Vulnerability Management

Company Vulnerability Administration Ppt PowerPoint Presentation Complete Deck With Slides

Vulnerability Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
This Vulnerability Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Vulnerability Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Enhancing Cyber Safety With Vulnerability Administration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty one slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
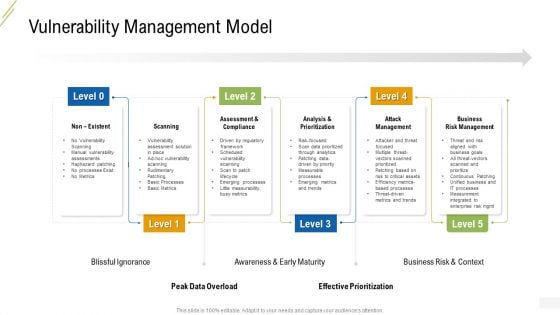
Company Vulnerability Administration Vulnerability Management Model Infographics PDF
This is a company vulnerability administration vulnerability management model infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment and compliance, analysis and prioritization, attack management, business risk management, scanning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
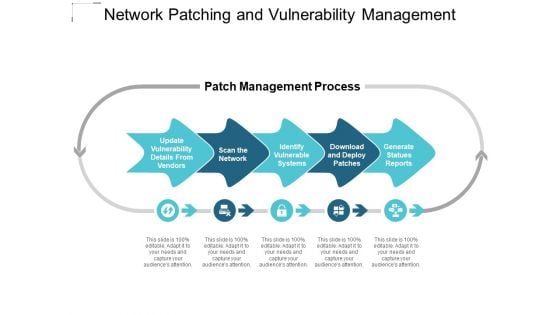
Network Patching And Vulnerability Management Ppt PowerPoint Presentation Ideas Themes
This is a network patching and vulnerability management ppt powerpoint presentation ideas themes. This is a five stage process. The stages in this process are patch management process, patch management procedure, patch management approach.
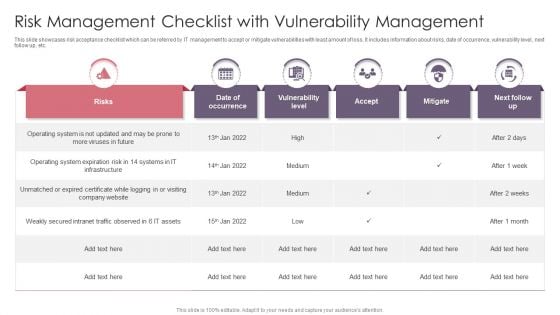
Risk Management Checklist With Vulnerability Management Pictures PDF
This slide showcases risk acceptance checklist which can be referred by IT management to accept or mitigate vulnerabilities with least amount of loss. It includes information about risks, date of occurrence, vulnerability level, next follow up, etc. Pitch your topic with ease and precision using this Risk Management Checklist With Vulnerability Management Pictures PDF. This layout presents information on Operating System, Risk, Intranet Traffic. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Vulnerability Management Patching Ppt PowerPoint Presentation Outline Demonstration Cpb
Presenting this set of slides with name vulnerability management patching ppt powerpoint presentation outline demonstration cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management patching to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Decision Making Process Flow For Vulnerability Management Portrait Pdf
The purpose of this slide is to represent decision making flow chart to handle vulnerabilities. It includes various steps such as identifying vulnerability, verifying vulnerability, determining possibility to remediate, applying remediation etc. Showcasing this set of slides titled Decision Making Process Flow For Vulnerability Management Portrait Pdf. The topics addressed in these templates are Identify Vulnerability, Verify Vulnerability, Apply Remediation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent decision making flow chart to handle vulnerabilities. It includes various steps such as identifying vulnerability, verifying vulnerability, determining possibility to remediate, applying remediation etc.
