Threat
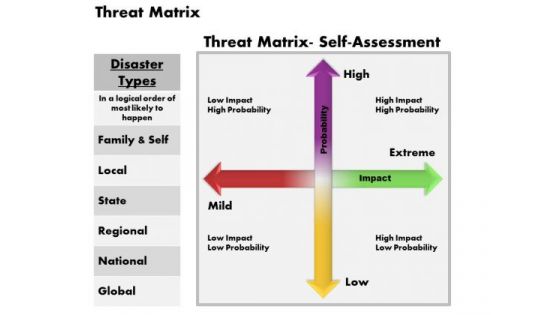
Business Framework Threat Matrix PowerPoint Presentation
A four dimensional matrix has been used to design this power point diagram template. This PPT diagram contains the threat matrix. Display multiple values in your business presentation by using this PPT.
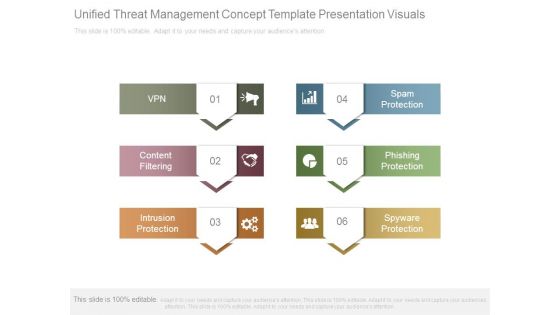
Unified Threat Management Concept Template Presentation Visuals
This is a unified threat management concept template presentation visuals. This is a six stage process. The stages in this process are vpn, content filtering, intrusion protection, spam protection, phishing protection, spyware protection.

Contingency Plan For Threat Handling Microsoft PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative contingency plan for threat handling microsoft pdf bundle. Topics like vendors coordination, contingency solutions, system backups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Contents Brochure Pdf
Presenting threat management at workplace contents brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like training schedule, determine staff training schedule, skills enhancement, selecting secured threat, management software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
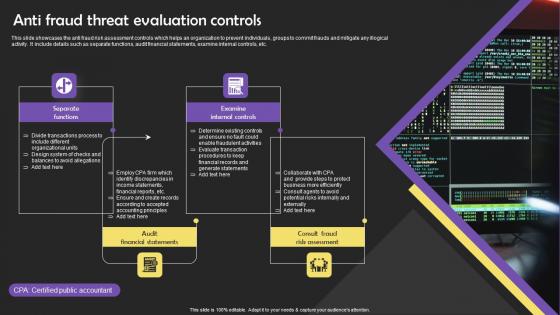
Anti Fraud Threat Evaluation Controls Slides Pdf
This slide showcases the anti fraud risk assessment controls which helps an organization to prevent individuals, groups to commit frauds and mitigate any illogical activity. It include details such as separate functions, audit financial statements, examine internal controls, etc. Showcasing this set of slides titled Anti Fraud Threat Evaluation Controls Slides Pdf The topics addressed in these templates are Separate Functions, Examine Internal Controls, Financial Statements All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the anti fraud risk assessment controls which helps an organization to prevent individuals, groups to commit frauds and mitigate any illogical activity. It include details such as separate functions, audit financial statements, examine internal controls, etc.

