Threat

Elements Of Anti Fraud Threat Evaluation Program Rules Pdf
This slide showcases the elements of anti fraud risk assessment program which helps an organization to check the prevalence and seriousness of the misconduct.it include details such as risk assessment, tone from the top, training, data analytics. Showcasing this set of slides titled Elements Of Anti Fraud Threat Evaluation Program Rules Pdf The topics addressed in these templates are Risk Assessment, Training, Data Analytics All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the elements of anti fraud risk assessment program which helps an organization to check the prevalence and seriousness of the misconduct.it include details such as risk assessment, tone from the top, training, data analytics.
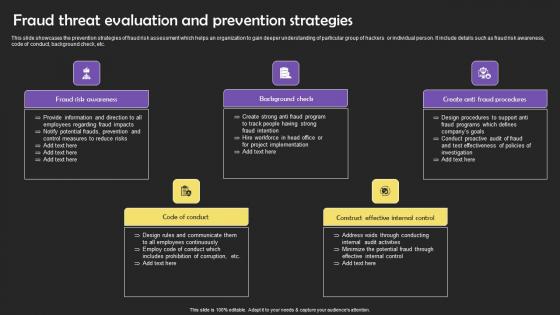
Fraud Threat Evaluation And Prevention Strategies Clipart Pdf
This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc. Showcasing this set of slides titled Fraud Threat Evaluation And Prevention Strategies Clipart Pdf The topics addressed in these templates are Fraud Risk Awareness, Background Check, Code Of Conduct All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc.
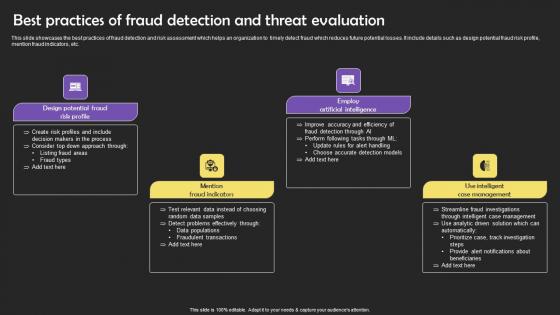
Best Practices Of Fraud Detection And Threat Evaluation Background Pdf
This slide showcases the best practices of fraud detection and risk assessment which helps an organization to timely detect fraud which reduces future potential losses. It include details such as design potential fraud risk profile, mention fraud indicators, etc. Showcasing this set of slides titled Best Practices Of Fraud Detection And Threat Evaluation Background Pdf The topics addressed in these templates are Design Potential, Mention Fraud Indicators, Artificial Intelligence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the best practices of fraud detection and risk assessment which helps an organization to timely detect fraud which reduces future potential losses. It include details such as design potential fraud risk profile, mention fraud indicators, etc.
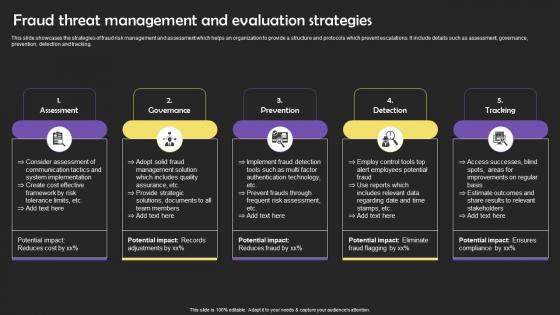
Fraud Threat Management And Evaluation Strategies Portrait Pdf
This slide showcases the strategies of fraud risk management and assessment which helps an organization to provide a structure and protocols which prevent escalations. It include details such as assessment, governance, prevention, detection and tracking. Pitch your topic with ease and precision using this Fraud Threat Management And Evaluation Strategies Portrait Pdf This layout presents information on Assessment, Governance, Prevention, Detection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the strategies of fraud risk management and assessment which helps an organization to provide a structure and protocols which prevent escalations. It include details such as assessment, governance, prevention, detection and tracking.

Key Components Of Fraud Threat Evaluation Information Pdf
This slide showcases the key elements of fraud risk assessment which helps an organization to understand their vulnerabilities to deploy countermeasures. It include details such as regulatory compliance, financial and non financial reporting, asset misuse, banned activities. Showcasing this set of slides titled Key Components Of Fraud Threat Evaluation Information Pdf The topics addressed in these templates are Regulatory Compliance, Asset Misuse, Banned Activities All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the key elements of fraud risk assessment which helps an organization to understand their vulnerabilities to deploy countermeasures. It include details such as regulatory compliance, financial and non financial reporting, asset misuse, banned activities.

