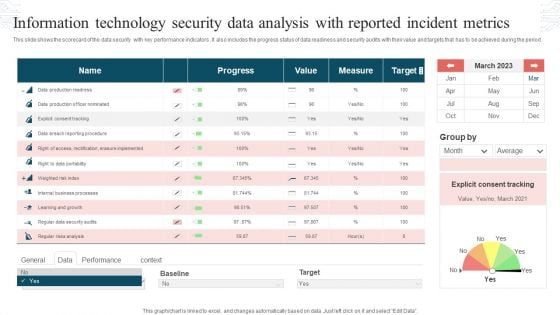
Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF
This slide shows the scorecard of the data security with key performance indicators. It also includes the progress status of data readiness and security audits with their value and targets that has to be achieved during the period. Pitch your topic with ease and precision using this Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF. This layout presents information on Progress, Value, Measure, Target. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
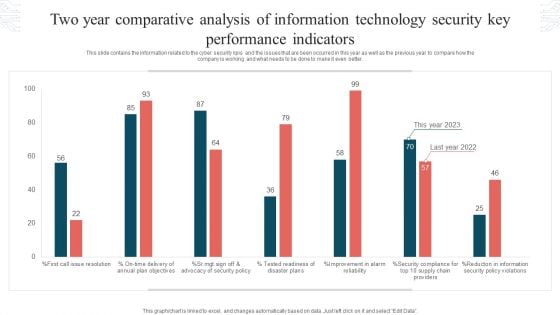
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information And Technology Security Operations How Firm Handle Insider Threats Pictures PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a information and technology security operations how firm handle insider threats pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
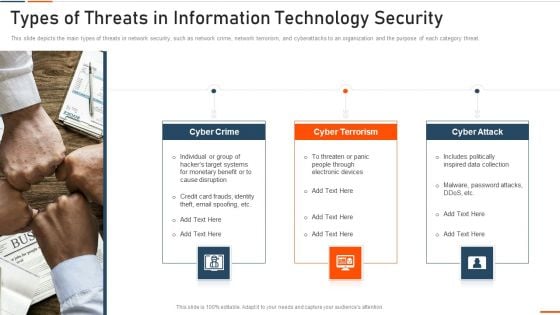
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact On Organization After Implementing Information Technology Security Ppt Infographic Template Examples PDF
This slide depicts the hardware software update measure under the network security model. It also tells the current status of the devices that need to update in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information technology security ppt infographic template examples pdf. Use them to share invaluable insights on hardware and software update in company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
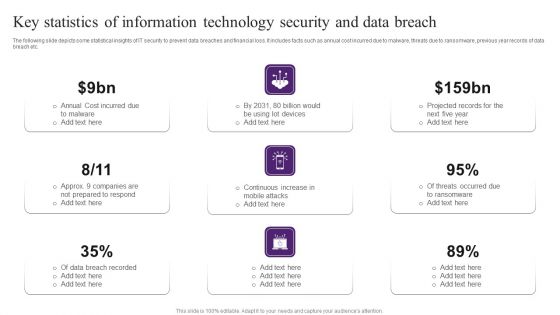
Key Statistics Of Information Technology Security And Data Breach Brochure PDF
The following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Persuade your audience using this Key Statistics Of Information Technology Security And Data Breach Brochure PDF. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including Cost Incurred, Data Breach Recorded, Projected Records. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Budget For Effective Secops System Management Slides PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this information and technology security operations budget for effective secops system management slides pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
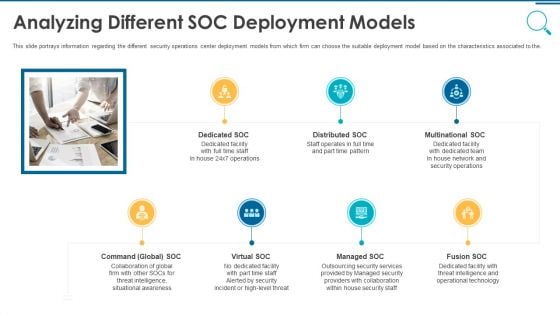
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Various Metrics To Measure Secops System Performance Mockup PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting information and technology security operations various metrics to measure secops system performance mockup pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
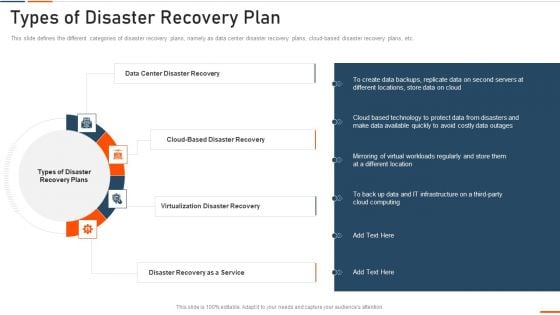
Information Technology Security Types Of Disaster Recovery Plan Ppt Show Smartart PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. Presenting information technology security types of disaster recovery plan ppt show smartart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data center disaster recovery, virtualization disaster recovery, disaster recovery as a service . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
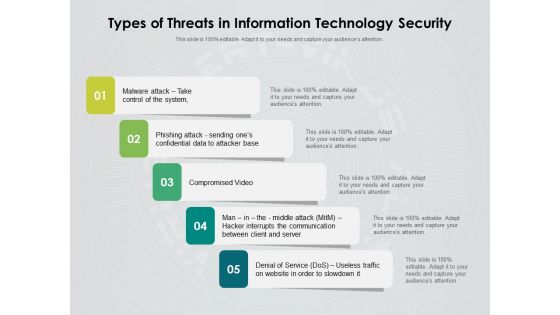
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
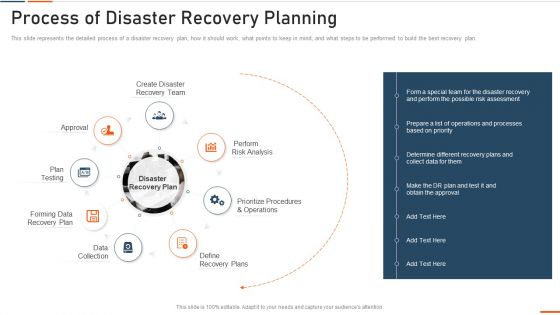
Information Technology Security Process Of Disaster Recovery Planning Ppt Portfolio Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information technology security process of disaster recovery planning ppt portfolio summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like approval, plan testing, recovery plan, data collection, perform . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
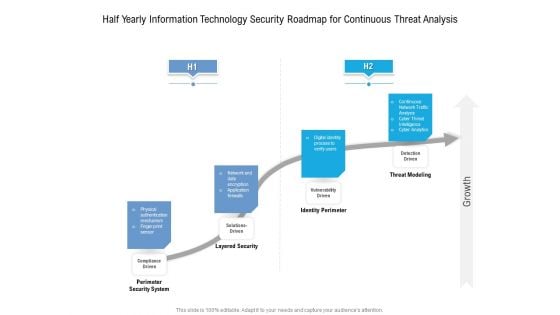
Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
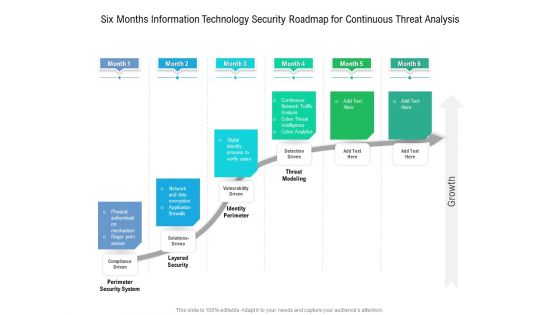
Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
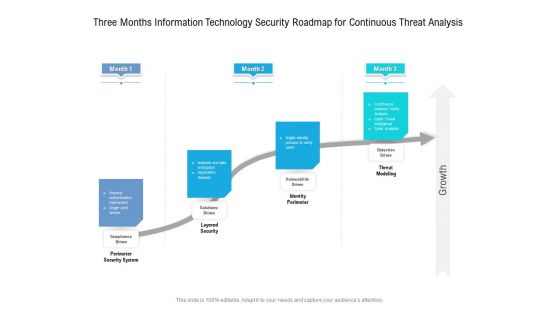
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