Determine Threat Management Team Structure Graphics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Find highly impressive Determine Threat Management Team Structure Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Determine Threat Management Team Structure Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
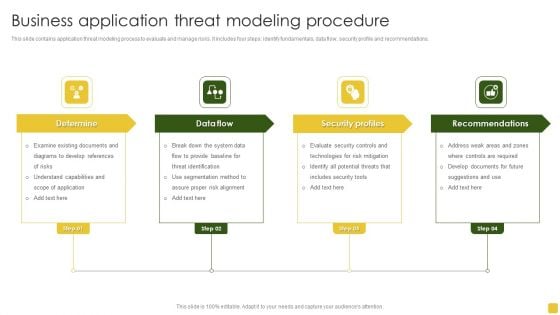
Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Event Threat Mitigation Action Plan Themes PDF
Pitch your topic with ease and precision using this Event Threat Mitigation Action Plan Themes PDF. This layout presents information on Failure To Meet, Compliance Obligations, Failure In Collecting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
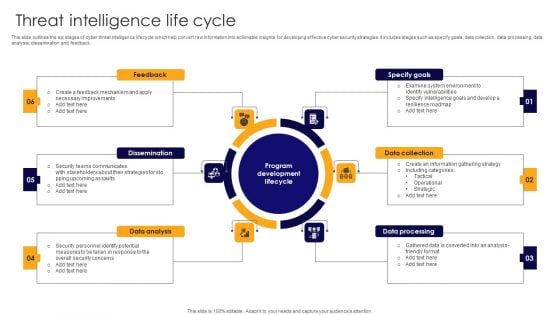
Threat Intelligence Life Cycle Elements PDF
Presenting Threat Intelligence Life Cycle Elements PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Feedback, Dissemination, Data Collection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Impact Management Plan Matrix Diagrams PDF
This slide covers the risk management matrix this prompts the team to identify risks, assess their potential impact, and devise mitigation strategies. It includes likelihood, metric, date , current value, etc. Presenting Threat Impact Management Plan Matrix Diagrams PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Metric, Action Plan, System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Management Strategy With Recommendations Demonstration PDF
This slide covers the risk mitigation plan which includes description of risk, its impact level and suggestions to mitigate risks such as maintaining sufficient inventory, provide training to workers to enhance their efficiency, ensuring supplier capacity, application of standardized packaging. Persuade your audience using this Threat Management Strategy With Recommendations Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Stock, Level Of Risk, Risk Mitigation Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
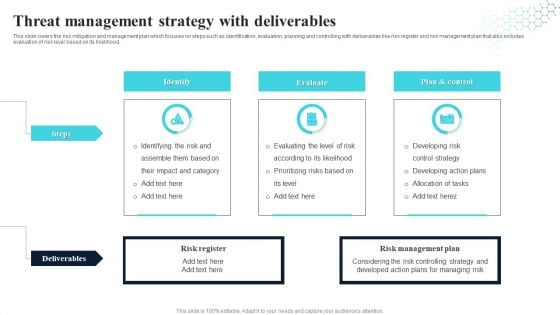
Threat Management Strategy With Deliverables Guidelines PDF
This slide covers the risk mitigation and management plan which focuses on steps such as identification, evaluation, planning and controlling with deliverables like risk register and risk management plan that also includes evaluation of risk level based on its likelihood. Persuade your audience using this Threat Management Strategy With Deliverables Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Evaluate, Plan And Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
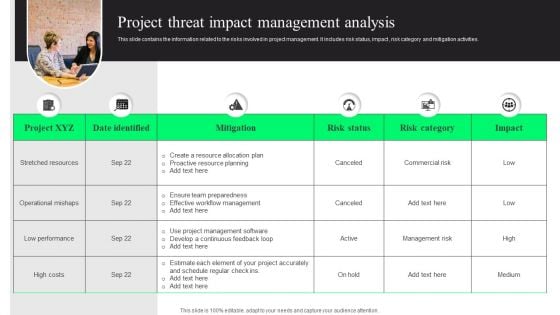
Project Threat Impact Management Analysis Portrait PDF