KPIS Of Fraud Threat Evaluation And Prevention Formats Pdf
This slide showcases the metrics of fraud risk assessment and prevention which helps an organization to maximize legitimate transactions and ensures better business decisions. It include details such as final approval rate, precision, recall, decline rate, etc. Pitch your topic with ease and precision using this KPIS Of Fraud Threat Evaluation And Prevention Formats Pdf This layout presents information on Final Approval Rate, Optimal Performance, Decline Rate It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the metrics of fraud risk assessment and prevention which helps an organization to maximize legitimate transactions and ensures better business decisions. It include details such as final approval rate, precision, recall, decline rate, etc.
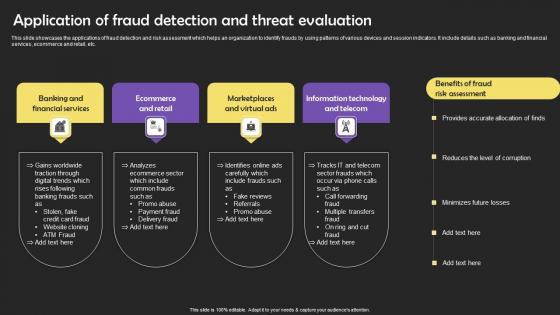
Application Of Fraud Detection And Threat Evaluation Professional Pdf
This slide showcases the applications of fraud detection and risk assessment which helps an organization to identify frauds by using patterns of various devices and session indicators. It include details such as banking and financial services, ecommerce and retail, etc. Pitch your topic with ease and precision using this Application Of Fraud Detection And Threat Evaluation Professional Pdf This layout presents information on Financial Services, Ecommerce And Retail, Information Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the applications of fraud detection and risk assessment which helps an organization to identify frauds by using patterns of various devices and session indicators. It include details such as banking and financial services, ecommerce and retail, etc.
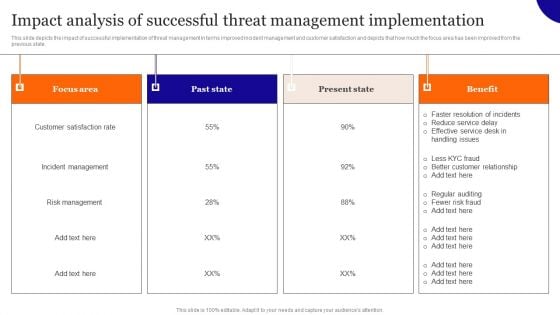
Impact Analysis Of Successful Threat Management Implementation Background PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Analysis Of Successful Threat Management Implementation Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Analysis Of Successful Threat Management Implementation Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