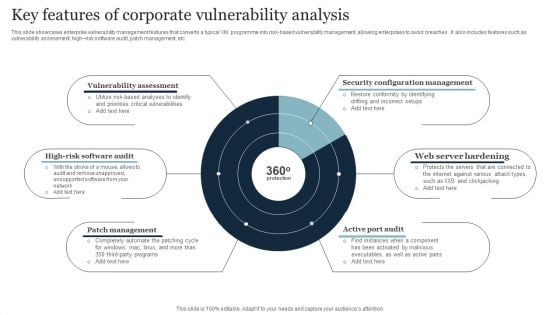
Key Features Of Corporate Vulnerability Analysis Inspiration PDF
This slide showcases enterprise vulnerability management features that converts a typical VM programme into risk-based vulnerability management, allowing enterprises to avoid breaches . It also includes features such as vulnerability assessment, high risk software audit, patch management, etc. Presenting Key Features Of Corporate Vulnerability Analysis Inspiration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security Configuration Management, Web Server Hardening, Active Port Audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vulnerability Management Powerpoint Templates Microsoft

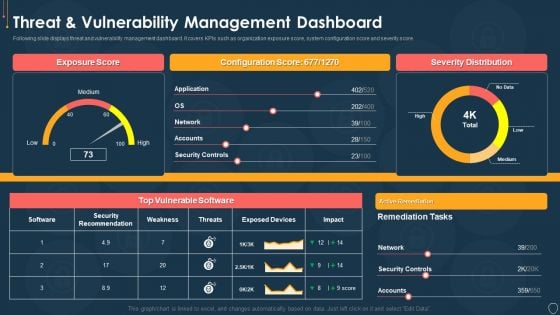
Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
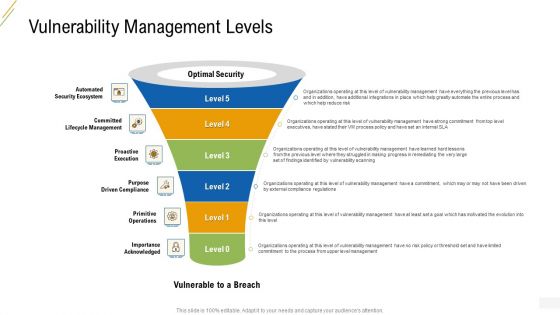
Company Vulnerability Administration Vulnerability Management Levels Elements PDF
Presenting company vulnerability administration vulnerability management levels elements pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like automated security ecosystem, committed lifecycle management, proactive execution, purpose driven compliance, primitive operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
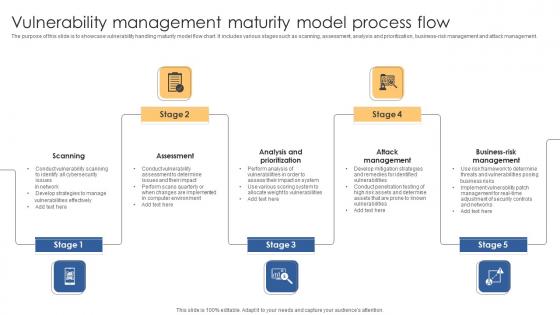
Vulnerability Management Maturity Model Process Flow Microsoft Pdf
The purpose of this slide is to showcase vulnerability handling maturity model flow chart. It includes various stages such as scanning, assessment, analysis and prioritization, business-risk management and attack management. Pitch your topic with ease and precision using this Vulnerability Management Maturity Model Process Flow Microsoft Pdf. This layout presents information on Scanning, Assessment, Analysis Prioritization. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase vulnerability handling maturity model flow chart. It includes various stages such as scanning, assessment, analysis and prioritization, business-risk management and attack management.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
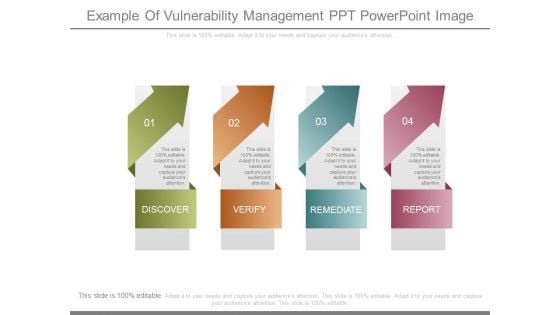
Example Of Vulnerability Management Ppt Powerpoint Image
This is a example of vulnerability management ppt powerpoint image. This is a four stage process. The stages in this process are discover, verify, remediate, report.
