Threat
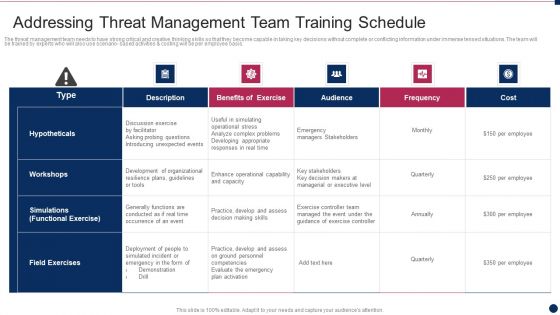
Threat Management At Workplace Addressing Threat Management Team Training Schedule Pictures Pdf
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative threat management at workplace addressing threat management team training schedule pictures pdf bundle. Topics like practice, develop and assess decision making skills, enhance operational capability and capacity, emergency managers stakeholders can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
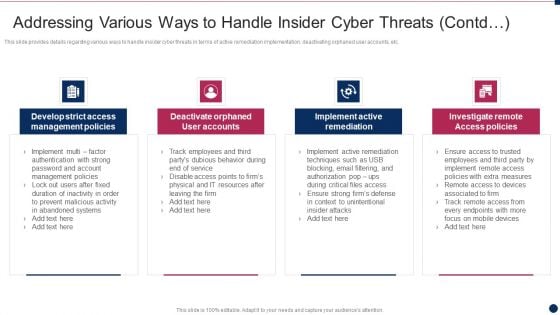
Threat Management At Workplace Addressing Various Ways To Handle Insider Cyber Threats Mockup Pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a threat management at workplace addressing various ways to handle insider cyber threats mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
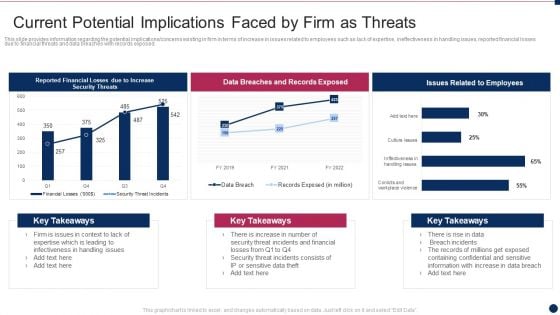
Threat Management At Workplace Current Potential Implications Faced By Firm As Threats Professional Pdf
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this threat management at workplace current potential implications faced by firm as threats professional pdf. Use them to share invaluable insights on data breaches and records exposed, breach incidents, financial losses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Different Kinds Of Insider Digital Threats Themes Pdf
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting threat management at workplace different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Threat Management At Workplace Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a threat management at workplace various types of workplace violence and threats designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harassment or intimidation, stalking, physical assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Budget For Effective Threat Ideas PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities budget for effective threat ideas pdf bundle. Topics like incident management, risk management, client onboarding process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user
Purpose Of Fraud Threat Administration Guide Fraud Threat Administration Guide Graphics PDF
This is a Purpose Of Fraud Threat Administration Guide Fraud Threat Administration Guide Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Assessment Methodologies, Tailored Address, Evolving Risk Landscape. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
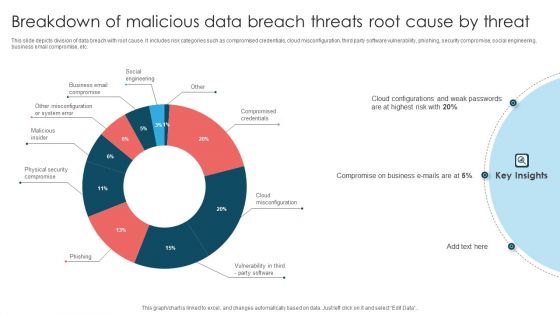
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Evaluation Icon Ppt PowerPoint Presentation Outline Graphics Tutorials
Presenting this set of slides with name threat evaluation icon ppt powerpoint presentation outline graphics tutorials. This is a three stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Secuirty Icon Ppt PowerPoint Presentation Infographic Template Design Inspiration