This slide contains the information related to the risks involved in project management. It includes risk status, impact , risk category and mitigation activities. Persuade your audience using this Project Threat Impact Management Analysis Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Low Performance, Stretched Resources, Risk Category. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
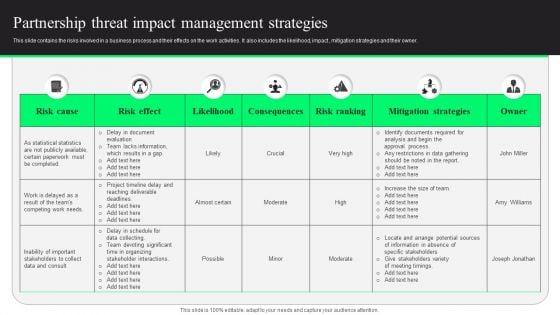
Partnership Threat Impact Management Strategies Mockup PDF
This slide contains the risks involved in a business process and their effects on the work activities. It also includes the likelihood, impact , mitigation strategies and their owner. Pitch your topic with ease and precision using this Partnership Threat Impact Management Strategies Mockup PDF. This layout presents information on Risk Effect, Risk Cause, Mitigation Strategies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
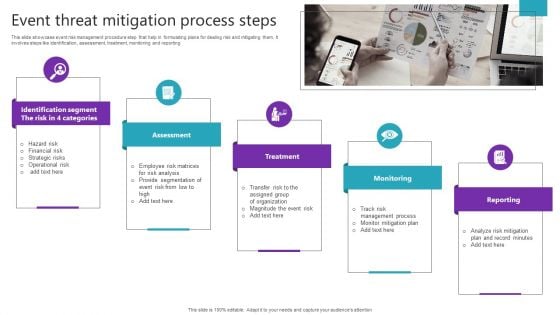
Event Threat Mitigation Process Steps Background PDF
This slide showcase event risk management procedure step that help in formulating plans for dealing risk and mitigating them. It involves steps like identification, assessment, treatment, monitoring and reporting. Persuade your audience using this Event Threat Mitigation Process Steps Background PDF. This PPT design covers Assessment, Treatment, Monitoring stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Treatment, Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Supply Threat Impact Management Strategies Portrait PDF
This slide covers the risks involved in the supply chain of the business which leads to various issues and discrepancies. It also includes its impact and plan for mitigating the risk. Persuade your audience using this Supply Threat Impact Management Strategies Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Quality, Cost, Mitigation Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
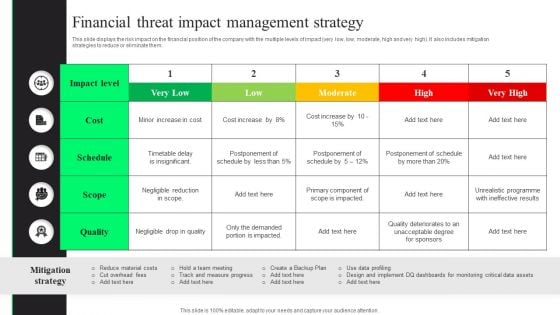
Financial Threat Impact Management Strategy Themes PDF
This slide displays the risk impact on the financial position of the company with the multiple levels of impact very low, low, moderate, high and very high. It also includes mitigation strategies to reduce or eliminate them. Showcasing this set of slides titled Financial Threat Impact Management Strategy Themes PDF. The topics addressed in these templates are Quality, Mitigation Strategy, Reduce Material Costs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
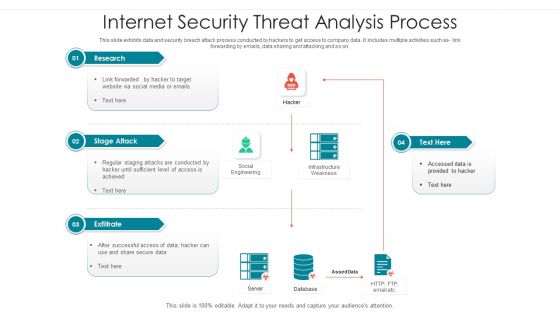
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
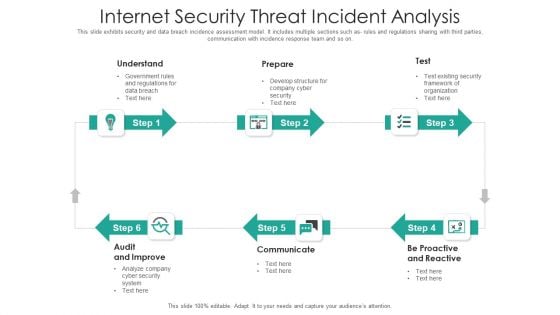
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
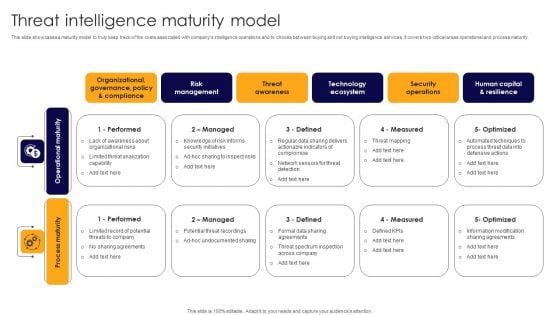
Threat Intelligence Maturity Model Professional PDF