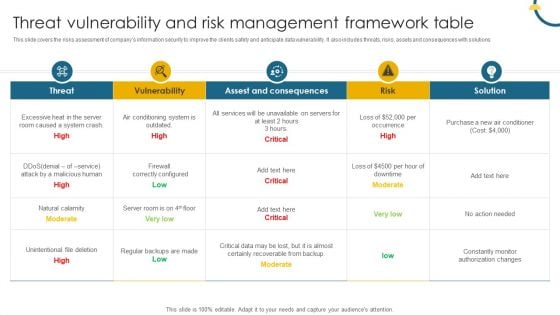
Threat Vulnerability And Risk Management Framework Table Portrait PDF
This slide covers the risks assessment of companys information security to improve the clients safety and anticipate data vulnerability. It also includes threats, risks, assets and consequences with solutions. Pitch your topic with ease and precision using this Threat Vulnerability And Risk Management Framework Table Portrait PDF. This layout presents information on Vulnerability, Threat, High, Low, Medium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
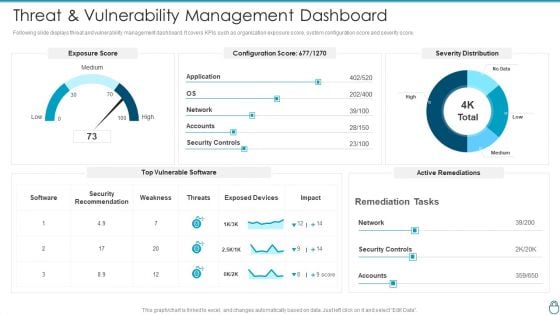
Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF Use them to share invaluable insights on Exposure Score, Remediation Tasks, Severity Distribution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Vulnerability Management Program Practices Ppt PowerPoint Presentation Inspiration Cpb
Presenting this set of slides with name vulnerability management program practices ppt powerpoint presentation inspiration cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management program practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Company Vulnerability Administration Need For Vulnerability Management Introduction PDF
Presenting company vulnerability administration need for vulnerability management introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detective controls, responsive controls, vulnerability management is a standard process, implementing a vulnerability management program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Manage Exposure To Discovered Vulnerabilities Introduction PDF
This is a company vulnerability administration manage exposure to discovered vulnerabilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine disposition methodology, test disposition, deploy disposition method, track to resolution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
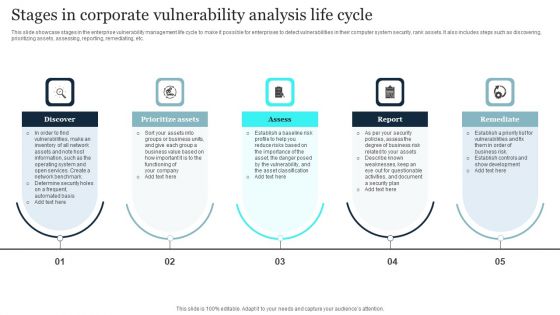
Stages In Corporate Vulnerability Analysis Life Cycle Slides PDF
This slide showcase stages in the enterprise vulnerability management life cycle to make it possible for enterprises to detect vulnerabilities in their computer system security, rank assets. It also includes steps such as discovering, prioritizing assets, assessing, reporting, remediating, etc. Presenting Stages In Corporate Vulnerability Analysis Life Cycle Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prioritize Assets, Report, Remediate, Assess. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
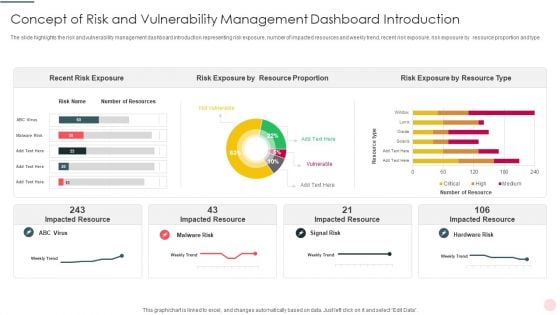
Concept Of Risk And Vulnerability Management Dashboard Introduction Portrait PDF
Showcasing this set of slides titled Concept Of Risk And Vulnerability Management Dashboard Introduction Portrait PDF The topics addressed in these templates are Recent Risk Exposure, Risk Exposure, Impacted Resource All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Web Application Vulnerability Administration Plan Pictures PDF
This slide defines the flowchart for adopting web application vulnerability management program. It includes information related to the enrollment process from introducing new web application to continuous assessment. Presenting Web Application Vulnerability Administration Plan Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including New Web Application, Gather Information, Scanner Enrollment, Scanner Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF
This slide showcases tools for enterprise vulnerability management helps businesses secure their networks by identifying and fixing issues. It also includes tools such as nessus professional,nexpose community edition, openvas, manageengine vulnerability manager plus, etc. Persuade your audience using this Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations Environment, Limitless Evaluation, Implement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
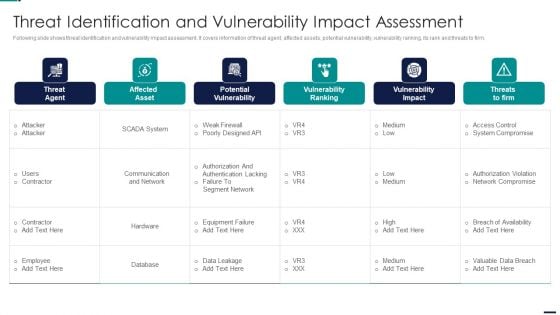
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
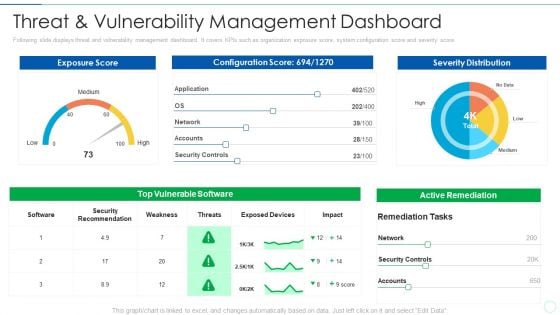
Effective IT Risk Management Process Threat And Vulnerability Management Rules PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this effective it risk management process threat and vulnerability management rules pdf. Use them to share invaluable insights on threat and vulnerability management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Vulnerability Management Remediation Process Ppt PowerPoint Presentation Ideas Styles Cpb
Presenting this set of slides with name vulnerability management remediation process ppt powerpoint presentation ideas styles cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management remediation process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Management Roles Ppt PowerPoint Presentation Professional Graphics Cpb
Presenting this set of slides with name vulnerability management roles ppt powerpoint presentation professional graphics cpb. This is an editable Powerpoint four stages graphic that deals with topics like vulnerability management roles to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Management Tracking System Ppt PowerPoint Presentation Summary Images Cpb
Presenting this set of slides with name vulnerability management tracking system ppt powerpoint presentation summary images cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management tracking system to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Attack Vulnerability Management In Powerpoint And Google Slides Cpb
Introducing our well designed Attack Vulnerability Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Attack Vulnerability Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Attack Vulnerability Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
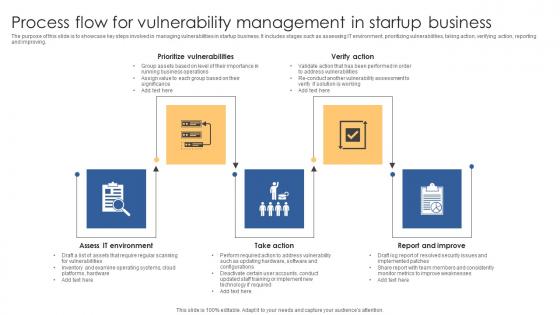
Process Flow For Vulnerability Management In Startup Business Background Pdf
The purpose of this slide is to showcase key steps involved in managing vulnerabilities in startup business. It includes stages such as assessing IT environment, prioritizing vulnerabilities, taking action, verifying action, reporting and improving. Pitch your topic with ease and precision using this Process Flow For Vulnerability Management In Startup Business Background Pdf. This layout presents information on Prioritize Vulnerabilities, Verify Action, Take Action. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase key steps involved in managing vulnerabilities in startup business. It includes stages such as assessing IT environment, prioritizing vulnerabilities, taking action, verifying action, reporting and improving.