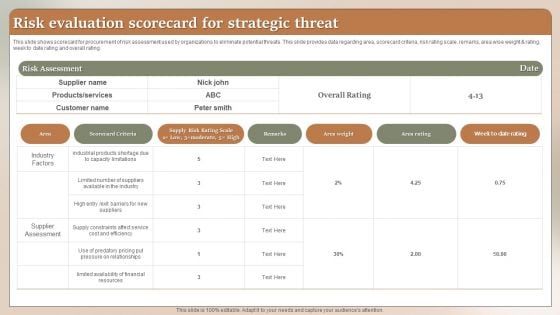
Risk Evaluation Scorecard For Strategic Threat Ppt Summary Gridlines PDF
This slide shows scorecard for procurement of risk assessment used by organizations to eliminate potential threats. This slide provides data regarding area, scorecard criteria, risk rating scale, remarks, area wise weight and rating, week to date rating and overall rating. Showcasing this set of slides titled Risk Evaluation Scorecard For Strategic Threat Ppt Summary Gridlines PDF. The topics addressed in these templates are Risk Assessment, Scorecard Criteria, Area weight. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
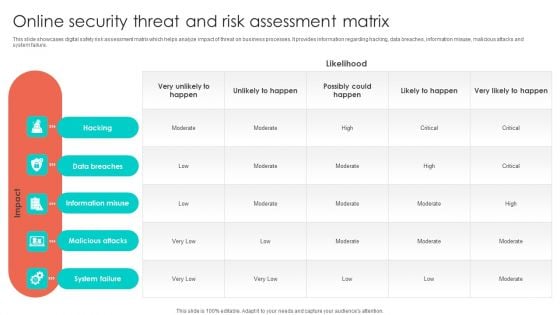
Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
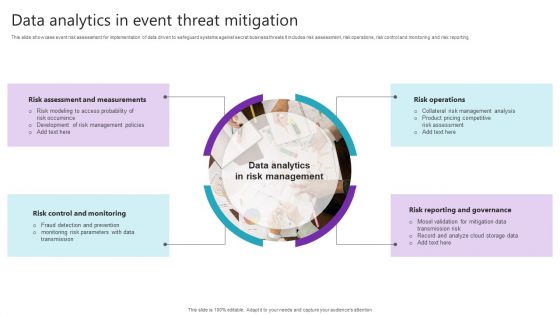
Data Analytics In Event Threat Mitigation Inspiration PDF
This slide showcase event risk assessment for implementation of data driven to safeguard systems against secret business threats It includes risk assessment, risk operations, risk control and monitoring and risk reporting. Persuade your audience using this Data Analytics In Event Threat Mitigation Inspiration PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment And Measurements, Risk Operations, Risk Control Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
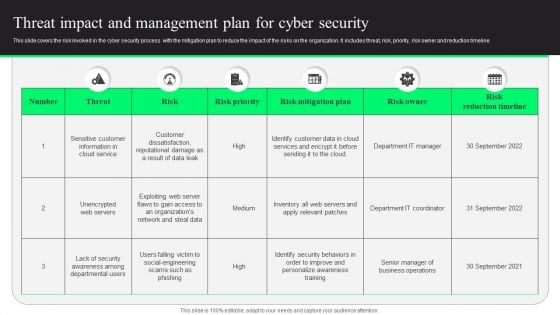
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
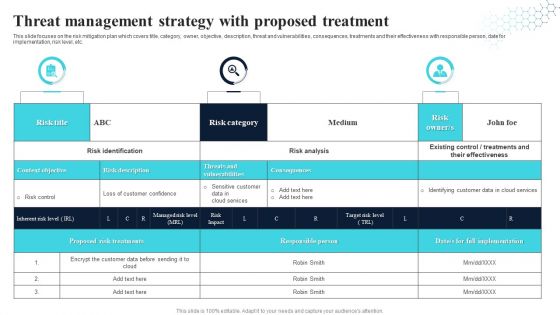
Threat Management Strategy With Proposed Treatment Structure PDF
This slide focuses on the risk mitigation plan which covers title, category, owner, objective, description, threat and vulnerabilities, consequences, treatments and their effectiveness with responsible person, date for implementation, risk level, etc. Showcasing this set of slides titled Threat Management Strategy With Proposed Treatment Structure PDF. The topics addressed in these templates are Risk Title, Risk Category, Risk Owner. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
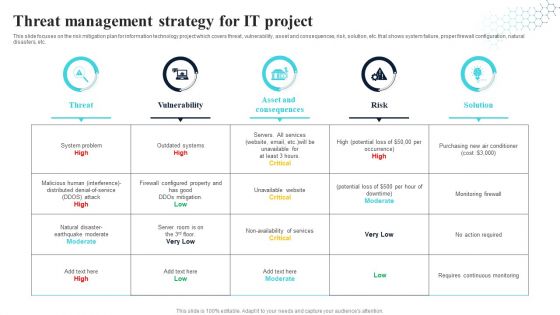
Threat Management Strategy For It Project Themes PDF