This slide showcases a maturity model to truly keep track of the costs associated with companys intelligence operations and to choose between buying and not buying intelligence services. It covers two critical areas operational and process maturity. Presenting Threat Intelligence Maturity Model Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Performed, Managed, Defined. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
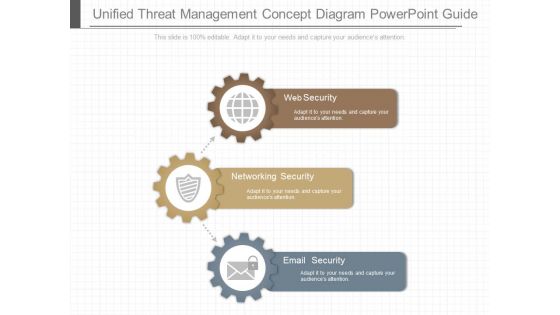
Unified Threat Management Concept Diagram Powerpoint Guide
This is a unified partnership in corporate development ppt powerpoint guide. This is a three stage process. The stages in this process are web security, networking security, email security.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Plan Mockup PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities threat management action plan mockup pdf. Use them to share invaluable insights on threat identification, threat treatment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF bundle. Topics like Computer Criminal, Industrial Espionage, System Intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
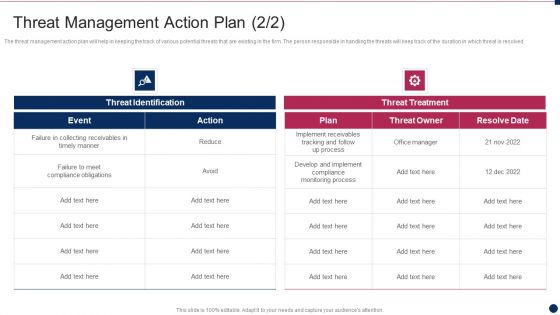
Threat Management At Workplace Threat Management Action Plan Identification Clipart PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an awe inspiring pitch with this creative threat management at workplace threat management action plan identification clipart pdf bundle. Topics like collecting receivables in timely manner, meet compliance obligations, implement compliance monitoring process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Threat Vulnerability Asset Matrix Ppt Gallery Templates PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative handling cyber threats digital era threat vulnerability asset matrix ppt gallery templates pdf bundle. Topics like erability asset matrix can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Addressing Internal And External Sources Of Threat Data Microsoft Pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing internal and external sources of threat data microsoft pdf. Use them to share invaluable insights on vendor security advisories, law enforcement and news media, commercial solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
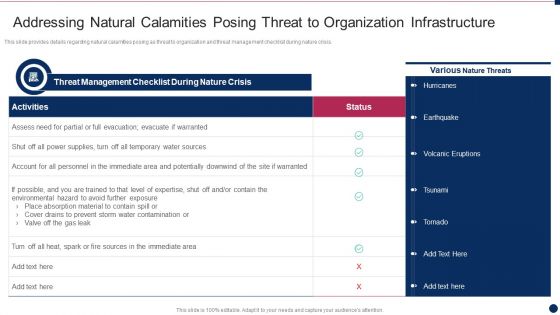
Threat Management At Workplace Addressing Natural Calamities Posing Threat To Organization Slides Pdf
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative threat management at workplace addressing natural calamities posing threat to organization slides pdf bundle. Topics like volcanic eruptions, hurricanes, tsunami can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