Company Vulnerability Administration Define And Plan For Vulnerability Management Ideas PDF
Presenting company vulnerability administration define and plan for vulnerability management ideas pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like overview, define and document the plan, define measures of effectiveness, define training requirements, determine tools aligned to the strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Determine The Scope Of Vulnerability Management Designs PDF
This is a company vulnerability administration determine the scope of vulnerability management designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like document the candidate assets and services to be assessed and monitored, determine the operational environment for analysis and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vulnerability Management Policy Statement Production Execution Business Intelligence Ppt PowerPoint Presentation Inspiration Template
This is a vulnerability management policy statement production execution business intelligence ppt powerpoint presentation inspiration template. This is a four stage process. The stages in this process are vulnerability management policy statement, production execution, business intelligence.
Vulnerability Management Process Business Accounting Venture Capital Availability Ppt PowerPoint Presentation Icon Graphics
This is a vulnerability management process business accounting venture capital availability ppt powerpoint presentation icon graphics. This is a two stage process. The stages in this process are vulnerability management process, business accounting, venture capital availability.

Human Resources Development Enterprise Vulnerability Management 5S Manufacturing Ppt PowerPoint Presentation Professional Microsoft
This is a human resources development enterprise vulnerability management 5s manufacturing ppt powerpoint presentation professional microsoft. This is a five stage process. The stages in this process are human resources development, enterprise vulnerability management, 5s manufacturing.
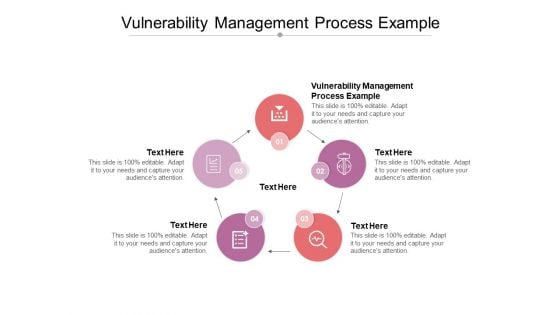
Vulnerability Management Process Example Ppt PowerPoint Presentation Slides Background Designs Cpb
Presenting this set of slides with name vulnerability management process example ppt powerpoint presentation slides background designs cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management process example to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
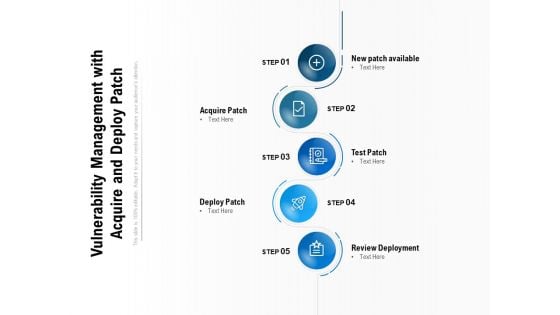
Vulnerability Management With Acquire And Deploy Patch Ppt PowerPoint Presentation Infographic Template Pictures PDF
