Vulnerability Management

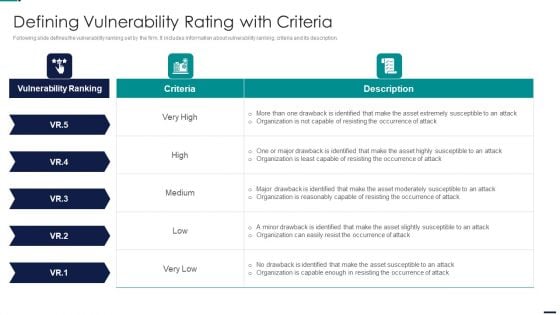
Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
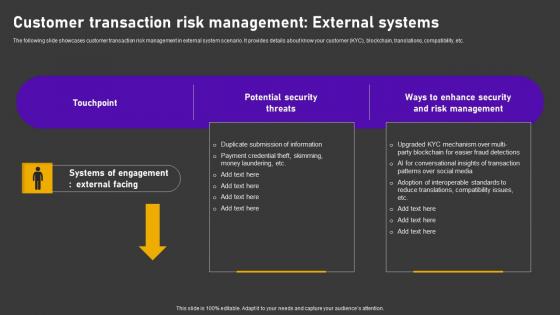
Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf
The following slide showcases customer transaction risk management in external system scenario. It provides details about know your customer KYC, blockchain, translations, compatibility, etc. Are you searching for a Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Customer Transaction Risk Management Minimizing Customer Transaction Vulnerabilities Clipart Pdf from Slidegeeks today. The following slide showcases customer transaction risk management in external system scenario. It provides details about know your customer KYC, blockchain, translations, compatibility, etc.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
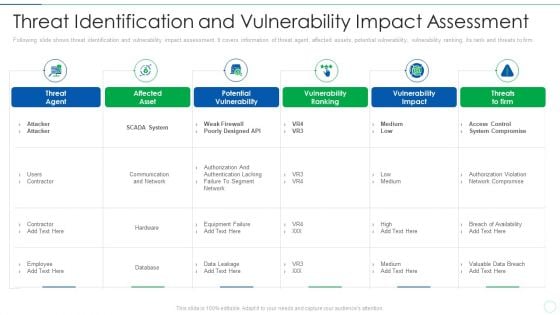
Effective IT Risk Management Process Threat Identification And Vulnerability Professional PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative effective it risk management process threat identification and vulnerability professional pdf bundle. Topics like potential vulnerability, system, network, designed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
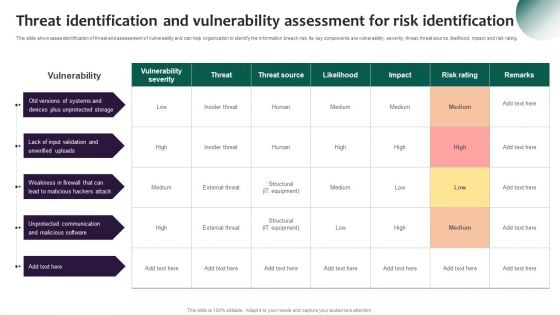
Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
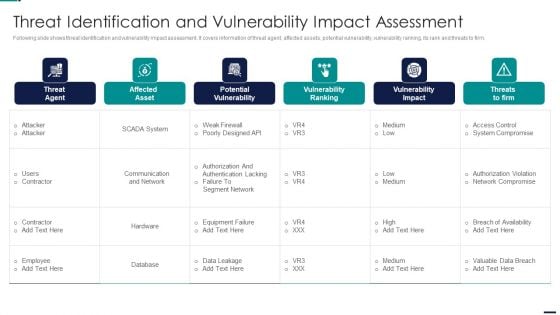
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
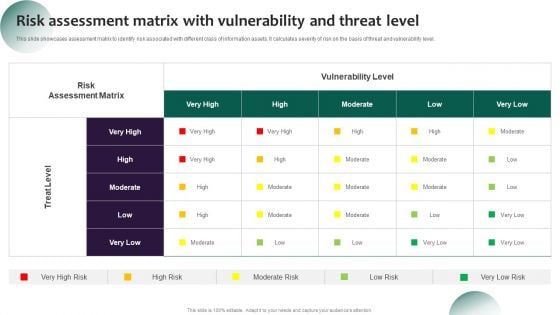
Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

Company Vulnerability Administration Introduction Designs PDF
Presenting company vulnerability administration introduction designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like need for vulnerability management, vulnerability management model, vulnerability management levels, overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Company Vulnerability Administration Overview Process Icons PDF
Deliver an awe inspiring pitch with this creative company vulnerability administration overview process icons pdf bundle. Topics like vulnerability management strategy, list of stakeholder, management support, budget for vulnerability management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
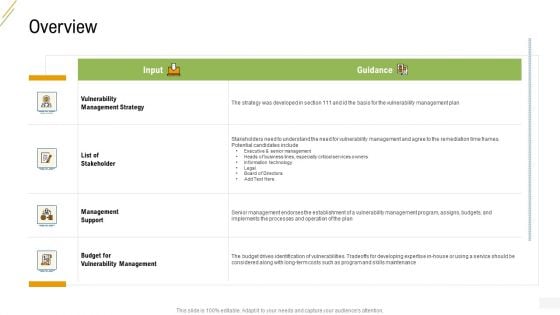
Company Vulnerability Administration Overview Guidance Slides PDF
Deliver an awe inspiring pitch with this creative company vulnerability administration overview guidance slides pdf bundle. Topics like vulnerability management strategy, list of stakeholder, management support, budget for vulnerability management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