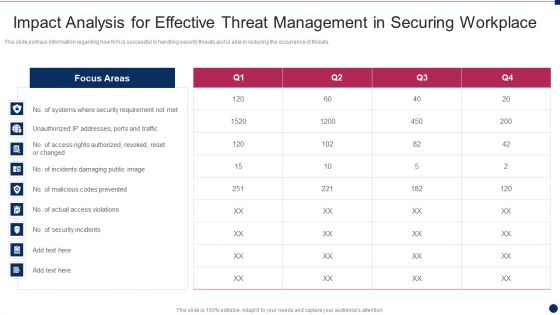
Threat Management At Workplace Impact Analysis For Effective Threat Management In Securing Structure PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative threat management at workplace impact analysis for effective threat management in securing structure pdf bundle. Topics like security incidents, incidents damaging public image, actual access violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Business Threats Landscape Icon For Financial Threat Ppt Professional Master Slide
Persuade your audience using this Business Threats Landscape Icon For Financial Threat Ppt Professional Master Slide. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Business Threats, Landscape Icon, Financial Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis For Effective Threat Graphics PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. This is a mitigating cybersecurity threats and vulnerabilities impact analysis for effective threat graphics pdf template with various stages. Focus and dispense information one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis for effective threat management in securing workplace. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
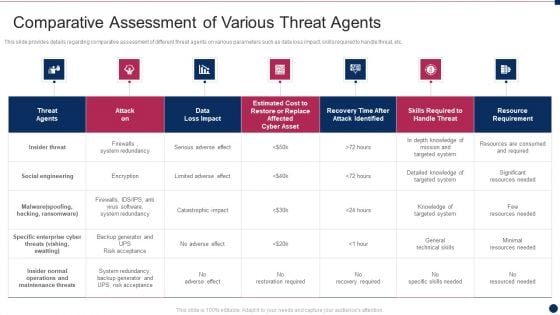
Threat Management At Workplace Comparative Assessment Of Various Threat Agents Professional Pdf
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace comparative assessment of various threat agents professional pdf. Use them to share invaluable insights on maintenance threats, catastrophic impact, general technical skills, knowledge of targeted system, significant resources needed and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods IT Vulnerabilities With Threat Source And Action Template PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. This is a Information Technology Threat Mitigation Methods IT Vulnerabilities With Threat Source And Action Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerabilities, Threat Source, Threat Action. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
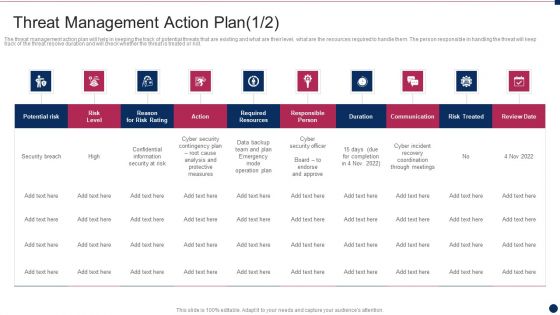
Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
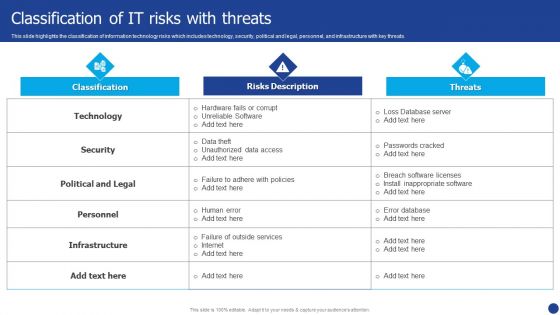
Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF bundle. Topics like Risks Description, Technology, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
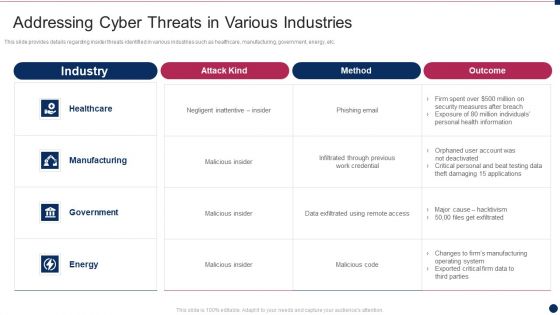
Threat Management At Workplace Addressing Cyber Threats In Various Industries Ideas Pdf
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing cyber threats in various industries ideas pdf. Use them to share invaluable insights on healthcare, manufacturing, energy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Addressing Indicators Associated To Insider Cyber Threats Portrait Pdf