This slide focuses on the risk mitigation plan for information technology project which covers threat, vulnerability, asset and consequences, risk, solution, etc. that shows system failure, proper firewall configuration, natural disasters, etc. Pitch your topic with ease and precision using this Threat Management Strategy For It Project Themes PDF. This layout presents information on Vulnerability, Asset And Consequences, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
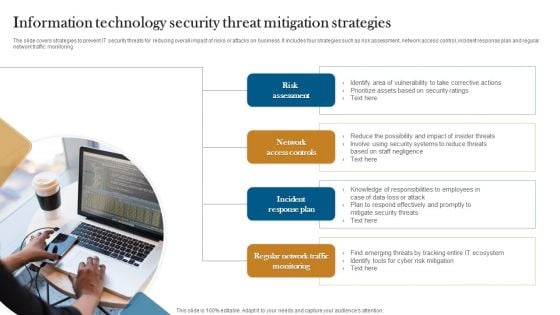
Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
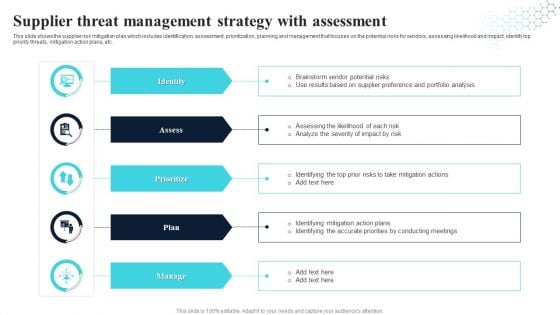
Supplier Threat Management Strategy With Assessment Infographics PDF
This slide shows the supplier risk mitigation plan which includes identification, assessment, prioritization, planning and management that focuses on the potential risks for vendors, assessing likelihood and impact, identify top priority threats, mitigation action plans, etc. Presenting Supplier Threat Management Strategy With Assessment Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prioritize, Identify, Assess, Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
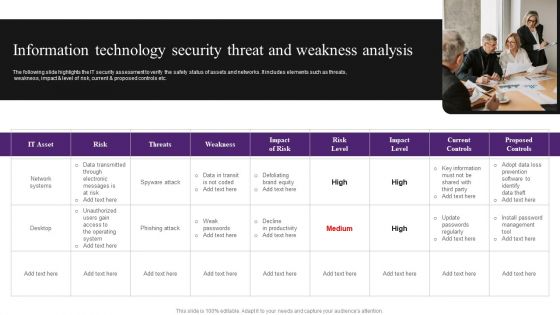
Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF
This slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Want to ace your presentation in front of a live audience Our Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
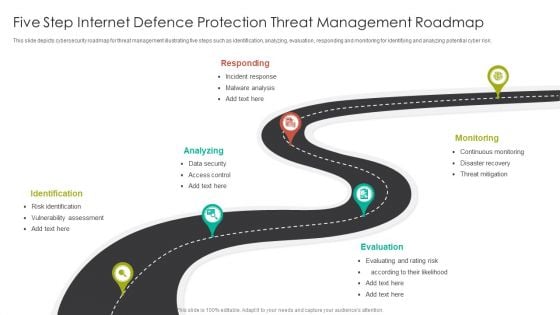
Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF
This slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk.Persuade your audience using this Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Analyzing, Responding. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
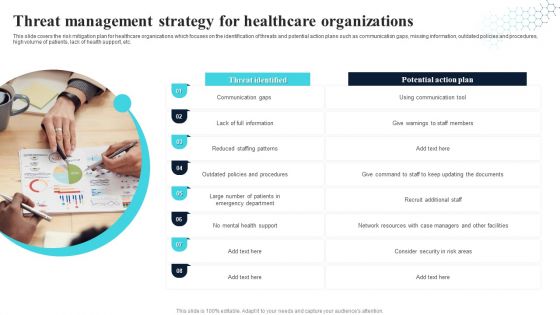
Threat Management Strategy For Healthcare Organizations Introduction PDF