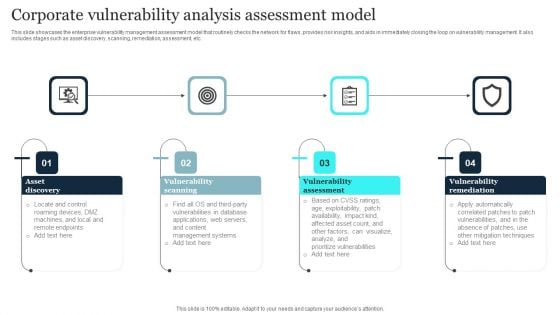
Corporate Vulnerability Analysis Assessment Model Elements PDF
This slide showcases the enterprise vulnerability management assessment model that routinely checks the network for flaws, provides risk insights, and aids in immediately closing the loop on vulnerability management. It also includes stages such as asset discovery, scanning, remediation, assessment, etc. Presenting Corporate Vulnerability Analysis Assessment Model Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Assessment, Vulnerability Scanning, Asset Discovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
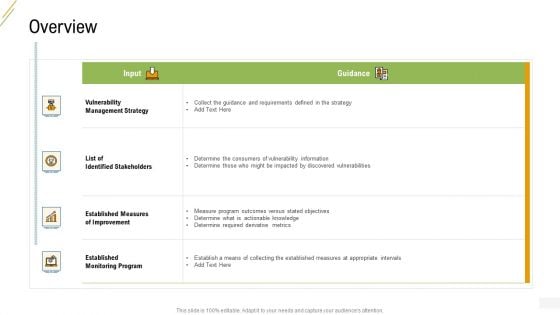
Company Vulnerability Administration Overview Strategy Themes PDF
Deliver and pitch your topic in the best possible manner with this company vulnerability administration overview strategy themes pdf. Use them to share invaluable insights on vulnerability management strategy, list of identified stakeholders, established measures of improvement, established monitoring program and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Company Vulnerability Administration Content Demonstration PDF
Presenting company vulnerability administration content demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like introduction, define a vulnerability analysis and resolution strategy, develop a plan for vulnerability management, implement the vulnerability analysis and resolution capability, assess and improve the capability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Determine Effectiveness Of Vulnerability Dispositions Microsoft PDF
This is a company vulnerability administration determine effectiveness of vulnerability dispositions microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate disposition efforts, update vulnerability repository, repeat disposition process as necessary. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Conduct Vulnerability Assessment Activities Elements PDF
This is a company vulnerability administration conduct vulnerability assessment activities elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like execute vulnerability scans, execute vulnerability assessments, personnel should possess the skills to appropriately execute the tasks defined, individuals need to be trained to use the specific tools, techniques, and methodologies . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Identify Sources Of Vulnerability Information Structure PDF