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver an awe inspiring pitch with this creative threat management at workplace addressing indicators associated to insider cyber threats portrait pdf bundle. Topics like financial stress, passed over for promotion, dissatisfaction towards organizational policies, hacktivism, revengeful can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
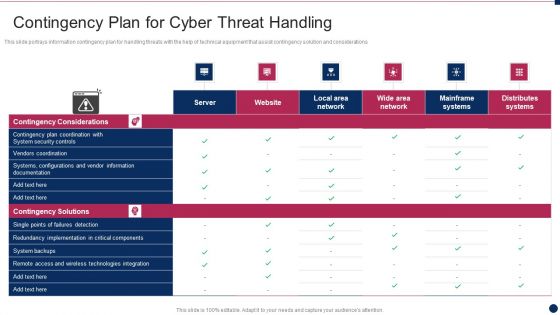
Threat Management At Workplace Contingency Plan For Cyber Threat Handling Infographics Pdf
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative threat management at workplace contingency plan for cyber threat handling infographics pdf bundle. Topics like remote access and wireless technologies integration, vendors coordination, system backups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Determine Several Threat Actors Profile Ideas Pdf
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative threat management at workplace determine several threat actors profile ideas pdf bundle. Topics like hacktivists, cyber criminal, moderate intensity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
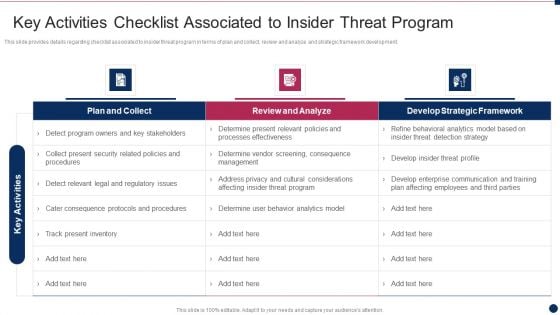
Threat Management At Workplace Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver an awe inspiring pitch with this creative threat management at workplace key activities checklist associated to insider threat program download pdf bundle. Topics like review and analyze, plan and collect, develop strategic framework can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
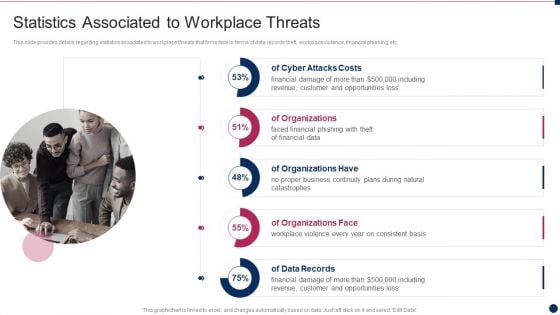
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
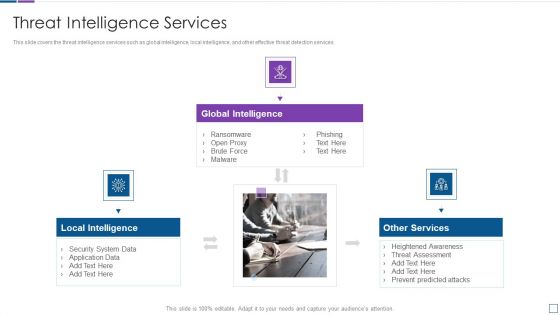
Real Time Assessment Of Security Threats Threat Intelligence Services Guidelines PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a real time assessment of security threats threat intelligence services guidelines pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
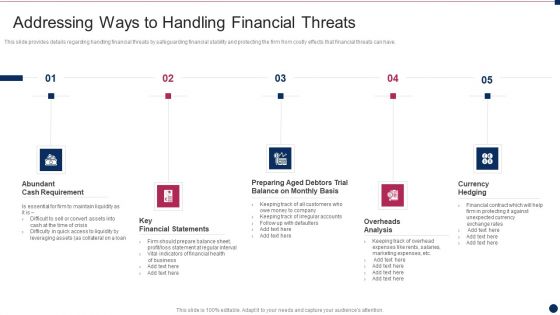
Threat Management At Workplace Addressing Ways To Handling Financial Threats Template Pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting threat management at workplace addressing ways to handling financial threats template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like abundant cash requirement, overheads analysis, currency hedging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
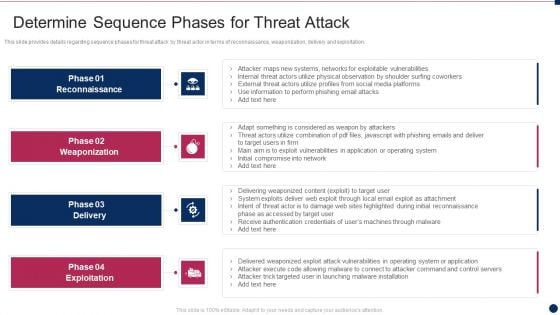
Threat Management At Workplace Determine Sequence Phases For Threat Attack Pictures Pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a threat management at workplace determine sequence phases for threat attack pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