Presenting this set of slides with name threat secuirty icon ppt powerpoint presentation infographic template design inspiration. This is a one stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Risk Management Icon Indicating Threat Assessment Download PDF
Presenting Risk Management Icon Indicating Threat Assessment Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Management Icon Indicating, Threat Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Risk Management Icon For Threat Avoidance Information PDF
Presenting Risk Management Icon For Threat Avoidance Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Management Icon, Threat Avoidance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threat Warning Attention Symbols Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name threat warning attention symbols ppt powerpoint presentation icon portfolio pdf. This is a four stage process. The stages in this process are threat warning attention symbols. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
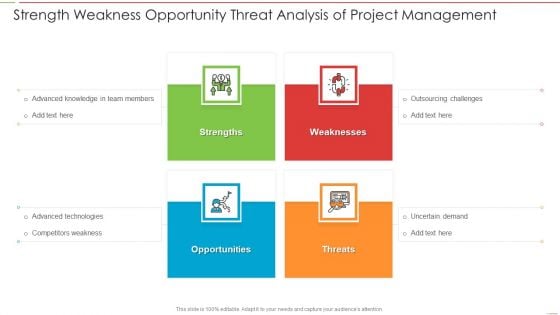
Strength Weakness Opportunity Threat Analysis Of Project Management Clipart PDF
Persuade your audience using this Strength Weakness Opportunity Threat Analysis Of Project Management Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strength, Weakness, Threats, Opportunity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
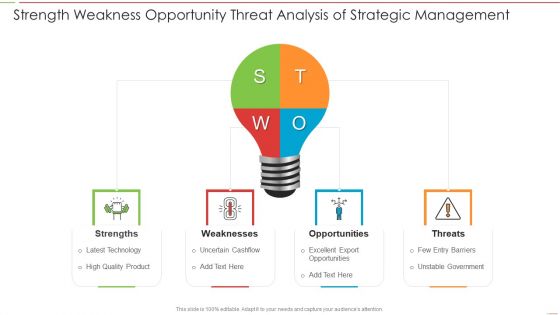
Strength Weakness Opportunity Threat Analysis Of Strategic Management Ideas PDF
Persuade your audience using this Strength Weakness Opportunity Threat Analysis Of Strategic Management Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strength, Weakness, Threats, Opportunity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
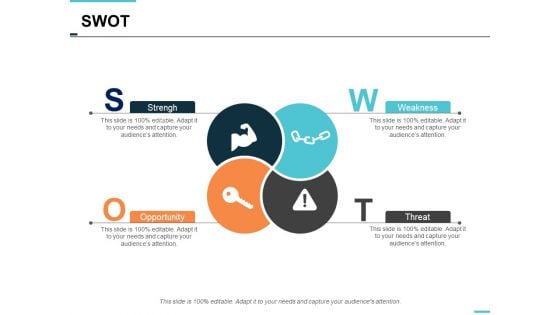
swot strength opportunity weakness threat ppt powerpoint presentation slides demonstration
This is a swot strength opportunity weakness threat ppt powerpoint presentation slides demonstration. This is a four stage process. The stages in this process are finance, marketing, management, investment, analysis.
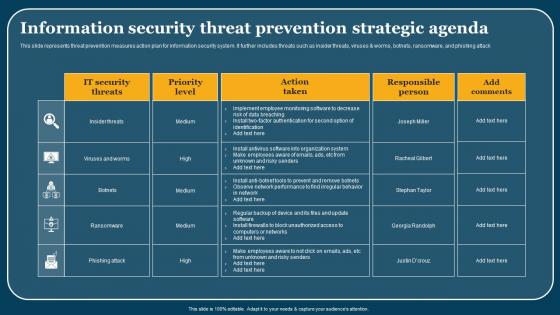
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
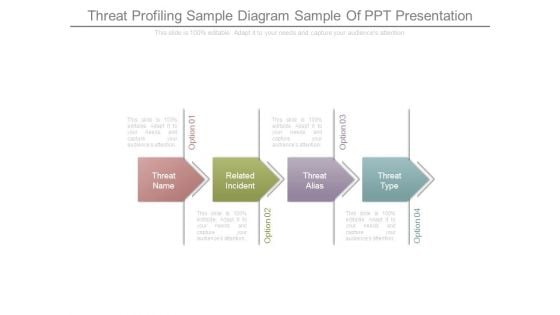
Threat Profiling Sample Diagram Sample Of Ppt Presentation
This is a threat profiling sample diagram sample of ppt presentation. This is a four stage process. The stages in this process are threat name, related incident, threat alias, threat type.
Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Determine Threat Scenario Analysis Monitoring Digital Assets Icons Pdf
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Want to ace your presentation in front of a live audience Our Determine Threat Scenario Analysis Monitoring Digital Assets Icons Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim.