This is a company vulnerability administration identify sources of vulnerability information structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify assets in use, model numbers for hardware, version numbers for software, location of the component. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
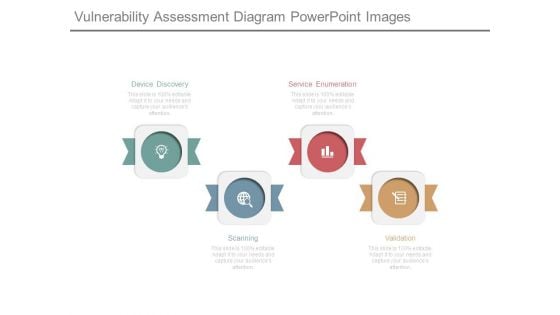
Vulnerability Assessment Diagram Powerpoint Images
This is a vulnerability assessment diagram powerpoint images. This is a four stage process. The stages in this process are device discovery, scanning, service enumeration, validation.

Web Application Vulnerability Administration Plan Pictures PDF
This slide defines the flowchart for adopting web application vulnerability management program. It includes information related to the enrollment process from introducing new web application to continuous assessment. Presenting Web Application Vulnerability Administration Plan Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including New Web Application, Gather Information, Scanner Enrollment, Scanner Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Company Vulnerability Administration Implement The Vulnerability Analysis And Resolution Capability Guidelines PDF
Presenting company vulnerability administration implement the vulnerability analysis and resolution capability guidelines pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like conduct vulnerability assessment activities, record discovered vulnerabilities, categorize and prioritize vulnerabilities, manage exposure to discovered vulnerabilities, analyze the root causes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Company Vulnerability Administration Define And Vulnerability Analysis And Resolution Strategy Icons PDF
This is a company vulnerability administration define and vulnerability analysis and resolution strategy icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overview, determine the scope of, vulnerability management, determine approved methods of vulnerability assessment, resource the activities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
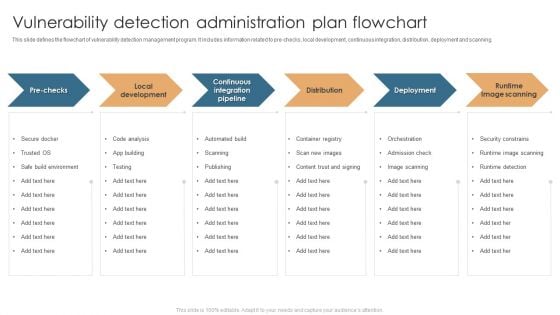
Vulnerability Detection Administration Plan Flowchart Sample PDF
This slide defines the flowchart of vulnerability detection management program. It includes information related to pre-checks, local development, continuous integration, distribution, deployment and scanning. Presenting Vulnerability Detection Administration Plan Flowchart Sample PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Local Development, Deployment, Runtime Image Scanning, Distribution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
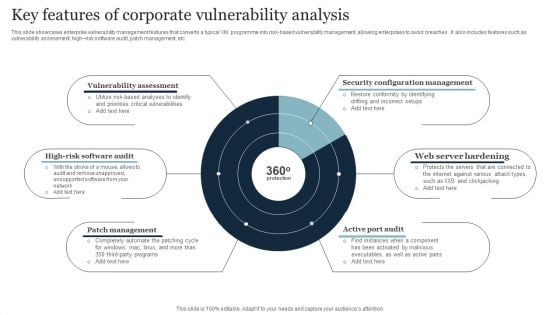