This slide covers the risk mitigation plan for healthcare organizations which focuses on the identification of threats and potential action plans such as communication gaps, missing information, outdated policies and procedures, high volume of patients, lack of health support, etc. Persuade your audience using this Threat Management Strategy For Healthcare Organizations Introduction PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Communication Gaps, Recruit Additional Staff. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
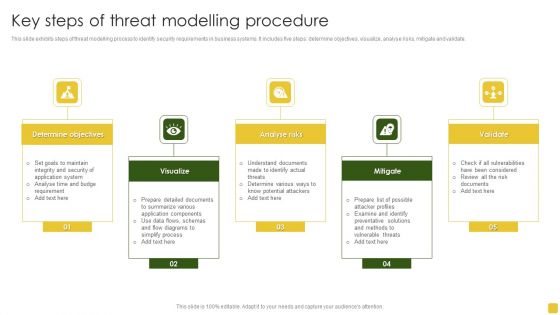
Key Steps Of Threat Modelling Procedure Brochure PDF
This slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate.Persuade your audience using this Key Steps Of Threat Modelling Procedure Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Objectives, Preventative Solutions, Determine Various Ways. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
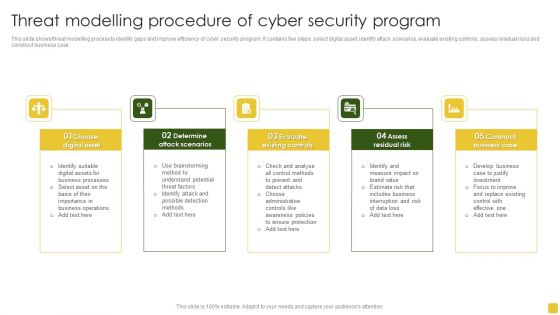
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
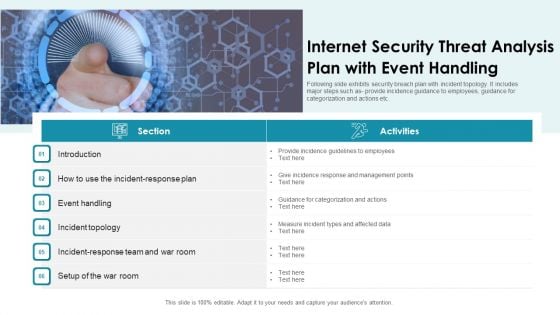
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
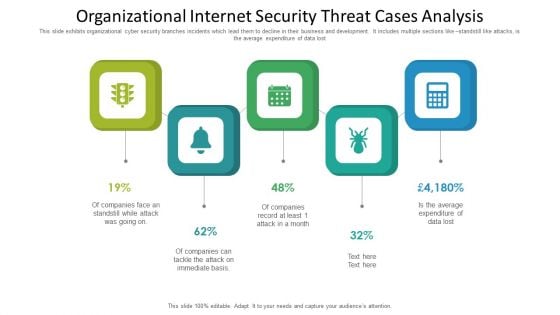
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
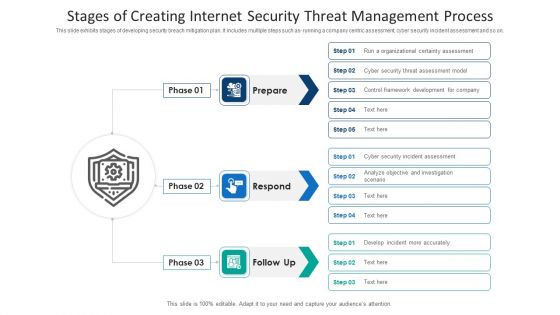
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
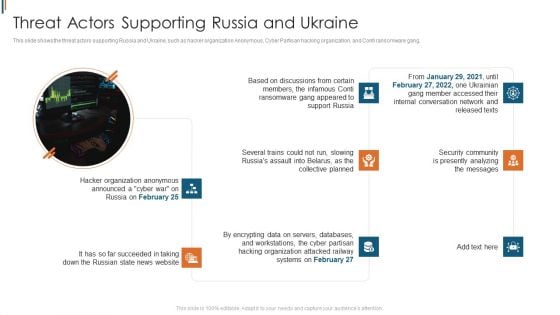
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
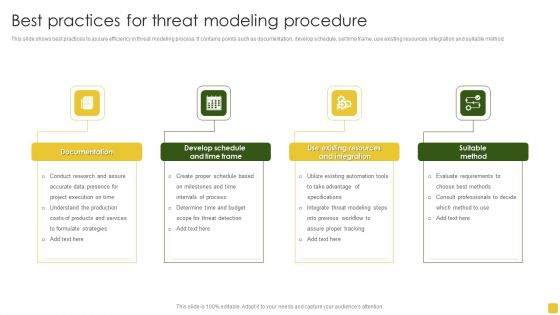
Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
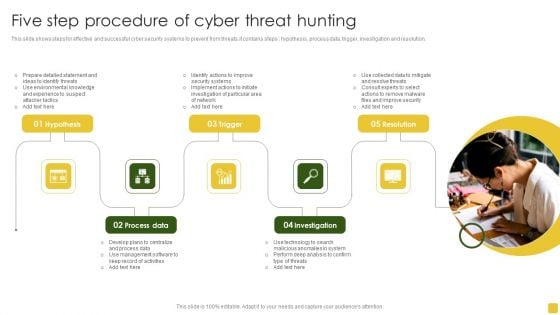
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
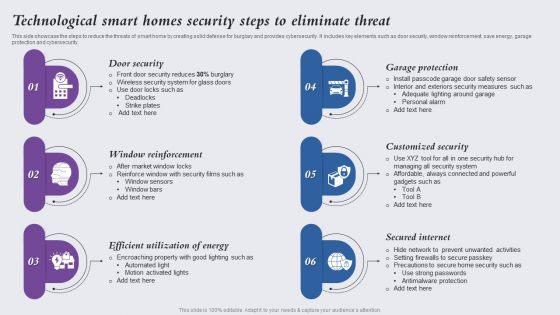
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
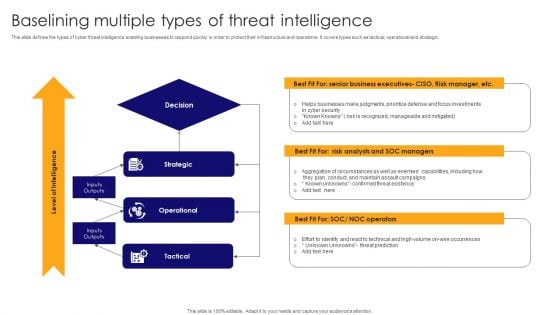
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
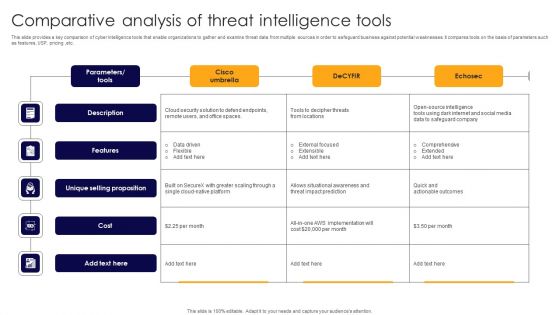
Comparative Analysis Of Threat Intelligence Tools Rules PDF
This slide provides a key comparison of cyber intelligence tools that enable organizations to gather and examine threat data from multiple sources in order to safeguard business against potential weaknesses. It compares tools on the basis of parameters such as features, USP, pricing ,etc. Showcasing this set of slides titled Comparative Analysis Of Threat Intelligence Tools Rules PDF. The topics addressed in these templates are Description, Features, Unique Selling Proposition. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