Fraud Threat Evaluation And Management Icon Mockup Pdf
Pitch your topic with ease and precision using this Fraud Threat Evaluation And Management Icon Mockup Pdf This layout presents information on Fraud Threat Evaluation, Management Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Fraud Threat Evaluation And Management Icon Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
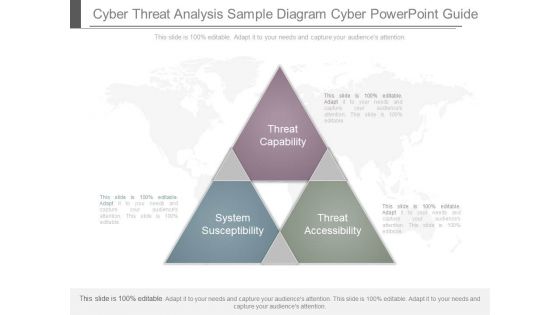
Cyber Threat Analysis Sample Diagram Cyber Powerpoint Guide
This is a cyber threat analysis sample diagram cyber powerpoint guide. This is a three stage process. The stages in this process are system susceptibility, threat capability, threat accessibility.
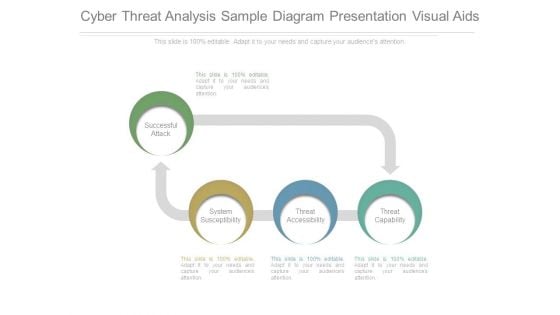
Cyber Threat Analysis Sample Diagram Presentation Visual Aids
This is a cyber threat analysis sample diagram presentation visual aids. This is a four stage process. The stages in this process are successful attack, system susceptibility, threat accessibility, threat capability.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Strategic Threat Management Ppt PowerPoint Presentation Show Graphics Download Cpb
This is a strategic threat management ppt powerpoint presentation show graphics download cpb. This is a four stage process. The stages in this process are strategic threat management.
Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf
Showcasing this set of slides titled Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf The topics addressed in these templates are Fraud Threat Evaluation, Icon Showcasing Hacker All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Incident Management Strategic Plan For Bomb Threat Slides PDF
This slide presents incident action plan for bomb threat in office premises, helpful in managing and mitigating highly hazardous threat in proper way. It includes stages such as receiving information, threat confirmation and threat mitigation. Pitch your topic with ease and precision using this Incident Management Strategic Plan For Bomb Threat Slides PDF. This layout presents information on Receive Information, Threat Identification And Confirmation, Threat Mitigation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Breach Icon To Prevent Threat Brochure Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon To Prevent Threat Brochure Pdf This layout presents information on Cyber Security Breach, Icon To Prevent Threat It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon To Prevent Threat Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Safety Incident Management Threat Management Action Plan Sample PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
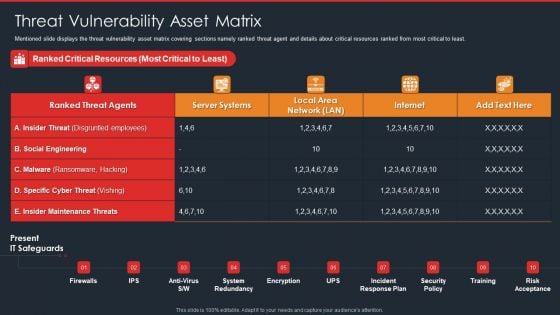
Data Safety Initiatives Threat Vulnerability Asset Matrix Themes PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this data safety initiatives threat vulnerability asset matrix themes pdf. Use them to share invaluable insights on ranked threat agents, insider threat, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