Key Features Of Corporate Vulnerability Analysis Inspiration PDF
This slide showcases enterprise vulnerability management features that converts a typical VM programme into risk-based vulnerability management, allowing enterprises to avoid breaches . It also includes features such as vulnerability assessment, high risk software audit, patch management, etc. Presenting Key Features Of Corporate Vulnerability Analysis Inspiration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security Configuration Management, Web Server Hardening, Active Port Audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
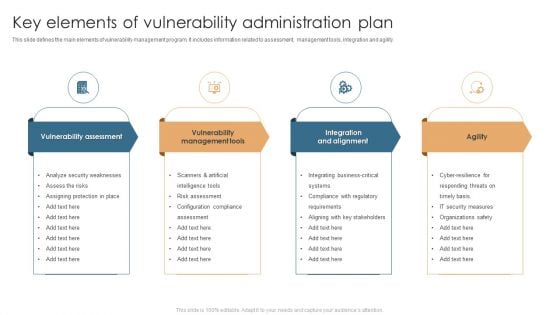
Key Elements Of Vulnerability Administration Plan Sample PDF
This slide defines the main elements of vulnerability management program. It includes information related to assessment, management tools, integration and agility. Persuade your audience using this Key Elements Of Vulnerability Administration Plan Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Vulnerability Assessment, Vulnerability Management Tools, Integration And Alignment, Agility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Top Metrics For Corporate Vulnerability Analysis Diagrams PDF
This slide showcases enterprise vulnerability management metrics that are used to evaluate how well vulnerability management VM program is works. It also includes measures such as detection, meantime in resolving, scanner coverage, etc. Presenting Top Metrics For Corporate Vulnerability Analysis Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Scanner Coverage, Average Window Exposure, High Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF
This slide showcases tools for enterprise vulnerability management helps businesses secure their networks by identifying and fixing issues. It also includes tools such as nessus professional,nexpose community edition, openvas, manageengine vulnerability manager plus, etc. Persuade your audience using this Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations Environment, Limitless Evaluation, Implement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
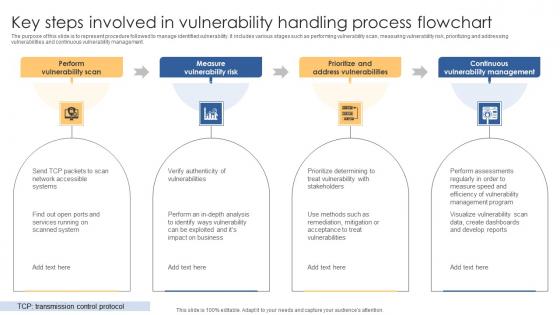
Key Steps Involved In Vulnerability Handling Process Flowchart Summary Pdf
The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management. Showcasing this set of slides titled Key Steps Involved In Vulnerability Handling Process Flowchart Summary Pdf. The topics addressed in these templates are Perform Vulnerability Scan, Measure Vulnerability Risk, Prioritize Address Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management.