Presenting this set of slides with name vulnerability management with acquire and deploy patch ppt powerpoint presentation infographic template pictures pdf. This is a five stage process. The stages in this process are new patch available, acquire patch, test patch, deploy patch, review deployment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Graphics PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities threat management action graphics pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
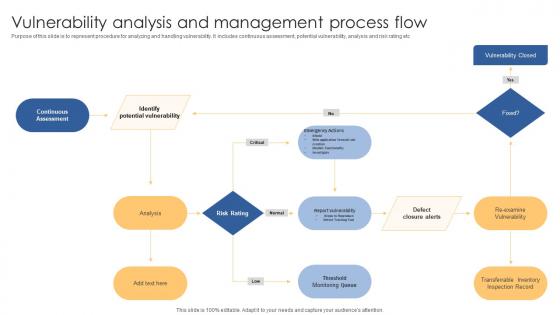
Vulnerability Analysis And Management Process Flow Introduction Pdf
Purpose of this slide is to represent procedure for analyzing and handling vulnerability. It includes continuous assessment, potential vulnerability, analysis and risk rating etc Showcasing this set of slides titled Vulnerability Analysis And Management Process Flow Introduction Pdf. The topics addressed in these templates are Identify Potential Vulnerability, Analysis, Defect Closure Alerts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Purpose of this slide is to represent procedure for analyzing and handling vulnerability. It includes continuous assessment, potential vulnerability, analysis and risk rating etc
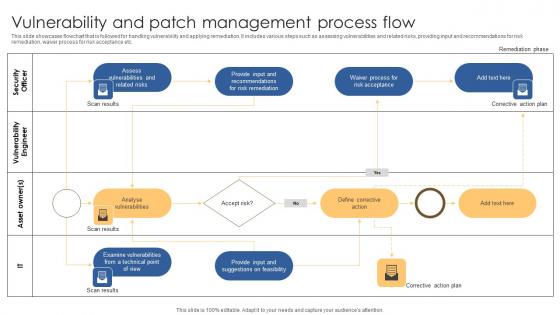
Vulnerability And Patch Management Process Flow Microsoft Pdf
This slide showcases flowchart that is followed for handling vulnerability and applying remediation. It includes various steps such as assessing vulnerabilities and related risks, providing input and recommendations for risk remediation, waiver process for risk acceptance etc. Pitch your topic with ease and precision using this Vulnerability And Patch Management Process Flow Microsoft Pdf. This layout presents information on Security Officer, Vulnerability Engineer, Asset Owner. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart that is followed for handling vulnerability and applying remediation. It includes various steps such as assessing vulnerabilities and related risks, providing input and recommendations for risk remediation, waiver process for risk acceptance etc.
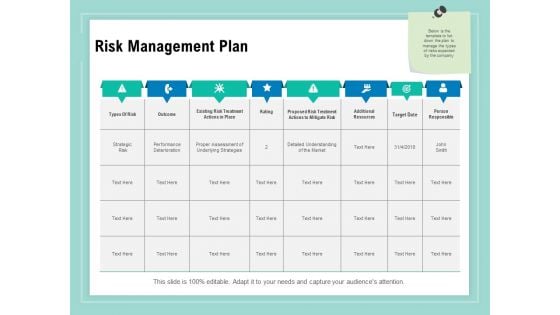
Vulnerability Assessment Methodology Risk Management Plan Ppt Inspiration Backgrounds PDF
Presenting this set of slides with name vulnerability assessment methodology risk management plan ppt inspiration backgrounds pdf. The topics discussed in these slides are types of risk, outcome, existing risk treatment actions in place, rating, proposed risk treatment actions to mitigate risk, additional resources, target date, person responsible. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Management Brochure PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting mitigating cybersecurity threats and vulnerabilities determine threat management brochure pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