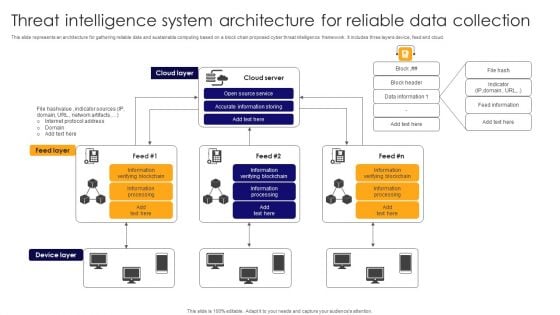
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Assessment Icon Ppt PowerPoint Presentation Show Tips
Presenting this set of slides with name threat assessment icon ppt powerpoint presentation show tips. This is a one stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business People With Threat Icon Ppt PowerPoint Presentation Show Gallery
Presenting this set of slides with name business people with threat icon ppt powerpoint presentation show gallery. This is a one stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
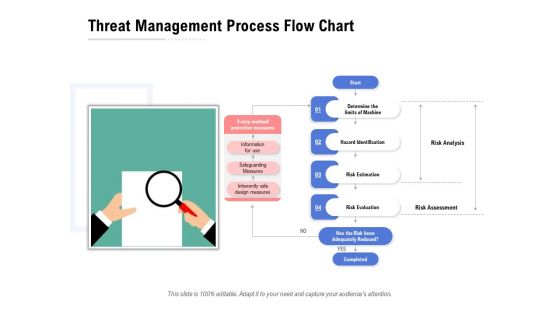
Threat Management Process Flow Chart Ppt PowerPoint Presentation Inspiration Structure
Presenting this set of slides with name threat management process flow chart ppt powerpoint presentation inspiration structure. This is a four stage process. The stages in this process are hazard identification, risk estimation, risk evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
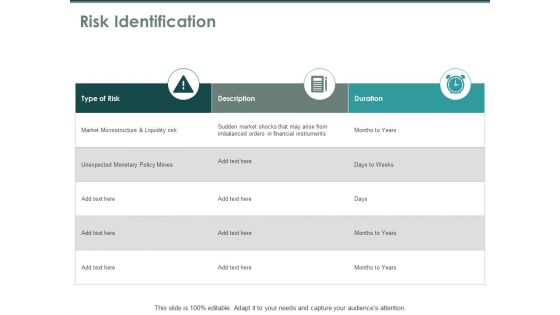
Risk Identification Threat Ppt PowerPoint Presentation Model Show
Presenting this set of slides with name risk identification threat ppt powerpoint presentation model show. The topics discussed in these slides are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Administration Bundle Business Risk Management Audit Checklist Infographics PDF
Deliver an awe inspiring pitch with this creative threat administration bundle business risk management audit checklist infographics pdf bundle. Topics like location, communication, strategies, implemented, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Event Threat Mitigation In ECR Project Clipart PDF
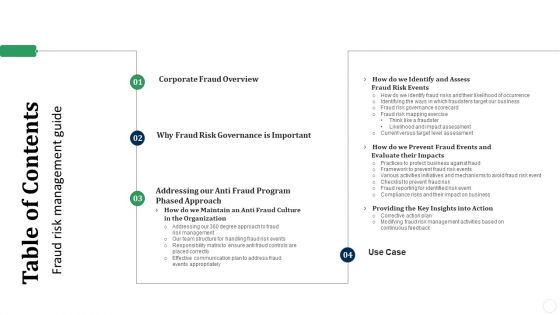
Table Of Contents Fraud Threat Administration Guide Pictures PDF