Company Vulnerability Administration Define And Document The Plan Demonstration PDF
Deliver an awe inspiring pitch with this creative company vulnerability administration define and document the plan demonstration pdf bundle. Topics like build the vulnerability management team, coordinate with risk management. define standard remediation timelines, define how vulnerabilities should be documented, define periodic activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Company Vulnerability Administration Overview Input Template PDF
Deliver and pitch your topic in the best possible manner with this company vulnerability administration overview input template pdf. Use them to share invaluable insights on scoping statement, identify stakeholder, define regulatory and other legal requirements, stakeholder investment, management involvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
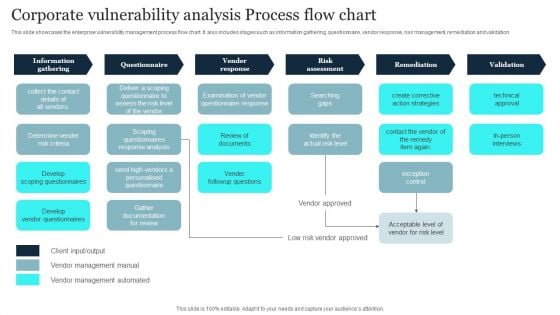
Corporate Vulnerability Analysis Process Flow Chart Summary PDF
This slide showcases the enterprise vulnerability management process flow chart. It also includes stages such as information gathering, questionnaire, vendor response, risk management, remediation and validation. Pitch your topic with ease and precision using this Corporate Vulnerability Analysis Process Flow Chart Summary PDF. This layout presents information on Vender Response, Risk Assessment, Information Gathering. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
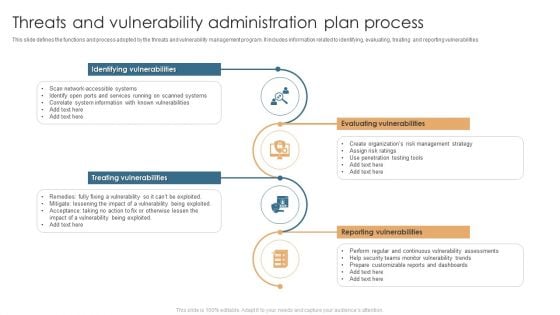
Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
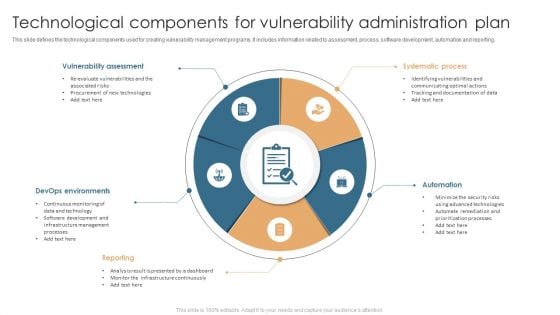
Technological Components For Vulnerability Administration Plan Slides PDF
This slide defines the technological components used for creating vulnerability management programs. It includes information related to assessment, process, software development, automation and reporting. Presenting Technological Components For Vulnerability Administration Plan Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Vulnerability Assessment, Systematic Process, Automation, Devops Environments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
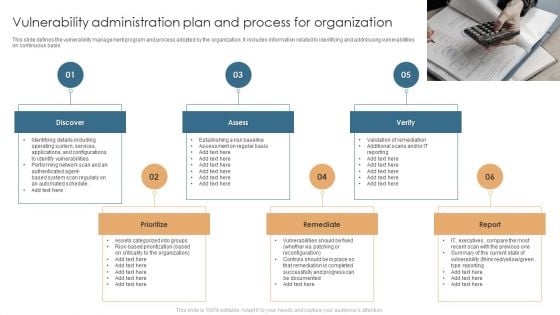
Vulnerability Administration Plan And Process For Organization Structure PDF
This slide defines the vulnerability management program and process adopted by the organization. It includes information related to identifying and addressing vulnerabilities on continuous basis. Presenting Vulnerability Administration Plan And Process For Organization Structure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Discover, Assess, Verify, Report, Remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
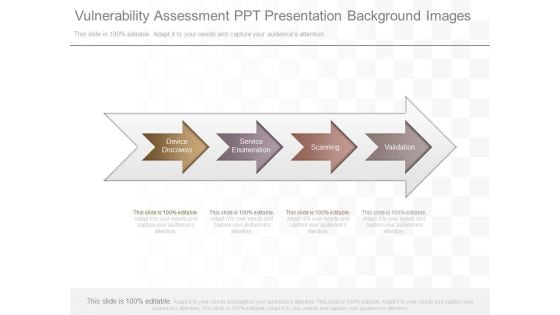
Vulnerability Assessment Ppt Presentation Background Images
This is a vulnerability assessment ppt presentation background images. This is a four stage process. The stages in this process are device discovery, service enumeration, service enumeration, validation.