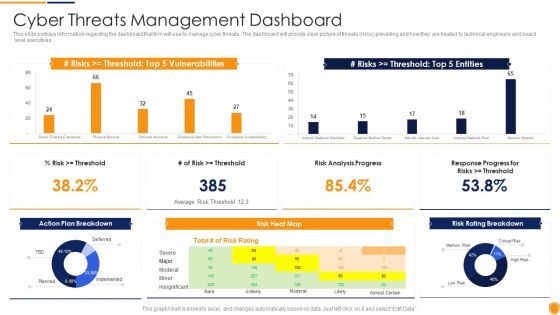
Mitigating Cybersecurity Threats And Vulnerabilities Cyber Threats Management Slides PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities cyber threats management slides pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
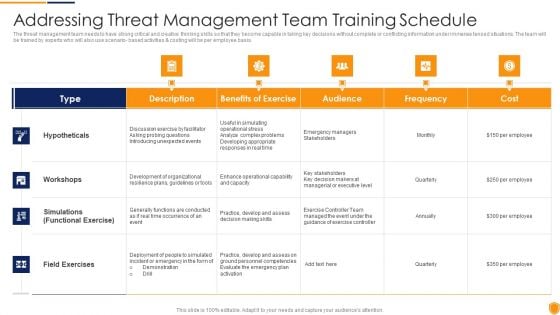
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Threat Management Download PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing threat management download pdf bundle. Topics like hypotheticals, workshops, field exercises can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Plan Mockup PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities threat management action plan mockup pdf. Use them to share invaluable insights on threat identification, threat treatment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective IT Risk Management Process Defining Vulnerability Rating Infographics PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this effective it risk management process defining vulnerability rating infographics pdf. Use them to share invaluable insights on defining vulnerability rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Enhancing Cyber Safety With Vulnerability Administration Log Management Services Metrics Icons PDF
Presenting enhancing cyber safety with vulnerability administration log management services metrics icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like logfiles, configurations, messages, metrics, scripts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhancing Cyber Safety With Vulnerability Administration Log Management Services Structure PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting enhancing cyber safety with vulnerability administration log management services structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
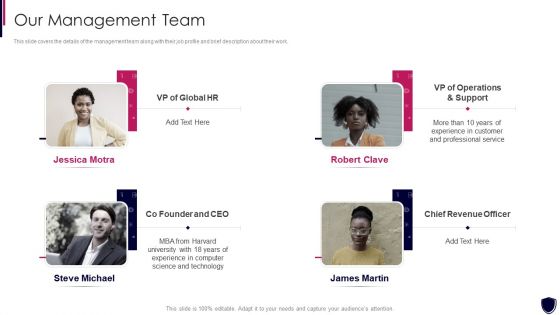
Enhancing Cyber Safety With Vulnerability Administration Our Management Team Information PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a enhancing cyber safety with vulnerability administration our management team information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
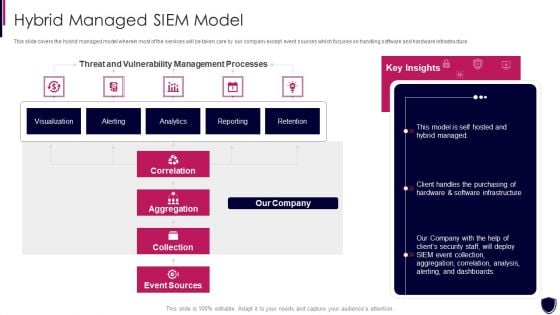
Enhancing Cyber Safety With Vulnerability Administration Hybrid Managed SIEM Model Summary PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration hybrid managed siem model summary pdf bundle. Topics like correlation, aggregation, collection, event sources, our company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
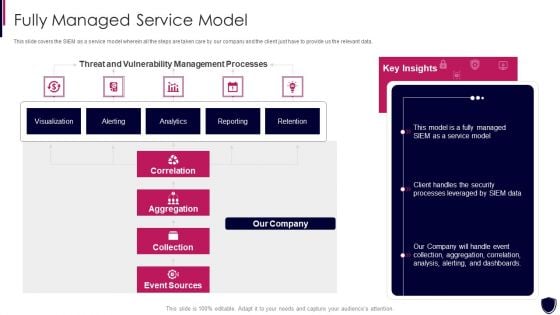
Enhancing Cyber Safety With Vulnerability Administration Fully Managed Service Model Clipart PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration fully managed service model clipart pdf bundle. Topics like correlation, aggregation, collection, event sources, our company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