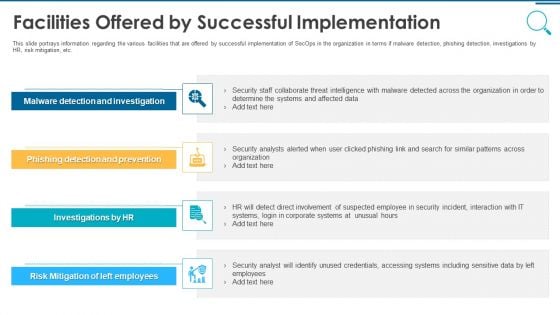
Information And Technology Security Operations Facilities Offered By Successful Implementation Guidelines PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a information and technology security operations facilities offered by successful implementation guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
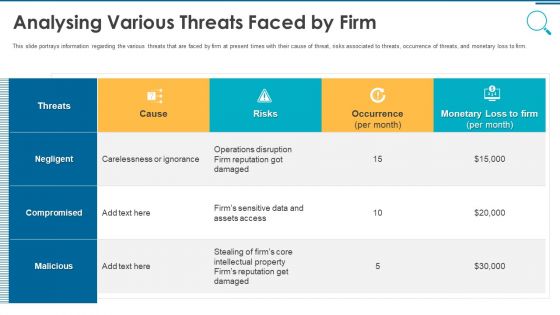
Information And Technology Security Operations Analysing Various Threats Faced By Firm Microsoft PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative information and technology security operations analysing various threats faced by firm microsoft pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
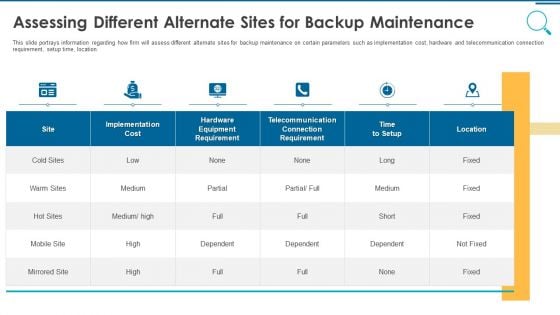
Information And Technology Security Operations Assessing Different Alternate Sites For Backup Maintenance Rules PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this information and technology security operations assessing different alternate sites for backup maintenance rules pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
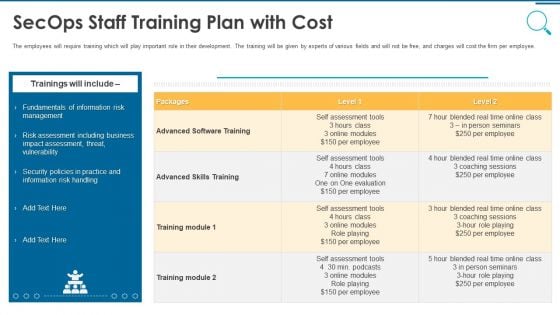
Information And Technology Security Operations Secops Staff Training Plan With Cost Introduction PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative information and technology security operations secops staff training plan with cost introduction pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
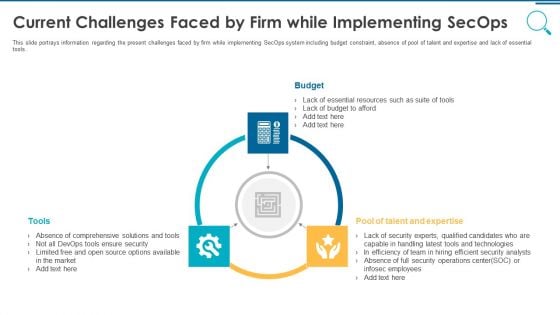
Information And Technology Security Operations Current Challenges Faced By Firm While Implementing Secops Slides PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting information and technology security operations current challenges faced by firm while implementing secops slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides
This Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
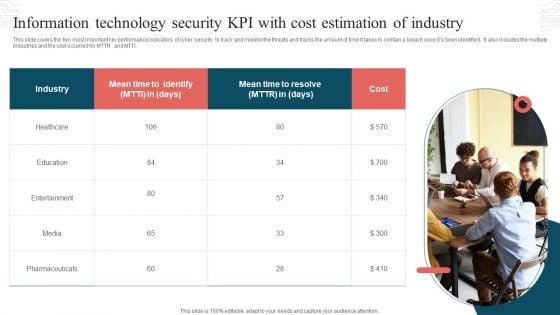
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home