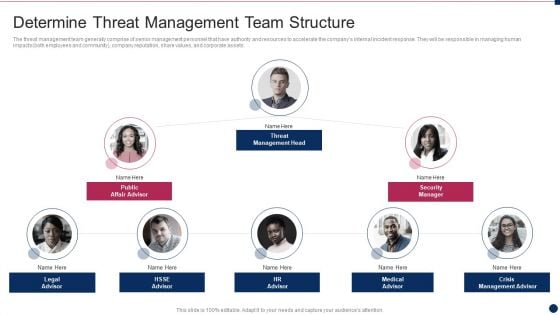
Threat Management At Workplace Determine Threat Management Team Structure Designs Pdf
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting threat management at workplace determine threat management team structure designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like threat management head, public affair advisor, security manager. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
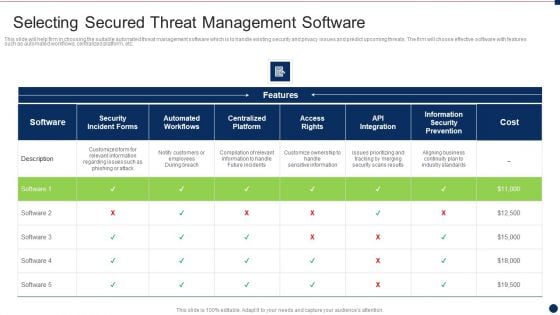
Threat Management At Workplace Selecting Secured Threat Management Software Information PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace selecting secured threat management software information pdf. Use them to share invaluable insights on customize ownership to handle sensitive information, compilation of relevant information to handle future incidents, aligning business continuity plan to industry standards and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
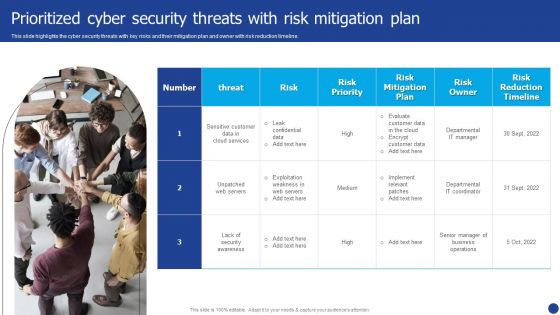
Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
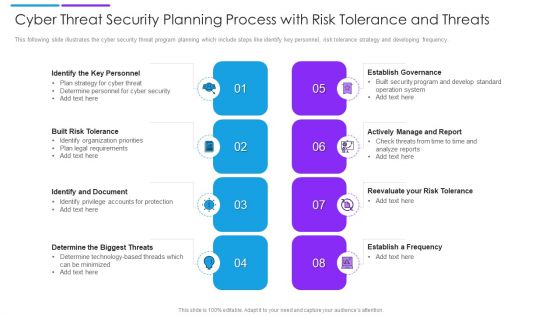
Cyber Threat Security Planning Process With Risk Tolerance And Threats Formats PDF
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
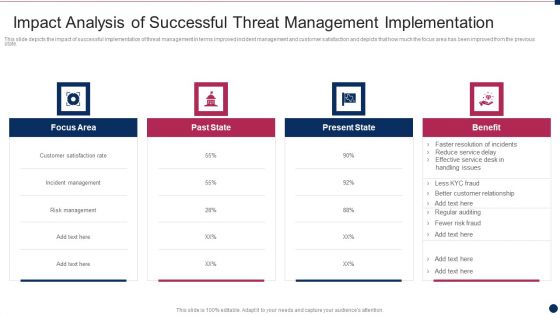
Threat Management At Workplace Impact Analysis Of Successful Threat Management Implementation Diagrams PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this threat management at workplace impact analysis of successful threat management implementation diagrams pdf. Use them to share invaluable insights on customer satisfaction rate, incident management, risk management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
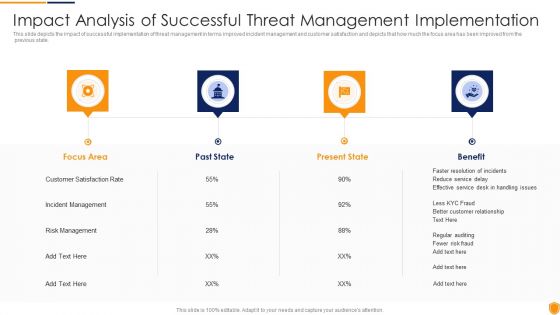
Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis Of Successful Threat Slides PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Presenting mitigating cybersecurity threats and vulnerabilities impact analysis of successful threat slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like focus area, past state, present state, benefit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
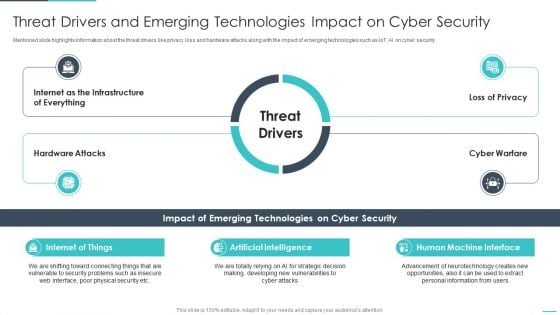
Handling Cyber Threats Digital Era Threat Drivers And Emerging Technologies Ppt Styles Ideas PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era threat drivers and emerging technologies ppt styles ideas pdf. Use them to share invaluable insights on internet of things, artificial intelligence, human machine interface and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
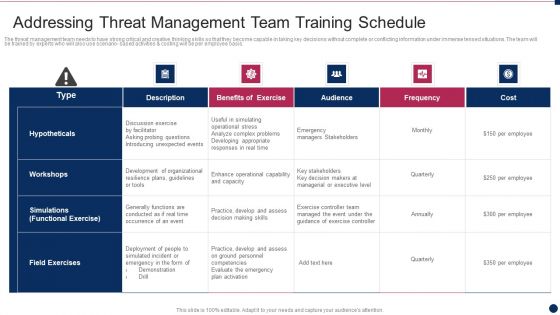