Planning Vulnerability Administration Plan Icon Pictures PDF
Presenting Planning Vulnerability Administration Plan Icon Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Planning Vulnerability, Administration Plan, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Company Vulnerability Administration Roadmap Designs PDF
Presenting company vulnerability administration roadmap designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap 2018 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
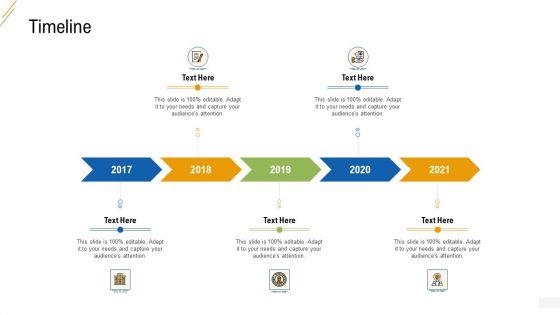
Company Vulnerability Administration Timeline Guidelines PDF
This is a company vulnerability administration timeline guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Overview Structure PDF
This is a company vulnerability administration overview structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it is a security weakness or flaw of a component in the technology stack of an organization, vulnerabilities may exist on network devices, servers pcs mobile devices applications or any other elements connected to the network, a typical organizations network has many vulnerabilities per device or system therefore even a small organization may have tens of thousands of vulnerabilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
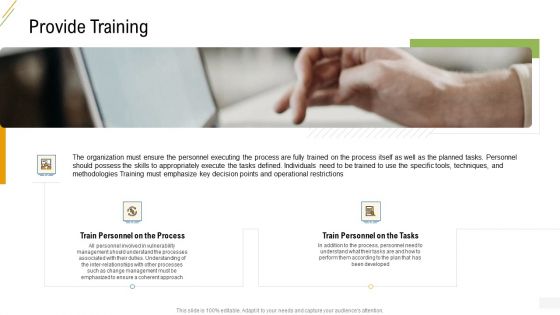
Company Vulnerability Administration Provide Training Background PDF
This is a company vulnerability administration provide training background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like train personnel on the process, train personnel on the tasks, in addition to the process, personnel need to understand, understand the processes associated with their duties. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
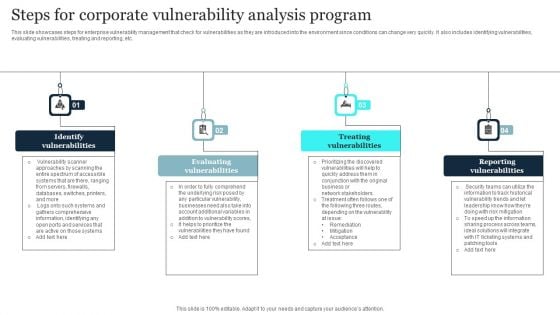
Steps For Corporate Vulnerability Analysis Program Background PDF
This slide showcases steps for enterprise vulnerability management that check for vulnerabilities as they are introduced into the environment since conditions can change very quickly. It also includes identifying vulnerabilities, evaluating vulnerabilities, treating and reporting, etc. Persuade your audience using this Steps For Corporate Vulnerability Analysis Program Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Treating Vulnerabilities, Reporting Vulnerabilities, Evaluating Vulnerabilities. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Company Vulnerability Administration Define And Document The Plan Team PDF
This is a company vulnerability administration define and document the plan team pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build the vulnerability management team, coordinate with risk management, define standard remediation timelines, define how vulnerabilities should be documented, define periodic activities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
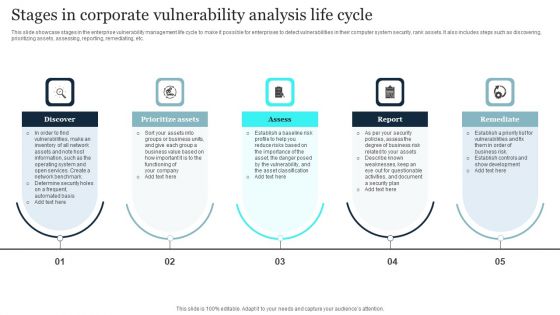
Stages In Corporate Vulnerability Analysis Life Cycle Slides PDF