Deliver an awe inspiring pitch with this creative Table Of Contents Fraud Threat Administration Guide Pictures PDF bundle. Topics like Corporate Fraud, Risk Governance, Prevent Fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Steps Of Threat Management Process Ppt Show Inspiration PDF
Presenting this set of slides with name four steps of threat management process ppt show inspiration pdf. This is a four stage process. The stages in this process are prevention, mitigation, preparedness, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Analysis Process Planning Management Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name threat analysis process planning management ppt powerpoint presentation complete deck. The topics discussed in these slides are process, planning, management, evaluation, organization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
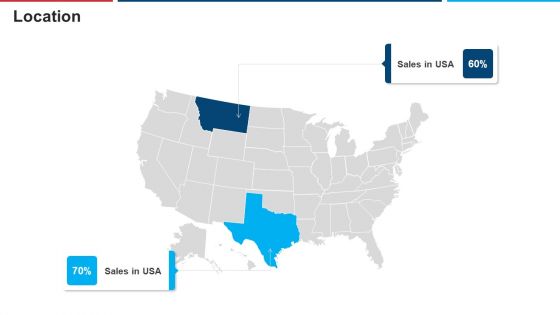
Mitigation Strategies For Operational Threat Location Ppt Portfolio Introduction PDF
This is a mitigation strategies for operational threat location ppt portfolio introduction pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
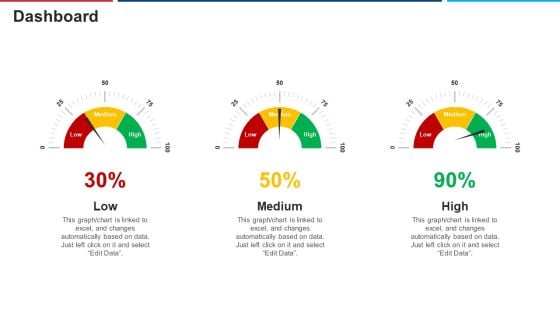
Mitigation Strategies For Operational Threat Dashboard Ppt Layouts Topics PDF
Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat dashboard ppt layouts topics pdf bundle. Topics like dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Threat Administration Bundle Guidelines PDF
Introducing our well designed icons slide for threat administration bundle guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Threat Administration Bundle Table Of Contents Microsoft PDF
Presenting threat administration bundle table of contents microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like business, organization, management, communication, action plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Threat Management At Workplace Elements Pdf
Introducing our well designed icons slide for threat management at workplace elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slides For Fraud Threat Administration Guide Pictures PDF
Introducing our well designed Icons Slides For Fraud Threat Administration Guide Pictures PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