Threat Management At Workplace Addressing Threat Management Team Training Schedule Pictures Pdf
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative threat management at workplace addressing threat management team training schedule pictures pdf bundle. Topics like practice, develop and assess decision making skills, enhance operational capability and capacity, emergency managers stakeholders can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
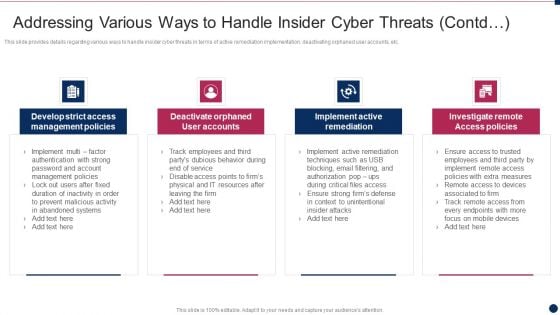
Threat Management At Workplace Addressing Various Ways To Handle Insider Cyber Threats Mockup Pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a threat management at workplace addressing various ways to handle insider cyber threats mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
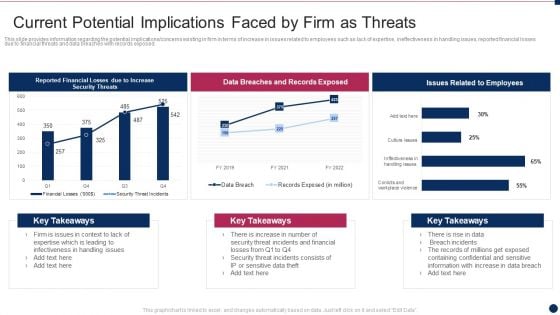
Threat Management At Workplace Current Potential Implications Faced By Firm As Threats Professional Pdf
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this threat management at workplace current potential implications faced by firm as threats professional pdf. Use them to share invaluable insights on data breaches and records exposed, breach incidents, financial losses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Different Kinds Of Insider Digital Threats Themes Pdf
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting threat management at workplace different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Threat Management At Workplace Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a threat management at workplace various types of workplace violence and threats designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harassment or intimidation, stalking, physical assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Budget For Effective Threat Ideas PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities budget for effective threat ideas pdf bundle. Topics like incident management, risk management, client onboarding process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user
Purpose Of Fraud Threat Administration Guide Fraud Threat Administration Guide Graphics PDF
This is a Purpose Of Fraud Threat Administration Guide Fraud Threat Administration Guide Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Assessment Methodologies, Tailored Address, Evolving Risk Landscape. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
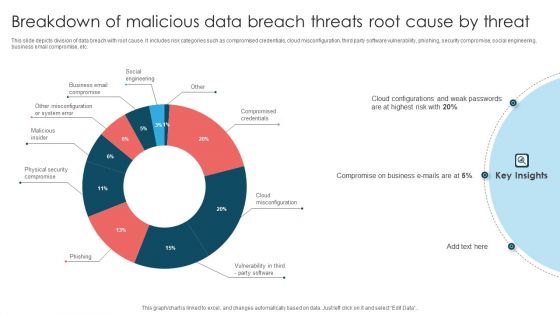
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Evaluation Icon Ppt PowerPoint Presentation Outline Graphics Tutorials
Presenting this set of slides with name threat evaluation icon ppt powerpoint presentation outline graphics tutorials. This is a three stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home