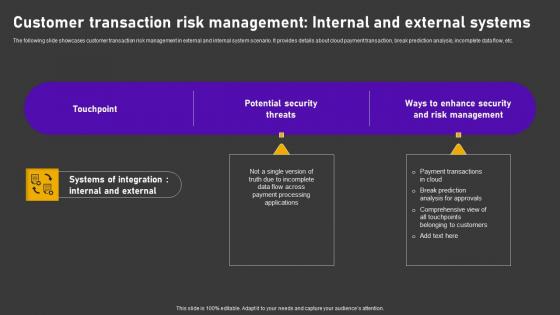
Minimizing Customer Transaction Vulnerabilities Customer Transaction Risk Management Clipart Pdf
The following slide showcases customer transaction risk management in external and internal system scenario. It provides details about cloud payment transaction, break prediction analysis, incomplete data flow, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Minimizing Customer Transaction Vulnerabilities Customer Transaction Risk Management Clipart Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Minimizing Customer Transaction Vulnerabilities Customer Transaction Risk Management Clipart Pdf. The following slide showcases customer transaction risk management in external and internal system scenario. It provides details about cloud payment transaction, break prediction analysis, incomplete data flow, etc.

Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Find highly impressive Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
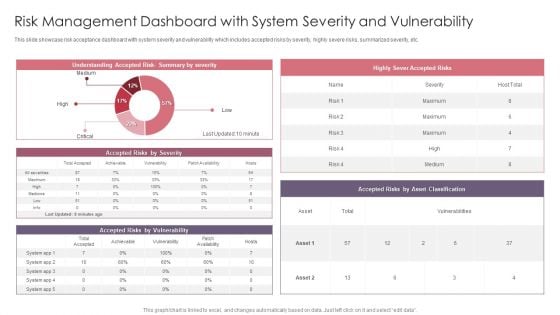
Risk Management Dashboard With System Severity And Vulnerability Template PDF
This slide showcase risk acceptance dashboard with system severity and vulnerability which includes accepted risks by severity, highly severe risks, summarized severity, etc. Showcasing this set of slides titled Risk Management Dashboard With System Severity And Vulnerability Template PDF. The topics addressed in these templates are Risk Management Dashboard, System Severity And Vulnerability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
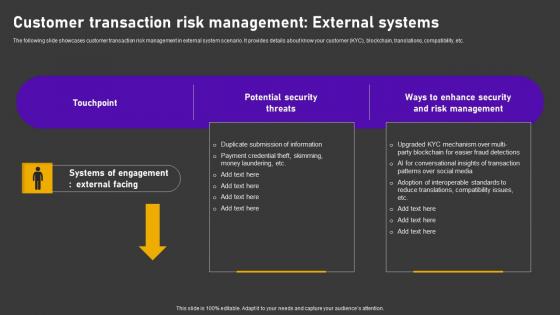
Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf
The following slide showcases customer transaction risk management in external system scenario. It provides details about know your customer KYC, blockchain, translations, compatibility, etc. Are you searching for a Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf from Slidegeeks today. The following slide showcases customer transaction risk management in external system scenario. It provides details about know your customer KYC, blockchain, translations, compatibility, etc.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
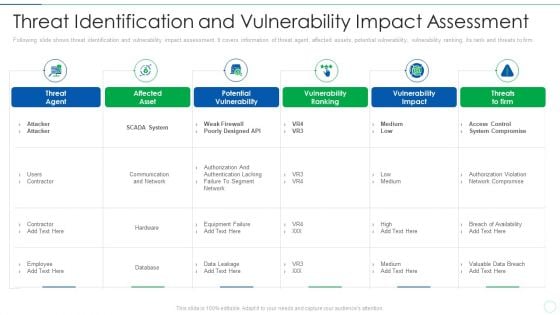
Effective IT Risk Management Process Threat Identification And Vulnerability Professional PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative effective it risk management process threat identification and vulnerability professional pdf bundle. Topics like potential vulnerability, system, network, designed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home