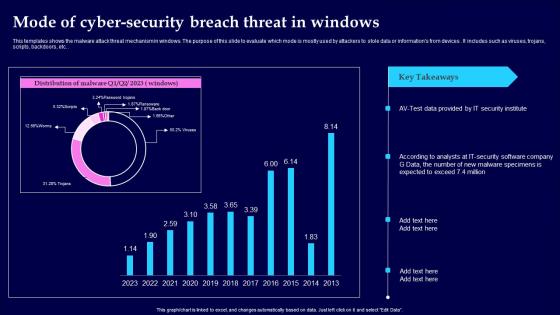
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
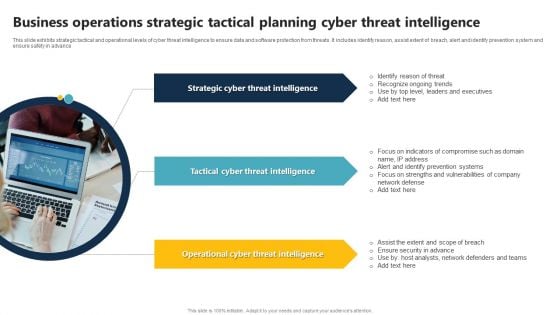
Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
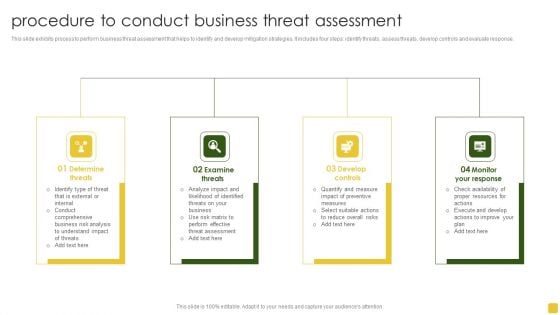
Procedure To Conduct Business Threat Assessment Topics PDF
This slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response.Presenting Procedure To Conduct Business Threat Assessment Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Threats, Examine Threats, Develop Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cert Insider Threat Reports In Powerpoint And Google Slides Cpb
Introducing our well-designed Cert Insider Threat Reports In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cert Insider Threat Reports. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cert Insider Threat Reports In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
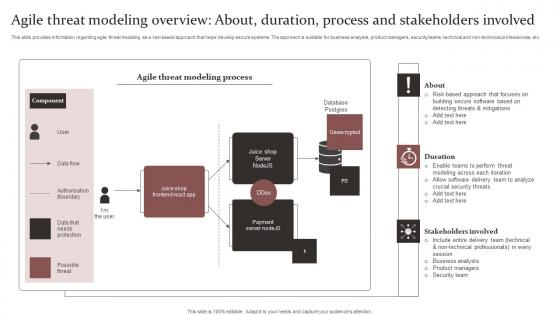
Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Create an editable Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.

Bomb Threat Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with the threat of a bomb Secure your promotion with our Bomb Threat Security PowerPoint Templates And PowerPoint Backgrounds 0211. Download without worries with our money back guaranteee.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Stereotype Threat In Powerpoint And Google Slides Cpb
Introducing our well-designed Stereotype Threat In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Stereotype Threat. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Stereotype Threat In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Building An Effective Threat Intelligence Framework Icons PDF
This slide showcases steps to create a framework for effective cyber threat intelligence that will help prevent firms from cyber threats. It includes steps such as scope definition, defines specific goals, cyber threat intelligence tools and continuous refinement. Presenting Building An Effective Threat Intelligence Framework Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Scope Definition, Define Specific Goals, Cyber Threat Intelligence Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
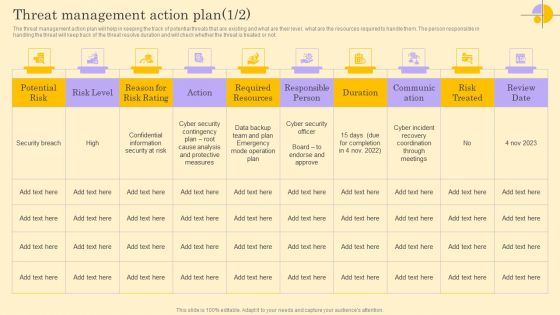
Threat Management Action Plan Ppt File Introduction PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Get a simple yet stunning designed Threat Management Action Plan Ppt File Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Management Action Plan Ppt File Introduction PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Determine Several Threat Actors Profile Monitoring Digital Assets Topics Pdf
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Determine Several Threat Actors Profile Monitoring Digital Assets Topics Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc.