This slide showcase stages in the enterprise vulnerability management life cycle to make it possible for enterprises to detect vulnerabilities in their computer system security, rank assets. It also includes steps such as discovering, prioritizing assets, assessing, reporting, remediating, etc. Presenting Stages In Corporate Vulnerability Analysis Life Cycle Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prioritize Assets, Report, Remediate, Assess. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
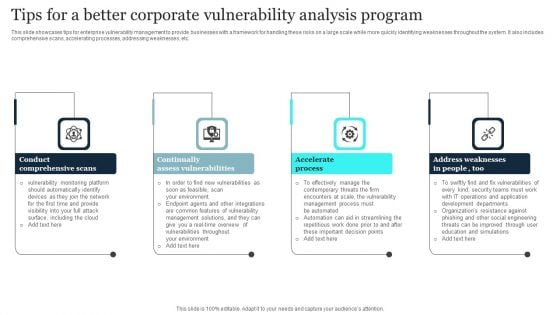
Tips For A Better Corporate Vulnerability Analysis Program Mockup PDF
This slide showcases tips for enterprise vulnerability management to provide businesses with a framework for handling these risks on a large scale while more quickly identifying weaknesses throughout the system. It also includes comprehensive scans, accelerating processes, addressing weaknesses, etc. Presenting Tips For A Better Corporate Vulnerability Analysis Program Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Continually Assess Vulnerabilities, Conduct Comprehensive Scan, Accelerate Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
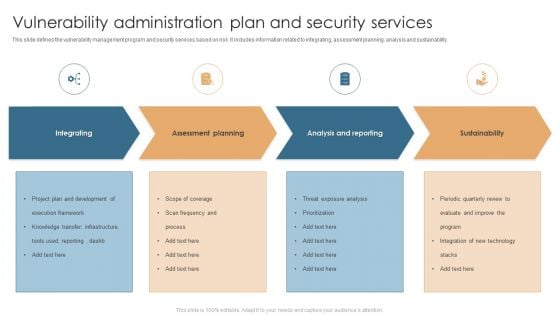
Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
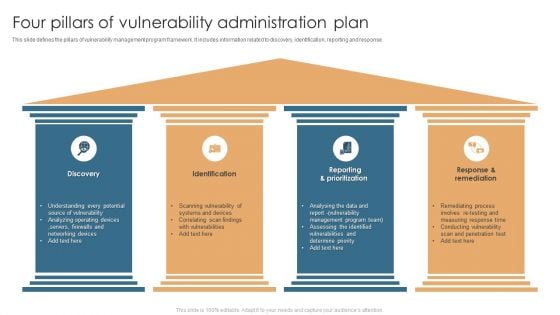
Four Pillars Of Vulnerability Administration Plan Formats PDF
This slide defines the pillars of vulnerability management program framework. It includes information related to discovery, identification, reporting and response. Persuade your audience using this Four Pillars Of Vulnerability Administration Plan Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Discovery, Identification, Reporting And Prioritization, Response And Remediation . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Open Source Corporate Vulnerability Analysis Software Tools Demonstration PDF
This slide showcases open source enterprise vulnerability management software tools that aids companies in securing their networks by locating and repairing flaws. It also includes descriptions regarding tools such as triviy, metasploit, openscap, etc. Persuade your audience using this Open Source Corporate Vulnerability Analysis Software Tools Demonstration PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Environment, Secure Web Applications, Industrial. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vulnerability Identification And Administration Plan Checklist Brochure PDF
This slide defines the checklist for vulnerability identification and management program. It includes information related to assets effected, vulnerability rankings and threats. Pitch your topic with ease and precision using this Vulnerability Identification And Administration Plan Checklist Brochure PDF. This layout presents information on Assets Affected, Potential Vulnerability, Vulnerability Ranking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Company Vulnerability Administration Determine Approved Methods Of Vulnerability Assessment Microsoft PDF