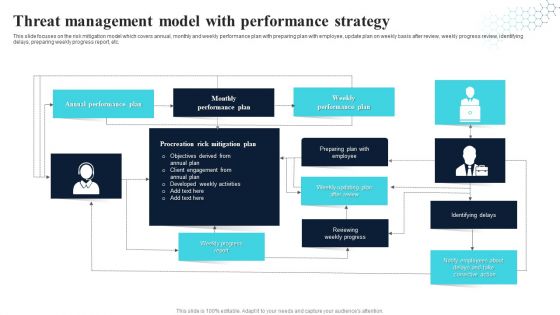
Threat Management Model With Performance Strategy Topics PDF
Showcasing this set of slides titled Threat Management Model With Performance Strategy Topics PDF. The topics addressed in these templates are Monthly Performance Plan, Weekly Performance Plan, Annual Performance Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Information Technology Threat Mitigation Methods Icons PDF
Presenting our innovatively structured Icons Slide For Information Technology Threat Mitigation Methods Icons PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
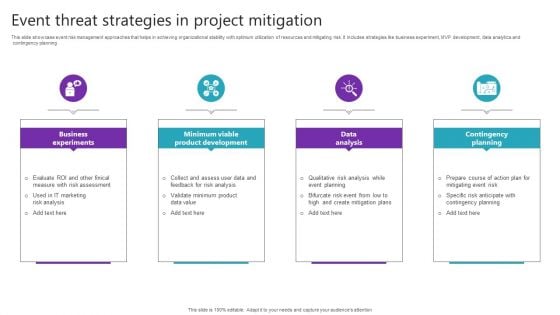
Event Threat Strategies In Project Mitigation Diagrams PDF
Presenting Event Threat Strategies In Project Mitigation Diagrams PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Business Experiments, Minimum Viable, Product Development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
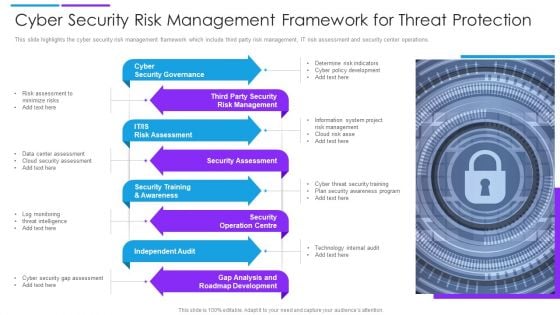
Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
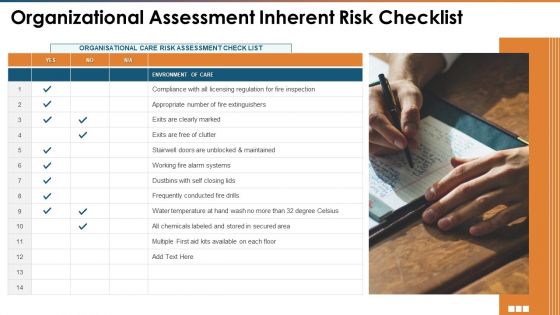
Threat Administration Bundle Organizational Assessment Inherent Risk Checklist Pictures PDF
This is a threat administration bundle organizational assessment inherent risk checklist pictures pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational assessment inherent risk checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
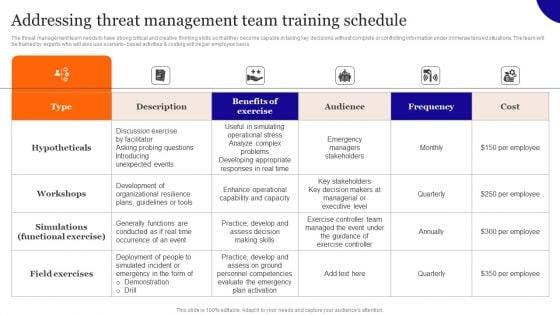
Addressing Threat Management Team Training Schedule Designs PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Addressing Threat Management Team Training Schedule Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Threat Administration Bundle Project Management Risk Submission Form Structure PDF
Presenting threat administration bundle project management risk submission form structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like general project information, opportunity statement, business goal, project scope, projected costs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home