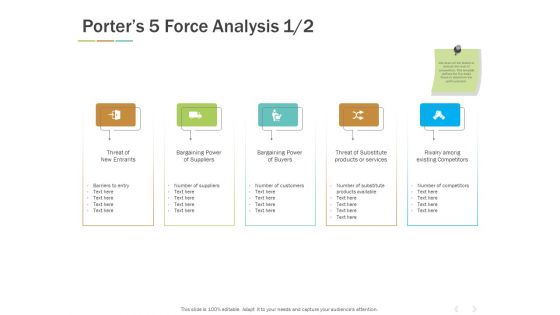
Porters 5 Force Analysis Threat Ppt PowerPoint Presentation Gallery Deck
Presenting this set of slides with name porters 5 force analysis threat ppt powerpoint presentation gallery deck. This is a five stage process. The stages in this process are threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat substitute products or services, rivalry among existing competitors. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
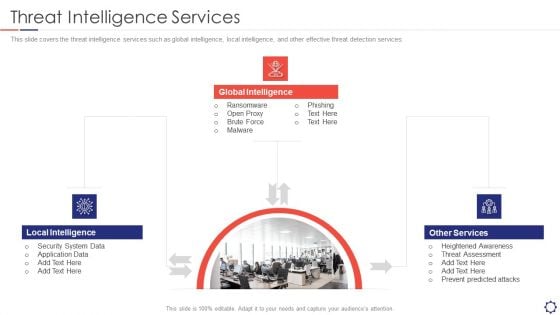
SIEM Threat Intelligence Services Ppt Layouts Background PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting siem threat intelligence services ppt layouts background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Local Intelligence, Global Intelligence, Other Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
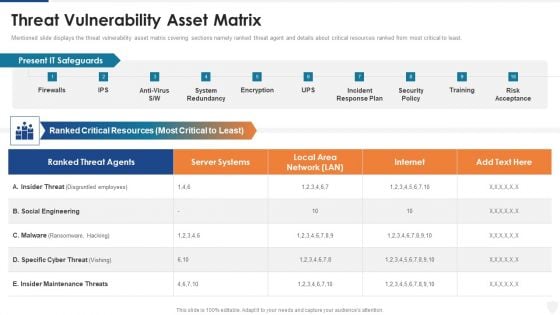
Threat Vulnerability Asset Matrix Ppt Pictures Good PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this threat vulnerability asset matrix ppt pictures good pdf. Use them to share invaluable insights on server systems, network, resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Contingency Plan For Threat Handling In Security Centre Demonstration PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative contingency plan for threat handling in security centre demonstration pdf bundle. Topics like contingency plan for threat handling in security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
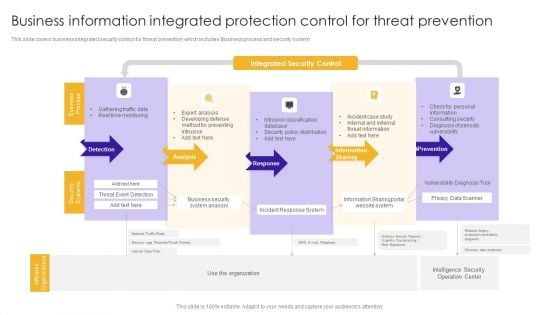
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
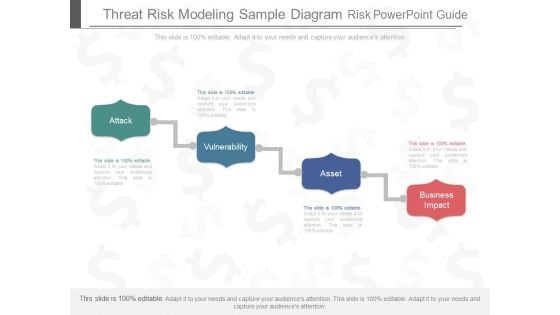
Threat Risk Modeling Sample Diagram Risk Powerpoint Guide
This is a threat risk modeling sample diagram risk powerpoint guide. This is a four stage process. The stages in this process are attack, vulnerability, asset, business impact.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
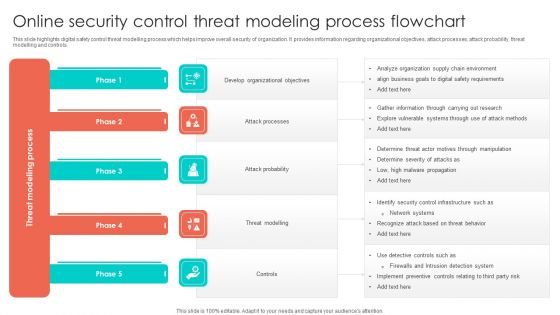
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
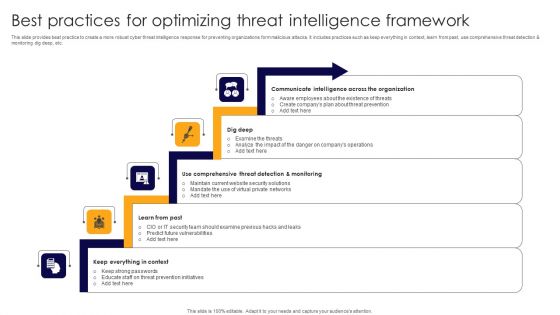
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
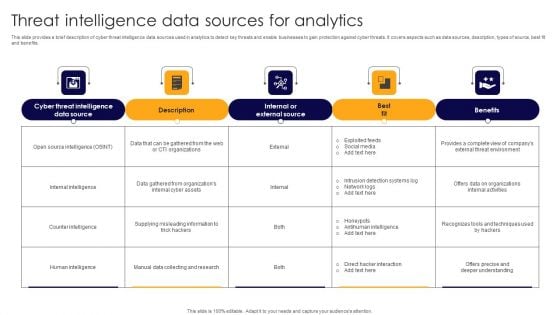
Threat Intelligence Data Sources For Analytics Ideas PDF
This slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Showcasing this set of slides titled Threat Intelligence Data Sources For Analytics Ideas PDF. The topics addressed in these templates are Exploited Feeds, Social Media, Intrusion Detection Systems Log. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
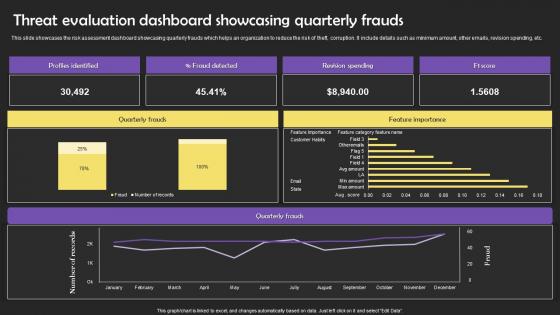
Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf
This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc. Pitch your topic with ease and precision using this Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf This layout presents information on Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc.
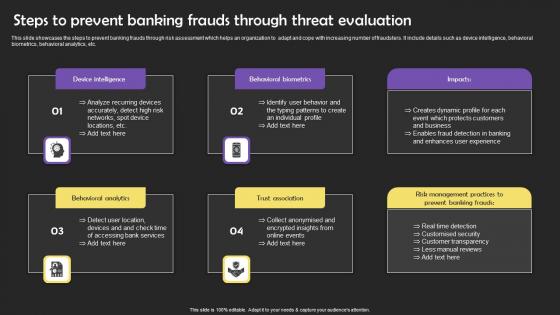
Steps To Prevent Banking Frauds Through Threat Evaluation Microsoft Pdf
This slide showcases the steps to prevent banking frauds through risk assessment which helps an organization to adapt and cope with increasing number of fraudsters. It include details such as device intelligence, behavioral biometrics, behavioral analytics, etc. Showcasing this set of slides titled Steps To Prevent Banking Frauds Through Threat Evaluation Microsoft Pdf The topics addressed in these templates are Steps To Prevent Banking Frauds Through Threat Evaluation Microsoft Pdf All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the steps to prevent banking frauds through risk assessment which helps an organization to adapt and cope with increasing number of fraudsters. It include details such as device intelligence, behavioral biometrics, behavioral analytics, etc.
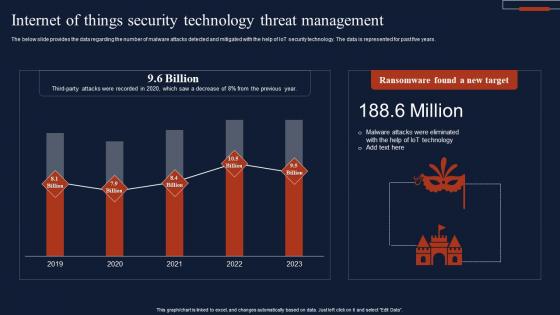
Internet Of Things Security Technology Threat Management Summary Pdf
The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Pitch your topic with ease and precision using this Internet Of Things Security Technology Threat Management Summary Pdf This layout presents information on Ransomware Found, New Target, Threat Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years.
Online Risk And Threat Identifying Icon Ideas PDF
Presenting Online Risk And Threat Identifying Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Online Risk, Threat Identifying Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Swot Strength Threat Ppt PowerPoint Presentation File Master Slide
Presenting this set of slides with name swot strength threat ppt powerpoint presentation file master slide. This is a four stage process. The stages in this process are swot, strength, weakness, opportunities, threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Swot Analysis Threat Ppt PowerPoint Presentation Infographics Guide
Presenting this set of slides with name swot analysis threat ppt powerpoint presentation infographics guide. This is a four stage process. The stages in this process are strength, opportunity, weakness, threat, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home