Presenting company vulnerability administration determine approved methods of vulnerability assessment microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine the methods required by regulation, determine the methods required to meet the operational requirements, determine the legal implications, determine the impact imposed by candidate methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Record Discovered Vulnerabilities Ideas PDF
Presenting company vulnerability administration record discovered vulnerabilities ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like discovery date and time, categorization, affected assets, priority assure access control of the repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Categorize And Prioritize Vulnerabilities Background PDF
This is a company vulnerability administration categorize and prioritize vulnerabilities background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analyze for relevance, determine responsibility, prioritize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
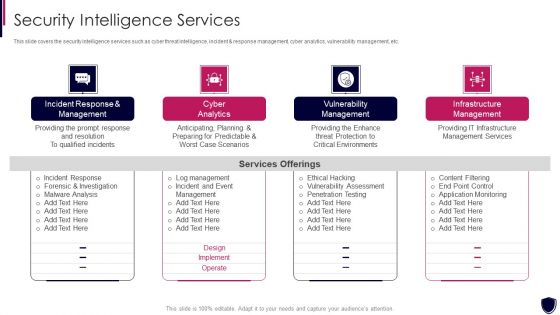
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
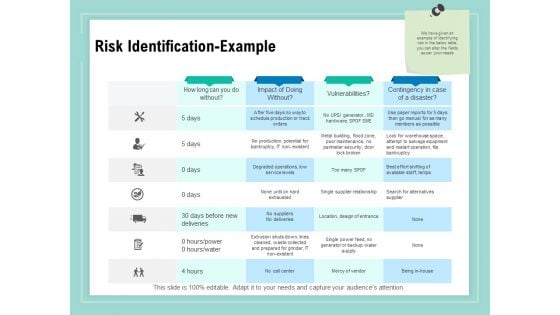
Vulnerability Assessment Methodology Risk Identification Example Ppt Portfolio Topics PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification example ppt portfolio topics pdf. The topics discussed in these slides are contingency in case of a disaster, vulnerabilities, impact of doing without, how long can you do without. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vulnerability Assessment Methodology Content Ppt Summary Infographics PDF
Presenting this set of slides with name vulnerability assessment methodology content ppt summary infographics pdf. The topics discussed in these slides are risk identification, risk register, risk assessment, risk analysis, risk mitigation plan, risk mitigation chart, risk tracker, risk management plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vulnerability Assessment Methodology Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name vulnerability assessment methodology ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are analysis, assessment, management, matrix, strategies. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vulnerability Assessment Methodology Risk Control Matrix Ppt Portfolio Infographics PDF
Presenting this set of slides with name vulnerability assessment methodology risk control matrix ppt portfolio infographics pdf. The topics discussed in these slides are key process number, process, risk number, risk, control objective, control number, control description, control owner, process narrative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
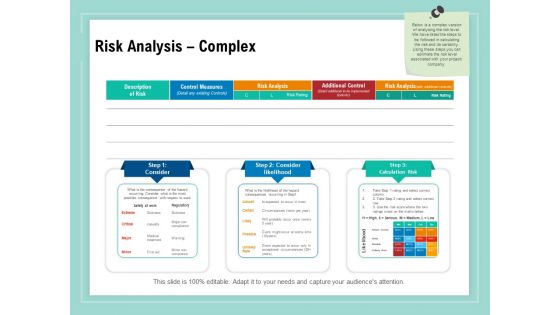
Vulnerability Assessment Methodology Risk Analysis Complex Ppt Outline Gridlines PDF
Presenting this set of slides with name vulnerability assessment methodology risk analysis complex ppt outline gridlines pdf. The topics discussed in these slides are description of risk, control measures, risk analysis, additional control, risk analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home